The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

After the first image leaked of the upcoming successor to the Razer Phone, many were taken aback by its design, specifically how familiar it was. Last year's Razer already stood out with its boxy design and large bezels, and many thought the successor would change this. It didn't. But what if the reason for the familiar form factor is a project they teased earlier in the year?

With the new iPhones coming out, many see the current mobile market as just another epic battle between Samsung and Apple. But let's not forget there are many other phones that run Android. And when you start to sift through the specs, one stands out as a competitive alternative to the iPhone XR, the LG G7 ThinQ.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

The world finally received its first official look at the iPhone XR, XS, and XS Max, Apple's 2018 suite of smartphones, on Wednesday, Sept. 12. If you're someone looking to get their hands on one, two, or three of these new iPhones as soon as possible, you'll need to know all of the important dates so you don't end up missing out to others ahead of the line.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

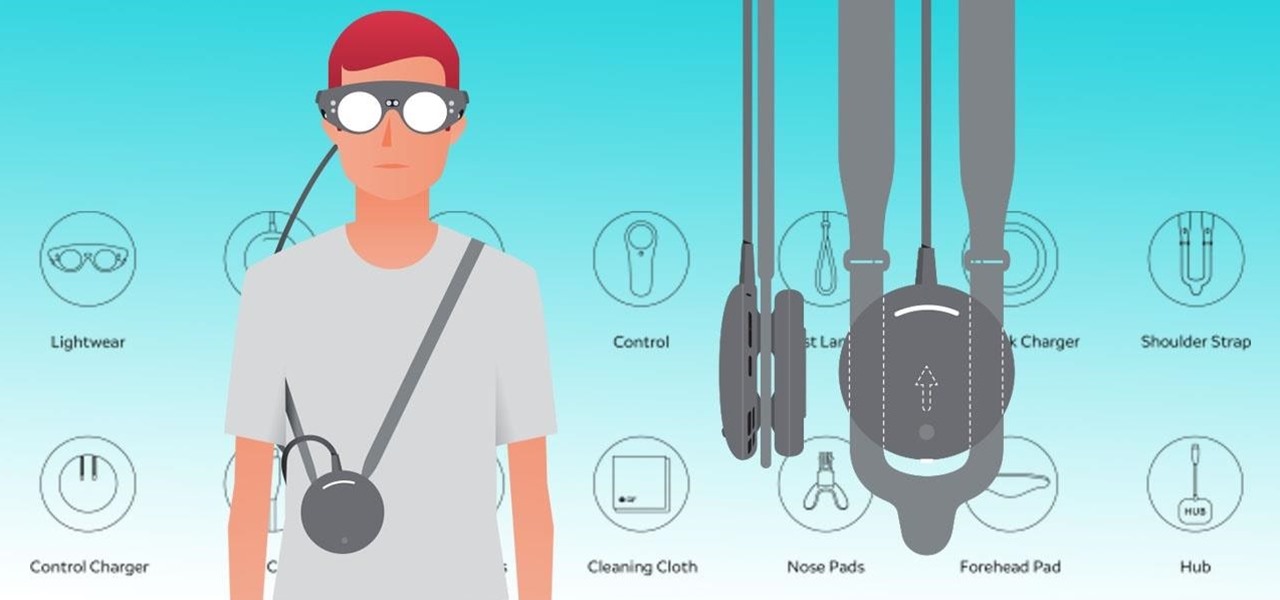
I've had a few days to live with the Magic Leap One, and it's time to finally weigh in with some thoughts as someone who has been tracking this company from the beginning, for almost five years now.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Every once in a while, we find ourselves in a predicament where we need an inexpensive smartphone. Whether we're finally upgrading from that feature phone we held onto too long or we dropped our current smartphone, sometimes we need a quick replacement to get back on track. That's where Android One comes in.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Many of us rely on our smartphones for all our media needs. Now more than ever, we're using Bluetooth connections to play audio over speakers, headphones, car sound systems — the list goes on. If you own a Samsung smartphone like the Galaxy S9, there are a number of Bluetooth tweaks and hidden tricks that can maximize your audio experience.

The share menu is a vital part of Android that lets you send data between between apps. Many of your favorite apps support the feature, including the new Direct Share sub-menu, which can lead to a messy share menu. However, there are a number of tools to clean up this clutter, three of which don't require root.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

Whether it's for your company, your professional image, or just your personal account, making a poll on Instagram is a great way to reach out to followers, friends, family, and other users to measure their thoughts and opinions about any given topic. Instagram for Android and iOS makes it fun and simple to do so, offering the same tools to professional and personal users alike.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

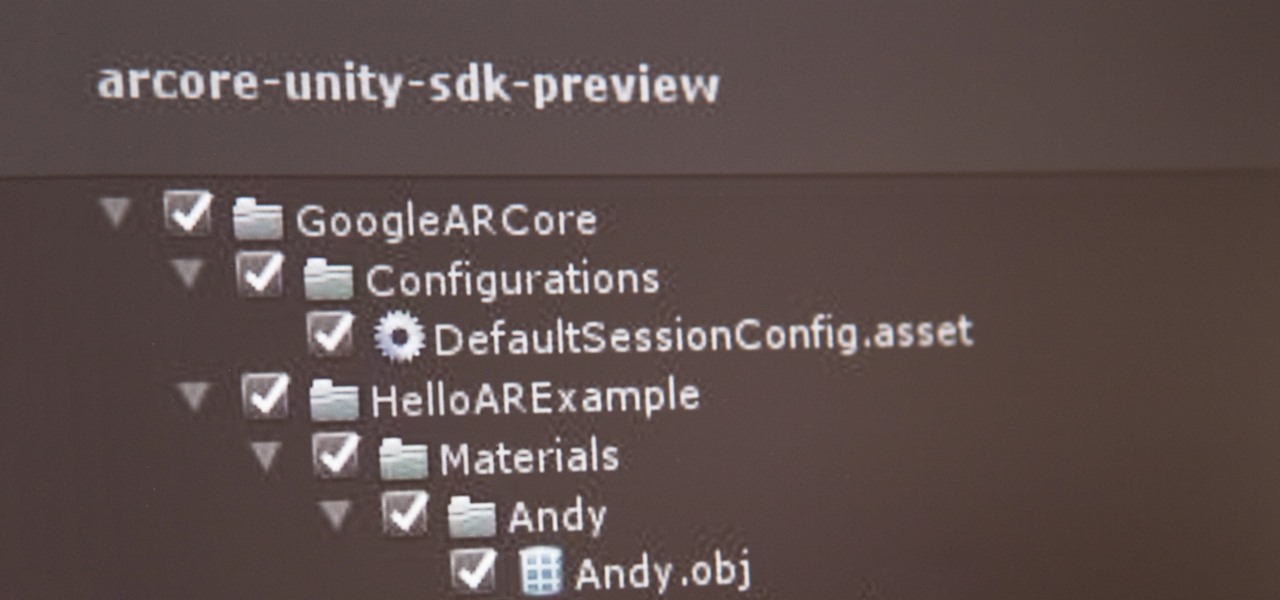
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

With much of the hype centered around its powerful cameras, it's easy to overlook the equally impressive audio capabilities of the Galaxy S9. After all, the S9 and S9+ are the first Samsung flagships to feature AKG-tuned stereo speakers, and that's not even mentioning all the software enhancements that help deliver rich, immersive sound in several different listening situations.

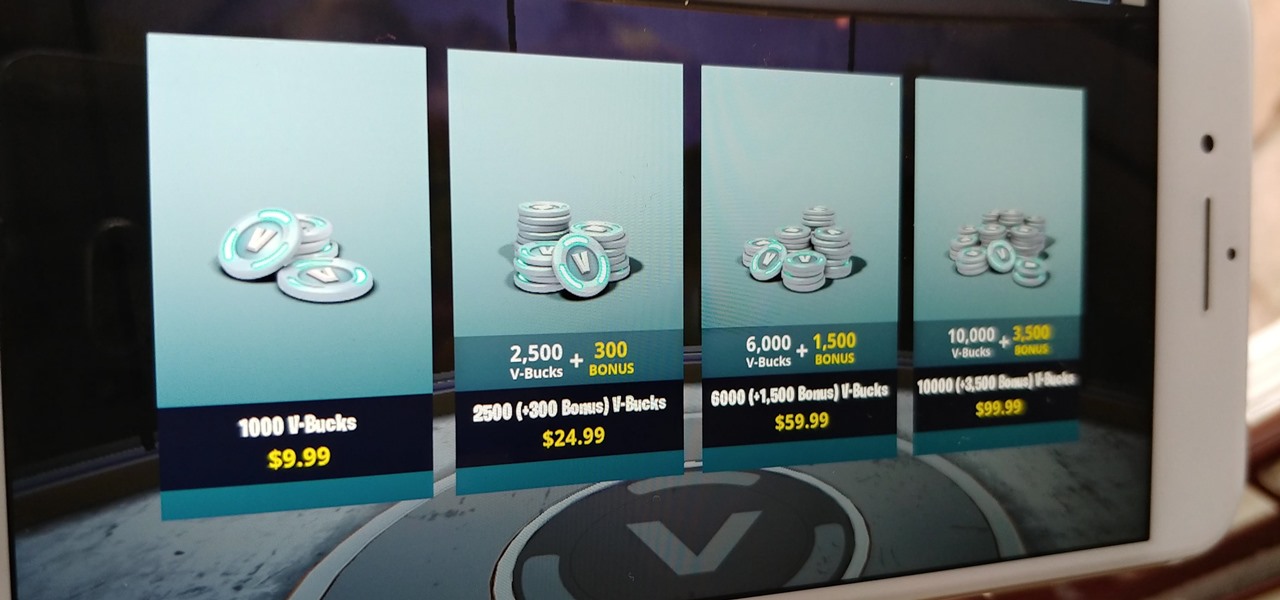
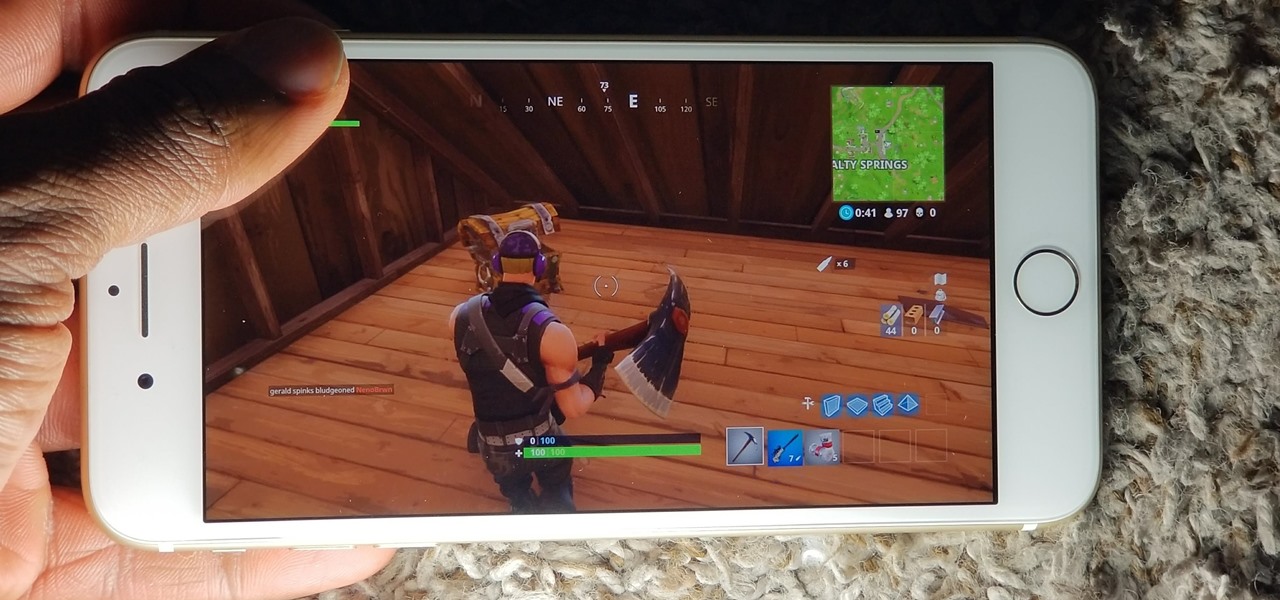
Thanks to its free-to-play strategy, many items in Fortnite Battle Royale require V-Bucks, the in-game currency. You can purchase V-Bucks with real-world money, but many would rather earn V-Bucks instead of getting nickeled and dimed by micro-transactions. While limited, there are a few ways to earn free V-Bucks in the game.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

If you tend to use the app switcher a lot to open recent apps, then all of the apps you accessed months ago are just sitting there cluttering things up. While force-closing all of the recent apps on your iPhone isn't really necessary, it's sometimes nice to wipe the slate clean and empty the app switcher completely to start fresh.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

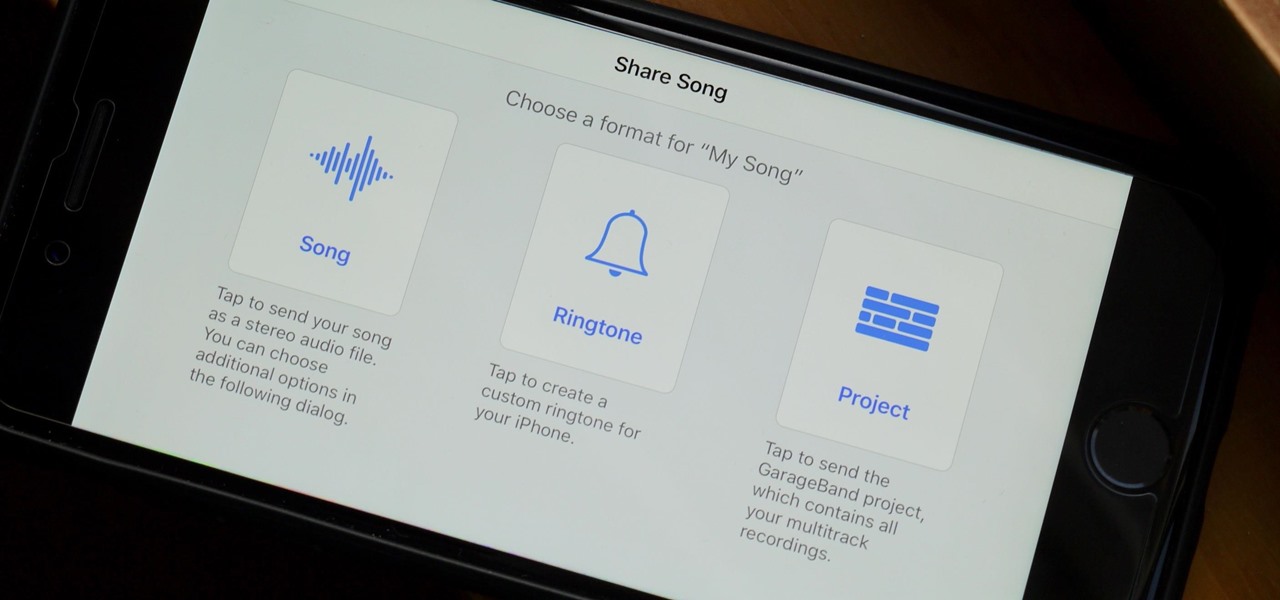
When you make an awesome song or beat that you're proud of in GarageBand for iOS, one way to show it off is to turn it into a ringtone or alert tone for your iPhone. That way, anytime you get a phone call or a notification, your musical creation will sound off, and everyone around you will hear it in all its glory. Plus, it's way cheaper to make your tones than to buy them off of iTunes.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Nintendo set the internet ablaze Wednesday night with two big announcements. First, Nintendo revealed that the Switch's paid online service will begin in September (boo), but it was the other report that really got fans excited — Mario Kart is coming to your iPhone.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.