If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.
There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

Video: . A fun loving character from an art site called DeviantART. This is widely used in comments across the Deviant art forums and comments.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

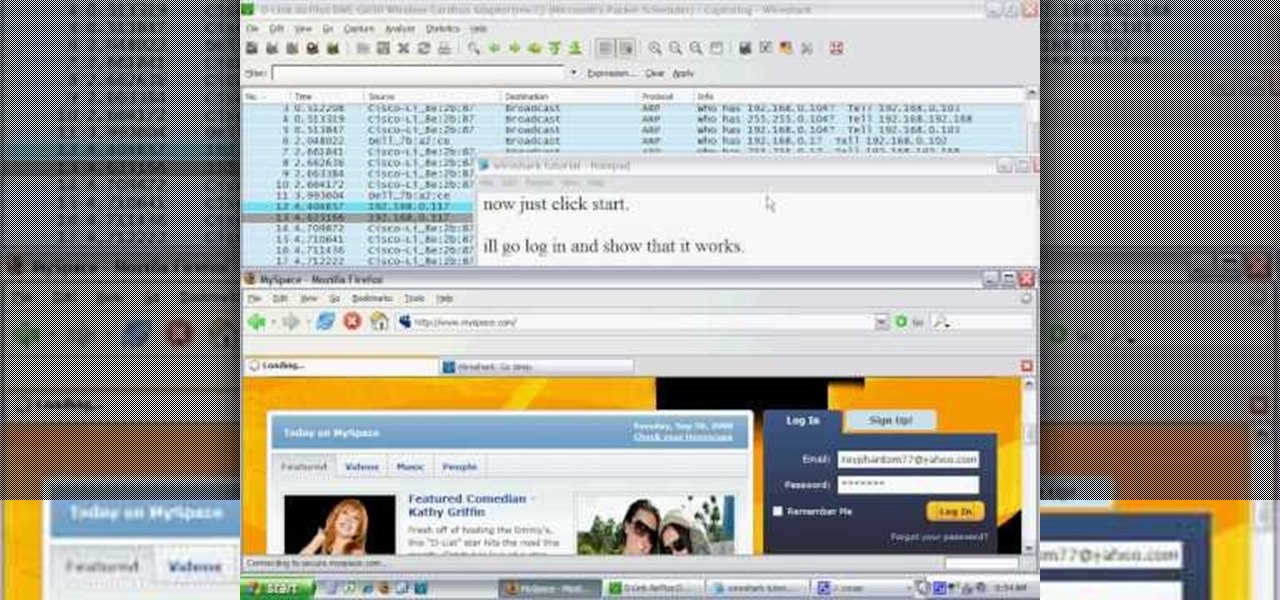
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!

If you've recently upgraded you doorknob to an elegant Schlage Plymouth Handleset, then it's time to match your front entry locks and install a new electronic high-security Schlage Plymouth Keyless Entry Deadbolt. This keypad is great if you never want to lock your bottom handleset (or doorknob). Watch this step-by-step installation video to see how it's done! You'll need a phillips head screwdriver or electric drill. To see how to install the matching handleset, click here.

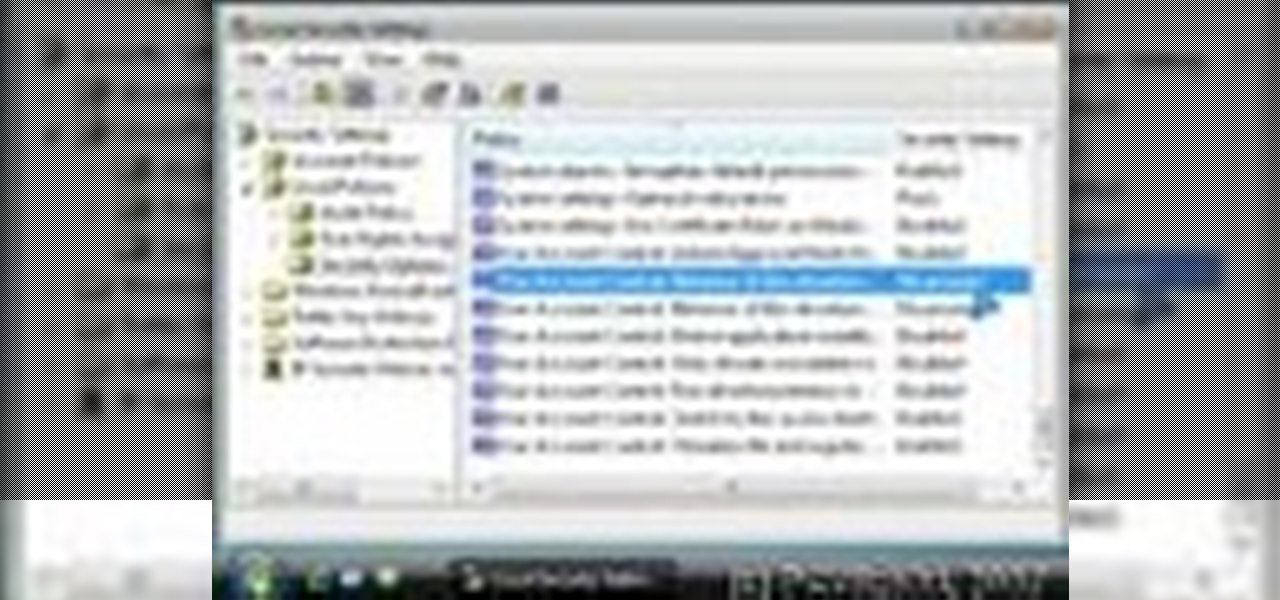
Why is Windows always asking you for permission before you do anything? Since when does Windows control your computer, and not you? Those user account control popups can be so frustrating, especially when it comes to simple tasks.

In this video, we learn how to protect your privacy while using Twitter. Your personal information can get stolen in an instant with the internet. With Twitter, when you are doing updates showing where you are and what you are doing, someone could try to find you and potentially create harm to you. To help you avoid situations like this, you need to go to the security settings of your Twitter account. When you go here, you can change the account so that it only allows people you want to follo...

In this tutorial, we learn how to use the notepad to get by school internet blocks. First, open up Notepad on your computer, then type in "<html>" "<body>", "iframe src=http://www.youtube.com", then "height=100%", then "width =100%". To finishe, type in "<iframe>>/body><html>". Save this as hack.html as all files. After this, open up your browser, then you should be able to go to the website that you wanted to go to! This is a great way to get around the security settings that your school has...

In this video tutorial, viewers learn how to test their system performance. Begin by clicking on the Start menu and select Control Panel. Then click on System and Security, and select "Check the Windows Experience Index" under System. Now click on "Rate this computer". The system will then begin to run some tests. This will take about 1-2 minutes. The Windows Experience Index assesses key system components on a scale of 1.0 to 7.9. This video will benefit those viewers who use a Windows 7 com...

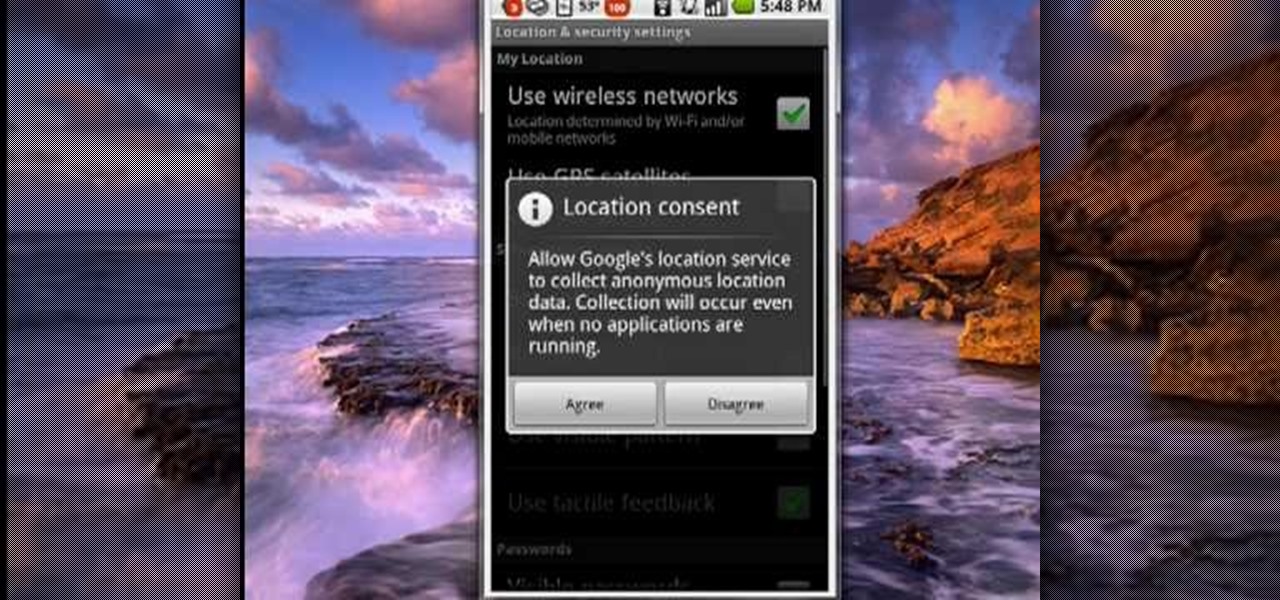
Many applications, especially those found in the Android Market are more effective when they know your physical location; like an app that's going to find the nearest gas station, restaurant or ATM. One of the salient advantages of a Google Android smartphone over, say, an Apple iPhone, is the inherent extendibility of the open-source Android mobile OS. There are a seemingly infinite number of settings to tweak and advanced features to discover and use. This free video tutorial, in particular...

Fashion designer Cate Adair demonstrates dressing with a sarong for Modern Mom. She also discusses how to buy or extend a sarong when the one you find isn’t long enough. One important consideration for beginners is finding a sarong that can wrap around the body twice for security. One way she wraps is to simply wrap under the armpits twice and tie a flower or ornament with the corner. Another way is to put the full sarong on from the front, wrap each end backward and then over the shoulders...

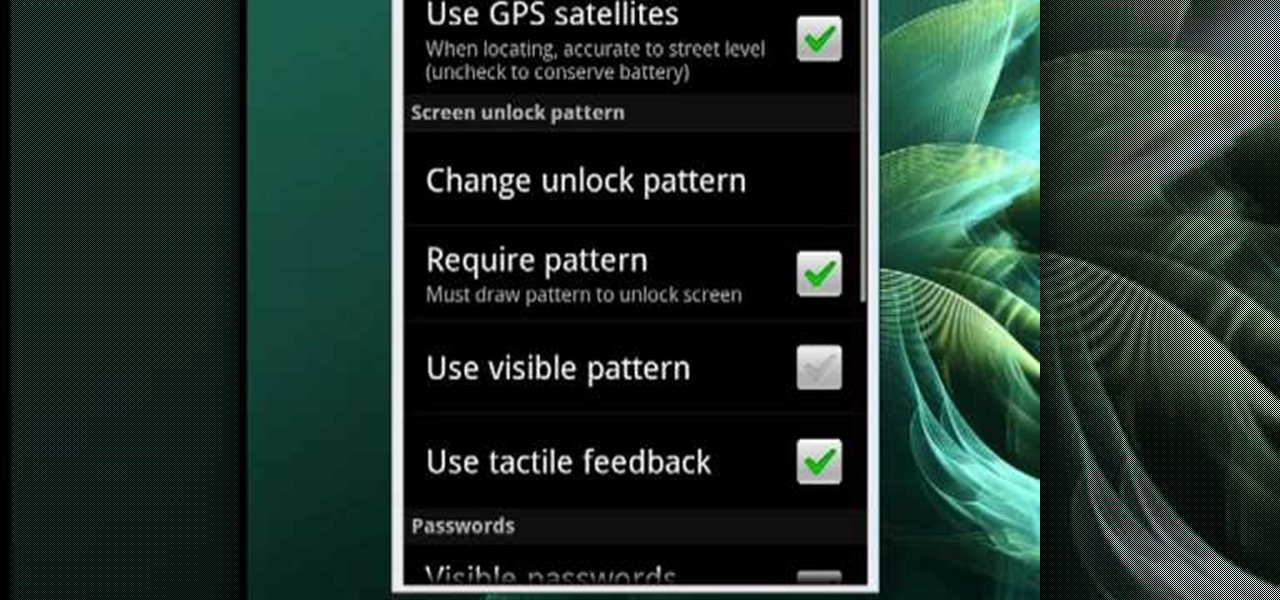
In this video, Mike Callahan shows us how to make our unlock pattern visible on an Android phone. First, unlock your phone and go to the home screen. Then, go to 'settings, location & security". After this, click the button that says "use visible pattern" so that the check mark and button are both gray instead of green. To test this, tap back on the home screen and lock your phone. Now, when you draw in your pattern you will be able to see it on the screen. This way you can see the pattern as...

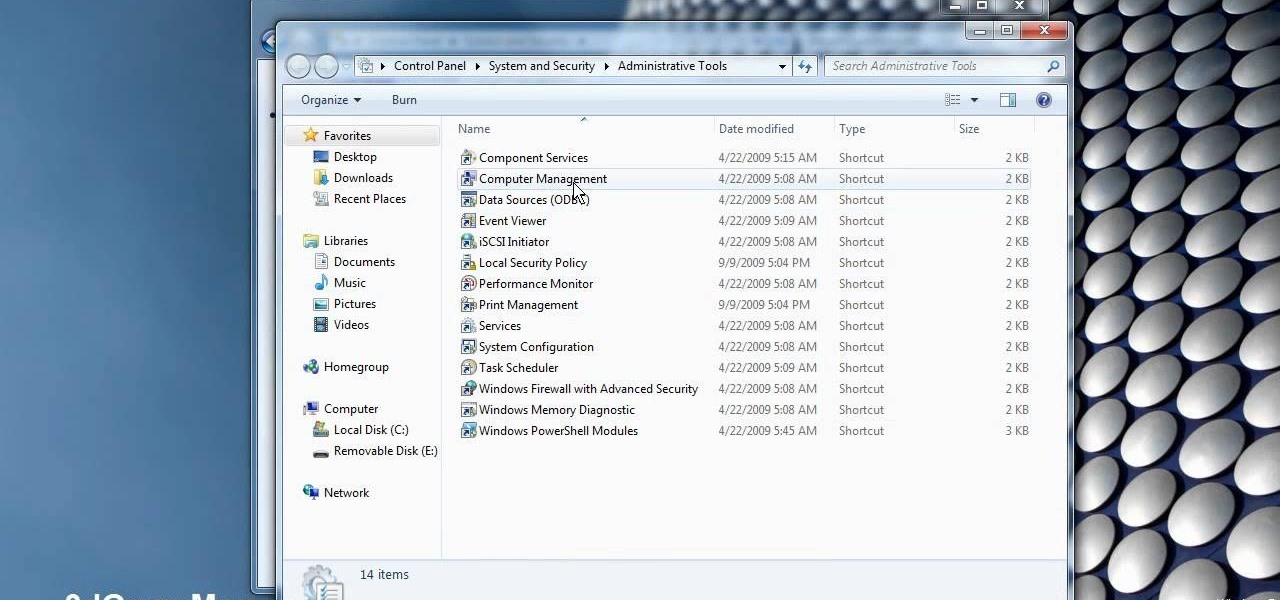
This video demonstrates how to change a drive letter to a certain drive in your Windows 7 computer. On you Windows 7 computer, go to Start > Control Panel. In the Control Panel, select System and Security then open the Administrative Tools. Look for and open the Computer Management tool. On the left side pane of the Computer Management window, select Disk Management. Look for and right click on the drive you want the drive letter changed. Select 'Drive Letter and Paths...'. Click change and s...

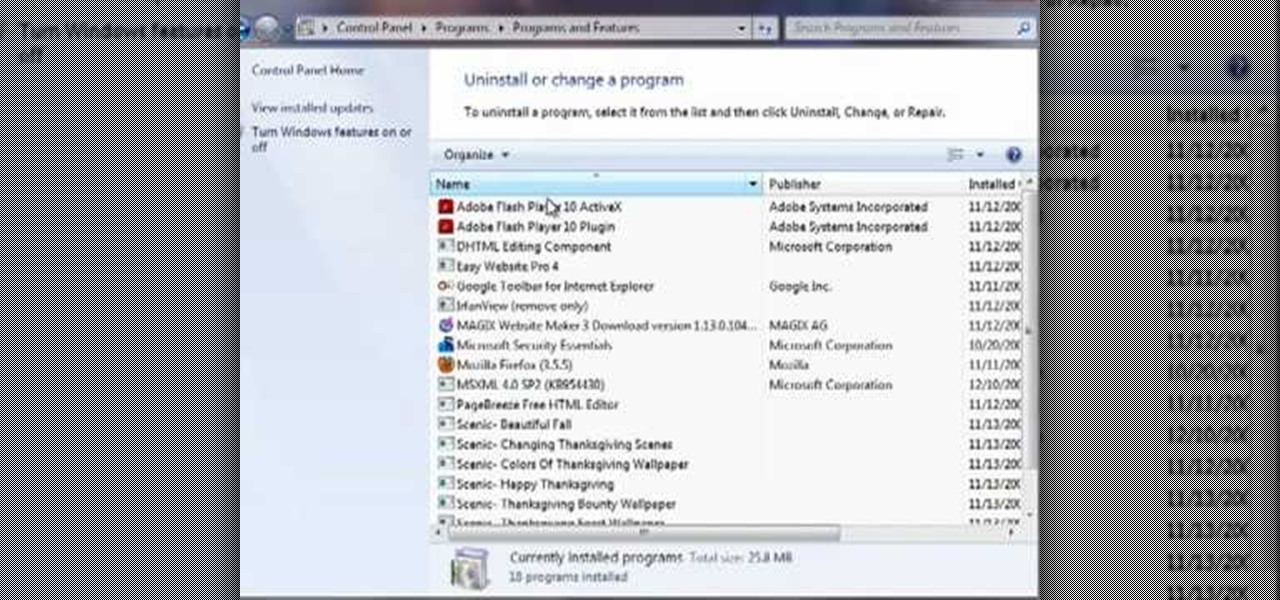
This video by Butterscotch shows viewers how to uninstall a program in Windows 7. To begin, click on the start button at the bottom-left of the screen. Click 'Control Panel' in the boxes that pop up. Click 'System and Security'. On the left side of the window, there will be a link marked 'Programs'. Click on it. Click 'Uninstall a program' beneath the 'Programs and Features' heading. Highlight the program you want to uninstall, then click the 'Uninstall/Change' button near the top of the wind...

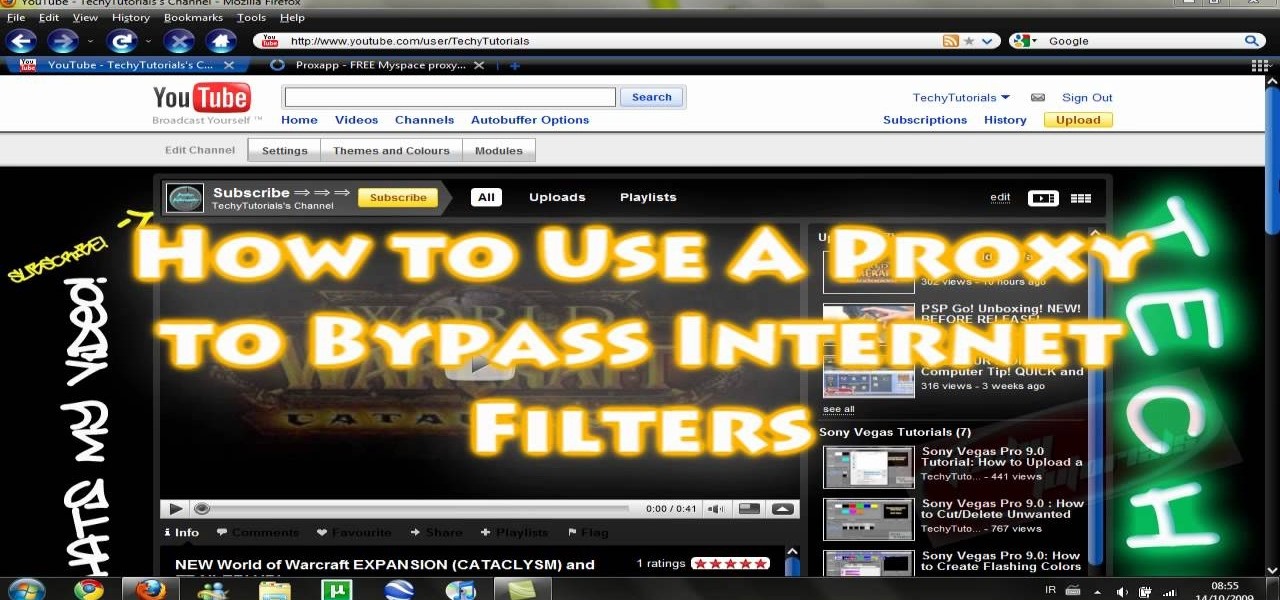
The video shows us how to use a proxy to bypass the Internet Filters. Most of the times in our schools and colleges most of the websites including the social networking ones will be blocked for security reasons and makes us unable to log into those websites. In such cases even the ones from the YouTube, several videos will be blocked. So in this video, we will be shown how to bypass those filters and log into those sites. Firstly go to the website Proxapp and over there you will be asked the ...

RAID, or Redundant Array of Independent Disks, lets you divide and replicate data among multiple hard disk drives for information storage security. This video tutorial demonstrates how to install Ubuntu in a RAID 0 array. Before starting, you'll need at least 2 hard drives and an Ubuntu alternate installation CD. RAID 0, or striped disks, let's you install an operating system, such as Ubuntu, on a partition, while using others for data storage, as illustrated in this instructional segment.

In this video you will learn how to update your version of Windows 7 and how to check the system settings for automatic updates. In order to do this you need to go in the Start Menu and then in the Control Panel. Then you need to click System and Security. The next step is to click Windows Update. A new window will pop-up and you will see two types of updates: Important Updates and Optional Updates. To install them just click on the blue link and then check the boxes. To check for updates you...

In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...

Check out this Mahalo video walkthrough of Marshlands in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

If you work in the film industry, are currently in film school, or have aspirations of being involved in the movie making process in some way, shape or form, you're probably very familiar with a certain set of books published by 411 Publishing that are commonly referred to as the "production bibles". If you live in the Los Angeles area, LA 411 is a valuable source of information when it comes to fulfilling your production needs. And if you're in New York, the NY 411 book is just as crucial fo...

Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

The guys over at @evleaks continue their slow trickle of leaks about Samsung's upcoming flagship device. The first drop is simple enough, a confirmation that Samsung will continue its branding strategy, naming their next device the Samsung Galaxy S5. These next two are a little more interesting, despite their graphical shortcomings—screenshots of two APKs, or application files, from an "official" Galaxy S5 system dump.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Welcome back, my rookie hackers!

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.