If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

See how fast and precisely you can transfer glass onto the mandrel using our electric mandrel spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to build transfer glass from the cane using a lampwork torch and an ele...

This video shows the features of the Deluxe electric mandrel spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to use all of the features of an electric mandrel spinner.

See how you can quickly, easily, and consistently you can make uniform lampwork spacers using the Electric Mandrel Spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to make glass spacer beads using a lampwork torch an...

This video animation tutorial demonstrates a technique for creating a fabric-like effect out of clay for stop motion figures, or armatures. Instead of smooth clay, try to give a more authentic finish to clay that will be used to create clothing. This technique will also create patterned fabrics. You'll need to chop the clay up first in a food processor, and then put it through a pasta machine. Watch this instructional video and learn how to make clay look like fabric for claymation armature c...

In this video clip series, our expert will demonstrate the ways in which you prepare a welding machine, manage voltage and energy levels as well as techniques for the different modes of operation and equipment. Learn how to use the weld supplies, tig, wig and arc welds and more. Techniques such as the “Push and Pull” are explained and demonstrated, as well as basic information such as setting up the welding machine and an introduction to the gases used for welding are included.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

It feels like every few months, some new feature is discovered in the Pixel's Camera app. By taking advantage of machine learning and the high-quality camera, Google continues to add hidden functions that improve your life even if they're a little niche.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

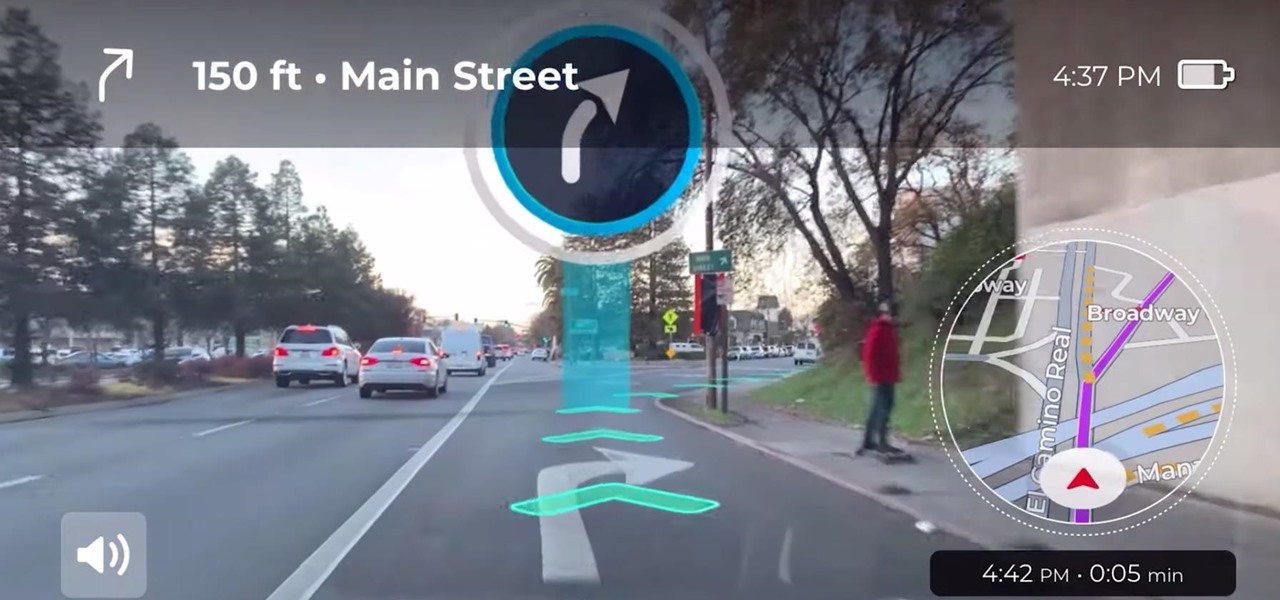
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.

When Google introduced the Call Screen feature with the Pixel 3, I had never been more excited to get a Pixel device. This AI feature provided real protection against rising spam and robocalls, which billions of people deal with each year. After a recent update to the feature, you can reduce robocalls and other spam calls to nearly zero.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

Roughly six months after emerging from stealth, AR cloud company 6D.ai is now ready for public consumption, and it has a big name partner to help it kick off its platform.

So you've been using iOS 13 for a little while and noticed your iPhone is pretty slow to charge. Using the 5-watt power adapter out of the box, in the time it used to take your iPhone to charge its battery to 100 percent, your iPhone is stuck at 80% or below instead. That's because Apple introduced a new feature in iOS 13 that slows down charging — but for a good reason.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

Because of its ability to place digital content into the real world, augmented reality lends itself well to artists and creatives.

After applying augmented reality as a solution for the sale and marketing of sneakers, Nike is taking the next step in its adoption of AR to improve the customer experience.

After announcing at Google I/O 2019 that augmented reality content would come to Search, Google revealed how it would make that happen with the latest round of updates to ARCore.

The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this means is that if you can get the Pixel's camera software, you can replicate the Pixel camera experience on other phones.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

We've seen a variety of AR experiences related to athletic footwear over the years, but Puma is betting sneakerheads will buy into a version of interactive design where sneakers are the augmented reality experience

The long guarded veil of mystery surrounding Magic Leap for years was finally lifted last year when the company revealed its Magic Leap One device.

While Google isn't ready to commit to a wide release of the AR walking navigation mode for Google Maps, the company has begun testing the feature with members of its Local Guides crowdsourcing community.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

Move over, cosmetics companies. The athletic footwear industry wants to be able to give their customers the opportunity to try on products in augmented reality as well.