Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

On mobile devices, the Notification Center received a huge facelift when iOS 8 was released, but it wasn't until Yosemite that its Mac OS X counterpart received the same amount of love—especially the much needed ability to add custom widgets, like a FaceTime dialer.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

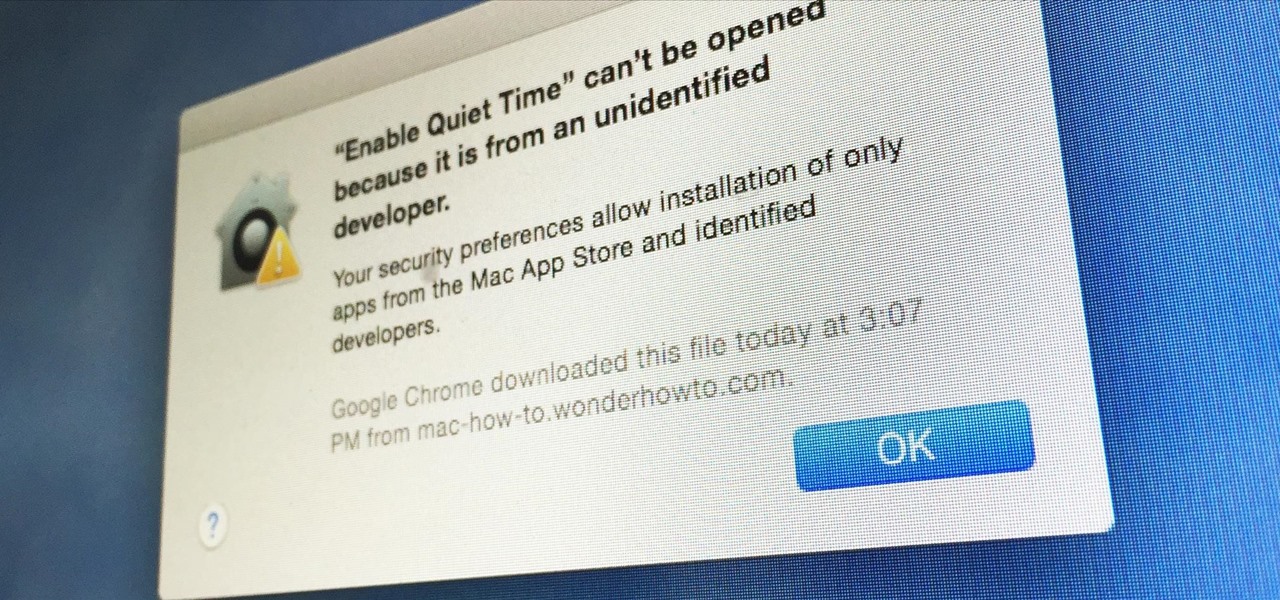
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone.

Most times when you take your smartphone out of your bag, pocket, or purse, you probably know exactly what you're going to do with it. Make a call, send a text, take a selfie, browse viral videos on YouTube, or one of the other many things a smartphone can do nowadays.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

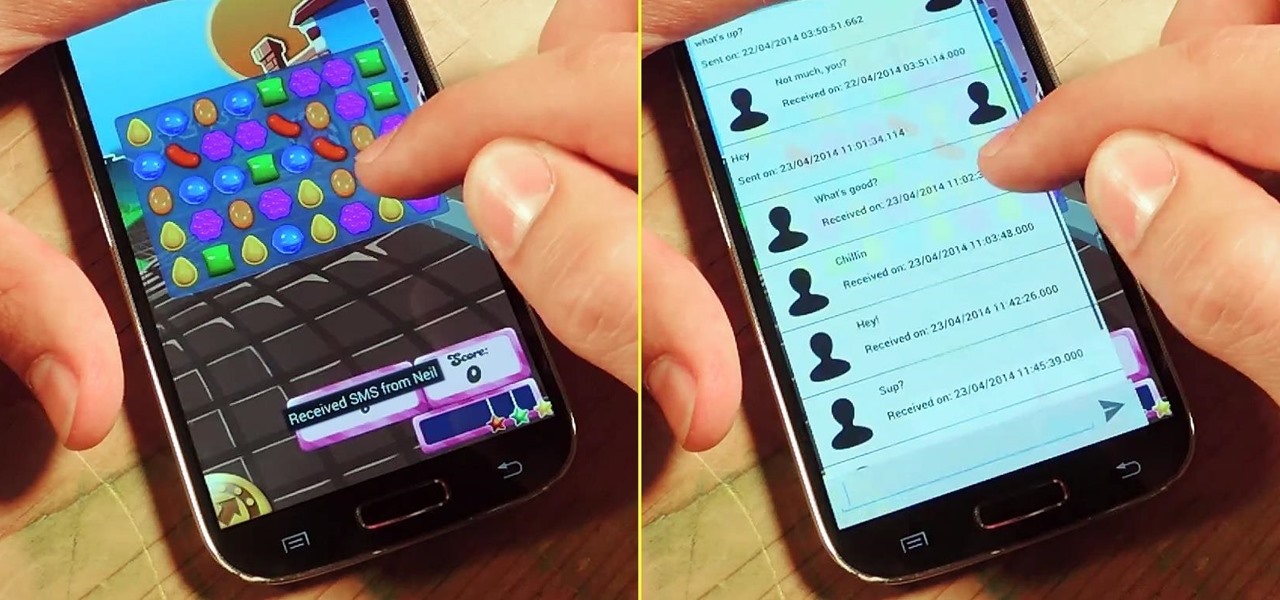
I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

As respectful as you may be, it's hard to resist looking through someone's iPhone when given the chance. You're not trying to snoop around, but it's just too easy to open up apps and read embarrassing emails or find scandalous Instagram follows. It's like looking through a digital diary riddled with deep, dark secrets.

Sometimes it's the little things that make our days better, like finding a dollar in our recently washed jeans or a box of donuts in the lunch room. But your Nexus 7 tablet's lock screen isn't typically one of those things—it's just a lock screen after all.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear Store.

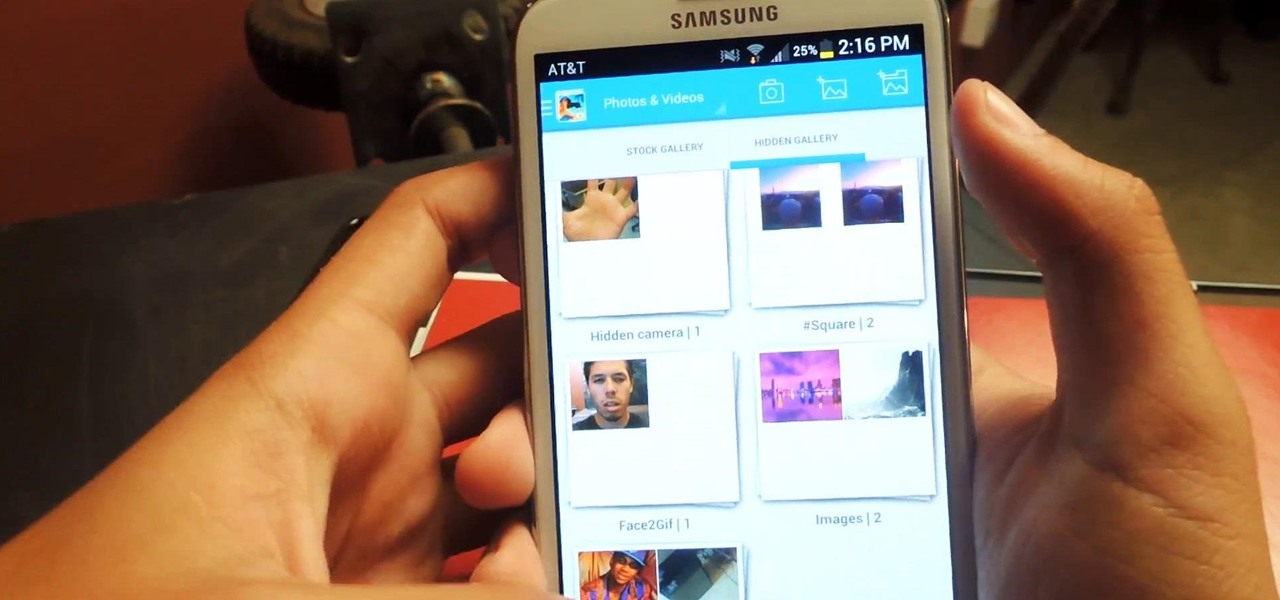
Regardless of how great your friends and family are, they'll more than likely go through your photographs if they had the chance. Hell, if my friend were to leave his/her phone lying around, I'd go through it—no doubt.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

According to WitsView, 8-inch displays will rule the tablet scene this year at 11.9% market share, compared to yesteryear's 2.6% market share. By year's end, it'll be almost 18%.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

Breaking into a low-security lock is easy (and thus, why it's the subject of a googolplex number of Youtube tutorials made by mischievous prepubescent boys). But add a combination number to a lock and your lock-picking life gets much harder.

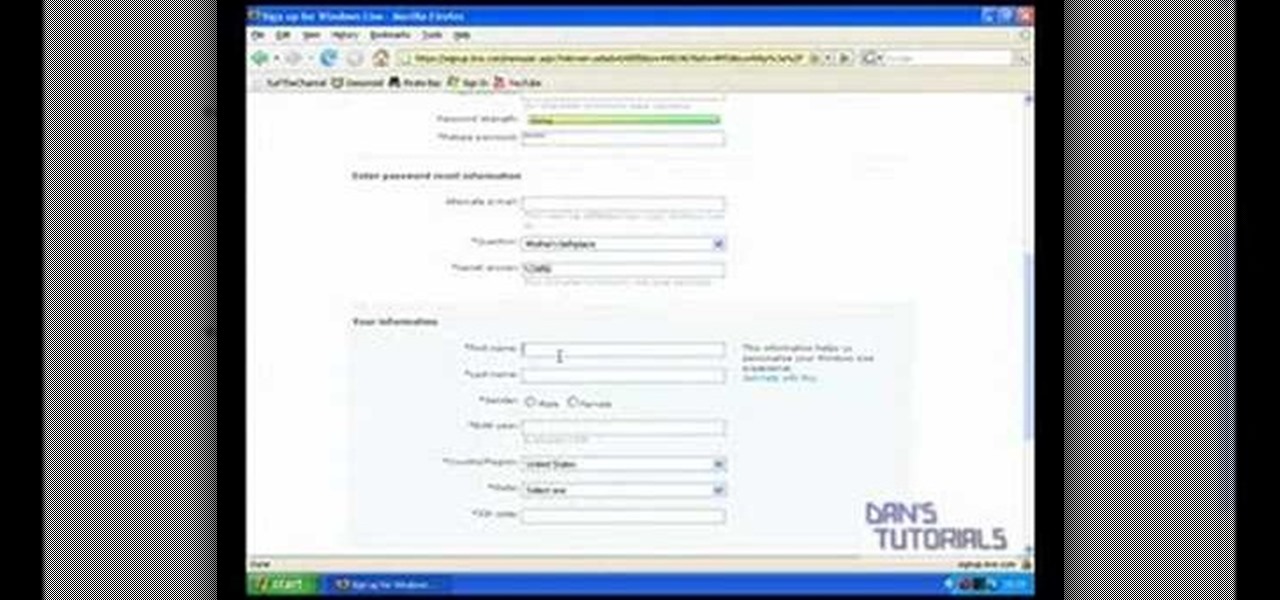
This tutorial shows how to create an email account in Windows Live. Use Google search to find the Windows Live Hotmail page. When you get to that page, click on the button that says, "Get it Free". On the next page, you can choose your email address, ending with either @live.com or @hotmail.com. If the email address is already in use, pick something else or add some numbers. Next, choose a password. There is a bar that shows how strong your password is. You can set a security question that ca...

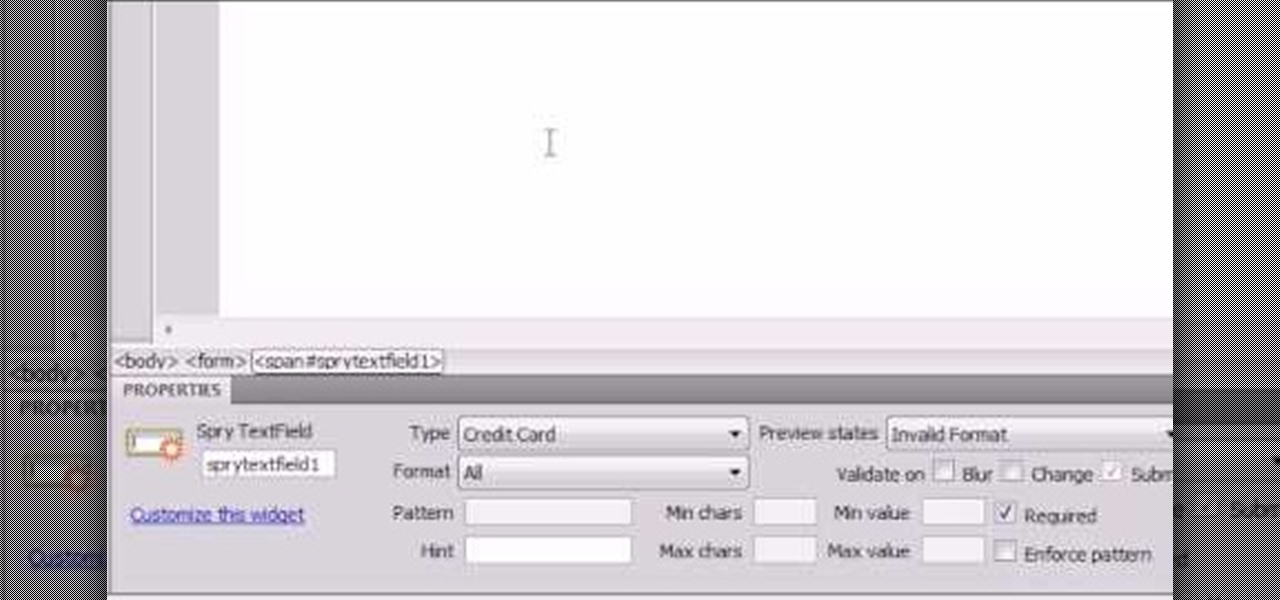
Here the New Boston shows you some tips about using the Spry Validation Text Field. To begin you will go to the Spry Validation Text Field, on Dreamweaver CS4. Looking at the bottom of the page notice the various options that are available for Properties. You find drop-down boxes for Type, Pattern, Minimum or Maximum values, Required, Enforce pattern, Format, Validate on, Blur or Change and Preview States. You can see the types of text available for validating by left mouse clicking the Type ...

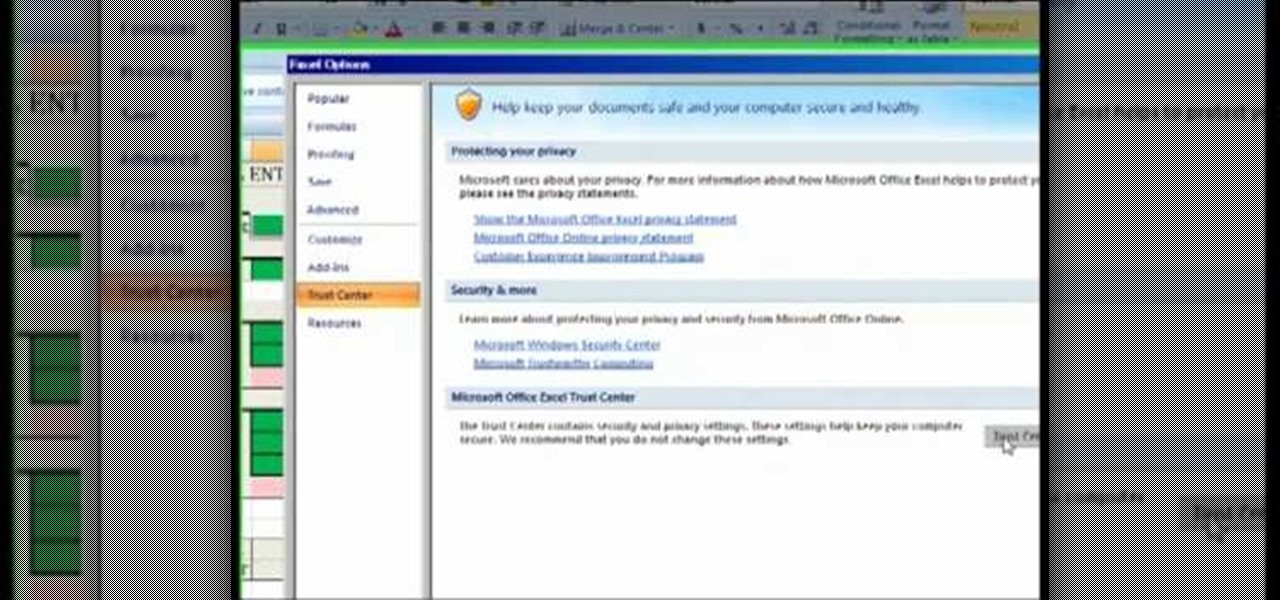
The Costsheet demonstrates how to enable macros in Excel 2007 to run correct spreadsheets. First, open up the spreadsheet. Make sure that the macros are enabled. If they have not, enable the macros by placing them in a trusted source by saving them in a particular folder. You can also choose to recognize the publisher as a trusted source. Click the office button and scroll down to Excel options. Click on the trust center option and go to trust center settings. Then, view the trusted locations...

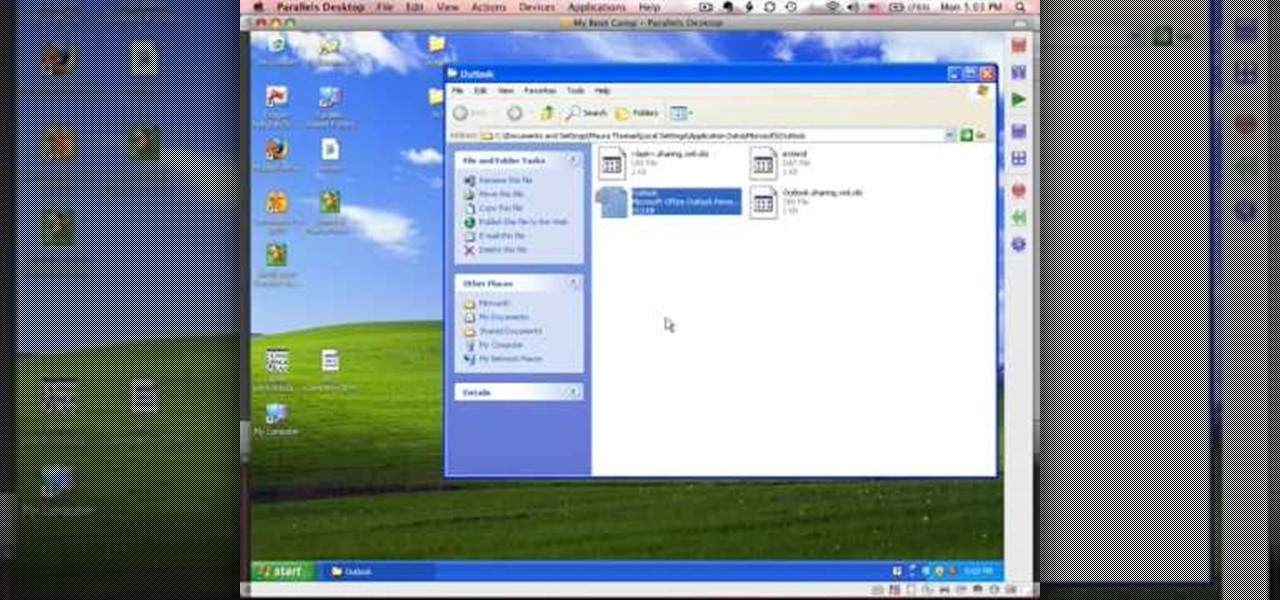
This tutorial describes how to backup the PST file of Outlook.

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

In this video the girls of Sugar Walk Catwalk dot com teach us how to walk in high heels. First you need to find the right heels, and there are three points you want to look for. First the fit of the arch. Second, that the ball of your foot is secured in the bottom. And, thirdly, test the heel balance. If the heels aren't working for you in the store, it's only going to get worse in real life! Once you've got a pair of shoes, we're shown how to make them better with foot petals or gel pads to...

This is a video that teaches you how to connect a Nintendo DSi to the internet. In order to connect a Nintendo DSi to the internet, you have to do this.

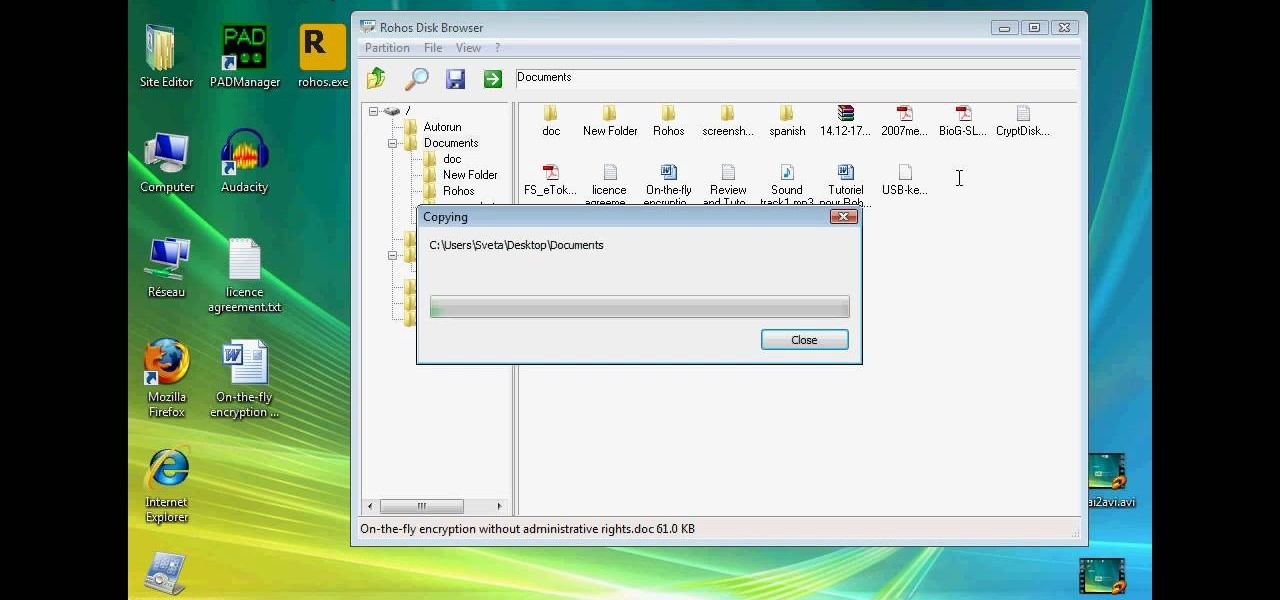
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).

A series of videos that help show just how tough it can be to install a remote car starter. Unless your an electrician or a technician, this complex job can result in a variety of electronic failures in your car including prevention of actually getting into your car as well as prevent you from driving home.

Professional truck driver, Yesterday Irmani, teaches us how to tie a time honored, weight sustaining knot, for transportation purposes.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a motorcycle camera mount for under five bucks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to homebrew and hack the PSP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.