In the Windows 8 Enterprise edition, you can use the Windows to Go feature to travel with Windows 8 OS, personal files, documents, settings and many more. All you need is an external hard drive or USB drive of 32 GB space or more and USB 3.0 support or more for fast Windows 8 booting. We need the storage media of above specification to create bootable USB to access the data anytime by plugging the media into different PC running latest version of Windows 8 PRO or Windows 7.

When you're capturing video with a DSLR, not having some type of stabilization system can lead to some pretty awful and shaky scenes. Camera instability is not only painful to watch, but breaks the fourth wall. Once that the invisible barrier between filmmaker and audience is apparent, it may break down that magical relationship between the two.

A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Who needs to go to bartending school when you've got the Inebriator to mix your favorite drinks for you? Want a cosmopolitan? No problem. Press a button. Want a tequila sunrise? Sure thing. Press a button. As long as you've got a good supply of liquor and mixers, the Inebriator is at your command. So, what exactly is this Inebriator thing? Well, it's a robotic bartender that can automatically pour 15 different pre-programmed cocktails. With 9 different liquors and 7 mixers on board, it's got ...

Believe it or not, it's possible to make your very own lava—if you have a furnace capable of heating up to 1,200 degrees Celsius, that is. Bob Wysocki and Jeff Karson started the Syracuse University Lava Project to study basaltic lava and give students a hands-on way (hypothetically, of course) to learn about it. Oh, and they also want to use it for art projects. Sign me up for that class! It all starts with 1.1 billion-year-old basalt gravel, which apparently anyone can buy. They put the gra...

Have a PC but hate Windows? Maybe you've just heard a ton about the new Mountain Lion OS X and want to see if it lives up to expectations. Either way, you can install Mountain Lion on your Intel-based PC in a few easy steps. All you need is a copy of the OS X and an 8 GB USB flash drive. The first step is getting Mountain Lion onto the flash drive. You'll need to format the drive with one partition as Mac OS Extended, Journaled and select Master Boot Record under options so that it's able to ...

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

Want an electric car without the price tag? You could always build your own, or maybe just hack your old gas guzzler into an eco-friendly electric machine... This weekend at Defcon, security consultant David Brown showed off his "Voltswagon" project, a 1974 Beetle named Shocky that he converted to electric for only $6,000. He removed the old combustion engine, radiator, and a few other unneeded parts to make it lighter. Then he loaded it with batteries front and back, ten Interstate DC-29, 12...

Remember those Choose Your Own Adventure novels? If your school was anything like mine, they were so popular you were lucky to find one to check out at the library. But there's no worries now, thanks to this handy HTML5 app, which makes it easy to write and share your own 'choose your own adventure' novels. inklewriter is a free tool designed to make writing interactive stories simple. Basically, you start typing and inklewriter helps you organize your story, making it easy to add, remove and...

Yesterday, Microsoft released the customer preview of its newest version of Office, the first version optimized for both touchscreens and desktop systems. The entire suite got a much-needed facelift and a few new cool features. Here are some of the most notable changes.

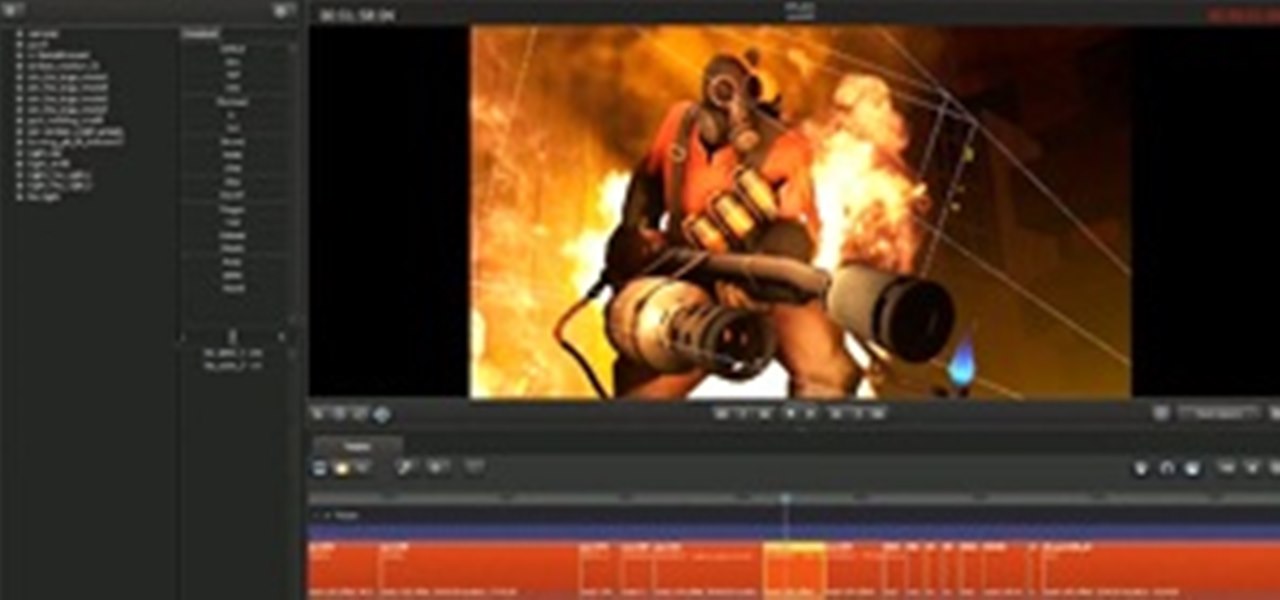
If you're familiar with games like Half-Life 2, Left 4 Dead, Portal, and Team Fortress 2, then you've probably seen some of the cool animated movies that Valve has made for them using their Source Filmmaker moviemaking software. It's a tool built to make animated films inside their Source game engine. It's even been licensed to make the upcoming animated film Deep.

In this tutorial, we learn how to make your own maternity jeans. First, you will take you favorite jeans, then cut the panel all around, including where the button goes. After this, use any type of shirt and sew it onto the jeans. This will go onto your stomach and under your breasts while you are pregnant. You won't be able to tell that you made these, and they will look great. Remember you can use any type of shirt you want to make the panel, just make sure you don't want to wear it again. ...

Do you have a fashion emergency? Are you out and about and your zipper just gave in? If you have a skirt that is falling apart as you wear it, or are camping and need to fix a sleeping bag at the last minute, check out this tutorial. In it, you will learn how to repair zippers with no tools or supplies. This is also useful if you do not know how to sew but want to avoid spending money on a tailor. So, don't sacrifice your favorite garments to broken zippers anymore, with this video learn how ...

Watch this video tutorial from the Polish Guy to see how to polish church appointments, like a chalice and candle. In this demonstration we use a Church Polish & Cleaning Kit that includes Simichrome and Flitz to polish a brass chalice and candle stick. The tutorial includes detailed work instructions and best practices.

In conclusion to our back to school week, Rob and Corinne are showing you how to take an old mens suit jacket and magically transform it into a backpack. So now it's time to raid uncle Ned's closet for an old sports coat, break out the scissors and start sewing. Be ready to go back to school with your own hand made backpack.

This video tutorial shows how to dry emboss with a crop-a-dile embossing machine. Embossing is one way of giving a unique and personalized touch to scrapbooking craft projects.

This video tutorial shows how to color the background of embossed paper with stamp ink. Learn how to multi-task with an embossing machine.

With all those cables coming from your computer, printer and fax machine there is hardly any room to do your work. This how to video demonstrates how to install a cable tidy device to keep all those cords nicely organized.

Learn how to save money by making your own Nepresso coffee maker capsules. Hack your coffee machine with this video.

Adam Gussow discusses the "machine language" of the blues harmonica and deconstructs a rhythm by Sonny Terry.

Advanced welding machine normally used for jewelery repair. Short clip showing how microscopic TIG welding repairs eyeglass frames by fusing metal surfaces directly to each other. High definition footage shot with a mixture of HV10 and HV20 cameras.

Dishwashers are amazing at cutting down kitchen clean-up time and providing dishes, cookware, and cutlery that are spotless and free of germs. Although the machine does do most of the work for you, using it properly will ensure that you get the best results. This video is going to show you how to properly load a dishwasher.

Having the right air quality can turn a room into an atmosphere. With a humidifier, you can see your skin dewy and your sinuses clear. Proper temperature control will keep you comfortable and content, and the right air purifier will give you clean air and peace of mind. If you're in the market for a humidifier, an air conditioner, a heater, or an air purifier but just need to find the perfect one to match your needs and your budget, then check out some of these great deals.

You won't have to ask Santa for holiday-themed augmented reality experiences, because practically any social and shopping app that offers AR effects has them available now.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on the design.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.