
News: Unity Hustles to Add ARKit 3 Support to AR Foundation
After Apple unveiled ARKit 3 at WWDC on Monday, Unity Technologies wasted little time on ensuring its developers can take advantage of it.


After Apple unveiled ARKit 3 at WWDC on Monday, Unity Technologies wasted little time on ensuring its developers can take advantage of it.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Electronic Arts is inviting players of The Sims Freeplay and their friends to visit the homes of their Sims in augmented reality with a new AR mode that supports multiplayer and persistent content using ARKit 2.0.
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console.

In this tutorial, we learn how to remove stretch marks with lasers. The laser treatment is the most effective for removing stretch marks. This will turn the purple marks lighter, and once they are silver/white, they will make those less apparent. The Affirm laser treatment is proven to be extremely effective to remove the stretch marks, and make them only noticeable under a microscope. It will take several sessions to drastically remove the stretch marks, but it will be worth it in the end. D...
This video provides a demonstration of how to beat the bosses of maps one through four of Epic Quest. The video game is an arcade style fighter where you lead teams of three creatures into battle. The first boss is a solitary enemy, easily taken down. The boss pair on map two is only slightly more challenging. The three squid creatures on map three are easily taken down, if you are level 31. On map four, you should be more careful. This boss team requires the use of several potions and healin...

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

In recent years, augmented reality has increasingly helped to take art off museum walls and bring it (virtually) into people's homes and communities, offering new perspectives on classic pieces and modern creations alike.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Remember concerts? Those were fun. While gathering in large groups to listen to live music might not be allowed at the moment, the live music part still is. Thanks to the internet, more and more musicians are taking the stage each day to perform for those of us stuck in social isolation due to the new coronavirus. The best part? Many of these concerts are 100% free.

It seems like people are always trying to lose weight..but what if you have the opposite problem? Whether you’re recovering from an illness, are a growing teen, or you are an athlete trying to bulk up, a little information can go a long way in helping you pack on a few extra pounds.
While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free movies, TV, music apps, concerts, internet, fitness sessions, classes, and more.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!
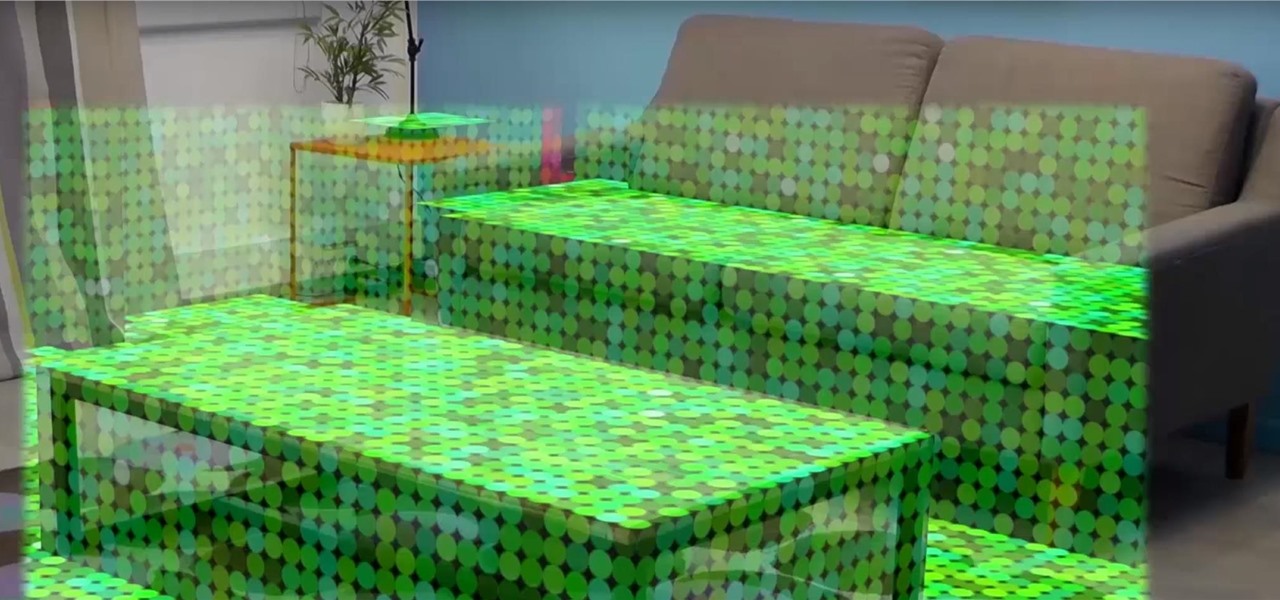
Once you've designed some holograms with HoloLens, you'll need to get them to interact with the environment. That's where Spatial Mapping comes in. There are five basic purposes for using HoloLens's Spatial Mapping with your app:
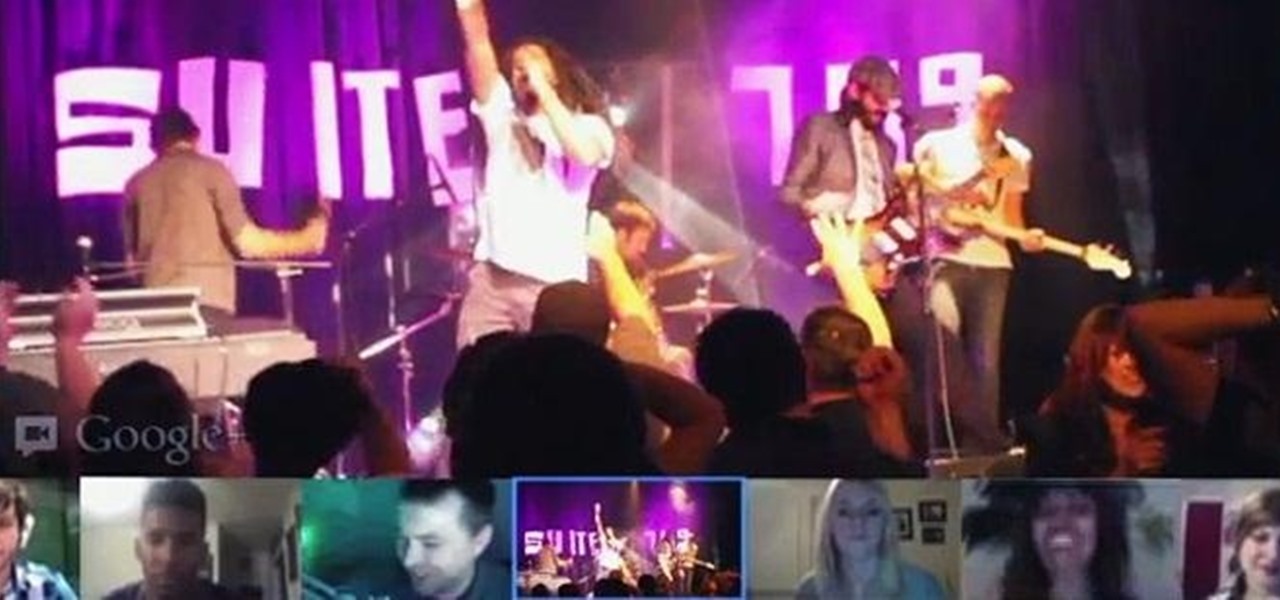
If you're a musician, Google wants you on Google+ Hangouts. In an effort to make it easier to stream your concerts, performances, and impromptu jam sessions, they've revealed their latest feature: Studio Mode. Enabling the new Studio Mode optimizes your Hangouts On Air for music, and the quality difference is massive.

If you're an AirPods user, things are a lot better with iOS 18 and iPadOS 18. If you're not, it may finally be time to grab yourself a set of AirPods, especially if you're into privacy and gaming.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.
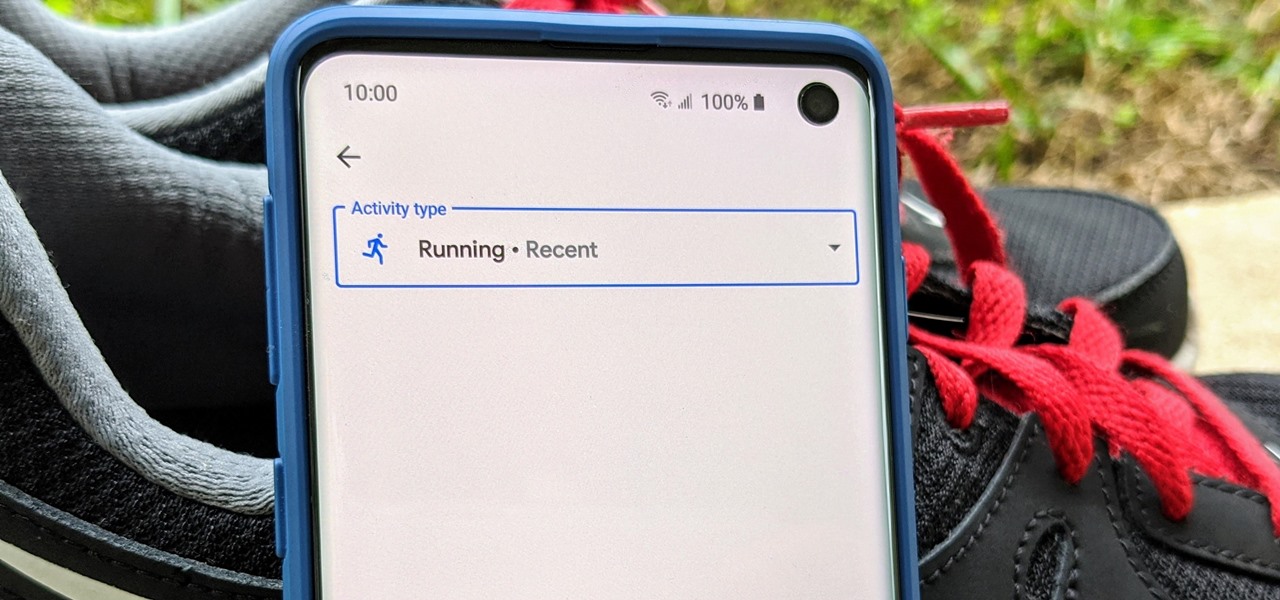
Google Fit houses all of your essential fitness-related information in the cloud for safekeeping at all times. You can easily let your device detect your workout sessions for you automatically based on a variety of sensors. At the same time, the Fit app makes it easy to manually start a workout as well.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Did you forget to get a Christmas gift for that niece or nephew who you see once a year? If you're lucky, the Walmart near you may have a Merge Cube in stock. When paired with the 57° North game for the Merge Cube, the mysterious-looking cube offers the possibility of extended sessions of virtual adventure in the palm of your hand. Available for $2.99 through the App Store or Google Play, 57° North is a choose-your-own-adventure game that takes place in augmented reality.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

When it published its 2016-2017 catalog last year, Savannah College of Art and Design (SCAD) became the first college to leverage augmented reality technology for a college catalog.

If you've been debating on whether or not HTC's new virtual reality headset, the Vive, is worth the $800 price tag, then you'll be able to find out for yourself soon enough.
You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

Trying to remember if it's "beer before liquor or liquor before beer" can be too much of a hassle, especially if you've already have had a few too many. While it would be great if one rhyme could determine the amount of pain you will feel the next morning, we must accept that we all react differently to alcohol and that's that.