
How To: 9 Things Super Successful People Do That You Should Too
Want to live your life like most high-achieving, successful people? First things first—set your morning alarm clock to at least 5 a.m. and don't be tempted to hit the snooze button.


Want to live your life like most high-achieving, successful people? First things first—set your morning alarm clock to at least 5 a.m. and don't be tempted to hit the snooze button.

Neuroscience (live!) resumes its 50 hour slicing session 8:00 am PST this morning. According to Gizmodo,

It's no secret that water and electronics don't mix well, but somehow, people always manage to combine the two. I've had my fair share of water-damaged electronics, everything from cheap headphones to a desktop computer. My devices are getting dunked in water so much, it's like doughnuts in coffee. And I know I'm not the only one. That jam session with your favorite song will end really quick when your iTouch is chilling in the toilet bowl.

What's your highest scoring game of Scrabble? Since starting this Scrabble World, I've been able to break 500 points on a regular basis. This year I've even managed to break the 600-point barrier a couple times. If you ask me, that's a pretty hefty sum to score in one game, but I'm not on par with the professionals yet.

With the rather large success of the Community Byte activities, both programming and HackThisSite, I have decided to continue to do both activities every session! With that said, when programming sessions occur, they will be lead by Sol Gates in Gobby. Also, the programming mission will no longer be to code a tool, we have changed it to be even more "noob friendly". This means that instead of coding a tool, you will be walked through puzzles and challenges that must be solved by coding a scri...

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.

Our first Community Byte went well! We had around 8 people in the room coding collaboratively and watching to learn. LukeStav did the kind task of hosting it on Gobby for all of us, so big thanks to him!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Note: This shower is only visible in the Northern Hemisphere. The Quadrantid meteor shower is one of my personal favorites, mainly because of the amount of meteors it produces. You can sight more than 100 meteors per hour- that's more than 1 meter per minute. Even though that doesn't sound like much, it will make your observing experience much more exciting. The peak is short, typically lasting no more than an hour or so. It is more easily observed on the fourth, with its peak at 1:00 AM EST.
Hello everybody, I am Merrill Kazanjian (aka kazanjianm on YouTube). I will be your instructor. Before starting your figure drawing session. Please watch this short, funny video first to learn the basics of human proportion. The rules that you learn in this video will be very helpful once we start figure drawing (The second video).

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...
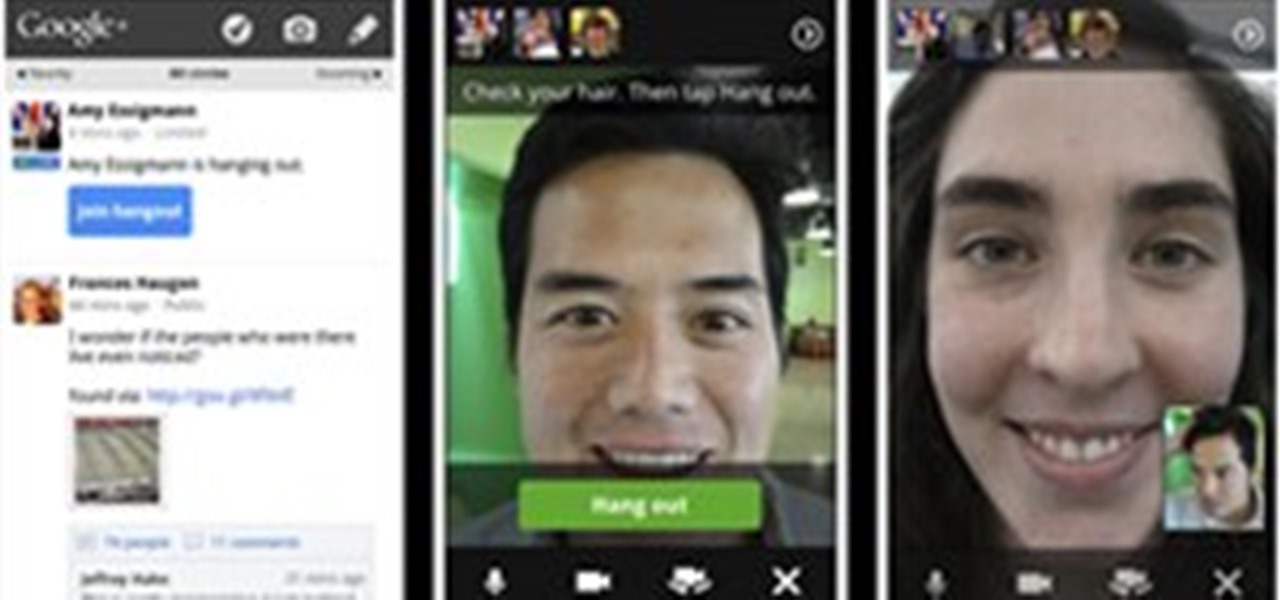
It may not seem like it, but it's been less than 90 days since Google+ was introduced to the world. Since then, we've seen many great features that have made Google+ one of the most attractive social networks around. Today, we've received even better news: major improvements and feature updates that are truly innovative.

The UK print media has been yellower than the middle traffic light for a long time now. The News of the World scandal has cast that into particularly sharp relief of late. The Sun, one of the biggest newspapers in the United Kingdom, demonstrated it again last week when they ran the front-page headline "DEATH BY XBOX".
Type: Digital, Theme Theme: Kid Toys Model
One of the common mistakes I see a lot of candidates make when they go to an interview is that they think it is a question and answer session. They approach the interview with a mindset that their role is to be prepared to answer a bevy of questions thrown at them. This puts you in a passive role, playing defense. A much more effective approach is to go into the interview with the mindset that you are a salesperson, and the product you are selling is you. You want to convince the employer tha...

There is an abstinence game being created by the University of Central Florida with $400k+ of taxpayer money. The game is directed at middle school girls to help them handle and cope with sexual advances.

FOXBORO, Mass. - The New England Patriots Alumni Club (NEPAC), announced that more than a dozen former Patriots players are gearing up to host a "Football for You" youth clinic in Worcester on Saturday, May 29 from 12:30-5:00 p.m.

Kizeme This Japanese word, kizeme, means "spirit of attack." It is said of Miyamoto Musashi, the famed Japanese swordsman, that as he grew older he relied more on kizeme to defeat adversaries and, as a result, emerged victorious from challenges without taking the life of his opponent.

Review: Marmaduke I liked the part where the fake dogs danced.

By now, most of you have updated to the new Xbox look. Just as expected, it's got some great new features. The dashboard looks great and Bing integration is awesome, but I'm very unhappy about the new Netflix interface. It's awkward, slow, and half of the items don't even load correctly. I can't even play some movies. And the instant play feature is kind of annoying. When I first chose a video, I was hoping when it instantly started playing that it was a trailer, à la Zune. Alas, no.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

You're never going to see a project from me that involves straight pipe. You would have when I was a kid, but after too many years in the construction industry, I need to see a good finish. If the project doesn't look slick, I don't want to say I did it.

From the onset of the popularization of apps for the iDevice, users have experimented with creating original artwork on their iPhone/iPad/iPod Touch. And when famed British artist David Hockney christened the iDevice with his painterly digital drawings, the trend exploded even more.

Love them or hate them, Live Photos have their place. The problem is, they're always on, requiring you to disable the feature every single time you open the Camera app. At least, that's how Apple has things set by default — but you can change that with just a few taps.
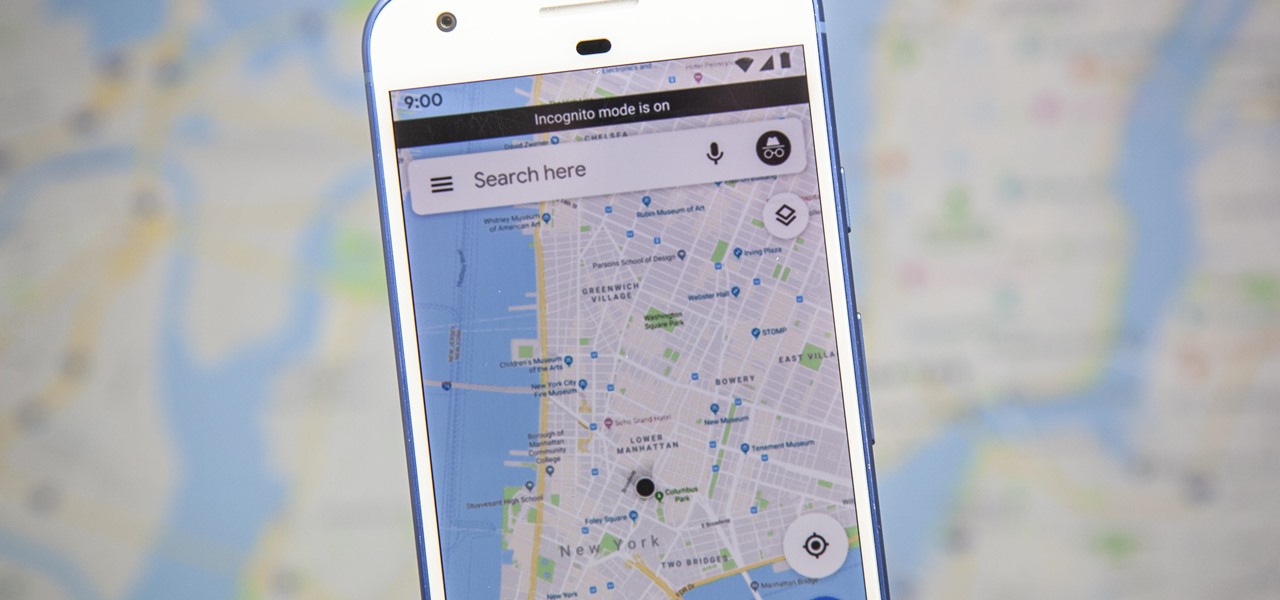
Google just recently added an incognito mode feature to Google Maps for iPhone and Android. With that, you can now use Maps in private at any time, which means you can browse and search with peace of mind.
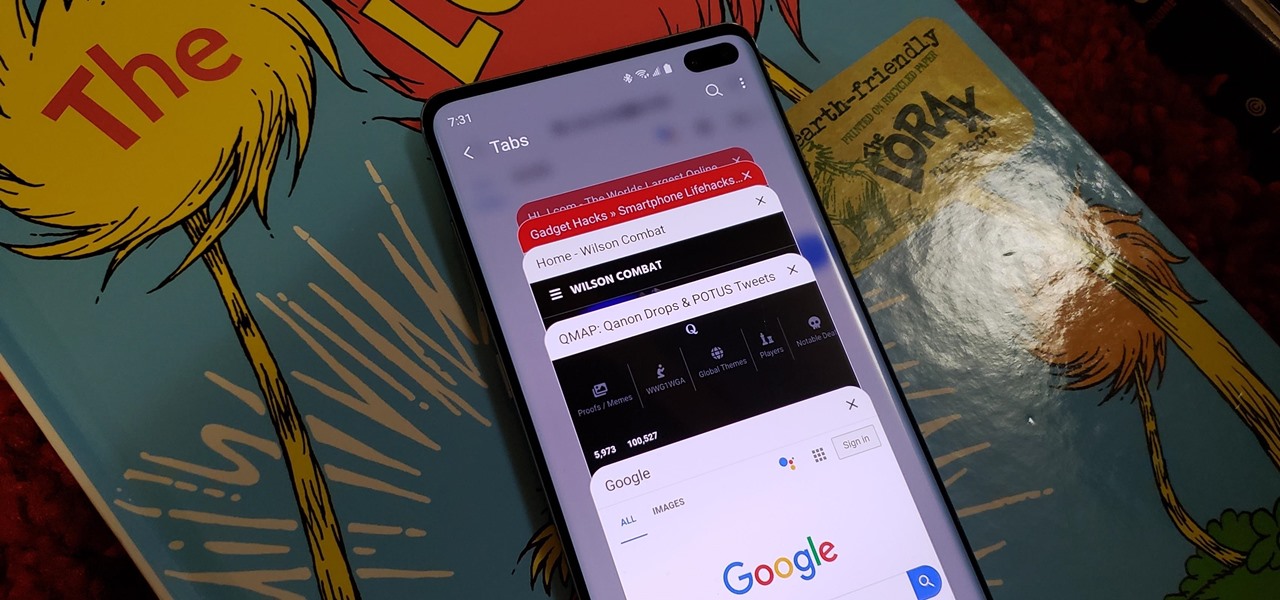
Samsung Internet makes it easy to close your browser tabs thanks to intuitive controls, but this also means it's easy to accidentally close a tab. Fortunately, you can recover recently closed tabs on your Galaxy in just a few taps.

As part of the Samsung Development Conference today, Samsung unveiled that they will expand support for Google's ARCore platform to include the Galaxy S8+ and Galaxy Note 8.

Want to sear the perfect restaurant-quality steak in the comforts of your own kitchen? Use a cast iron skillet.

What to do when your motivation is running low and you absolutely don't want to do something that needs to get done? If nothing is working for you, hack your brain with the following techniques to motivate yourself.

When you share a computer with other people, privacy can be a complicated matter. Even if you trust the other users, there are some things that you don't want anyone else having access to. Sure, you can encrypt everything, but what happens when someone needs to use the computer while you're in the middle of something?

To say Steven Purugganan is fast is an understatement. The twelve-year-old from Longmeadow, Massachusetts has won two Cup Stacking world championships, and appeared in commercials for McDonald's and Firefox.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...
+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...