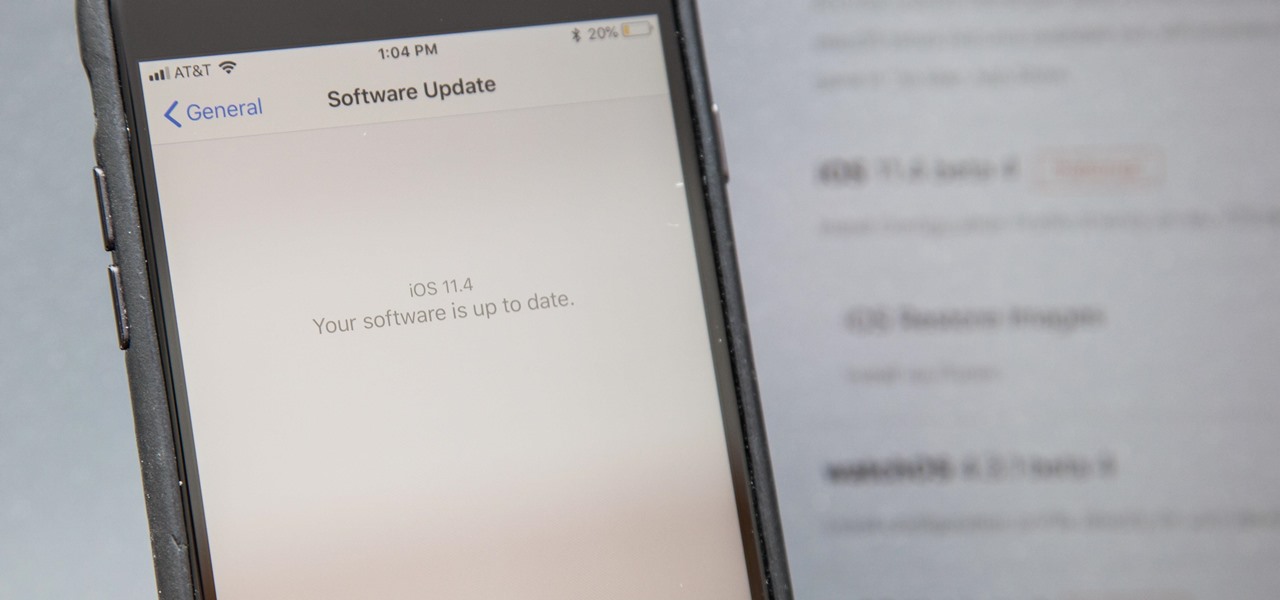
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.

While it may not be an obvious feature, Apple actually built a way into iOS that lets you hide specific pictures and videos in the Photos app that you want to keep on the down-low, for your eyes only. If you show off your photos a lot or stream slideshows to your TV, this is a great way to keep less appealing content private.

Instagram stories are a great way to share your day-to-day experiences with your followers. However, it can be disappointing to see them go after 24 hours, especially if you shared something really special. Now, Instagram has a way for you and your followers to relive those great stories you've created with a new feature called Story Highlights.

With technology giants like Apple and Google finally entering the fray, the move toward mass adoption of augmented reality is ramping up. Apple's ARKit and Google's ARCore will allow entirely new categories of apps to be made. Unfortunately, in a world of heavy competition, getting these two frameworks to work together wasn't a priority for either company.
You have a lot of choices when it comes to your next smartphone. iPhone, Galaxy, Pixel, G6, V20, and many more all vie for your wallet. Each of these phones are great for different purposes, but what if your main interest is mobile gaming? Which phone will give you the longest Minecraft session, or the best performance for Pixel Gun 3D?

At the eMerge Americas investors conference in Miami, Florida, Magic Leap founder and CEO Rony Abovitz previewed details of the launch of their highly-anticipated device.

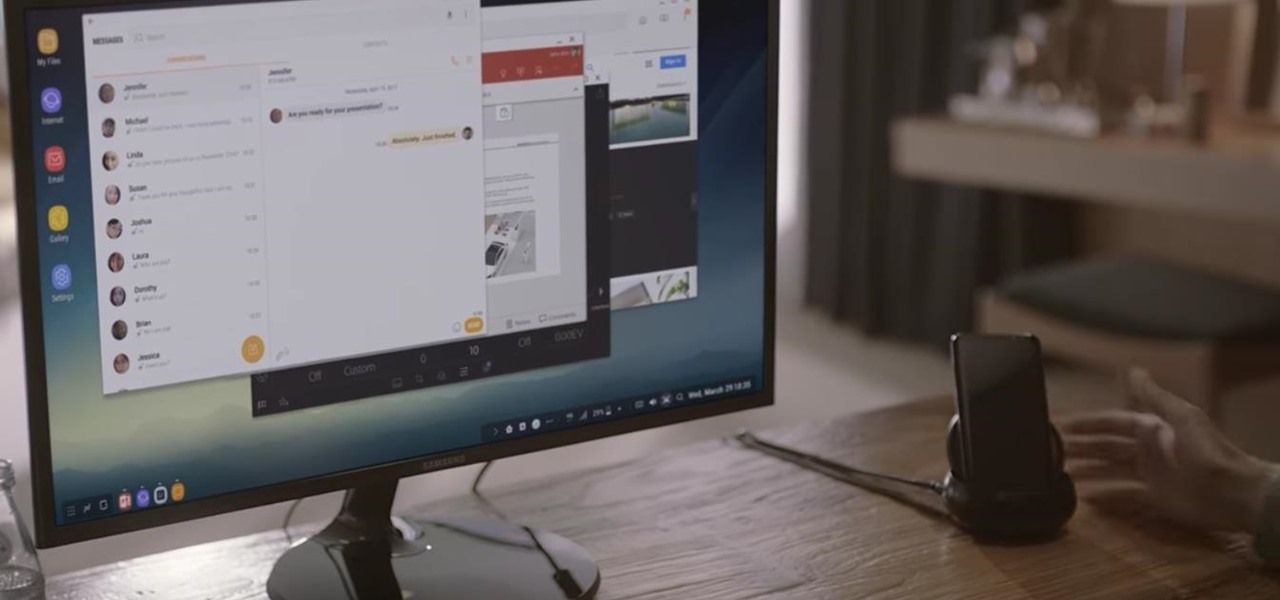
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in a browser any longer. Does this mark the end of the web browser entirely? Probably not. A lot of information works well on the page, and the Microsoft HoloLens still uses a pretty standard version of their own Edge brows...

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

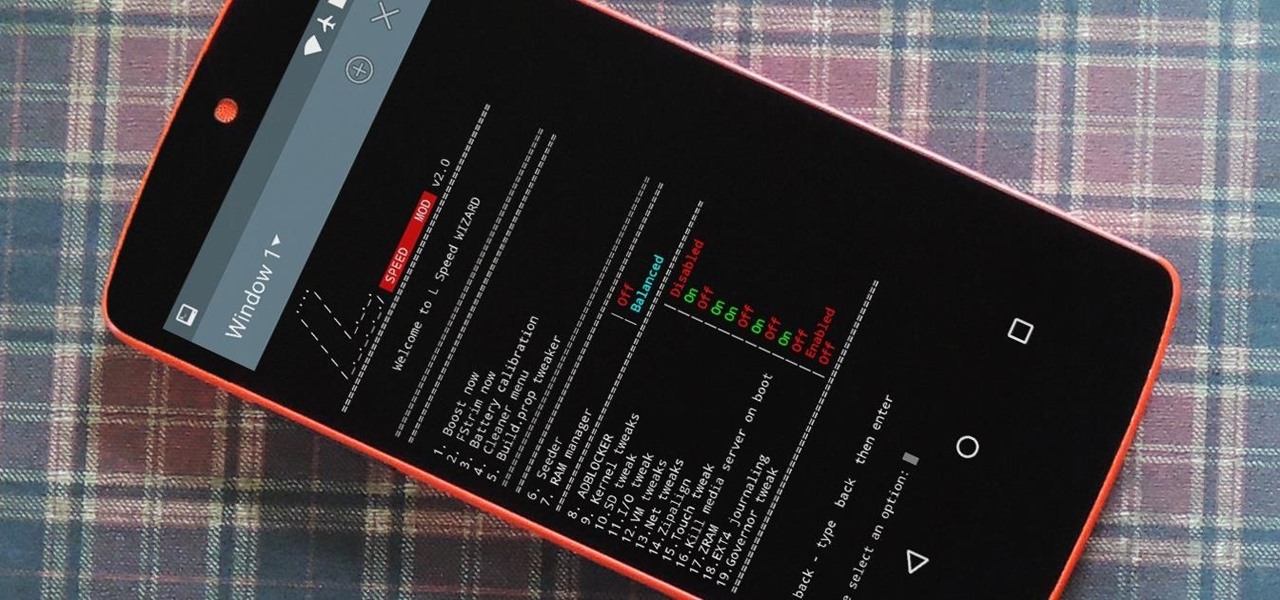
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management and other system-level functions, he created a flashable ZIP that will apply many fixes in one fell swoop.

YouTube's main player interface got a pretty big makeover recently, but chances are, the new UI hasn't made it your way just yet. Google has a habit of slowly testing the waters as they roll out new features, so cool tweaks like this can take some time to reach all users.

If you're the de facto tech support person in your family or circle of friends, you know how frustrating it can be to have to hold someone's hand and walk them through every troubleshooting step. Luckily, several options now exist for you to remotely access a Mac or Windows PC, which effectively skips the middle man and lets you get straight to fixing the issue yourself.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

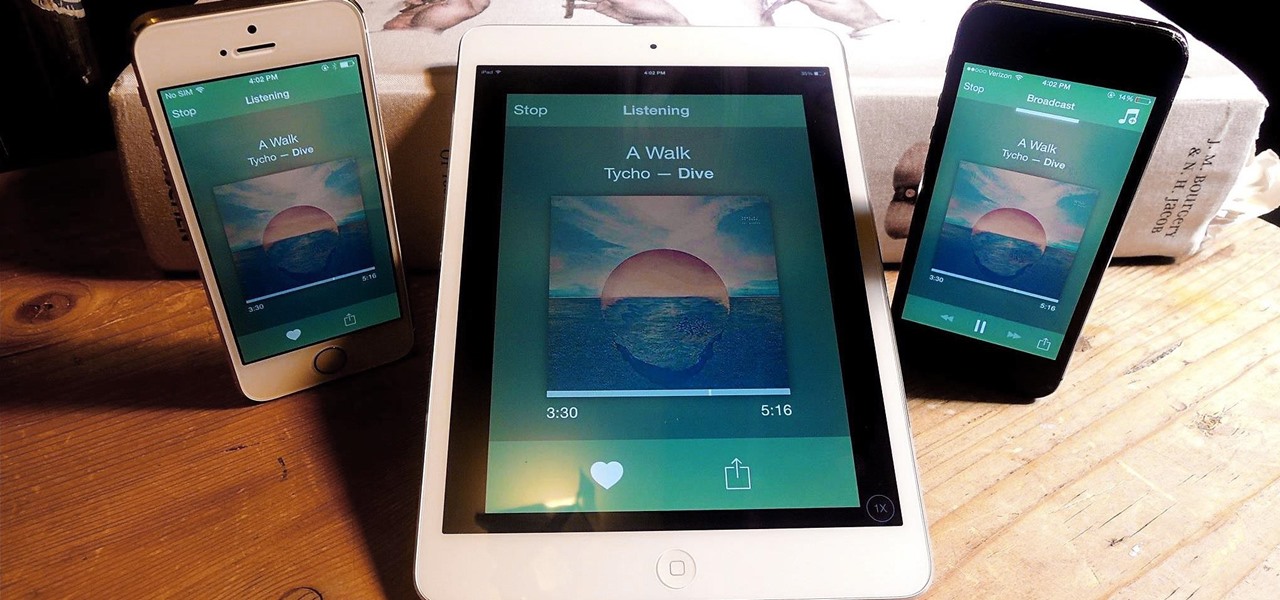
Audibly, from iOS developer Nick Frey, allows you create playlists and sync your music across other iOS devices. Like the Samsung-exclusive Group Play or the older Seedio app, you can connect a slew of compatible devices to create a surround-sound stereo of sorts when playing your music.

Merely fidgeting and shivering can burn calories, but now you can add trembling in fear to the list too. Just pop in a good horror movie and turn down the lights to burn off up to 200 calories. What would you rather do? Walk for over 30 minutes or watch a 90-minute scarefest?

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

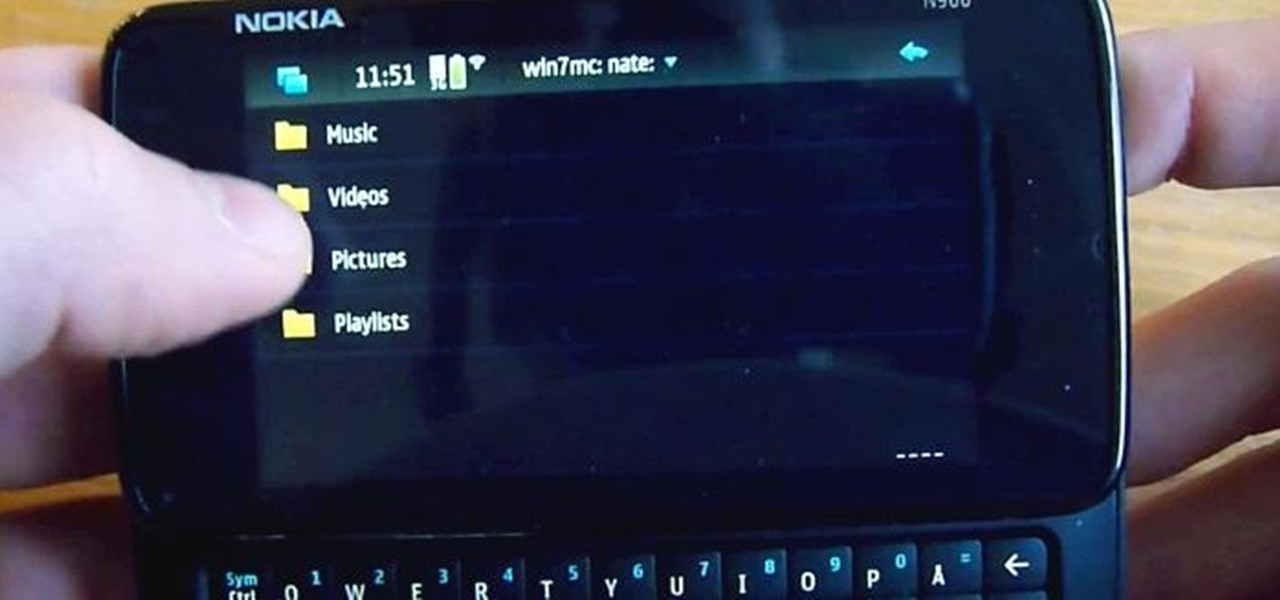
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Apple has revolutionized how we write with the introduction of its new Writing Tools, powered by Apple Intelligence. In beta on iPhone, iPad, and Mac, these tools allow you to select text and use intelligent features to summarize, proofread, or rewrite it until the tone and wording are just right. In a future beta, Writing Tools can even write original content for you.

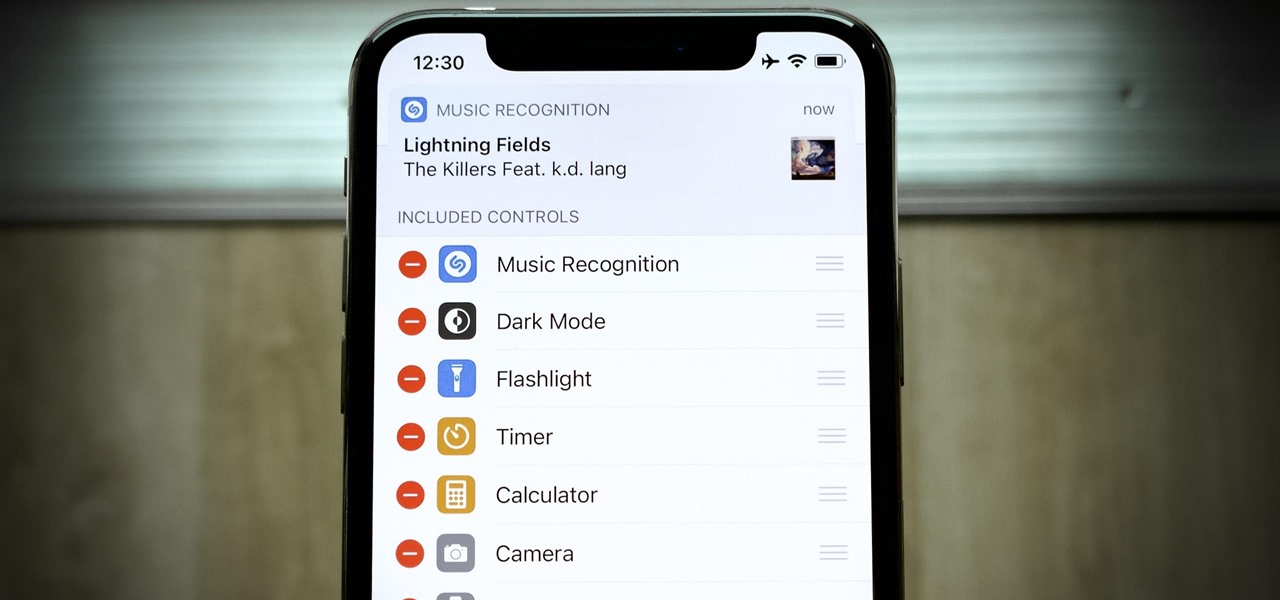
Apple just released the first beta for iOS 14.2 to iPhone software testers today, Monday, Sept. 21. This update brings a new Control Center tile for Shazam music recognition, a redesigned Now Playing Control Center tile, and a new "People Detection" feature in Magnifier.

Apple just released the fifth public beta for iOS 14 today, Wednesday, Aug. 19. This update comes one day after Apple released iOS 14 developer beta 5. It follows iOS 14 developer beta 4 by 15 days, and iOS 14 public beta 4 by 13 days.

Apple just released the fifth developer beta for iOS 14 today, Tuesday, Aug. 18. This update comes two weeks after Apple released iOS 14 developer beta 4, and 12 days after the release of iOS 14 public beta 4.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.

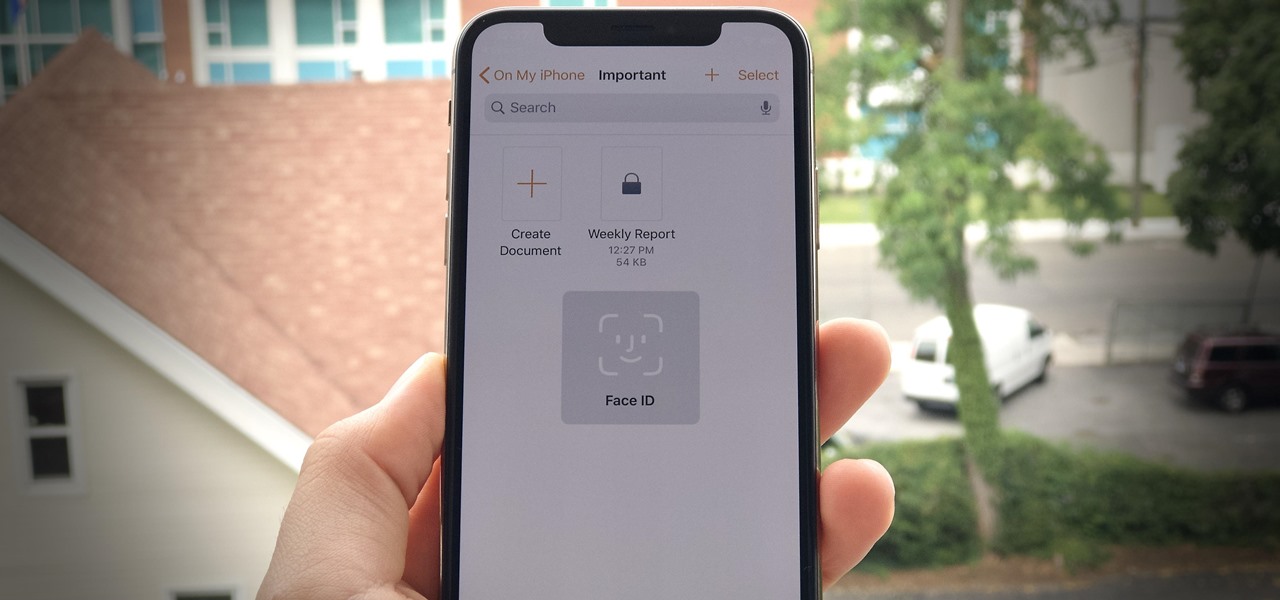
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

In this era of smartphones, we all know very well how easily we can get addicted to our devices. Spending hours each day doing the endless scroll through Facebook and other social media sites just because we feel like we'll miss something if we don't. Both Google and Apple are aware of this and are trying to help control smartphone addition in their own way for Android and iOS.

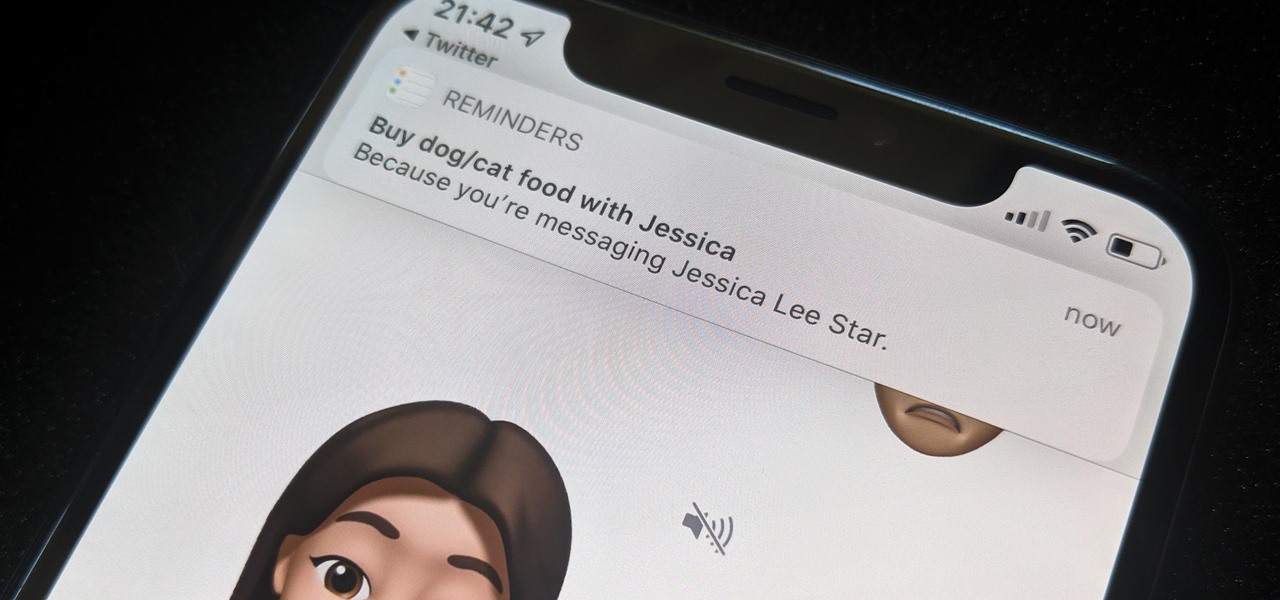
While iOS 13 might have made waves for some of its more prominent features — most notably system-wide Dark Mode — some of the more interesting tools lie with its smaller, unannounced updates. One of those updates is a new Reminders setting to tag contacts in a to-do task so that iOS pings you when texting that person in Messages.

Developers in the augmented reality industry got a lot of love this week.

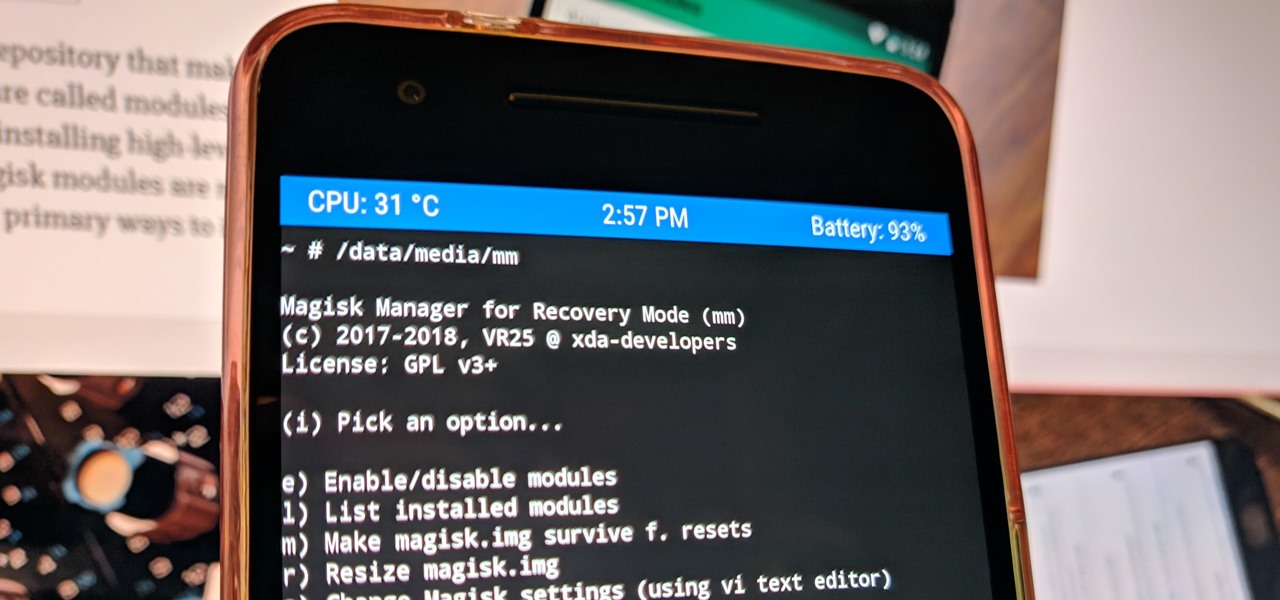
When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a while, which could cause some issues on its own.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.