An MSR sweetwater micron pre-filter will purify water to drinking quality. It's a handy water filter to take along on camping trips or outdoor activities. Watch this video survival training tutorial and learn how to replace an MSR Sweetwater 5 micron pre-filter.

Homemade candy is a great activity to do with the family. This how to video demonstrates who to make English toffee. This supper sweet and buttery toffee recipe is sure to impress anyone who has a bite.

This how to video will give you ideas on how to make a sandwich that looks like a sailboat. Preparing this sailboat sandwich is a fun activity to do with kids. Watch and learn how it done.

Dogs have been bred to be very active, and are most likely not getting enough physical activity. A lot of bad behavior stems from a dog's boredom or restlessness. Watch this video pet training tutorial and learn how to give a dog enough exercise.
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

A quick demonstration of how to tie a figure eight knot. This is multi-purpose knot that can be used in climbing or other wilderness activities.

For whatever reason, you may want or need to remove multiple posts from your Instagram grid. If you only have a couple to hide from the public, archiving or deleting posts one by one is fine, but there's a much faster way when you have tens or even hundreds of Instagram posts to purge from your account.

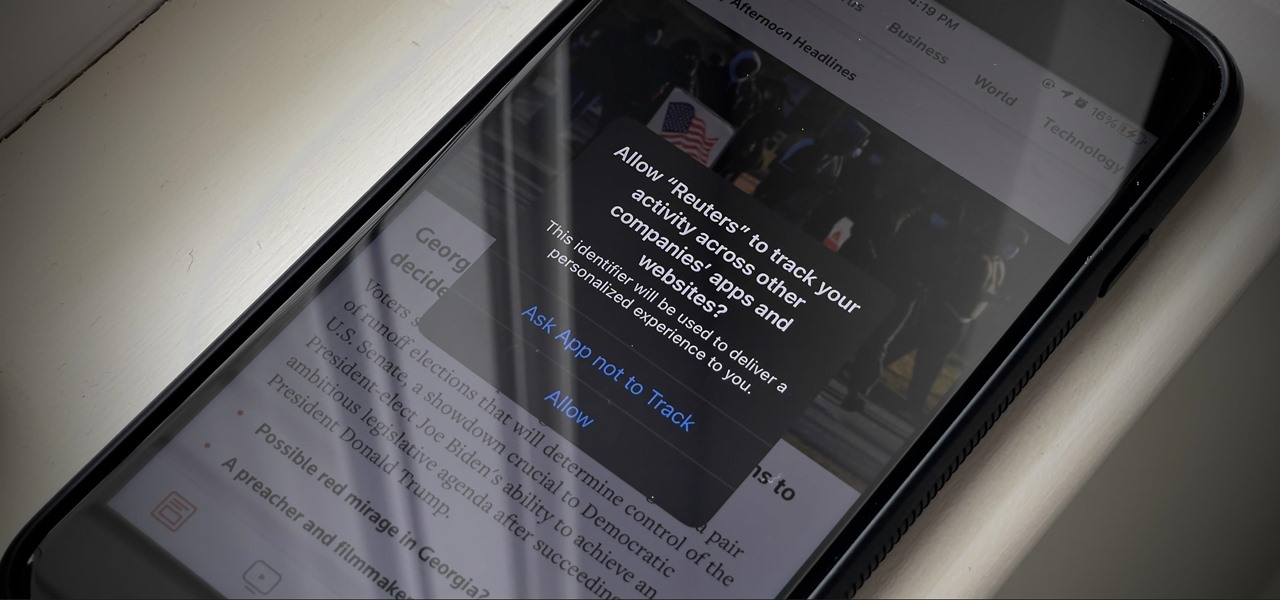
If you're like me, you're not too keen on being tracked. So when an app asks you if it can track your iPhone activity across other programs and websites for ads or data brokers, the answer is pretty much always "no." If you're tired of choosing "Ask App Not to Track" over and over again, there is a way to stop apps from even being able to ask in the first place.

With Shortcuts, Apple has designed a way to create your own tools and automations right on your iPhone. And to top it off, your creations can be accessed in a variety of ways, including Siri phrases, widgets, and the Shortcuts app itself. Perhaps even more useful is adding them as custom actions to your Share Sheet and making them available to you system-wide.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home — in just seven minutes a day? All you need is a chair, a wall, and a 7-minute workout app.

New year, new me. You finally committed to working on the best physical you by going to the gym multiple days a week. Except about an hour in, you start getting really tired of it all. Before you run to the exit, pick up your phone.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

In a world of seemingly endless streaming services, podcasts continue to offer free, unlimited entertainment for all. When you find a podcast that's just too good to keep to yourself, sharing it with family and friends is inevitable, but how you share may determine whether or not they listen to it or not. Links alone aren't enough. Audio and video clips are how you get them sucked in.

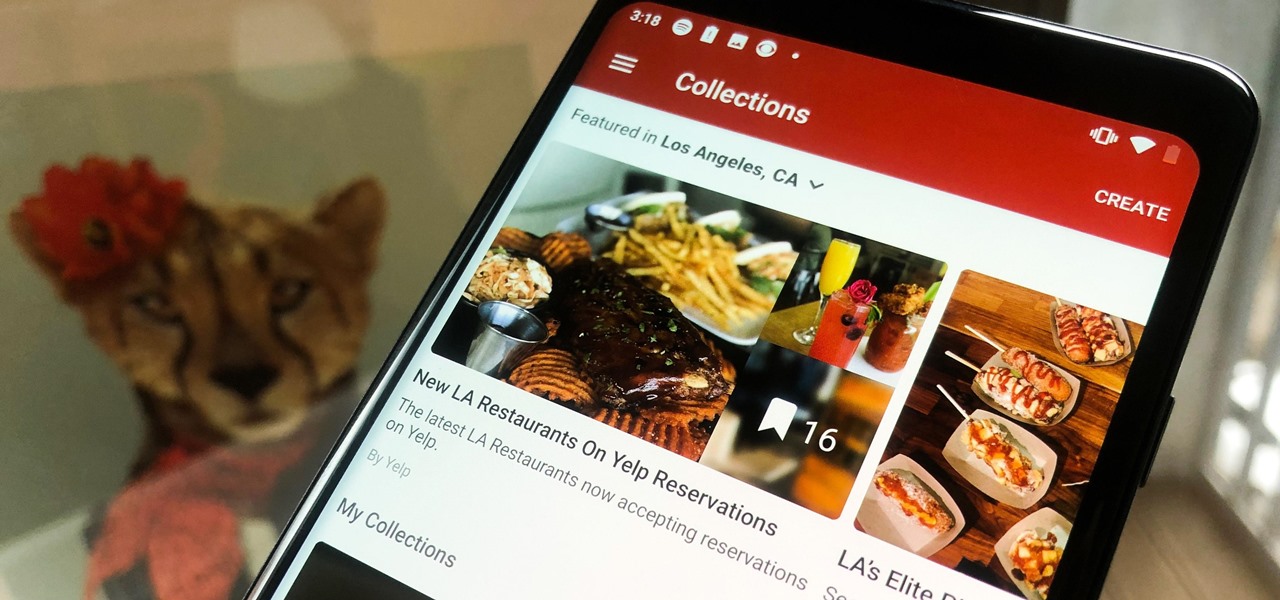
In the past, if you stumbled upon a Yelp listing you liked, you could bookmark it and check it out later on your profile. You can still take advantage of this feature in the mobile apps, but it's more refined now than it ever was thanks to Collections, a feature Yelp first added back in May 2018. You get more power over organizing, accessing, sharing, and discovering favorite businesses.

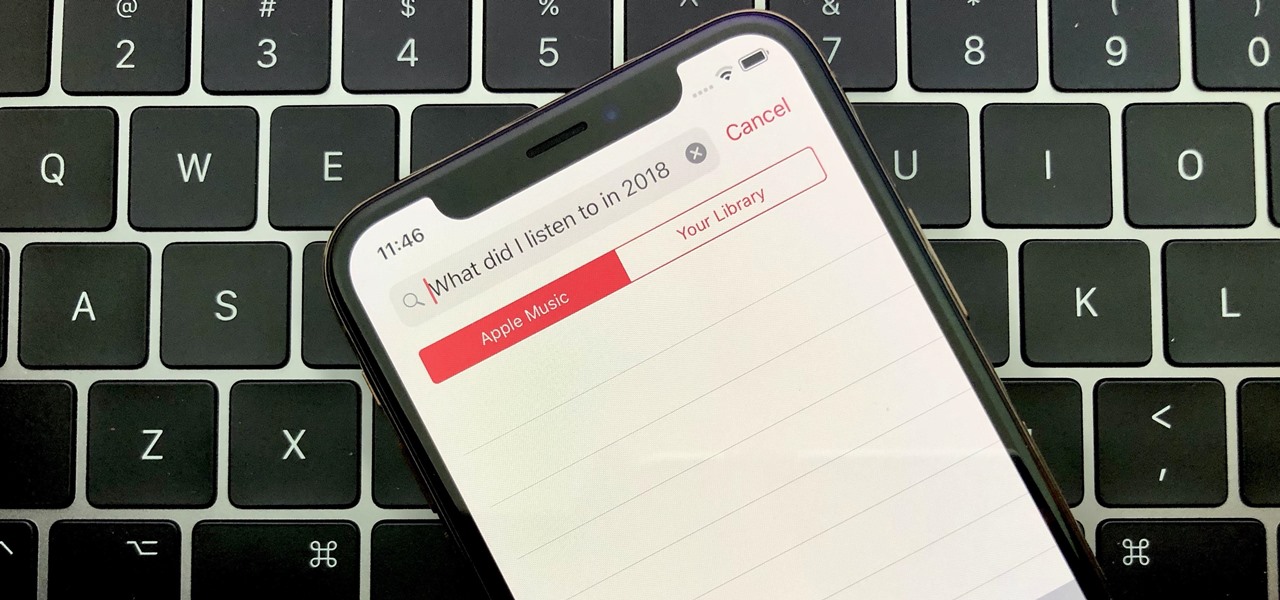
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

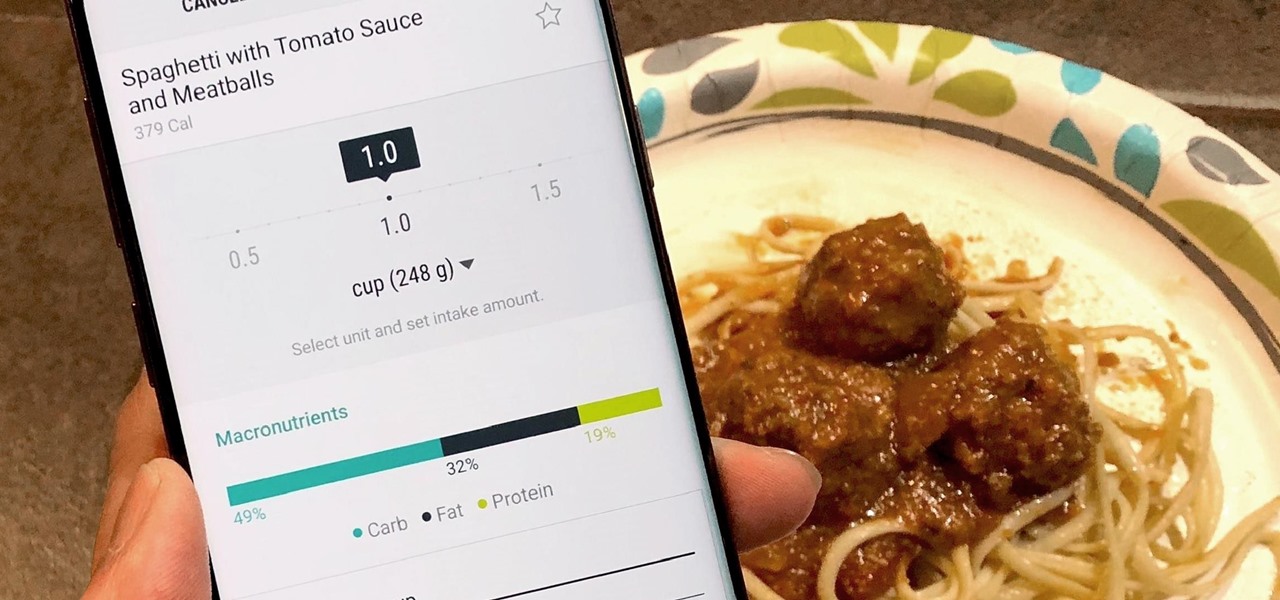
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

Niantic's most successful app, Pokémon GO, has become the first app to integrate the company's Real World Platform, the developer's AR cloud technology that enables multiplayer AR, persistent content, and occlusion with physical objects.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

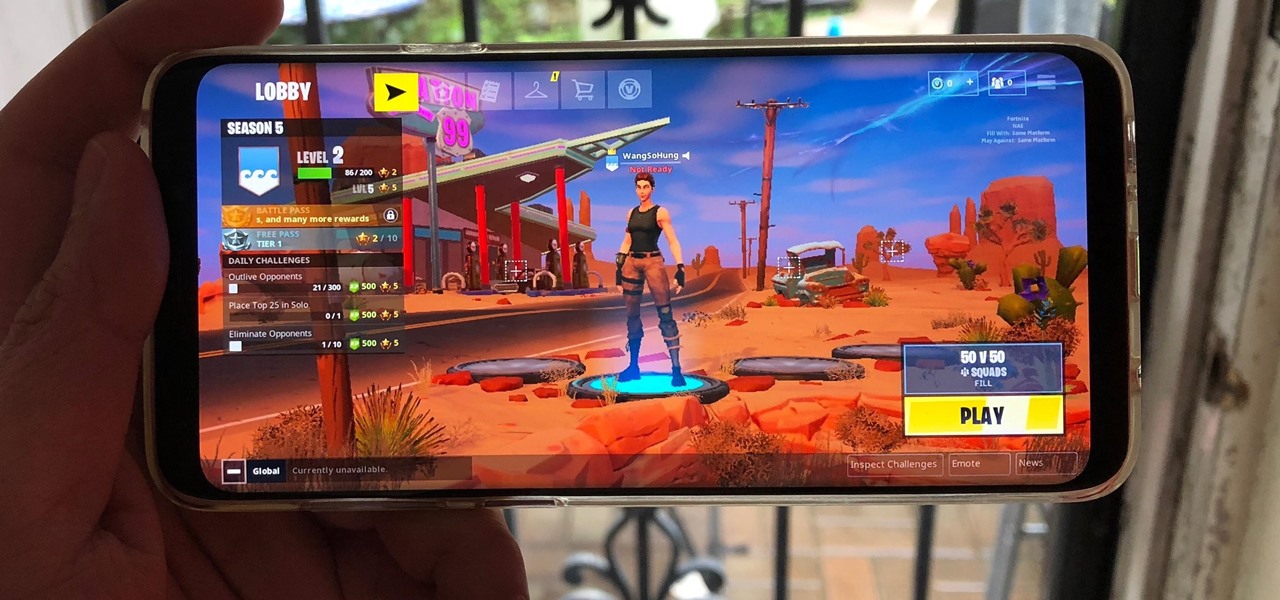
Fortnite's long awaited arrival on Android has ramped up excitement among gamers who are installing the beta version in astounding numbers. With so many midrange and budget devices running Android, however, it's important to stay on top of your device's performance to ensure smooth and uninterrupted gameplay.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

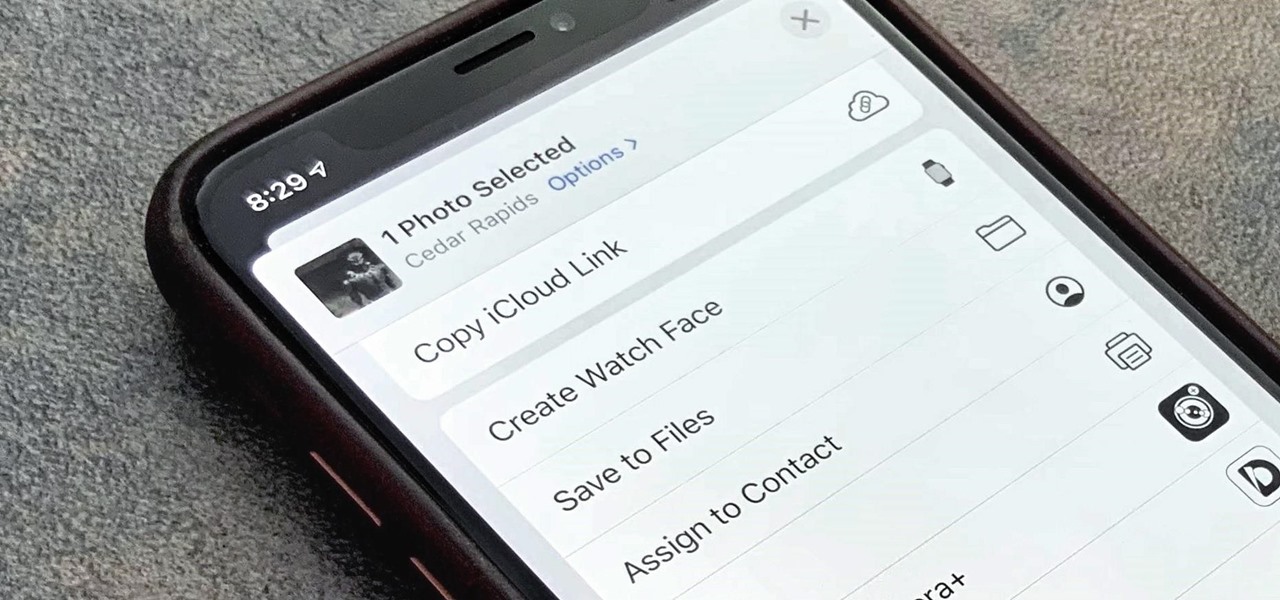
When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

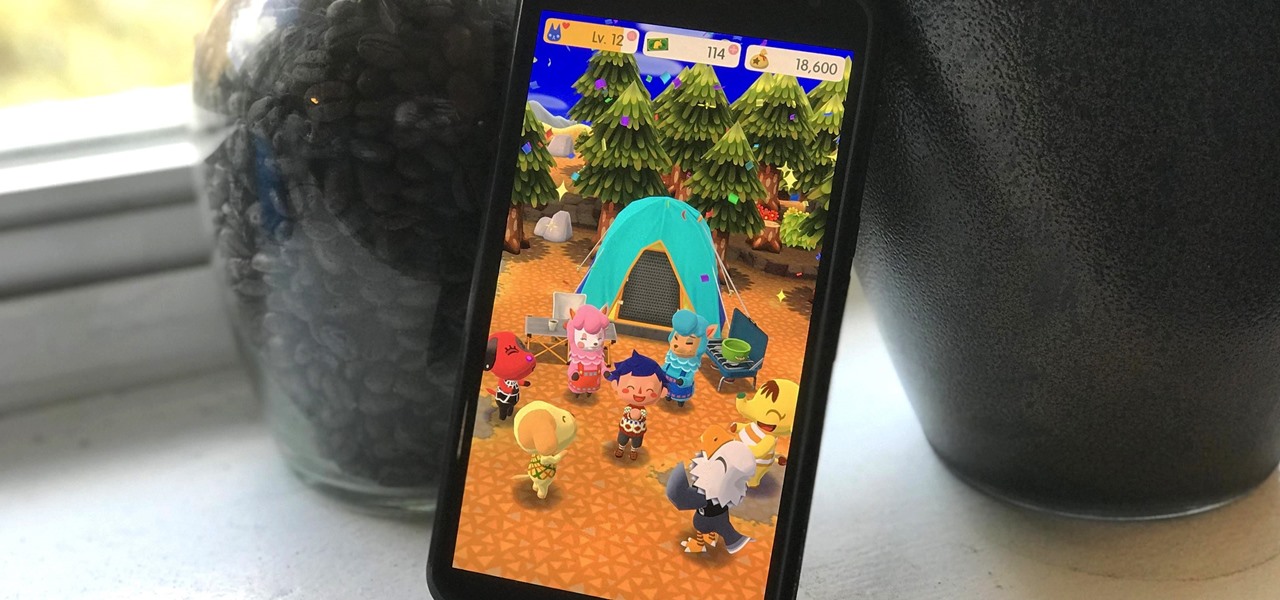
For a friendly mobile game, Animal Crossing: Pocket Camp has an overwhelming number of items and collectibles — from fruit to fish to friends. Even though it can be difficult to keep up, this guide will be a great stepping stone to creating the campsite of your dreams without spending a dime.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.

Heart disease is the leading cause of death of men and women in the US. Over half a million Americans die from it annually. Atherosclerosis — a build up of plaque in the arteries — is a common feature of heart disease and can be caused by smoking, fats and cholesterol in the blood, diabetes, and high blood pressure.

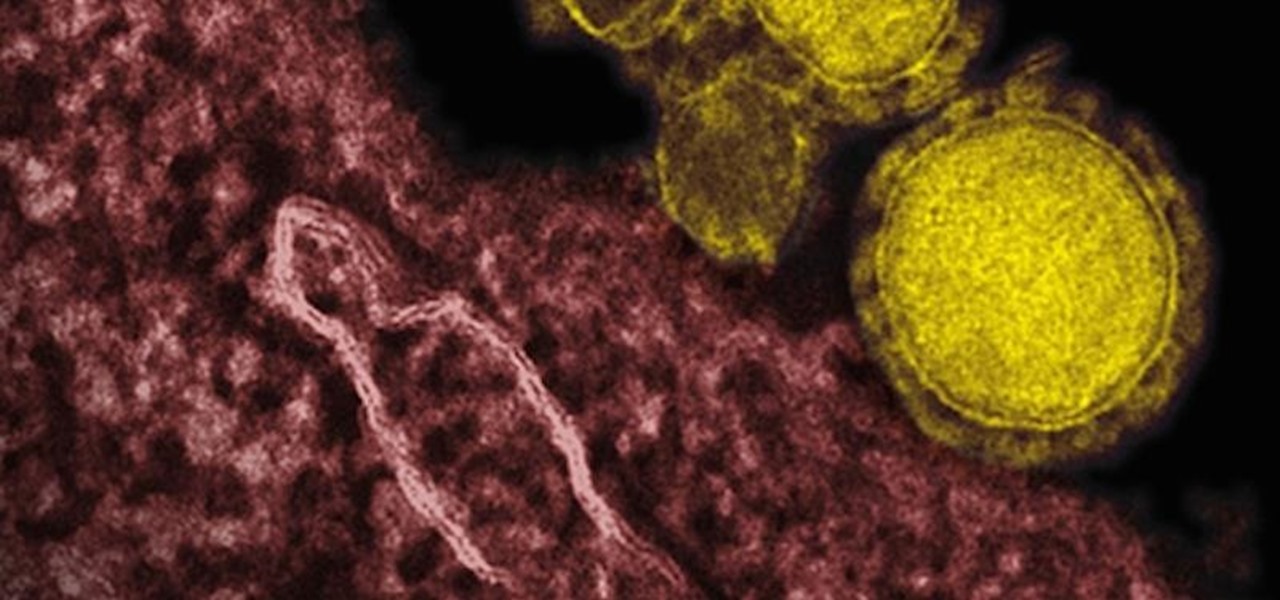
Coronaviruses are common viruses, and most of us catch one at some point — they cause about 30% of all common colds. A new accidental discovery could help fight these viruses, even the deadlier, emerging ones.

People who have heart disease get shingles more often than others, and the reason has eluded scientists since they first discovered the link. A new study has found a connection, and it lies in a defective white cell with a sweet tooth.

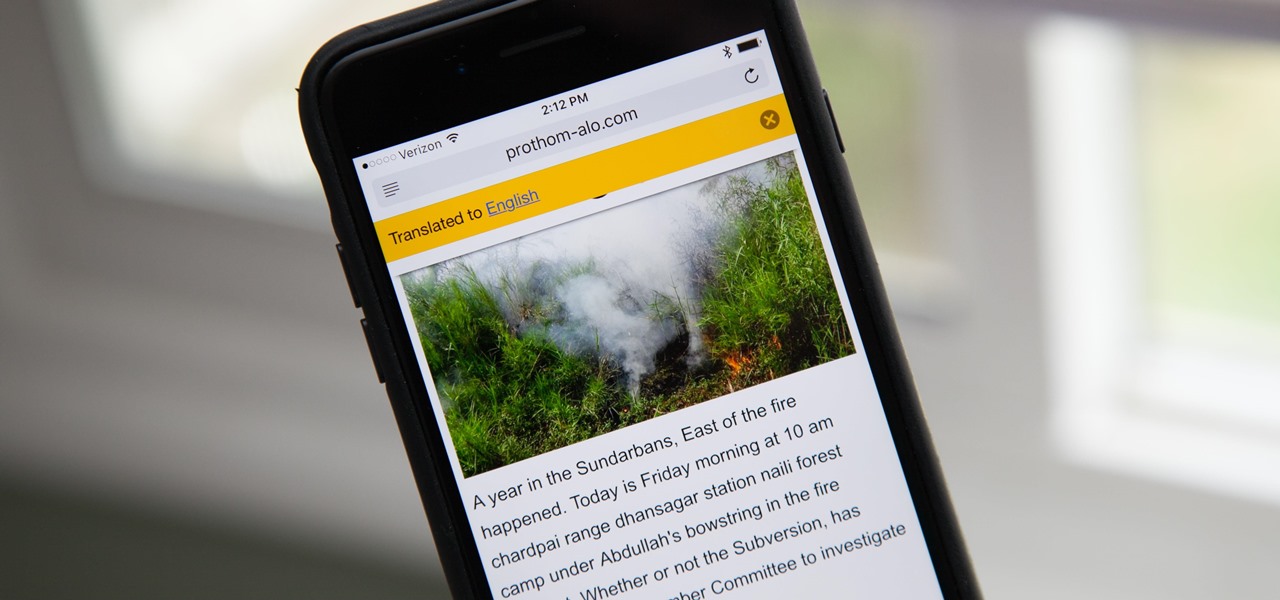
Yes, there's a way for you to get translations of foreign language websites on your iPhone using the built-in Safari app. Problem is, it's not super obvious. Actually, you'd never know the option was there if someone didn't tell you. But with a little setup on your part, you can have Safari translate webpages whenever you need it to.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.

It's 3 a.m. and you're wide awake—your mind is running wild with worries, workplace stress, and panic about the day that lies ahead. How can you possibly slip back into sleep and snag a few more hours of rest when you're so anxious?

Willpower is a pretty significant word. It's the difference between sticking with a clean eating diet and diving face-first into a plate of brownies. It's what drags you out of bed on Monday mornings and into work rather than letting you stay snuggled under the covers asleep. And, most importantly, it's the kick in the butt we all require to both accomplish goals and make changes.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.