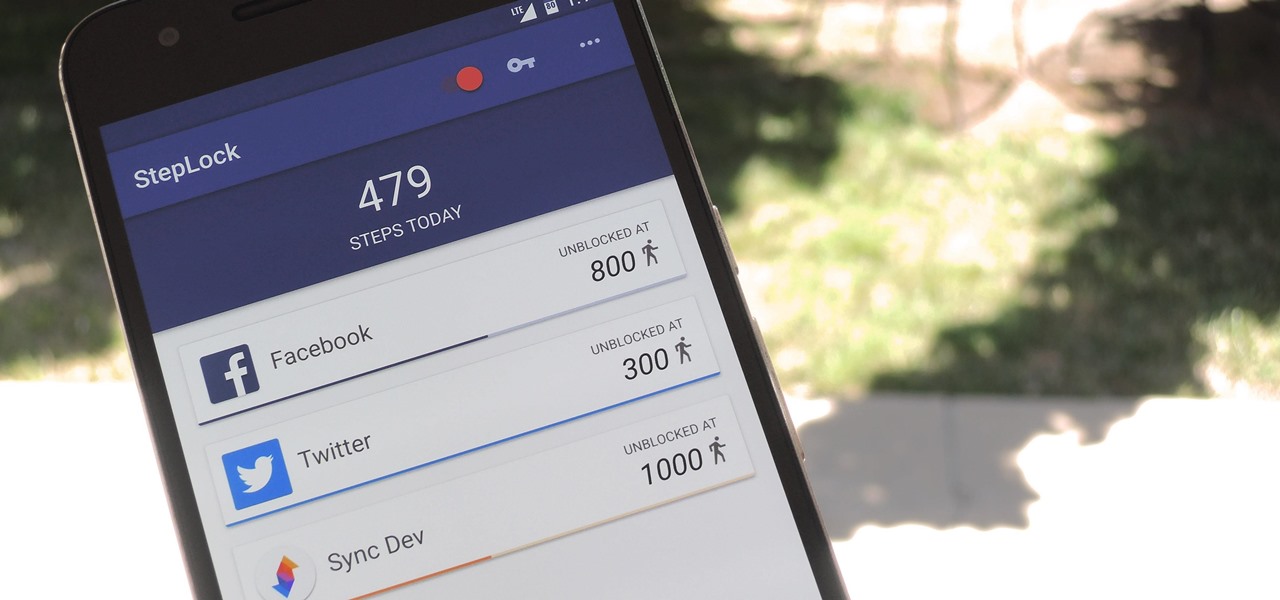
Most newer Android devices manufactured in 2014 or later have a built-in pedometer for tracking your fitness activity. This step counter is a great way to keep yourself in shape and motivated, but developer Leonardo Cavaletti has come up with an even better way to put it to use.

The internet, as I understand it, is a wonderful, magical place where people congregate to share memes and viral videos. Well, okay... there's a lot more to it than that, but let's just focus in on the good stuff.

Even today, smartphone text input leaves a lot to be desired. It's difficult to select specific words, the cut/copy/paste menu isn't always accessible in every app, and we're lacking undo and redo options, even though it's as simple as pressing Ctrl + Z on computers.
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

North American users get a raw deal when it comes to Sony devices. For some reason, the critically-acclaimed Xperia lineup of smartphones is hardly ever available here, whereas in Europe, the Sony Xperia Z series is one of the most popular flagship devices around.

Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that today's devices are capable of doing far more than beeping at 7 in the morning.

The new lock screen in iOS 10 is a lot different than previous versions, but one thing that stuck around is the quick access camera shortcut. The only real difference aside from aesthetics is that now you don't have to swipe up from the camera icon. Instead, you can simply swipe to the left from right side to quickly snap a picture.

I was skeptical when I first heard about GifWidget, an Android widget that lets you place GIFs on your home screen. As much as I love GIFs, did I really need to see this, this, this, or this, or even this, forever repeating on my phone?

Most sandboxes wait for children on a playground or the occasional zen garden raking. This one combines light, sand, and depth cameras to create a completely malleable topographical map you can alter with a brush of your hand.

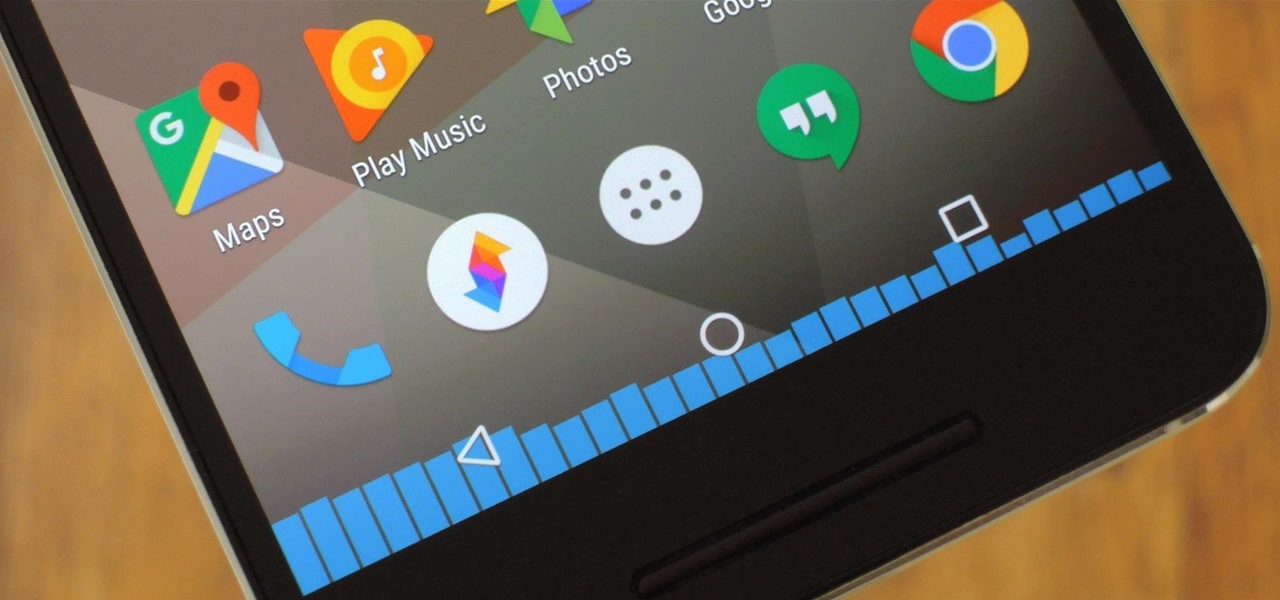
CyanogenMod, the popular custom ROM available for many Android devices, has a nice little feature that displays a music visualizer beneath your on-screen navigation keys while you're listening to your favorite songs. It's a subtle touch, but it makes for a more immersive experience when you're jamming out while using your phone or tablet.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

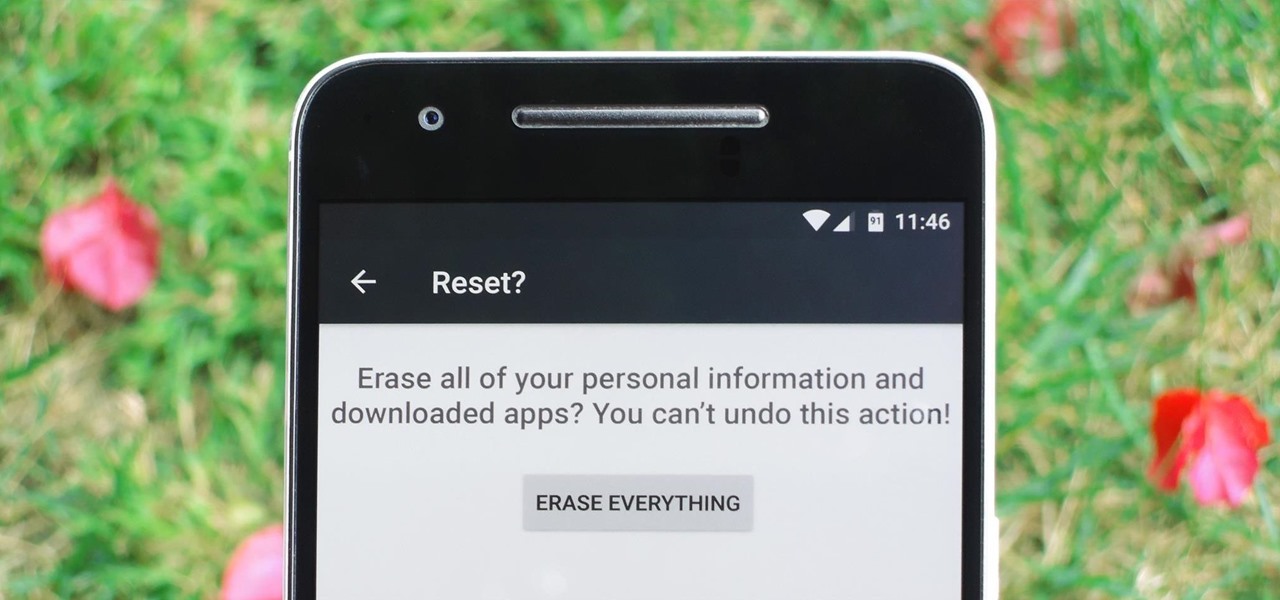
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

Samsung's latest flagship devices—the Galaxy S7 and S7 edge—both sport an interesting new feature called Always On Display, or simply AOD. When enabled, this feature keeps the clock, date, and other bits of information visible at all times—even when the screen is off.

The only knock on Samsung's last round of flagship devices is that TouchWiz is still alive and kicking. Aside from this overbearing skin that's been applied on top of Android, the Galaxy S6, S6 edge, Note 5, and this year's Galaxy S7 models are some of the best phones money can buy.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

Samsung has been on a tear with its flagship devices since the release of the Galaxy S6; The S6 edge, the Note 5, and this year's Galaxy S7 models have all been met with universal acclaim, and even the staunchest of critics have almost nothing negative to say. Almost.

Over the course of the past year, a lot of Android apps have added pull-to-refresh functionality. It's a very useful and intuitive gesture, because all you have to do to refresh the page you're viewing is scroll to the top of the screen, then slide your finger down one more time.

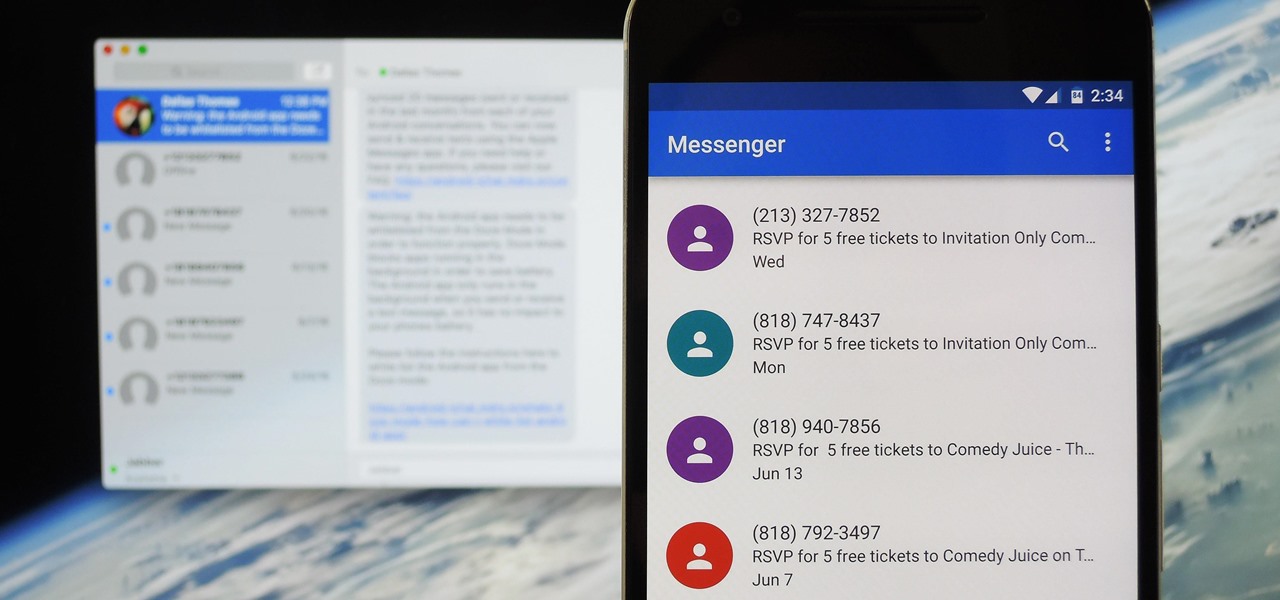
We've known for a while that Facebook had planned to reintegrate SMS and MMS into its Messenger app for Android. Well, it's finally live, and it's pretty great.

You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making it pitch black.

Smartphone displays are getting bigger every year, and Samsung devices are at the forefront of that trend. But, from a software standpoint, the icons, buttons, and other on-screen elements seem to stay at the same scale. So while phones are getting bigger, their interfaces are getting bigger as well.

When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

This gorgeous card is so easy to make and here I show you how, using some fabulous floral papers, however you could use any on hand, this card is a showstopper. Step 1: Items Used

Being able to customize the look and feel of your device is the main reason a lot of folks choose Android over iOS. And perhaps the single biggest way to visually overhaul your phone or tablet's UI is to apply an icon pack, which can liven up your home screen with bright colors or make things look a bit more classy with a sleek, minimalist style, for instance.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

You gotta love Android—not only can you replace your default home screen entirely, but there are tons of options that provide alternative methods for launching apps with ease. We've covered some of these options in the past, including an app called Bar Launcher that lets you launch apps from your notification tray—but that one's starting to look a little dated these days.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

This cardmaking tutorial shows how to make a truly elegant and quick card, that could be made for so many special occasions. The card looks amazing in the Ivory tones and has the look for being embossed, however it is a simple die-cut. Step 1: Items Used

For years, users have been clamoring for a "dark mode" theme in Android, but it has always seemed like Google is so committed to the white motif from their web services that such an option would never become a reality. But in a stunning turn of events, Google is finally embracing the idea with a night theme that will work in any app, and I'll cover all of the specifics below.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Android TV devices have had those beautiful Chromecast background images as their screensaver for quite a while now. Envious of this feature, Apple copied the idea for a similarly-styled screensaver in their newest Apple TV, but with one big twist—they used videos instead of still photos.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

Just about a year ago, Google launched an update to the Gmail app for Android that let you link accounts from other email services to Gmail, allowing you to read and respond to everything in one place.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

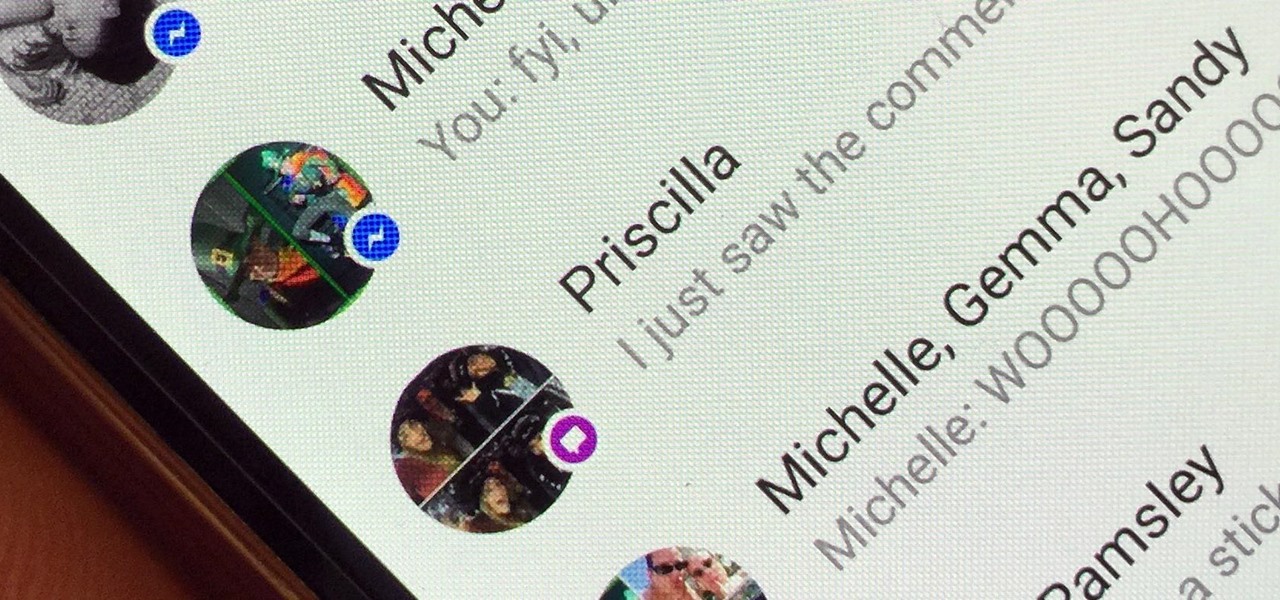
Earlier this week we showed you how to use multiple accounts on Instagram, and now Facebook is rolling out a similar feature for its Messenger app, as well as a few other features.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Unless you're in law enforcement, you won't usually have a flashlight on hand for those rare moments when you need to sift through the dark. However, it is very likely that you will have your phone on you, so you'll have fast access to a bright light with just a few easy taps.

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.