There are a total of 242 stars in Super Mario Galaxy 2 on the Nintendo Wii — 120 normal stars, 120 green stars and 2 bonus stars. If you've already found all of the stars in Worlds 1, 2, 3 & 4, now it's time for World 5!

Make your underwater dreams come true by turning yourself into a bona fide swimming mermaid. If mermaids did exist, you would be the perfect candidate to transform into the mythical creature. So check out this video tutorial form Little Orca to learn how to make your own mermaid tail costume.
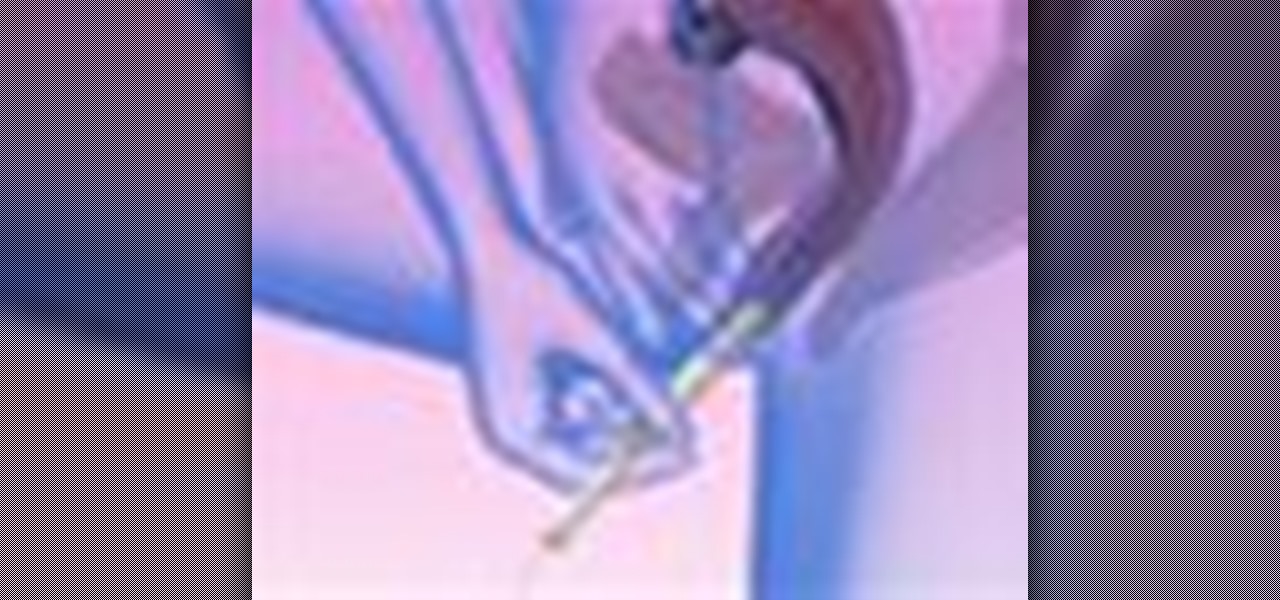
Inserting a tampon is a rite of passage for every teenage girl, so it's important to know how to insert a tampon the right way. It could seem tricky at first, but after trying several times, tampon insertion becomes as easy as putting on a glove. It just takes practice, & this video will show you the animated process. The key is to RELAX! Worrying about it may make you tense, making insertion even harder.

This is a video showing how to make a perfect latte at home. First the coffee is ground and then she pours some milk. The presenter says that 1/3 of the daily requirement of milk can be found in a latte. Once the coffee is ground it is brewed. She uses a lot of coffee so that it is richer. While the espresso is being made, the milk is steamed. The espresso should drip out like honey. The steamed milk is then poured over the coffee.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

This video shows you how to make a bridal veil for your doll. Take some 58 inch wide ivory tulle netting. Assorted floral decorations, scissors, thread and pins. You also need some floral tape, artificial leaves, wire and wire cutters, fancy ribbon, and some white feathers. First, make a floral arrangement with the flowers and leaves tied together with floral tape into a bunch. Wire some leaves and feathers to the outside of it. Cut 18 inches of tulle and leave it folded in half. Gather it at...

If you have thinning or short hair and are looking for a change, you may want to try a wig. There are many types of wigs today, different styles made up of different materials. Watch this video to find out information on buying a wig or hair piece so that you don't wind up looking like you have an animal on your head.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Creating a dress, or any other clothes for that matter, takes quite a bit of design, planning, and manufacturing to get it just right. Fashion designer Jim Reichert put on a HoloLens and saved himself a bunch of time designing a dress through the use of a life-sized holographic woman.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

How to do the sliced banana magic trick! Fool your friends and be the life of the party with this awesome magic trick! This video will show you how to cut a banana before you even peel it! All that you will need for this cool trick is a needle and a banana.

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

There are some pretty incredible camera techniques out there, but the biggest problem that amateur photographers run into is that they don't have the equipment to try them. You can still get some great shots, but there are some things that are really hard to do if you don't have the money to drop on expensive lenses and accessories.

If you ride your bike at night frequently, you've probably had at least one close call with a car, pedestrian, or some other moving obstacle because of reduced visibility. Not only is it dangerous to ride at night without lights, it's illegal in a lot of places. Make sure no one can miss you with these DIY handlebar lights from Becky Stern at Adafruit. What You'll Need

Watch this instructional knitting video to bond a vinyl hem with a knitting machine. Hang an elastic or ravel cord and push it against the bed. Fold the hem over the ravel cord. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to decrease the size of your knit piece. Use a single prong tool to unhook and tie off a single stitch on either side of the piece before completing each row to gradually decrease the width of the knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to weave a cast on. This is a cast on that many people find difficulty with. You may want to reference written instructions in addition to watching this knitting video.

This project requires very little sewing experience. If you can do a basic whip-stitch, cut fabric and use an iron, you can do this. This is a great gift idea and you can use up those old fabric scraps, trims and beads. The best thing about it, is that you can customize the box to any occasion. Watch this how to video tutorial and learn how to make a fabric gift box.

This flower arrangement tutorial shows you how to make a candle centerpiece using a pick machine. A pick machine attaches steel picks to the stems of your silk flowers. This makes arranging your flowers in floral foam much easier. Watch this how to video and you will be making this beautiful candle flower arrangement in no time.

System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

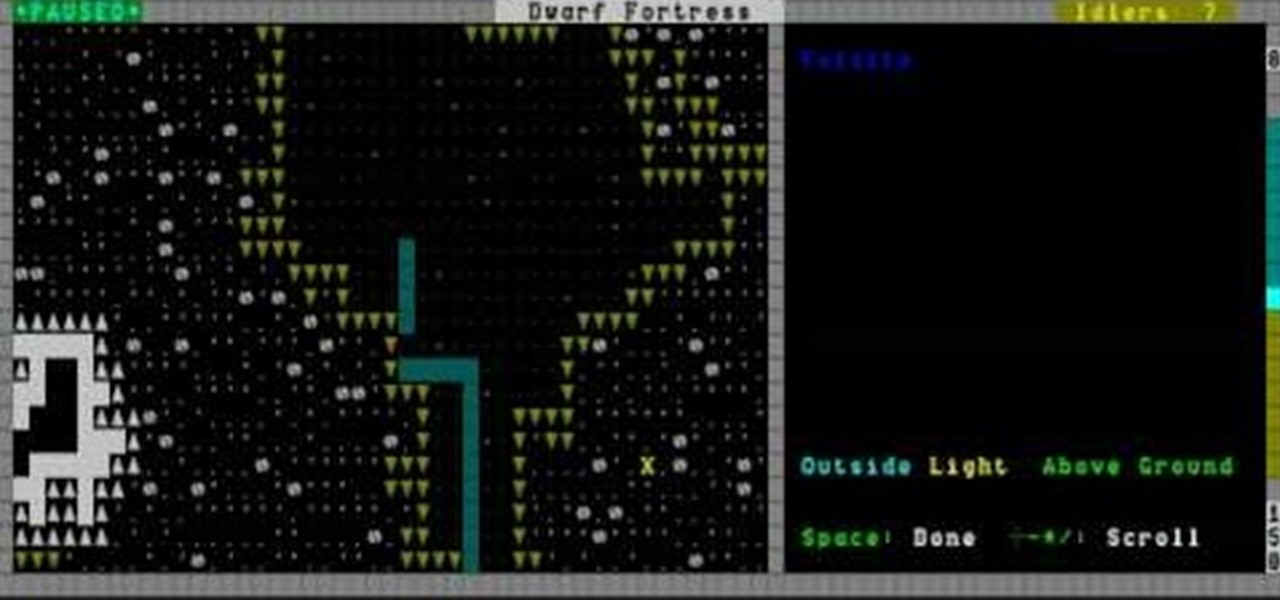
Late in the Dwarf Fortress game building machinery can allow you to pump water around the map and power mill stones to make more advanced food. This video will show you how to build and use machines safely, without destroying your fortress and the lives of your dwarves.

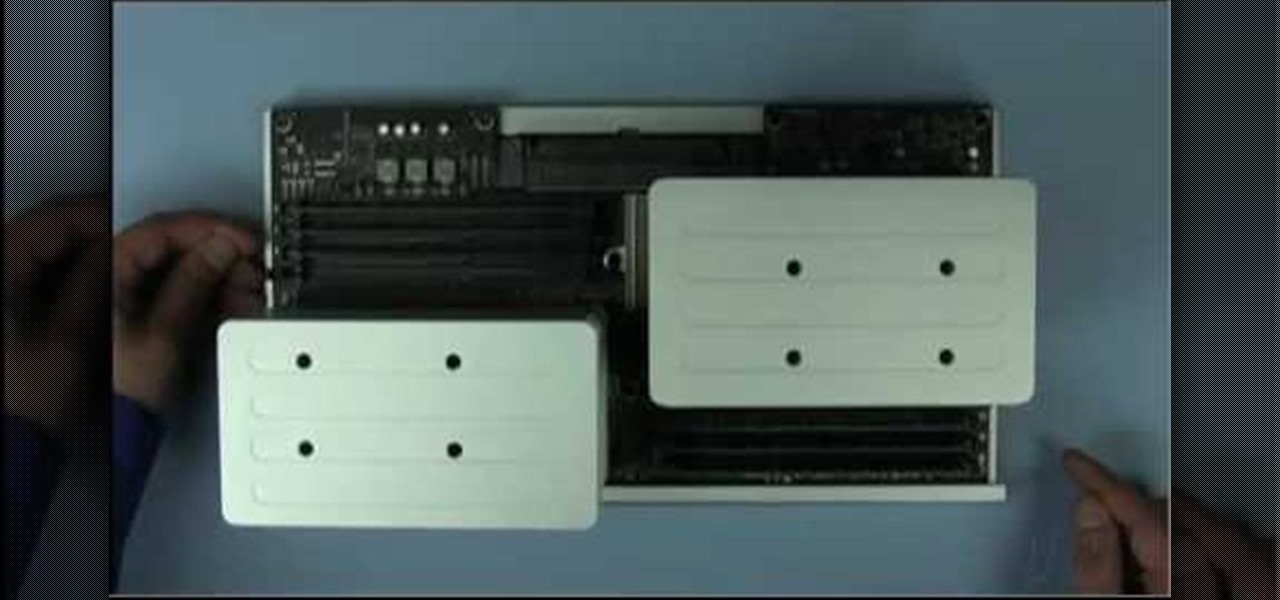
MacOSG demonstrates how to install memory in a 2009 Mac Pro. When performing this upgrade, be sure to take precautions for static by discharging static electricity before beginning. Shut down, unplug and place the Mac Pro on a static-free surface. To access the memory, you need to open the side access door by lifting the latch located on the rear of the Mac until it locks in the open position. You can then the door forward and then remove from the body. The memory is attached to the processor...

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

In this video Sarah Magid shows how to make dark chocolate cupcakes with espresso butter cream along with sugar flowers as follows:

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Watch this video tutorial from the Polish Guy to see how to polish a stainless steel roller using Autosol. In this polishing tip we polish a stainless steel roller using Autosol Metal Polish. The tutorial includes detailed work instructions and best practices.

These videos show you how to use baking strips to make a better cake. Use caution when using baking strips, and watch your oven carefully.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Watch this instructional knitting video to hang a knitted hem. Add weights the inside of a hem to keep your knitted piece straight. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

Here's a new way to look at making perfect mitered corners the first time, every time. This instructional quilting video demonstrates how to sew consistent mitered corners on your quilts in a few steps. Use a "Minute Miter" tool to hold the fabric in place. Learn why this seamstress says, "no snouts allowed."

Watch this instructional quilting video to sew a wide binding on your quilt. A 3" binding is recommended when you're learning to use these tools but after that you can create wider & narrower bindings. Here's info for wider bindings.

Watch this instructional quilting video to adjust the "Zip Bind Tool" by a small amount. The zip bind tool allows you to sew straight binding on your quilt without using a lot of measurements and pinning. Adjust the Zip Bind Tool 'a hair, a smidge, a scant, a skosh, a wee bit' for stitching in the ditch.