In this how-to video, you will learn how to quickly make a Windows 7 boot disk. This is essential for making backups or booting from something other than the operating system on your hard drive. First, go to the control panel and click the back up your computer option under system and security. Next, go to the left and click create a system repair disk. Put a blank DVD in to the optical drive. Select your drive and press create disk. This video shows just how quick and easy it is to make a bo...

In this video tutorial, viewers learn how to secure a Mac Book Pro. Begin by opening the System Preferences and select Security under Personal. In the General tab, users are able to put on a password when the computer goes to sleep or screen-saver, disable automatic log in and log out after a certain amount of minutes. To set a password, go back to System Preferences and select Accounts under System. Then click on Change Password and input your password. This video will benefit those viewers ...
In this video, you will learn exactly how to take pictures with your Apple iPad! Wifi or 3g model is fine, 16GB, 32GB, or 64GB models are all fine also! What you need for this to work:

First to connect to a wireless internet connection using Windows 7 you must first click on the icon that looks like sideways stairs that is located on your desktop in your task bar. Click on the icon and you will be taken to a page that will show all of the wireless connections in your area. Find your network then click on it. You will be prompted to type in your network security key, do so then your computer should connect to the wireless internet within the next few minutes. Close out of th...
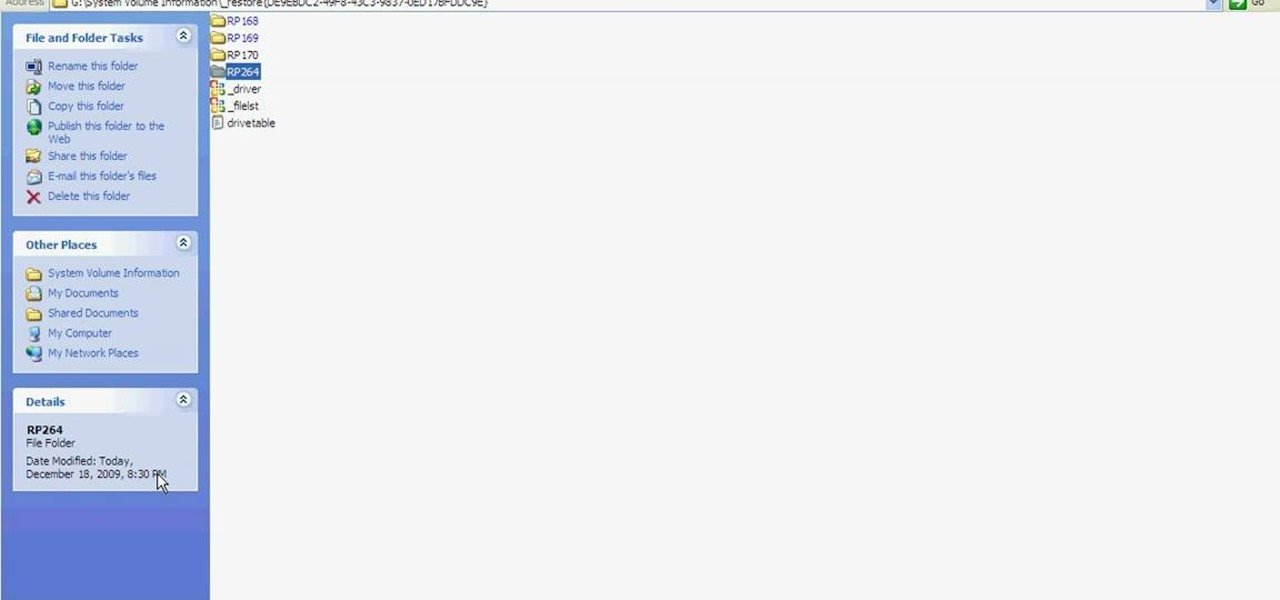
Learn how to fix or recover a corrupt windows registry following the steps outlined in this video tutorial. To begin, take the hard drive out of the computer with the corrupted registry and connect to another computer. To find the files you need to replace go to Start and My Computer. Look for the hard drive that you just added and double click on it. Go to Tools and Folder Options. On the View tab under Advanced Settings click Show Hidden Files and Folders, and unclick Hide Protected Operati...
Remote desktop is a very powerful feature using which you can access any desktop from another desktop over an internet. In this video the instructor shows how to enable remote desktop in Microsoft Windows XP. Remote desktop is a system that will allow other users from the internet or your local network to connect and control your computer. As this can be a security hazard be careful while sharing the details of your remote desktop connection. To enable this click on start button, right click ...

Wrapping your wrists for boxing is very important to provide protection and support when you are throwing your punches. This video shows you the right way to wrap your wrists to prevent injury. You'll be putting the seam side of the wrap against your skin, and start by putting the loop at the end over your thumb. You will start by wrapping the wrist a few times, depending on how long your wrap is. Watch to see the correct way to cover the knuckles and secure the wrap against your hand before ...

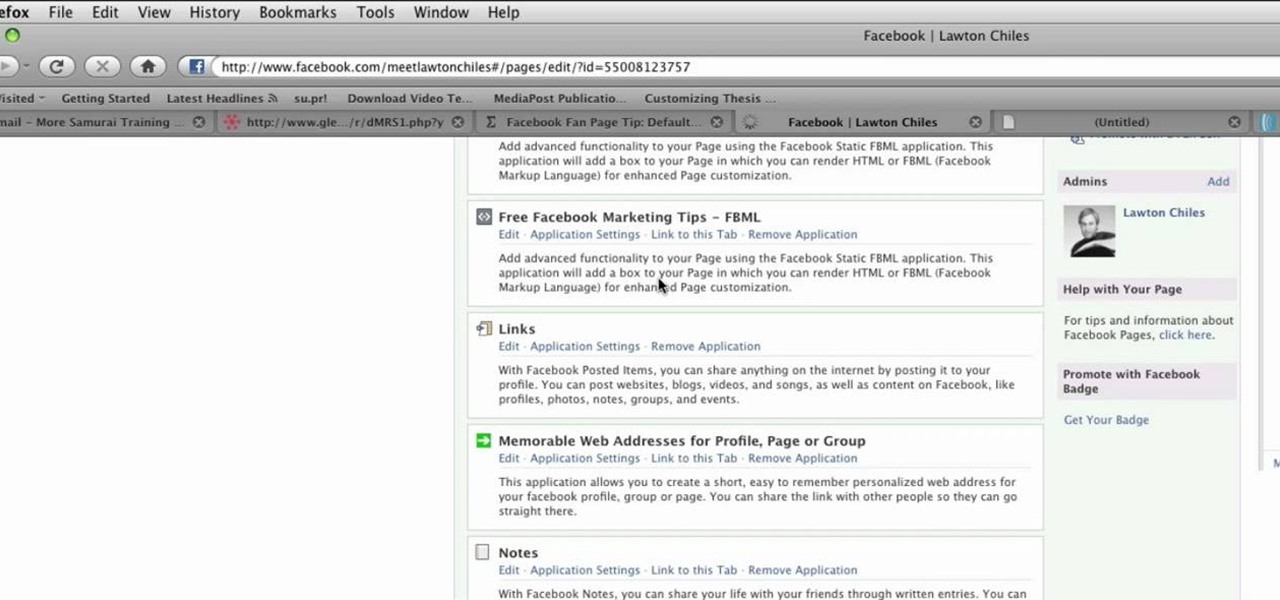
This video shows you how to make a custom Facebook Fan Page for your favorite Celebrity, Club, activity or anything you choose! First thing you must do is activate a Facebook account. Its really simple, just go to www.facebook.com and create a profile. After that type in FBML in your search bar and click on Static FBML. That application will enable you to create many different settings for your Fan page including ads and different looks and security measures for your profile. Now get to creat...

This instructional video by GoogleNexusOne shows you the features and how to set up a recently unboxed Nexus One Android phone. First the functions of the indicators and buttons are explained, and the different ports and jack are highlighted. After that the back of the phone is opened and the locations of the slots for the SIM card and the microSD card are shown, as well as how to insert the battery. Set up the phone as instructed after reading the documentation, sign in with your gmail accou...

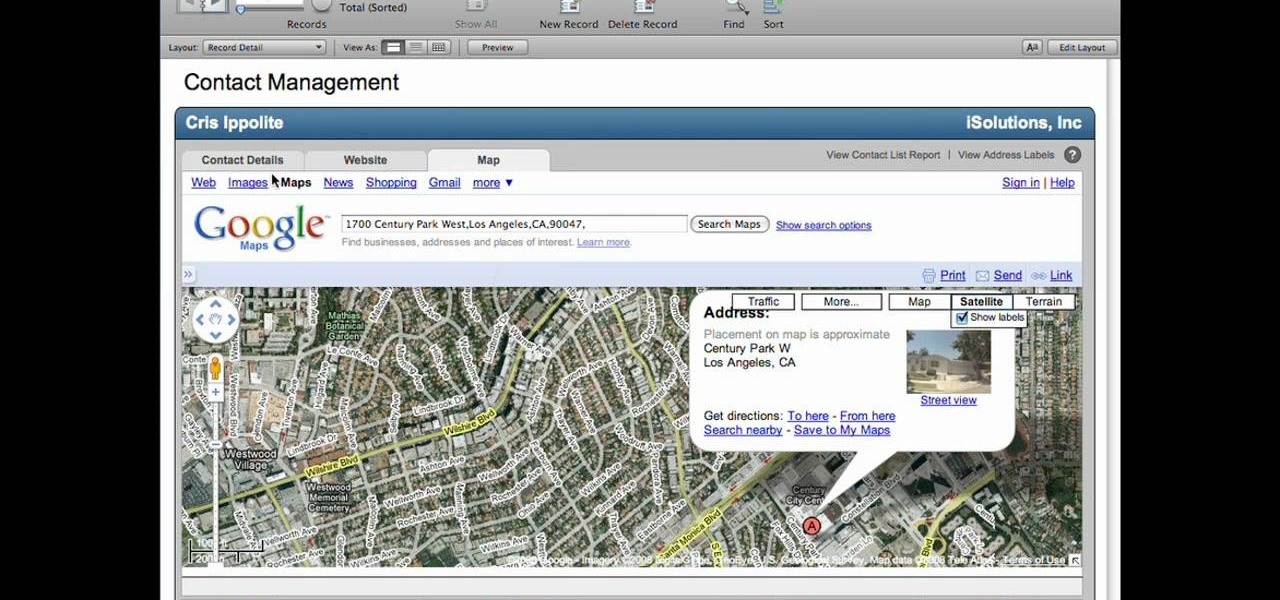
Lyndapodcast teaches you how to create a database using FileMaker Pro 10. You can link one contact with multiple addresses and information and store that into a single database. You can also add content from the web into your FileMaker layout, including maps, pictures and music. You have a security module where you can set permissions for the users using the database. You can also publish the FileMaker database to the web. For this go to File - Sharing - Instant Web Publishing. Another featur...

In this video you will learn how to do a Flair bartend: vertical toss grab reverse grip. Start this trick with an over hand grip, then reverse grip right hand. Reverse grip and pour. Make sure you are holding your bottle security. Your holding the bottle and spinning with the other hand. You might have to practice the end pour so you don't spill as you bring the bottle back up. This video does the sequence many time so you can get the hand work done correctly.

This video will allow you to view your saved usernames and passwords in Firefox. This may be useful for users in case you forget what your user names or passwords are for different sites and would like an easy way to find them. Under the Firefox toolbar, go to "Tools" and then "Options" in order to get a popup which will allow you to view different aspects you can change in Firefox. Go to the security tab and then click on the button which says "Saved Passwords" in order to view all your save...

AntiVirus Live is a fake antivirus software which comes onto your system and asks you to buy it. It doesn't provide any security to the computer. Here is the procedure to remove it: (1) disable the proxy server for your LAN in Internet Explorer. 2) download the process explorer from ms technet. 3) locate and kill the sysguard.exe. 4) finally remove AntiVirus Live. After following all these steps reboot the computer. Protection against future intrusion is mentioned. You should be aware of the ...

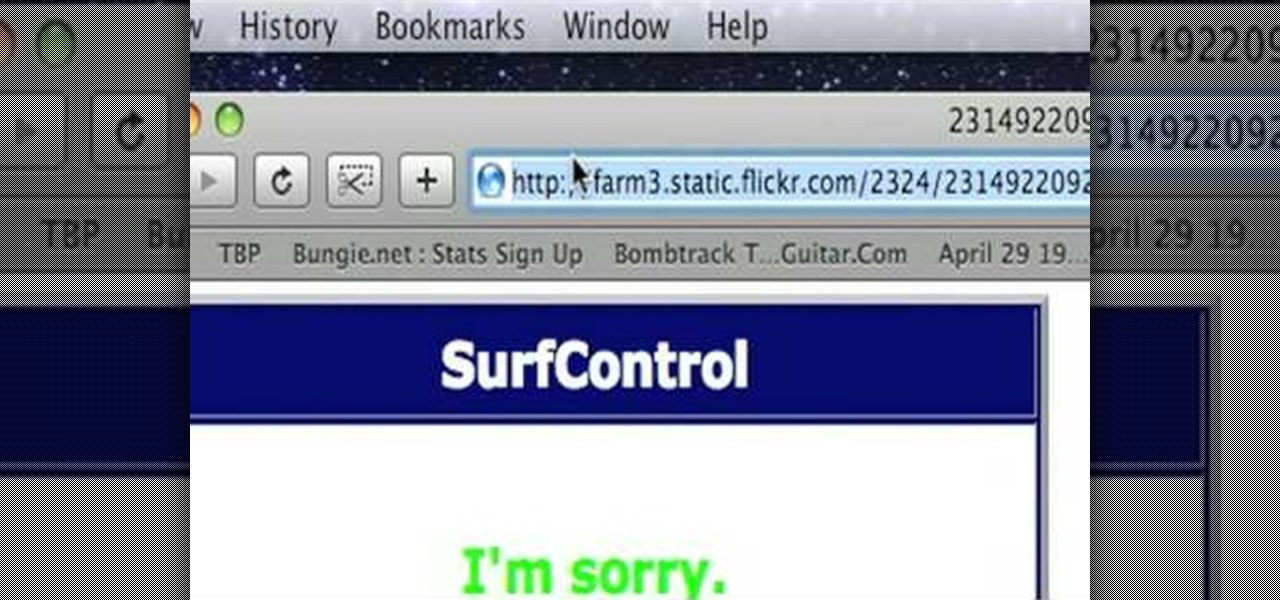
The author shows how to bypass SurfControl and access blocked websites at school. He shows how to open the OperaMini website from Google and to access the demo of OperaMini in that website. Now in that demo we can key in the website address and easily access the website from there. In this manner we can easily bypass small security software like SurfControl. If you are having trouble accessing websites because of SurfControl just follow the steps in this tutorial and you will be able to acces...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to install a Wii homebrew hack using the Twilight Hack.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wii games to SD to play in HD.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to get free WiFi by tunneling through DNS.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a web-enable remote controlled tank.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to make a Twitter tamagotchi bot with PHP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session hijack with a pineapple.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to boot Windows from a USB flash key.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to configure Cisco and iptables firewalls with a utility.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to break down IP and TCP header with Wireshark.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to organize your desktop with Microsoft Scalable Fabrics.

Beat the Level 2-3 Boss in Resident Evil 5 via this walkthrough and gameplay. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Looking for a fancy dessert for tonight? Then try this recipe, it is a specialty from the Cognac region in southwest France. This Souffle a la Cognac is sure to be a hit.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Check out this video tutorial to see how to construct an alarm system, that's based on the principle of motion detectors, which work by touch. It's very useful to catch unpleasant visitors red-handed. So make sure your chocolate bar never gets snagged again, catch the bandits with a motion detector alarm! Or just keep you kids away from the birthday present closet where peeping is not allowed.

This is a tutorial that shows you how to view and control your computer screen from your iPhone/iPod Touch. But this method is for people who have a jailbroken iPhone/iPod Touch. This works on Edge and Wifi. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

See how to make an X10 wireless security camera into a nice helmet cam on the cheap in this three-part video. All it takes is an X10 camera, ten bucks in parts, and two hours of your time.

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

Xeni visits the offices of the Electronic Frontier Foundation and speaks with Jake Appelbaum and Bill Paul, two of the authors of a security research paper that shows how your computer's memory can be tricked into revealing data you thought was safely encrypted, and out of the reach of others. Hack into encrypted computer data.

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.
While following a tutorial on python recon tools, I found a new way to access the command prompt on a school network. While there are other ways of bypassing security, it's nice to learn use Python's OS library.

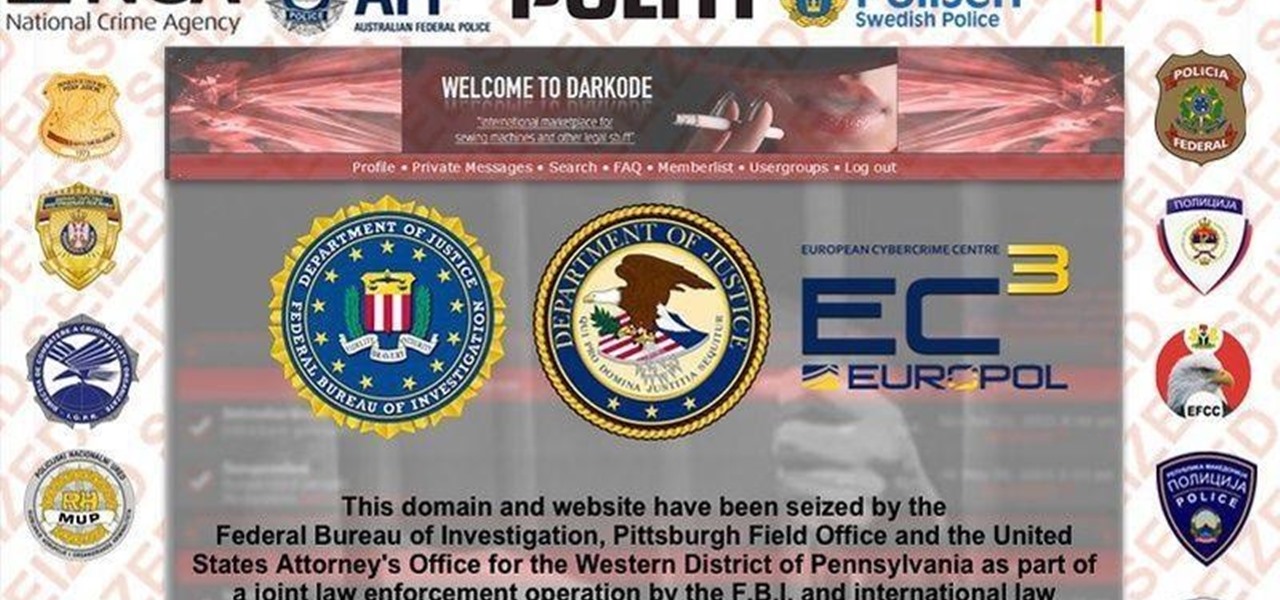
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...