Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even donated some of their AI smarts to AOSP for all Android manufacturers to share. But it looks like Samsung isn't exactly on board.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

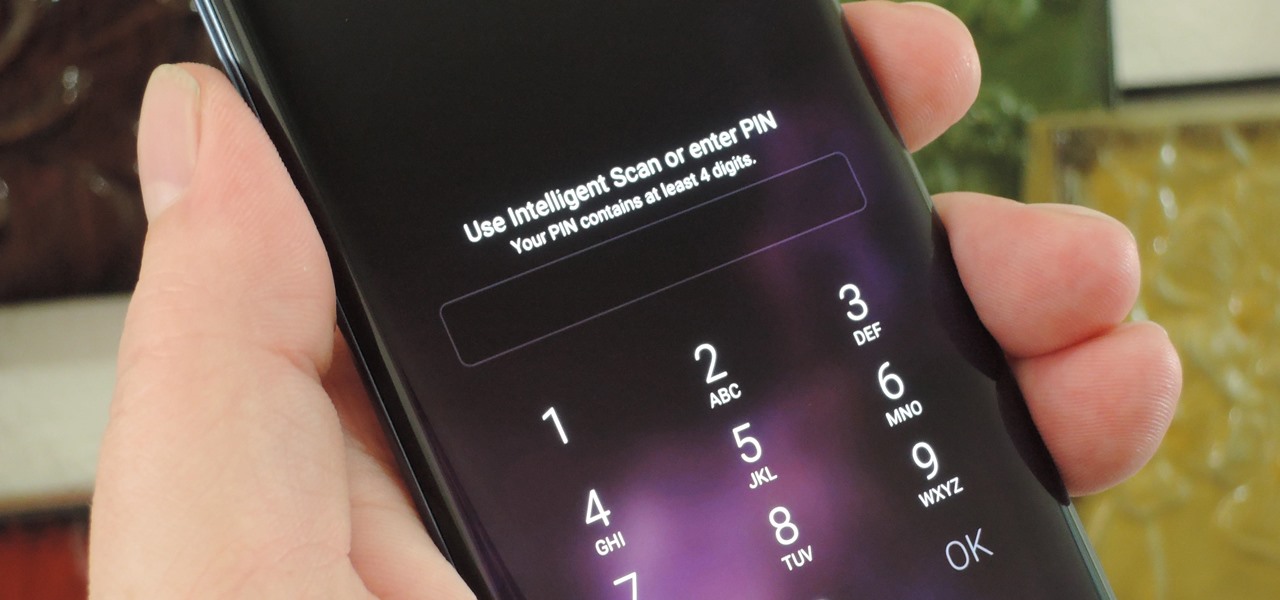
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

Google's new AI-powered camera, Google Clips, seems to be targeted at parents of young children in its current form, but the idea itself has unique potential. Just set it up somewhere, then you'll never miss a moment trying to capture the moment — you'll have a robot photographer taking care of that stuff for you.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Have an airbrush machine just for baking. Be certain that it is always clean. Cover the surface where you will be working as the color will fly. Cover around the cake and behind the cake. You can use newspaper, butcher paper or a disposable tablecloth. Pressure, angle and speed are very important when using an airbrush. It is best to practice. The more practice, the more comfortable you will become with the airbrush. Draw what you are going to put on the cake to use as a guide. Put just a bit...

Chocolate brownies aren't a well-known dessert in France— it's more of a United States favorite, but that doesn't mean it shouldn't be made by anybody with a carving for chocolate. Try making these fudge brownies. With the rich flavor and consistency of the nuts and chocolate combination in these fudge brownies, you'll fall in love with them. Watch the recipe for baking chocolate fudge brownies from Chef Hubert Keller.

Everybody's favorite food is pizza. But not everybody knows how to actually make a pizza, which is practically a sin. And this "margherita" style pizza is a great one to learn, full of Italian simplicity— red tomato sauce, mozzarella cheese, and green basil— all the colors of the Italian flag. Check out the recipe for this delicious margherita pizza.

Chef Hubert Keller is known for his ingenuity in cooking, like when Frank Sinatra came into his restaurant and ordered something not on the menu — a pizza. Quickly, he had to come up with a great pizza recipe and this is what's come of it. Check out the recipe for this mouthwatering pizza from Chef Hubert Keller. You learn the whole process, from dough to sauce to baking.