Shangri La Security Search Results
News: Red Dead Redemption LA Times Article
Red Dead Redemption LA Times Article http://www.latimes.com/entertainment/news/la-ca-reddead-20100425,0,3266497.story




How To: Cook Mexican Rajas Poblanas with CIA chefs
Learn to cook like a professional Culinary institute of America chef. Watch this how to video as CIA Chef Instructor Iliana de la Vega shows us how to prepare rajas Poblanas. This Mexican recipe is sure to impress everyone at your table. Serve with tortillas.
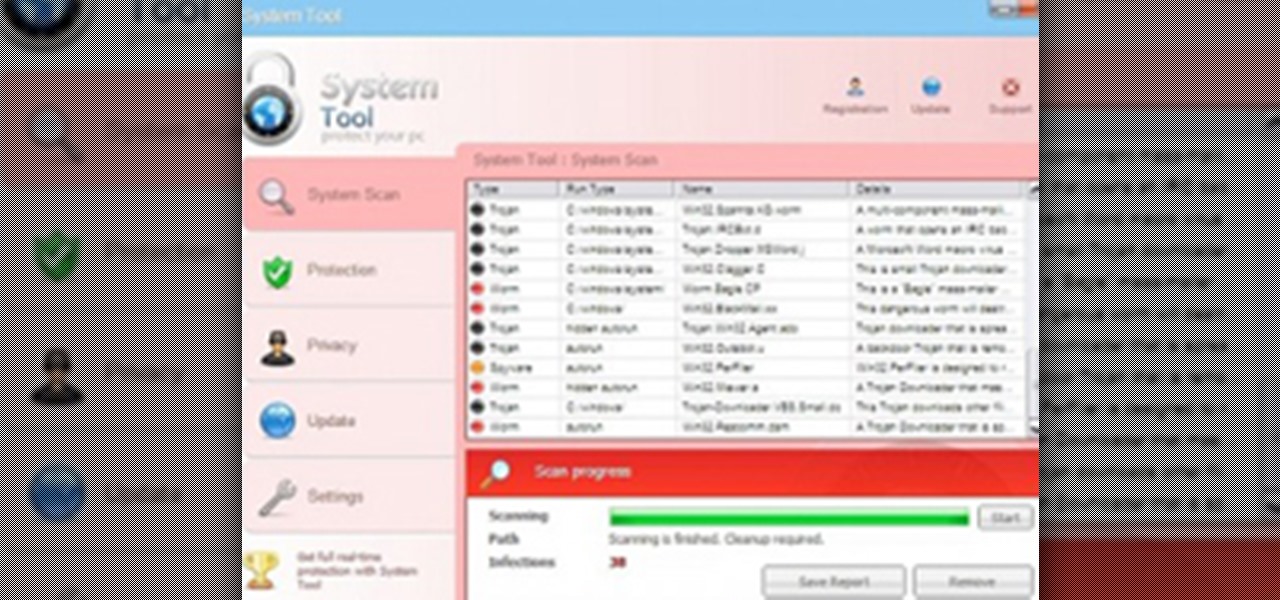
How To: Remove System Tool Malware (System Tool Antivirus) On Windows PCs
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

How To: Make a motion triggered spy camera
Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

How To: Password-Protect Files & Folders in Mac OS X (Snow Leopard)
What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

How To: Hack WPA wireless networks for beginners on Windows and Linux
WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

How To: Play the 2Pac song "California Love" on keyboard and talkbox
"California Love" by 2Pac, Dr. Dre, and Roger Troutman is one of the best rap songs ever and brought Roger Troutman's incredible use of the talkbox to mainstream audiences. If you have a talkbox and a keyboard, check out this video to learn how to play this hip-hop classic on the best instruments to do so.

How To: Play Bobby Darin's "Beyond the Sea" by on the ukulele
Want to play Bobby Darin's "Beyond the Sea" on your ukulele? Learn how with this free video ukulele lesson from Ukulele Mike. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For more information, and to get started playing "Beyond the Sea" or,...

How To: Create a super freaky alien makeup look for Halloween
All the other girls are going to be dressing up as slutty bunnies and slutty witches for Halloween, so stand out from the crowd and turn yourself into something interesting this Halloween by dressing up as this freaky scary female alien.

How To: Encrypt and digitally sign your emails to secure them from prying eyes
If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

How To: Play "Between the Devil and the Deep Blue Sea" on the ukulele
Want to play "Between the Devil and the Deep Blue Sea" à la George Harrison of the Beatles on the ukulele? Learn how with this free video ukulele lesson from Ukulele Mike. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For more information, a...

How To: Play free and rest strokes on the ukulele
In this free video ukulele lesson from Jens Albrecht, you'll learn how to play both free and rest strokes on your ukelele à la Ukulele Mike in his "Paris Nocturne." Whether you play the ukulele or bass kazoo, if you want to improve your technique, you'll need to practice. Fortunately, the Internet is awash in high-quality video tutorials like this one, which make practicing both easy and highly enjoyable. For more information, and to get started playing free and rest strokes on your own ukule...

How To: Do four different cupcaking icing techniques
In the confectionary world the way you ice or present a cupcake is just as important as how good a cupcake tastes. Thanks to cupcake bakeries like Magnolia Bakery in NYC and Sprinkles in L.A., the age of the yummy and chicly decorated cupcake has officially been ushered in. Make your own cupcakes that much more in line with the times by watching this cupcake decorating tutorial.

How To: Protect your privacy online
In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

How To: Make watermarks in paper for security
Don't fret too much if your watermark is barely noticeable when you're finished with this project - the less obvious it is, the better a job you've done. Watermarkers are present in many types of paper, especially the monetary kind. If you hold up a ten dollar bill you'll see a watermark of Thomas Jefferson's face on the right, proving the bill is real.

How To: Enable the 'Ctrl-Alt-Del' login window on Windows 7
Use Microsoft Windows 7? Miss the old Ctrl-Alt-Delete log-in prompt? It's easy to restore. So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete overview of the restoration process in just over a minute's time. For more information, and to get started restoring this useful security feature on your own Windows 7 PC, watch this free video tutorial.

How To: Hack your MacBook into a region free DVD player
If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial.

How To: Create a Chola look with the illusion of shaved brows
Ever needed to create the illusion of shaved eyebrows? If you are going to try a Chola makeup look you'll need to get rid of those brows!

How To: Make homemade brownies easily and on a budget
This video shows you how to make delicious moist homemade brownies for you and your guest. Step by step you'll go on a delicious chocolate journey in create some delectable brownies. Great for any chef, and to enjoy a la mode.

How To: Add a watermark to photos in Photoshop
The PhotoshopUniverse team effectively teaches a method of adding a watermark to an image, as a security feature to make it harder to copy or steal. Instructions are simple and easy to follow, using as an example a photo of two girls that one might have in his or her family album. Using Photoshop, the text that will become the watermark is added, rotated and patterned across the entire image. To finalize the watermark, the opacity is edited to a desired value so that it does not interfere wit...

How To: Turn your doorbell into a guard dog alarm
This video shows you how to make a security device out of a door bell. The concept is that most thefts happen when people are away from home. To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell. When the door bell rings i...

Beat Resident Evil 5 Chapter 2: Gigante
Check out this RESIDENT EVIL 5 Chapter 2: Gigante walkthrough from Machinima.com The behemoth from RE4 returns with some new tricks up his sleeve.

How To: Create a Moroccan magenta nail art design
Julieg713 is a nail art expert. Check out her nail art tutorials on WonderHowTo (Search Julieg713). Her nail art looks are fun & pretty, not to mention well demonstrated. This nail polish video demonstrate how to create a Moroccan magenta nail art design. Watch this video to learn how to recreate this nail art look.

How To: Prep for auto racing with proper seat belt security
There are two ways to properly lock your seat belt. You can use the childlock auto adhjustment. Or you can recline the seat, but then push forward to make your seat belt very tight. You don't want to be flopping around in the car. The bottom of your wrist is on top of the steering wheel and your shoulder is in the seat. It will loosen up when you get on the track.
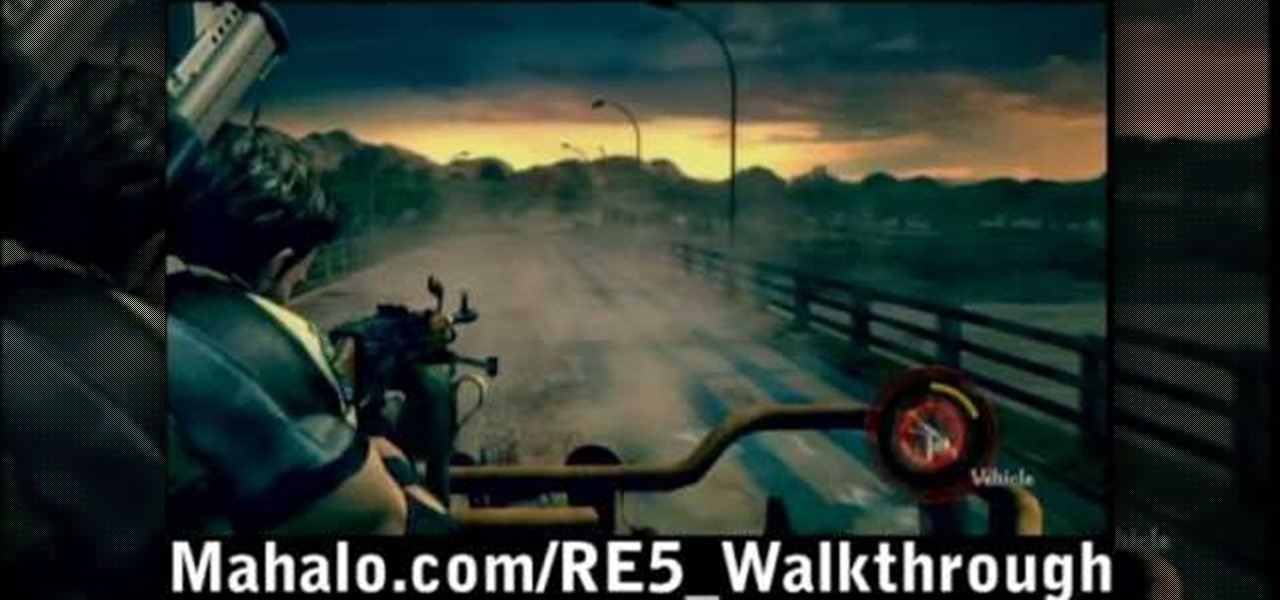
How To: Walkthrough & beat Resident Evil 5: Savannah
Check out this Mahalo video walkthrough of Savannah in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

How To: Fake a memory clear on your TI calculator to cheat
This video will show you how to fake a RAM, Flash, or entire memory clear. Lots of teachers and test administrators go around and clear your calculator so students don't cheat. This is any easy way to subvert the teacher's security measure. This is a good thing to know if you want to cheat on your GED, SAT or ACT test / exam.

How To: Hack websites using cross-site scripting (XSS)
In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...
News: Apple Releases iOS 14.4.1 for iPhone, Includes New Security Fixes
Apple just released iOS 14.4.1 for iPhone today, Monday, Mar. 8. The event marks 41 days since Apple released a public update for iPhones, with iOS 14.4 back on Jan. 26.

News: Apple's iOS 13.4.1 Fixes FaceTime Bug, Now Available for 2020 iPhone SE
Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.
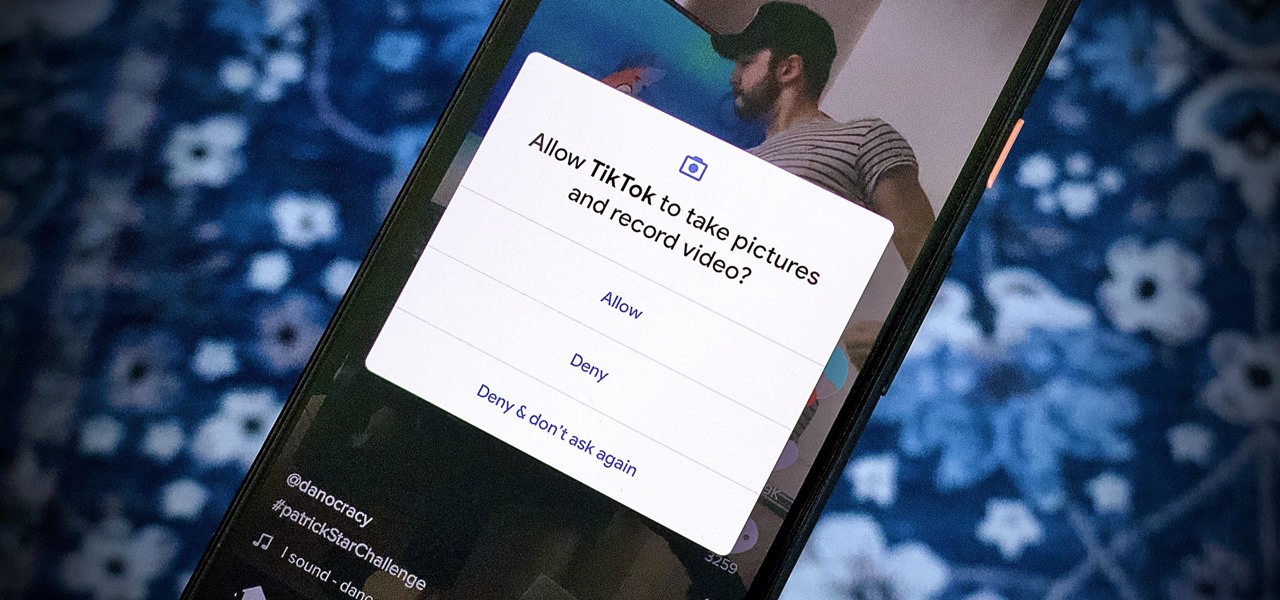
How To: Completely Prevent Apps from Accessing Your Camera & Microphone on Android
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.
News: Apple Just Released iOS 13.3 Public Beta 3 to Software Testers
Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.
News: Apple Releases iOS 13.3 Developer Beta 3 for iPhone
Just two days ago, on Nov. 18, Apple released iOS 13.2.3 to the general public, which included stability updates for bugs affecting iOS 13.2 and earlier. Today's update isn't for the general public, however. Instead, Apple just pushed out iOS 13.3 developer beta 3 for software testers.

News: Apple Releases iOS 13.3 Public Beta 2 to Software Testers
Apple is often unpredictable when it comes to beta releases, especially with public betas. Developers receive their updates first, then public testers have to wait and see if Apple will do the same for us. Sometimes, the iPhone OEM makes us wait until the following day, but not with iOS 13.3 public beta 2. This update is now available to download and install.
News: Apple Releases iOS 13.3 Beta 2 to iPhone Developers
We're finally back in the swing of things. For the first 26 days after the release of iOS 13.2, which introduced 22 new features and changes to the iOS 13 era, there wasn't a new beta. Then, Apple released iOS 13.3 developer beta 1, and now we seem to be back on schedule, as Apple just released 13.3 beta 2 to developers.
How To: Set Up Face Unlock on the Google Pixel 4
The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how.

