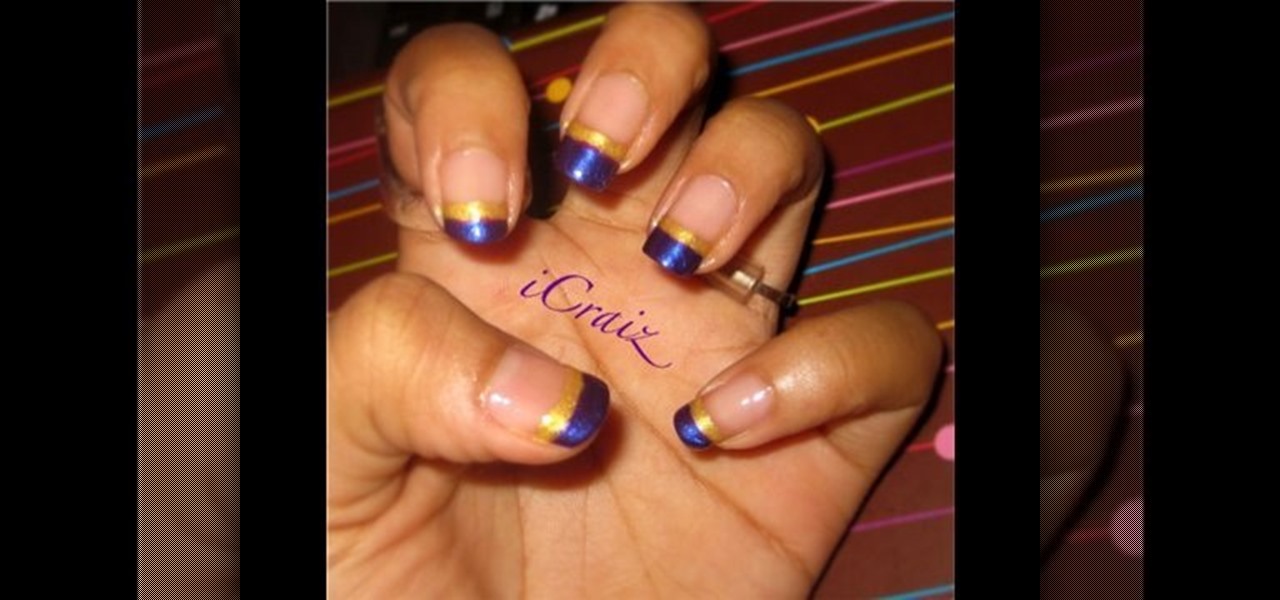Security is tighter than ever in U.S. airports. From the recent instigation of the hotly debated full-body scans and pat-downs to the TSA limiting every ounce of body lotion you bring, it's hard to make it through the security gates without some major airport hate.
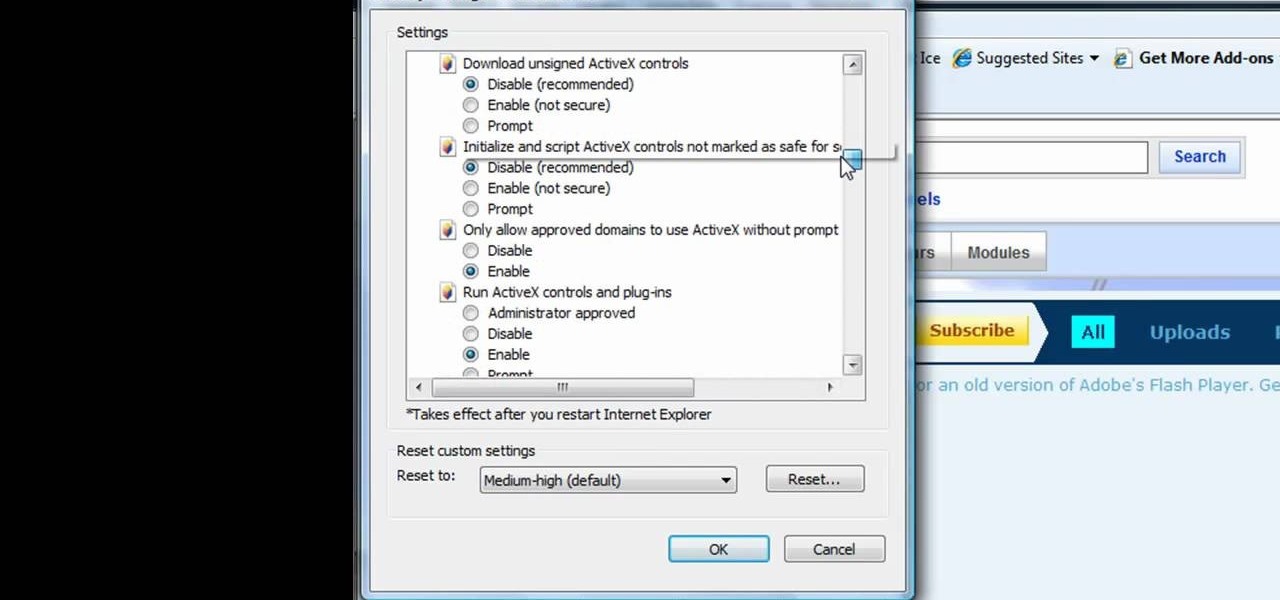
This tutorial shows us how to enable JavaScript in Internet Explorer. First, go to the top right of IE and click "tools". Then, click "internet options" and then go to the security tab. From here, select your security level that you want by clicking "custom level". Scroll down to the bottom and find the tab that says "active scripting" and make sure it's enabled. Click on "ok", then refresh the page that you are on. Now you should be able to watch videos and use anything that uses JavaScript ...

The difference between an amateur piece of jewelry and a professional one often lies in the details. Almost anyone can link chains together into a necklace and add small floral baubles, but the professional will take care to make sure the baubles are attached almost imperceptibly and the closure blends in with the rest of the necklace and also won't budge.

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...
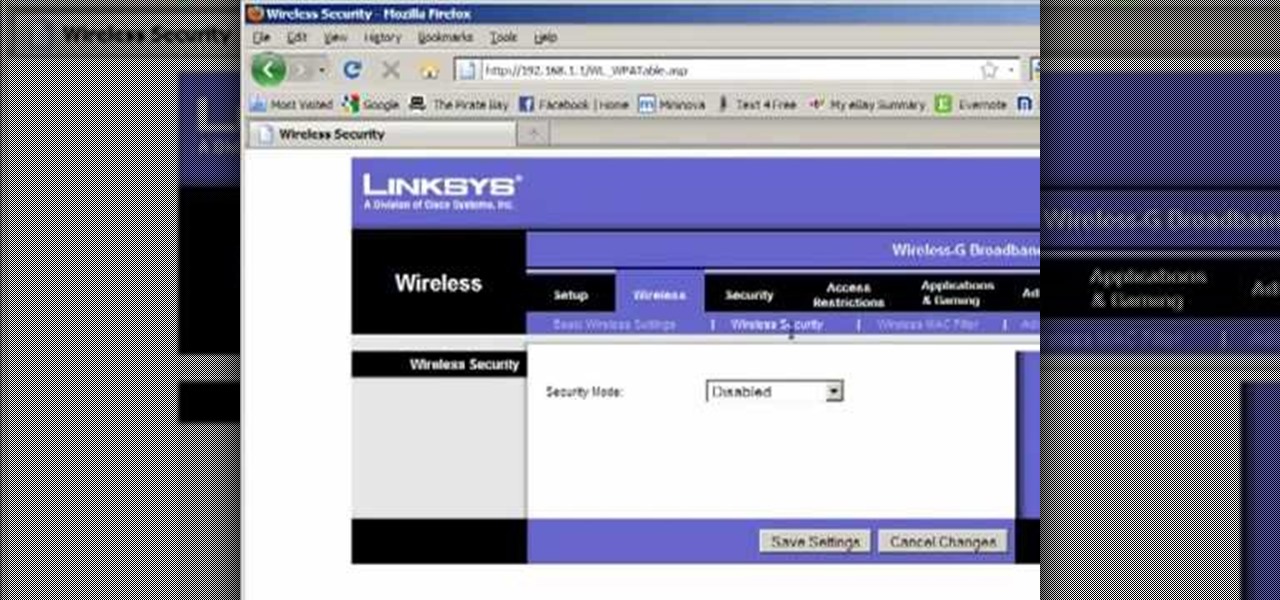
Llewyn demonstrates how to configure your router for Wifi. Access the router by opening up your internet browser and typing in your router's IP address. That will bring up the router configuration page. Now, click on the wireless tab. You can set the wireless network mode to accommodate your computers. As a precaution, set the mode to mixed for greater flexibility. Set your wireless SSD broadcast to enable which will enable your wireless card to actually see the webpage and the internet. You ...

This video shows the method of getting past blocked sites and opening them using proxy servers. The method shown is useful when the sites are blocked using another site. In this case it is 'www.lightspeedsystems.com'. It can be done using proxy servers. In the case shown it is 'treesniff.com'. The URL is typed and we choose the option of 'Continue to this website'. Press 'No' for the security information. After this the page of the proxy server is displayed. Type the name of the website you w...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to program a USB development board for cheap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In this video tutorial, you'll find a step-by-step guide to how a n00b hacker (like you?) can get usernames and passwords easily through one of the security flaws of the Ethernet ADSL router. More than half of Internet users never change their default password which makes this "hack" easy. Take your time to read the text on the slide. For more, and to get started testing the security of your own Ethernet ADSL router, watch this hacking how-to.

Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find.

A killswitch is exactly what you think it is: A switch that kills an operation in an emergency situation when the operation can't be shut down in the usual manner. It shuts your operation no matter what the consequences.

Back in the 1940, a lot of people called women Dames. It was okay then. You might not get away with it now. One thing you can't ever called a woman is an imbecile, with or without the French accent. But you can earn the Femme Imbecile trophy in the A Slip of the Tongue DLC for L.A. Noire on PS3.

Christina Hendricks has (relatively) short hair and pulls off the bob look beautifully. But that doesn't mean that longer-haired girls like you and I can't achieve bob edginess.

In this video, we learn how to do Andres Iniesta's signature soccer move La Croqueta. First, while you are on the field and have the ball, you need to turn and control it. Pay attention to those around you and move around them. Move the ball from left to right around the people coming towards you. Attack the open space to free yourself up and get away from crowds of the opponents. Once you do this, you will be close to the goal. Finish off the shot by kicking the ball into the goal. From here...

We don't know that we'd want to live a burlesque lifestyle - stripteases, pole dances, outrageously sequined costumes - but we do know we love ourselves a pretty burlesque hairstyle. After all, there is no better way to feel drop dead gorgeous and glamorous than with a romantic, retro 'do.

Want to play Bobby Darin's "Beyond the Sea" on your ukulele? Learn how with this free video ukulele lesson from Ukulele Mike, which presents a complete breakdown of the song and its chords. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For m...

La Carmina and her Scottish Fold cat, Basil Farrow, demonstrate how to make cute heart and star-shaped hard-boiled eggs... using bento molds from Japan!

Check out this video review of the 2-player abstract strategy game, Hive. Also, watch this how-to for tips on actually playing Hive. Oh la la! Hive is great if you like bees.

Check out this video to learn how to talk about "la nourriture," or food, in French.

Check out this video to learn how to talk about "la brocante" in French.

DJ Co-op and DJ Hunnicutt get disco dance lessons from Ming. Learn how to do the L.A Lock.

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

The Ironkey is a high security thumb drive designed to provide strong AES encryption, tamper resistance and other security services. Some of the topics covered will include: How is the drive mounted without admin privileges in Windows? How is it mounted in Linux? How does the "Self Destruct" feature work? What is Secure Sessions? How is the Ironkey better than just using Truecrypt? For answers to these questions, take a look. Use the Ironkey High Security Flash Drive.

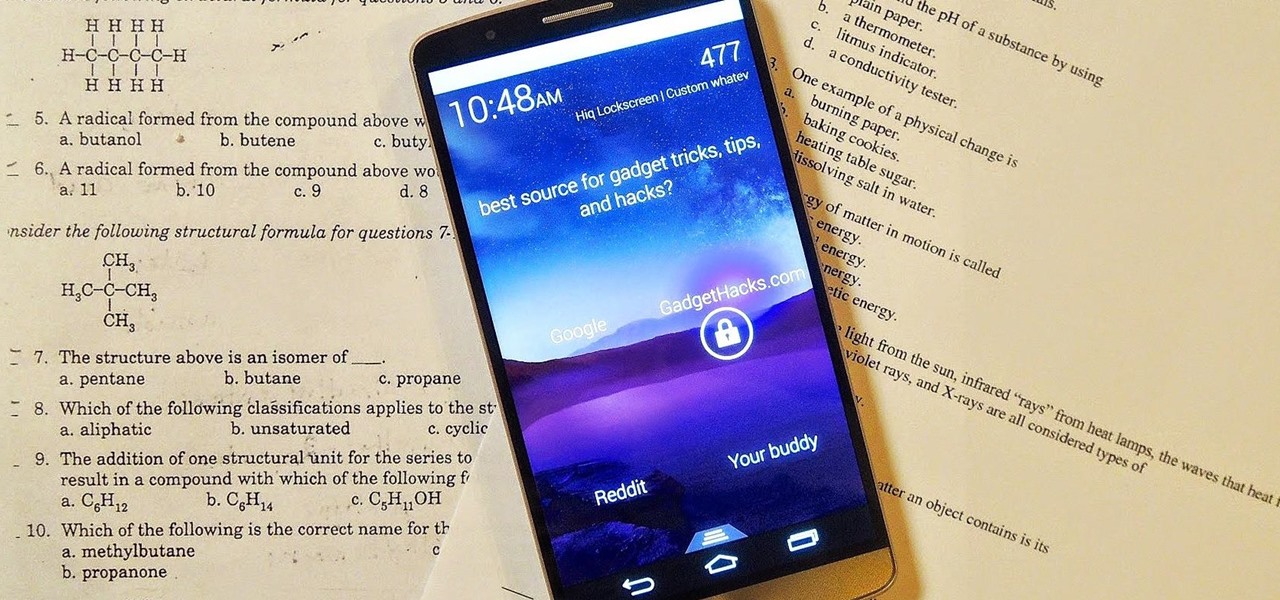
There are countless lock screens you can apply to your Android device, but very few offer more than just quick access to apps or advanced security functionality. Since you probably unlock your device a gazillion times every day, why not use this to your advantage and let it teach you something new?

In this tutorial, we learn how to create "viva la diva" lip art. First, prime your lips and blend it out with clean fingers. Next, take your favorite type of lipstick and then use lip liner on the edges. Blot the lipstick on the back of your hand, then apply the lipstick again. Next, grab rhinestones and apply them on your lips using a q-tip and Duo glue. When you are done with this, apply a clear lip gloss to the top of your lips. This will give you a glam look with beautiful rhinestones on ...

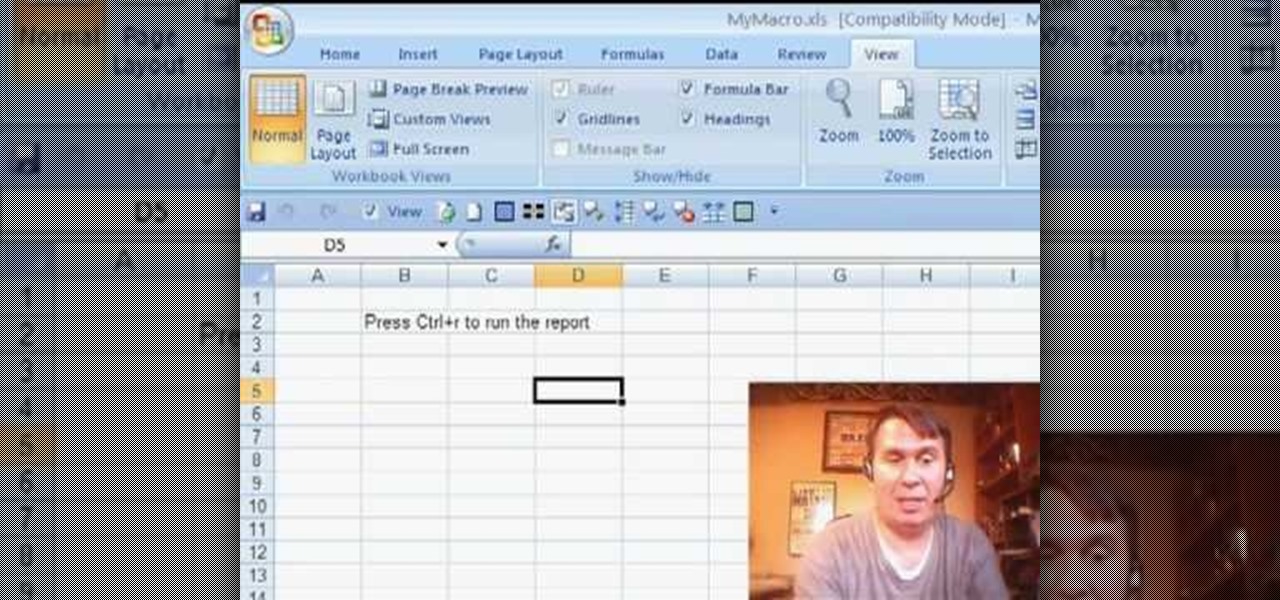
Some times when you upgrade your Microsoft Excel software to Excel 2007 your old macros may stop working. Some times this may be due to the settings and by enabling the macros you can get your old macros to work. Macros are turn off by default in Excel 2007. You can turn this on from the macro security settings. But the settings option is it self completely hidden. You cannot find it in any of the tabs present on the top of the program. Even the macros option present in the view tab has no se...

In this video, they show you how to do French nails with purple and gold tips. The nail polish used for the gold color is Ooh La La. The nail polish used for the purple color is N.Y.C. You also need a clear nail polish for a base coat as well as a skinny brush in order to paint the French nails with it. The base coat used is a Maybelline nail polish. You first apply a base of clear nail polish. Then you apply the purple nail polish to the tips. Using the brush, you apply the gold stripes. Fin...

Lauren, AKA QueenofBlendingMUA has joined the ranks with the other YouTube beauty gurus. Lauren is a makeup artist with a large collection of eye makeup & nail art video tutorials. Her eye makeup look span from everyday makeup to creative, more expressive party looks. Her nail art/ manicure looks are also lots of fun. Check out this nail art tutorial video to learn how to create a neon orange and dark blue nail art design. Search QueenofBlendingMUA on WonderHowTo for more beauty videos.

The C-Walk, AKA Crip Walk, originated in LA's Compton in the 70's. It is a hip hop dance started by the Crips gang. Originally meant to be a walk, not a dance, it was a way to identify whether you were a Crip. Watch this instructional video to learn how to do the Forward V. This move is hard to explain. It's like (for me anyway) going into a sideward V, and then a stepback.

The C-Walk, AKA Crip Walk, originated in LA's Compton in the 70's. It is a hip hop dance started by the Crips gang. Originally meant to be a walk, not a dance, it was a way to identify whether you were a Crip. Watch this instructional video to learn how to do the heel toe move. There are many variations of this move, and it can be a bit tricky to learn.

Want to learn how to play Coldplay on the guitar? With this tutorial you can learn how to play "Viva La Vida" by Coldplay on the acoustic guitar. This version is a simplified version of the song and is not exactly how Coldplay plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Viva La Vida" by Coldplay.

In this dance how to video, Larry Payne demonstrates the sissone a la seconde ferme (to the second position closed), then en avant (in front), finishing with a "changement." The step sissone is named for the person who invented it. ballet move. This is a basic move for the beginning ballet dancer. Follow along with this dance tutorial and you can do the sissone a la seconde ferme ballet move.

You've all probably heard about Apple's attempts to thwart iPhone 4 users from opening up their own devices, thanks to their sly maneuvers in switching out everyone's screws with those funky pentalobular screws. But one thing Apple will never learn— they will never have complete control. Where there's a will, there's a way. And if someone wants to fix their own iPhone or modify it slightly, they're going to do it, regardless of what screws bind it together.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.