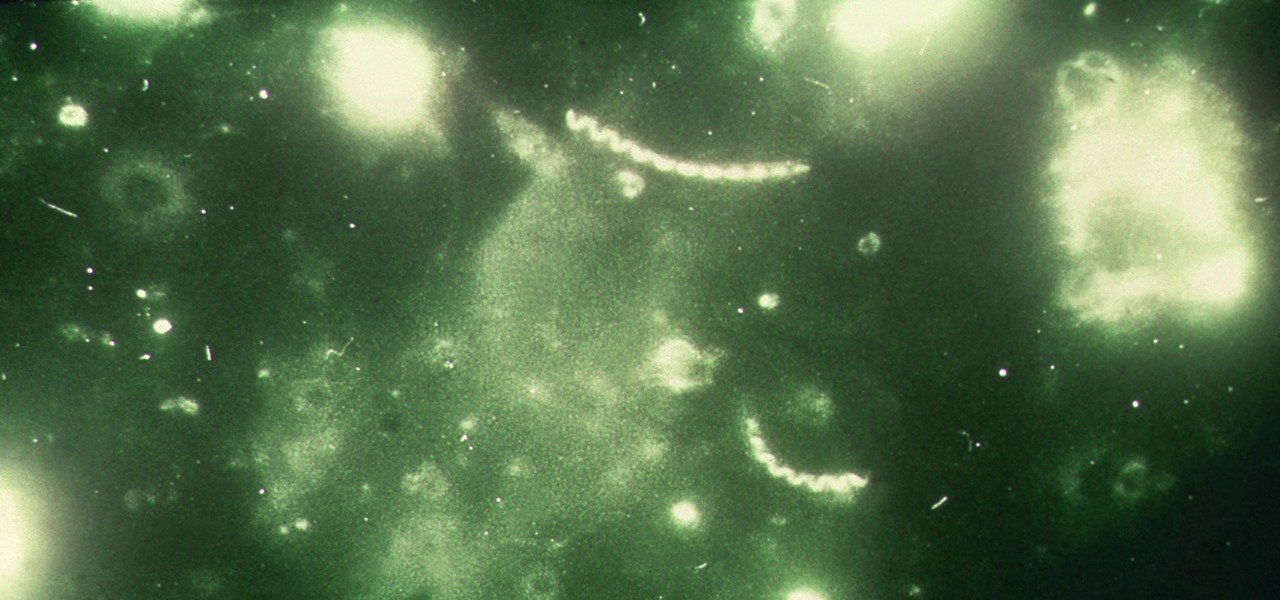
Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

With summer just ahead, you, or your children, may be looking forward to some pool time or the water park. When planning water-based fun this year, keep a heads-up for microbes.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

An advance in the race to stop birth defects caused by Zika-infected mothers has been made by a team of researchers from Rensselaer Polytechnic Institute in Troy, New York. They have identified the process Zika uses to gain entry into the placenta, and published their findings in the journal Biochemistry.

Phase 2 of a Zika vaccine trial began in the United States this week, along with Central and South America.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.

I'm starting to wonder if the people at Boston Dynamics have ever watched a Terminator movie. Not just because the robotics company with the oxymoronic name develops machines that are able to move around environments with animal- and human-like agility, but because the people testing them seem to take such joy in openly antagonizing their creations. It's one thing to tempt fate by creating superhuman robots that could potentially end mankind. You've reached a whole new level of hubris when yo...

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

There are so many cutesy pink, red, and heart-shaped desserts and drinks put out on Valentine's Day, but none of those really get you into a low-light mood. Instead, turn up the heat with one of these aphrodisiac cocktails for grown-ups.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Halloween may be finished, but the augmented reality chills are not over yet for some people. Arachnophobes are bravely facing their fears by cozying up to augmented reality spiders for a university study.

Whether you like to go swimming or jump in a hot shower with your Apple Watch on, the chance is pretty high that you'll get water inside its speaker. If you're a big runner, even sweat can get inside there. While there is no way to prevent water from getting inside your Apple Watch's speaker, there is an easy way to get it out so that your muffled speaker sounds brand new again.

General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

Apple seems to want the public to perceive it as an environmentally-conscious entity, as evidenced by the company's recently published Environmental Responsibility Report. But as it turns out, they may be hindering recyclers from salvaging old iPhones and Macs by ordering the devices to be shredded instead.

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

Like the buttons on your computer's mouse and keyboard, the Home key on your Samsung Galaxy S4 serves a vital function in navigating through your device. It can get pressed dozens of times a day, going through hours of use and abuse.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

The presence of certain bacteria can indicate whether the vaginal tract is healthy or not. It could also impact the likelihood of acquiring certain sexually transmitted diseases, like HIV, a new study suggests.

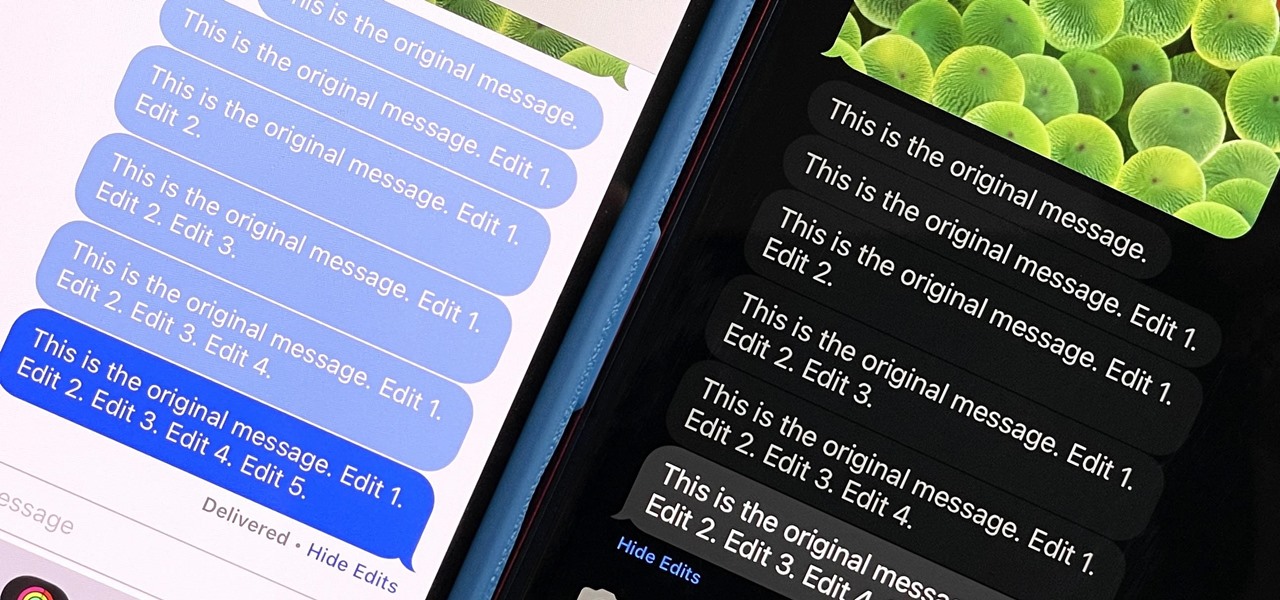
Apple's controversial iMessage-editing feature in iOS 16, iPadOS 16, and macOS 13 Ventura is now less likely to be abused by malicious users.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

It seems like all tech companies want to know where we are. Even Apple and Google have been caught abusing their location access on iOS and Android. Luckily, there are apps that can trick your phone into thinking it's somewhere it's not.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.