You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Emoji are, without a doubt, an integral part of messaging on smartphones. Whether you're team iPhone or Android, chances are you send emoji daily. However, years after their introduction, emoji remain static in most cases, even with animated stickers and GIFs supported on almost every major chat app. That said, one of those chat apps, Telegram, makes things more lively.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

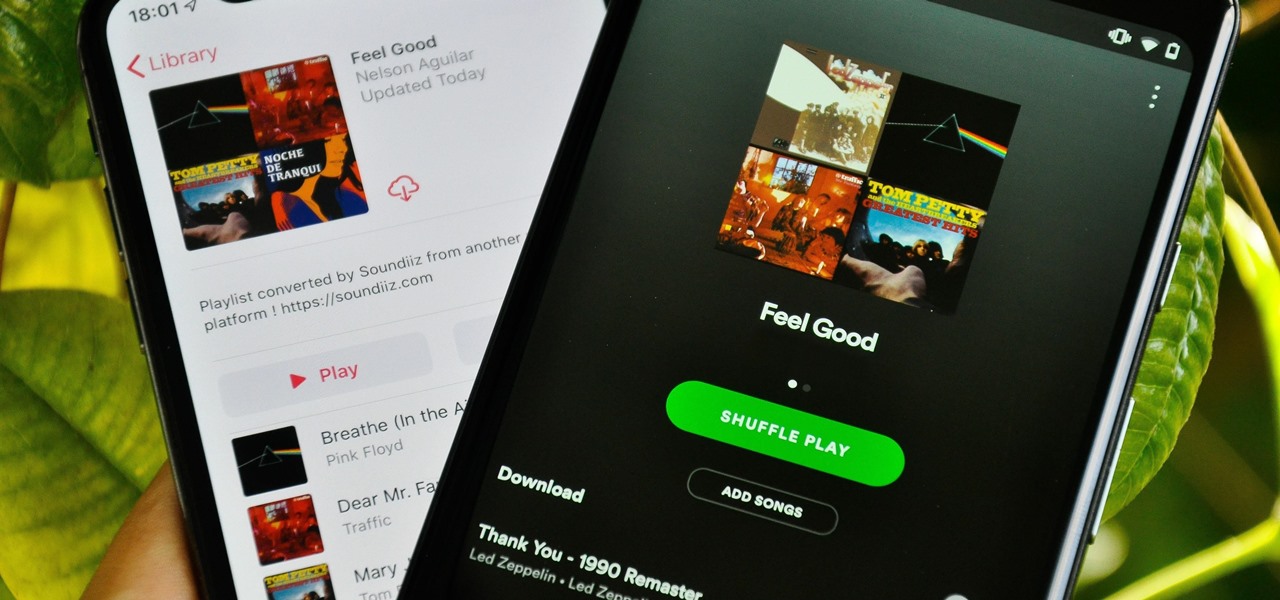
Music streaming services make it difficult to transfer your favorite songs and artists from one service to another and for a valid reason: they don't want you to leave. But when it comes to switching, playlists are a big concern, because who wants to do it all over again? Luckily, if you're moving from Spotify to Apple Music, you can use a third-party app to take playlists with you.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

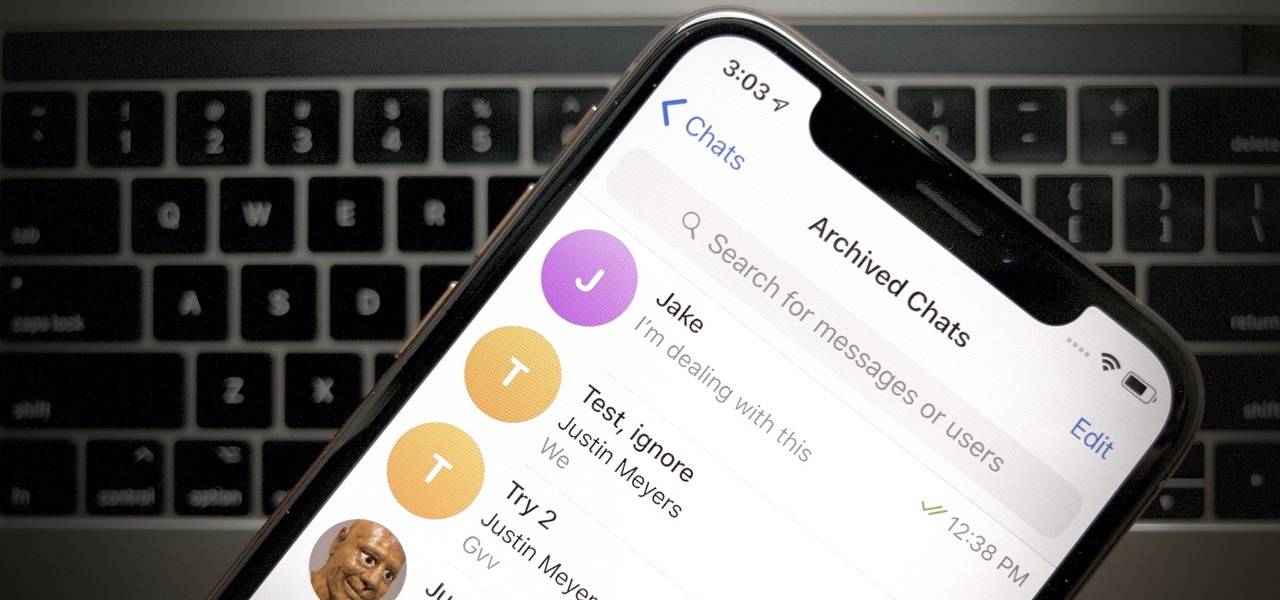
In Telegram — as with all instant-messaging apps — threads and conversations can pile up quickly. But you don't need to stare at all of your open chats on the main screen of the Android and iOS app. Instead, you can archive any conversation you like, keeping your main chats view relevant to your day-to-day communications without needing to delete any for good.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

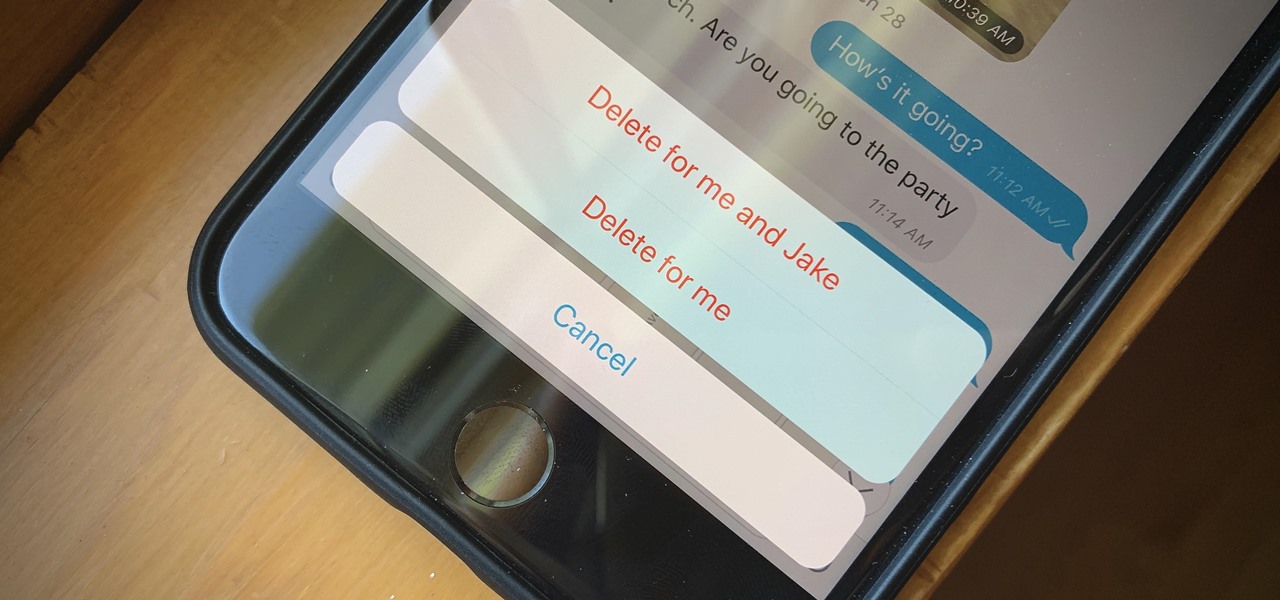
If you're looking to keep your conversations private, look no further than Telegram. Its cloud-based chats are secure and its optional end-to-end encrypted chats even more so, but you can't really prevent someone in the conversation from sharing your messages. However, you can lessen that chance by taking back your messages, deleting them for both you and the other end of the discussion.

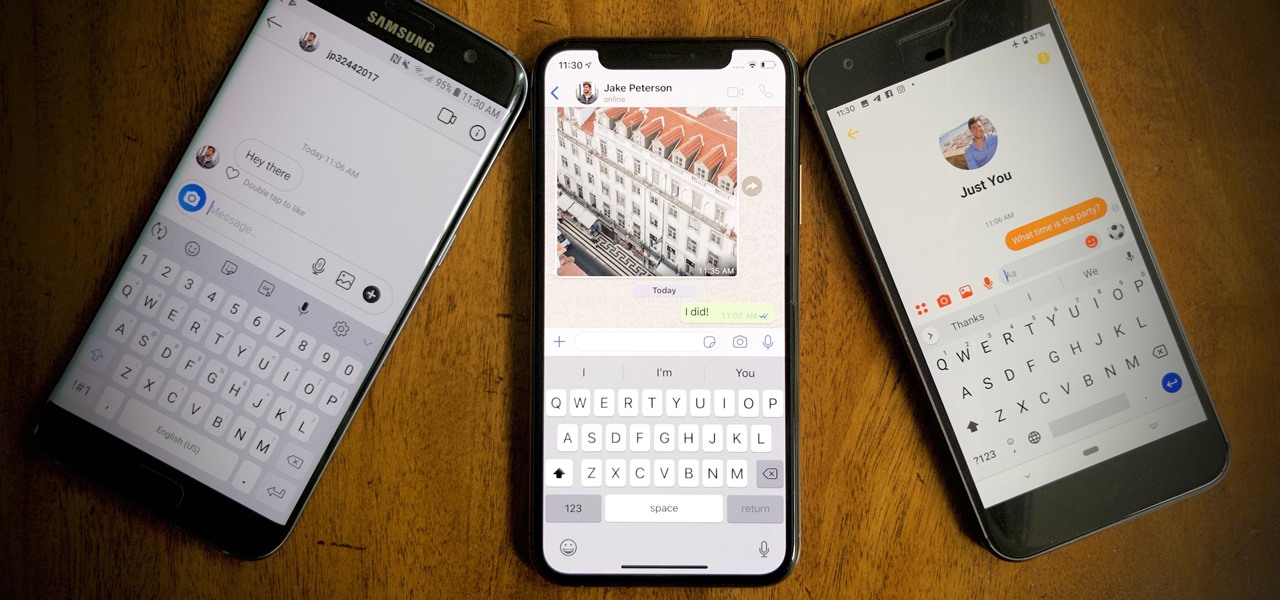
You're in constant communication with your friends and family. The only issue? Nobody uses the same app. Messenger, Instagram, WhatsApp — you have contacts spanning all three, and the resulting balancing-act to keep in touch can be overwhelming. That's why Facebook — who owns all three apps — is coming out with a way to call and message friends across all three platforms from one place.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasing design with impressive performance to boot.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

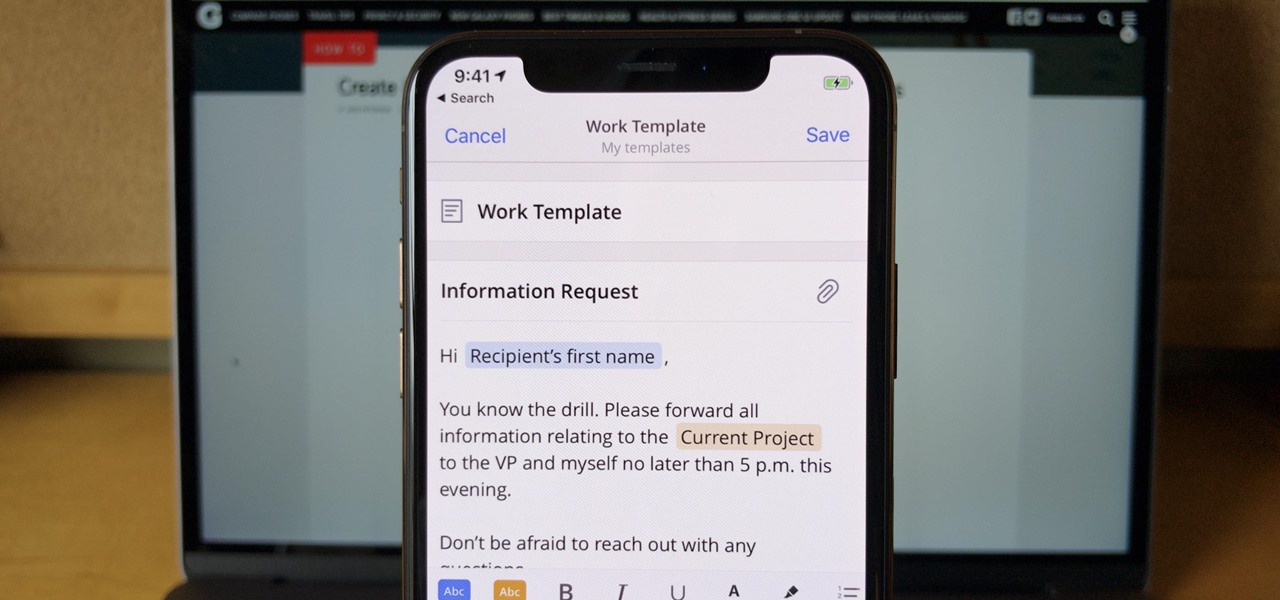
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, its new display is unmatched in the mobile space.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

With Apple releasing the iPhone XR, it appears Samsung is looking to challenge this "budget flagship" option head-on. They brought their usual two phone releases this year, but also threw in another three for a total of five phones, including the Samsung Galaxy S10e. And for many, this might be the option to look at.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

On the surface, Instagram is pretty intuitive, so you might think that you already know everything there is to know about using it on your iPhone or Android phone. But this photo and video-sharing app is constantly adding new features, some of which don't make the press releases. Even if you're an Instagram guru, chances are you've missed one of these hidden goodies.

When Facebook introduced Stories in 2017, many users despised the Snapchat-like feature on their main page. However, despite the outcry, Facebook doesn't plan to let you remove it. But you don't have to settle for this. With the help of some third-party apps, you no longer have to deal with Stories.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.