The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.
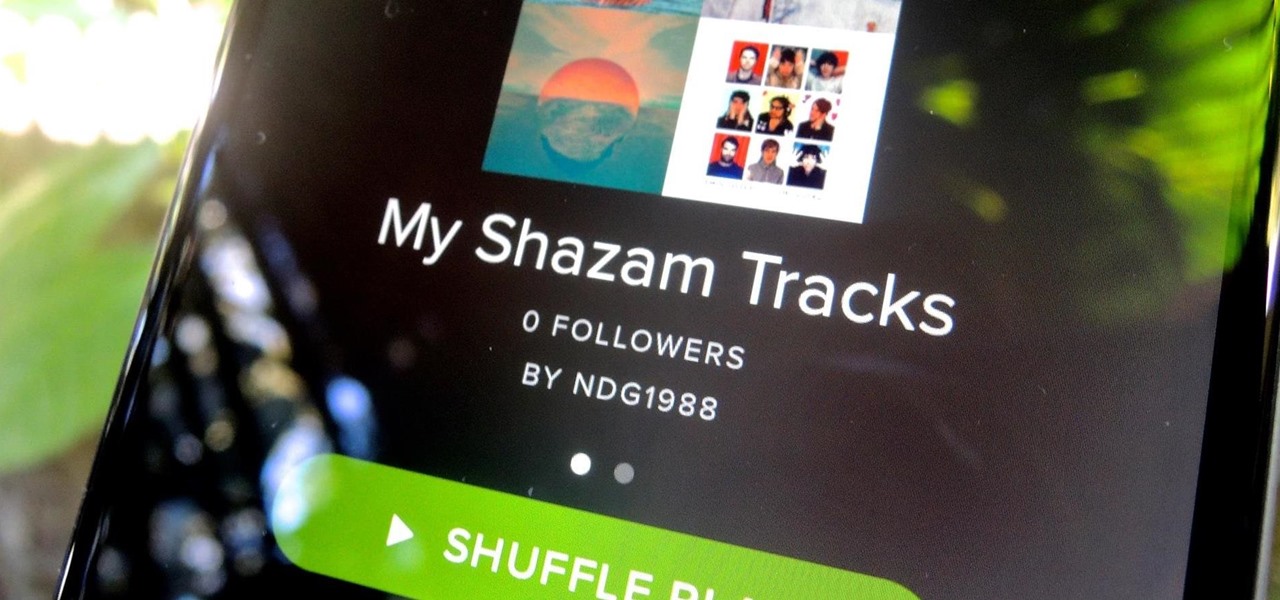
We recently showed you how to recover your Shazam history from Siri, which is a lot less intuitive than finding the songs you've tagged directly in the Shazam app. But with a subscription to Rdio or Spotify, there's no need to even locate your history. You can Shazam songs and have them automatically added to a newly created playlist titled "My Shazam Tracks."

Lateral muslces - better known as your obliques or love handles - typically don't get trained during ab workouts which focus on upper and lower abs but nothing on the side.
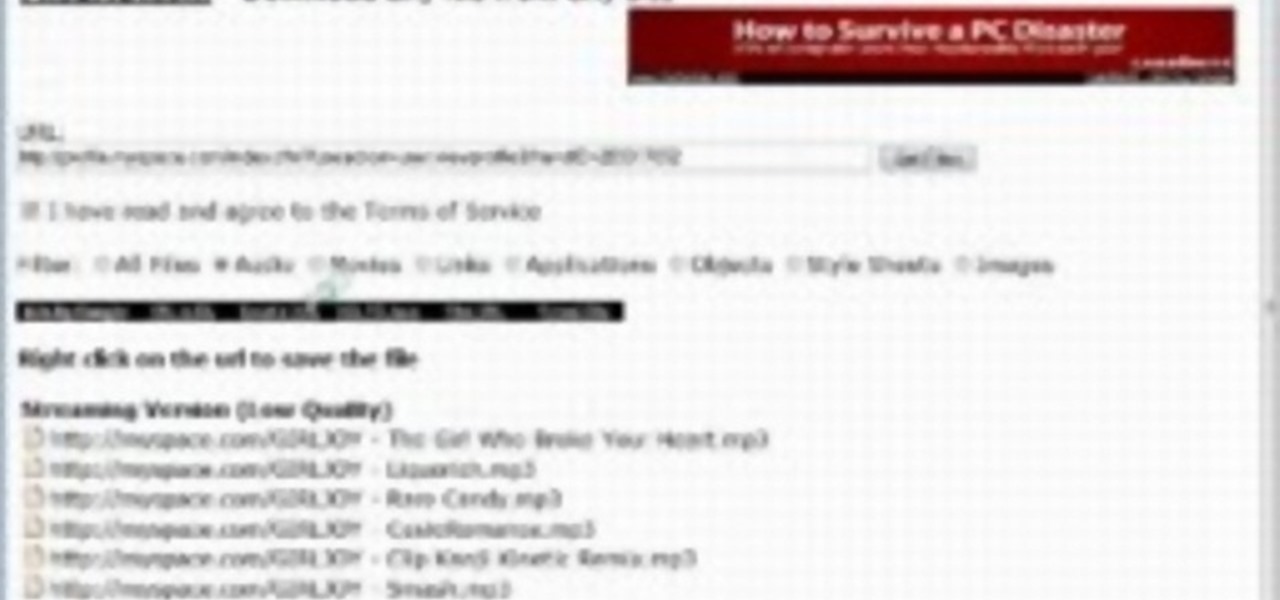
This video describes how get mp3s from MySpace that typically would not available for download on your computer. Even though the download link is not clickable the songs are still downloadable! Download all of your favorite music so you can listen to it whenever you want without an internet connection. Put the latest tunes, from your favorite musicians, on an MP3 player and show all of your friends cool new artists!
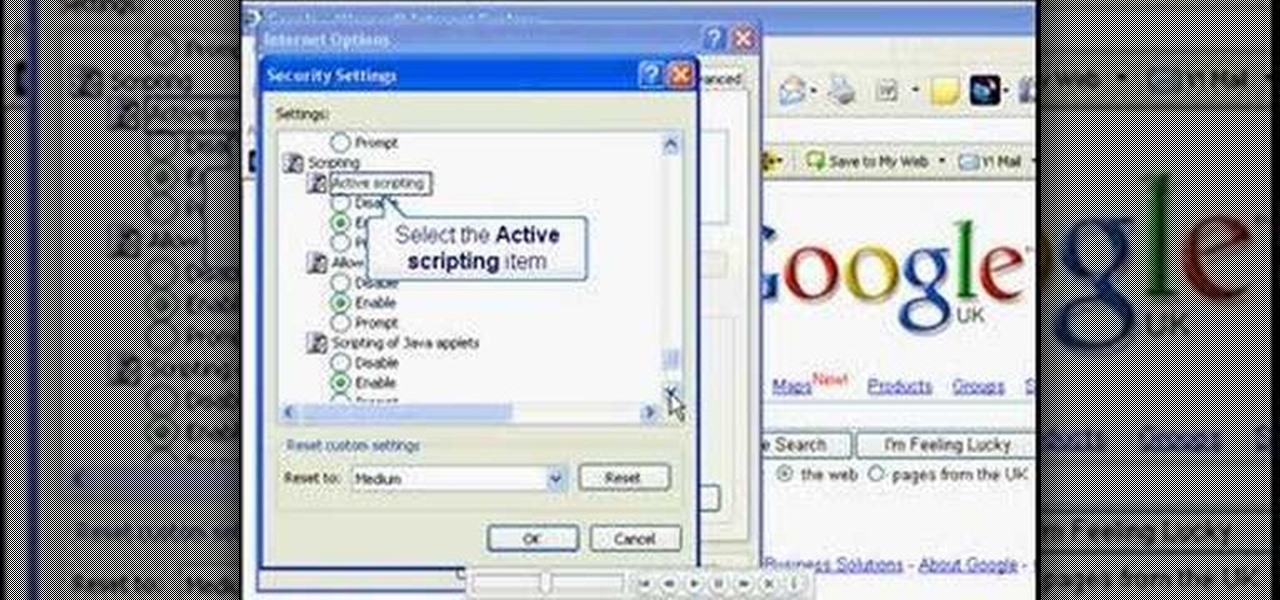
In this video, you will learn the steps to take to enable JavaScript in Microsoft's Internet Explorer (IE) web browser. Although JavaScript support is typically enabled by default in most modern browsers and many web applications depend on JavaScript being enabled to function properly, some persons and organizations may occasionally disable JavaScript to negate the effects of annoying or insecure implementation of JavaScripts on some web pages (such as pop-ups, hidden tracking links, unwanted...

This medical how-to video demonstrates how to do an equipment setup for hemodynamic monitoring. Follow the instructions and protocol for the equipment needed to setup hemodynamic monitoring before the physician arrives. This procedure is typically used for pulmonary artery catheter insertion.

How do I stop knitting? This instructional knitting video demonstrates how to do a basic knit bind off. Binding off is the process of taking the stitches off of your needle and securing them so that they don't unravel. The basic bind-off using knit stitches most popular with beginners. This version of the knit bind of is typically used with the stockinette stitch.

Coaxial cables are typically used for home video equipment, particularly TV AV (aerial and video) leads. Take a look at this instructional video and learn how to wire a coaxial plug. The coax plug consists of a body, a pin, a collett, a braid, and a clamp.

Moroccan food is delightfully delicious. Watch this how to video and learn how to make a Moroccan avocado and fig smoothie. Avocado is typically used in salads but you will be pleasantly surprised when you mix it up with dried figs.

Learn how to play your hand in no limit Texas Hold'em after the river. Learn what strong poker players typically do and how you should react to figure out what you should do to get the best odds for winning the hand. Master the game of Texas Hold'em!

Discover a new exotic typically Brazilian ingredients - Palmito. Despite being very popular in South and Central America, Palmito (Heart of Palm) has yet to make it into North American and European menus(much). Here's a very simple recipe to introduce you to the wonderful - Palmito.

The microwave "defrost" button typically serves as Tom’s magic one-step "braising" method. Fortunately, Chef Paul shows the correct way by featuring braised lamb in cabernet franc with currants and dried plums and braised osso buco with bacon. He even makes spaetzle on the side.

You aren't just born with broad Stallone shoulders and arms, gentlemen. Of course we know you wish you never had to work to get those tight, chiseled arms and shoulders, but even the best of the best - that's right, including Stallone - have to work what their mama gave them to keep in shape.

In this tutorial, we learn how to remove stretch marks with lasers. The laser treatment is the most effective for removing stretch marks. This will turn the purple marks lighter, and once they are silver/white, they will make those less apparent. The Affirm laser treatment is proven to be extremely effective to remove the stretch marks, and make them only noticeable under a microscope. It will take several sessions to drastically remove the stretch marks, but it will be worth it in the end. D...

This video provides a demonstration of how to beat the bosses of maps one through four of Epic Quest. The video game is an arcade style fighter where you lead teams of three creatures into battle. The first boss is a solitary enemy, easily taken down. The boss pair on map two is only slightly more challenging. The three squid creatures on map three are easily taken down, if you are level 31. On map four, you should be more careful. This boss team requires the use of several potions and healin...

In this photography tutorial video, the self-appointed "Prince of Cheap" shows you how to use natural light and enhance it with continuous fluorescent light for some really killer headshots that stand strong! This photographs are really strong. In this 5 minute clip, David explains his thought process while you watch one of his garage shoots that lead to great quality and many "How'd he do that?" exclamations. This time you'll be able to see him on his session! How much can you learn in 5 min...

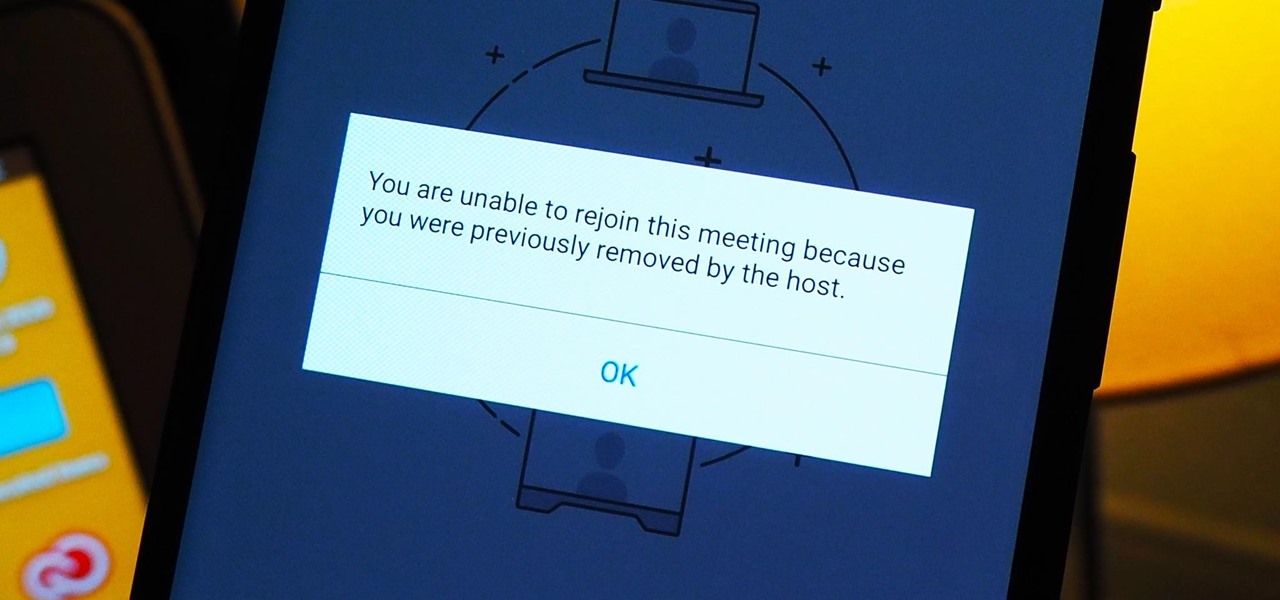
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

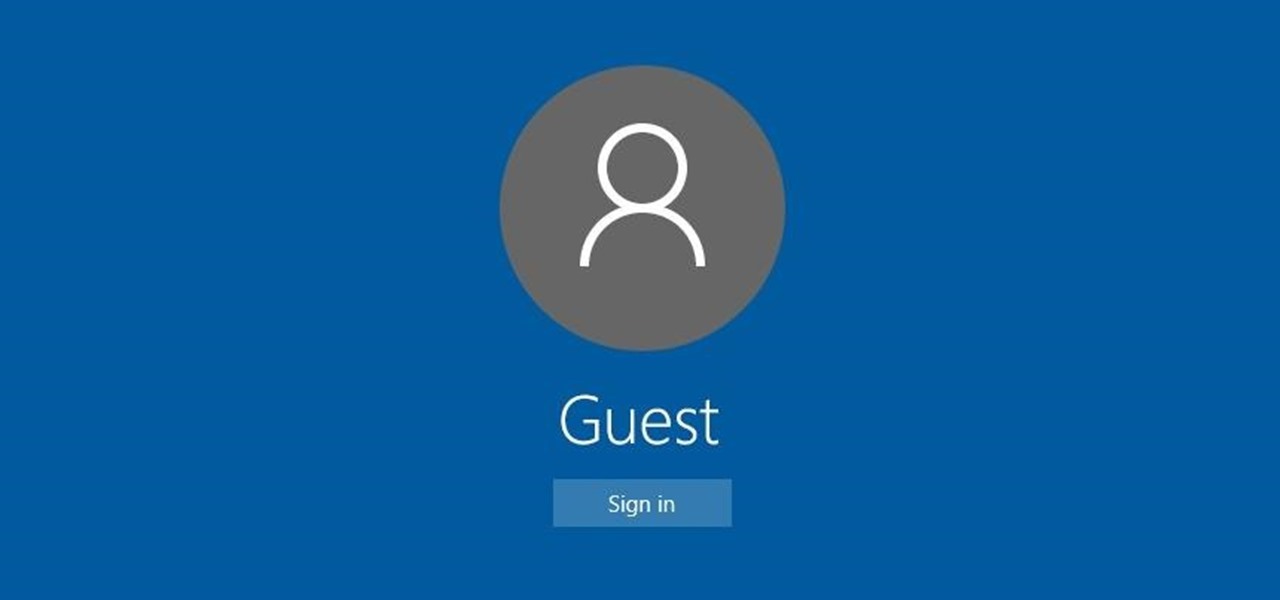
For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.

Heavy Water & Light Ice Experiment. What happens? Ice floating over vegetable oil but it decreases in baby oil.

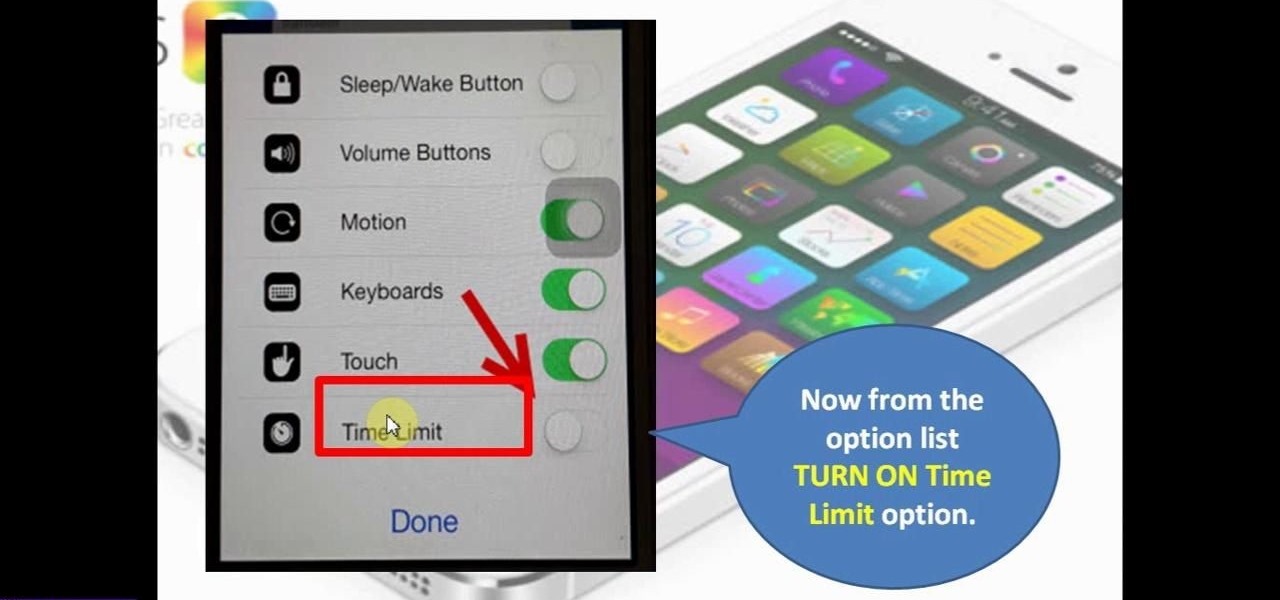
This video will show you how to set time limit for your children games in your iPhone or iPad. This will restrict children from excessive use of your iPhone or iPad. When this time limit is over, the game your child is playing will be stopped automatically. They will not be able to continue playing games until you start a new session for them. So please watch the video and employ it in your phone.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

Magic Leap just did something it didn't do during its recent Twitch hardware demo: show us some new demo footage of what augmented reality really looks like through the Magic Leap One.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

During Google Developer Days, taking place now at the ICE Congress Center in Krakow, Poland, an introductory session on ARCore provides some insights on how the platform operates.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Brought to you by Berocca® Video: .

The traditional method of installing drywall typically calls for a hand held screwdriver and a box full of drywall screws. This Home & Garden how to video demonstrates the proper operation of the automatic screw gun for installing drywall. Cut remodeling time in half by learning how to use an automatic screw gun.

A pop filter or pop shield is an anti-pop noise protection filter for microphones, typically used in a recording studio. In this how to video learn how you can make a pop filter out of cardboard and fabric for recording with microphones.

Barrel distortion is a lens effect which causes images to be "inflated". Barrel distortion is associated with wide angle lenses and typically occurs at the wide end of a zoom lens. In this video tutorial you will learn how to correct the lens distortion in Photoshop.

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.