
News: Renault Trucks Tests HoloLens to Visualize Quality Control in Engine Assembly Operations
French manufacturer Renault Trucks is looking to the HoloLens to improve quality control processes with its engine assembly operations.


French manufacturer Renault Trucks is looking to the HoloLens to improve quality control processes with its engine assembly operations.

Advertisers must love when their commercials go viral. Take for instance the Esurance commercial where an elderly woman completely misunderstands Facebook jargon.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Over the past eight months, ten infants at UC Irvine Medical Center tested positive for the same strand of methicillin-resistant Staphylococcus aureus (MRSA). Despite the danger of this superbug due to its high resistance to most antibiotics, this information was only released to the public on Thursday. Thankfully, all ten babies survived and are currently healthy.
After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

Every day the young world of mixed reality is creating new ways for people to work with with computers. We are looking for, and finding, new ways for these head-worn computers to understand what we tell them. Sometimes it is with our hands, sometimes it is where we turn our head, sometimes it is what we say. In the case highlighted below, it's where we walk.
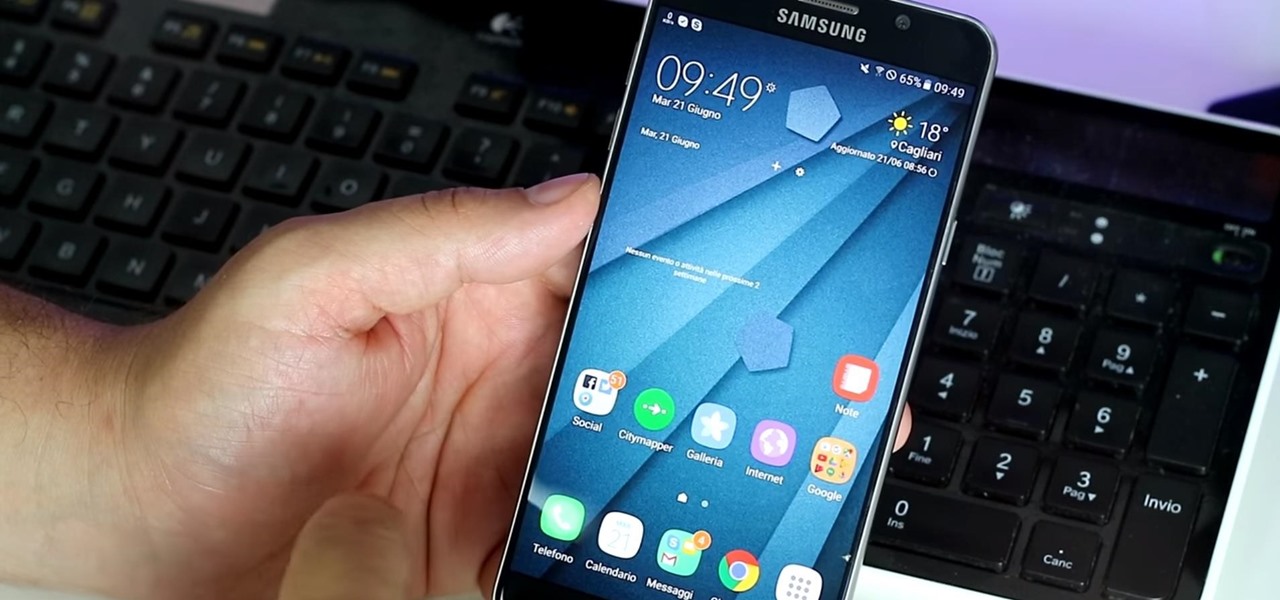
It looks as though Samsung will continue to tone down the look of TouchWiz, according to a leaked look at the newest "Grace" user interface for the upcoming Galaxy Note 7. HDblog, who acquired the leaked UI, shows off the beta version of the new skin in their video below.

For generations, parents have been struggling to come up with innovative ways to get their kids to eat their vegetables. They'll cut them into fun shapes, bake them in cheese, batter, and deep-fry them.

With the high rate of obesity in the United States, it's fantastic to see the massive wave of fitness tools available, even if it's just a trend. And with the companionship of your Apple Watch, keeping track of your progress or fitness goals has never been easier. As my LA Fitness intercom repeatedly announces, "What gets measured gets improved." (Corny, but very true.)
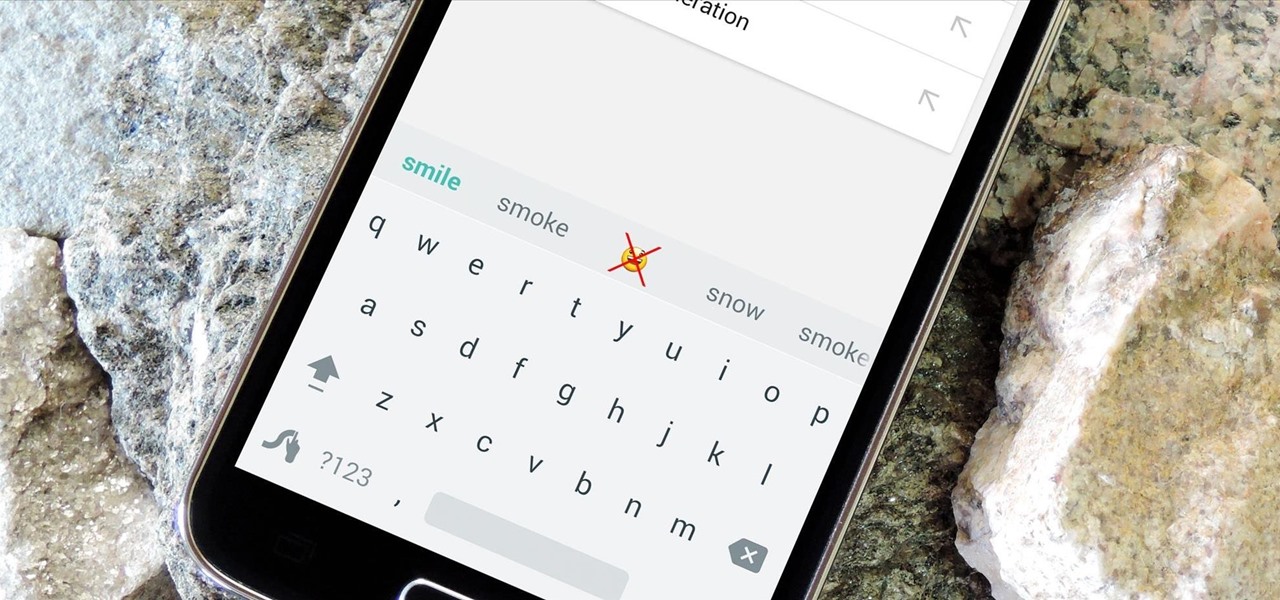
As the granddaddy of all gesture-based keyboards, Swype has seen quite a few updates in its day. A recent version bump, however, added a feature that has been universally panned by Swype users.
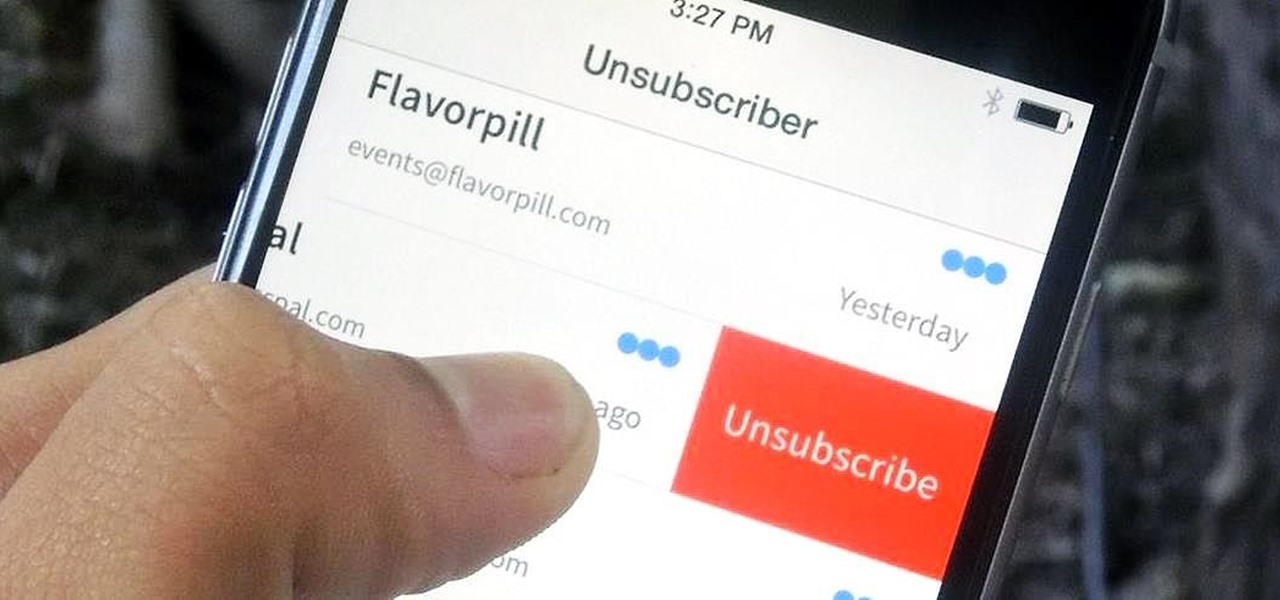
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.
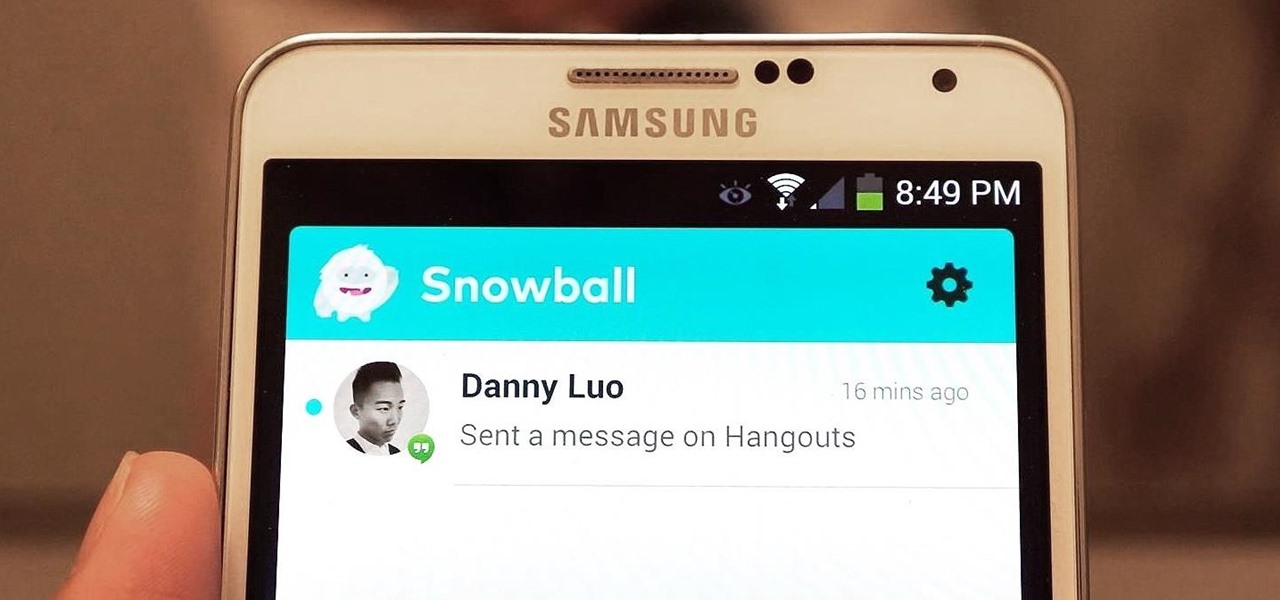
Your favorite instant messaging service might not be your friend's preferred choice of communicating, and your sibling might prefer yet another. So when they send you messages via different apps, it's like having one address but multiple mailboxes on a single porch.

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.
While it may not serve much of a purpose here in sunny Los Angeles, it's still a good idea to keep constant tabs on the weather forecast, because you don't want anything to rain on your parade.

One good thing about having friends who are constantly on their phones and tablets is it's easy to figure out what to get them for Christmas. Everyone hates getting gifts that just sit around, so it's always nice to get something that improves an item you use on a daily basis.
There may only be a few hardware buttons on your Samsung Galaxy Note 2, but when they're not working, your phone might as well be a doorstop. A few years back, I was texting while walking to class and a student on a bicycle crashed into me. My phone was flung thirty feet—straight into a puddle. I picked it up and checked for damage, but everything seemed okay. The biker apologized profusely, but nothing was wrong, so I told him not to worry about it and proceeded to class.

TIFF 2012 Wrap-Up - Pounds Personally Gained: 4.5

What is Internet Download Manager? Internet Download Manager (IDM) is a tool to increase download speeds by up to 10 times, resume and schedule downloads. Have you ever wanted to increase you download speed form 4kps to 80kps? If you answered yes then you need Internet Download Manager. It can and will increase your download speed so you can get the files you want quicker and easier than ever before.

Access your computer's BIOS settings

This video will show you how to disable secure virtual memory in Mac OS X. From the top left of your screen click on the apple icon. Click on system preferences from the pull down menu. Click on the security icon. Click on the image of the closed lock from the bottom left of the window so that you can change make changes.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

Smash Bros LA, also known as SBLA, is a Jerk dance crew from Los Angeles, consisting of six members who have taken their jerkin' skills to the Interweb with this tutorial on Jerk dancing. Within the video, SBLA go over how they perform ten jerk moves, and how you can do it the easy way. Moves include: The Reject, Dip, Pin-Drop, Spongebob, and Berries & Cream.
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

A Google trick to bypass computer security at your school and access blocked websites. Access blocked websites using Google.

How to bypass the web security at your school to go to restricted websites. Access any website at school.

Dress up like the Omish & block traffic in LA or NYC .

You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your account security.
The newest feature for Pixel smartphones puts a home theater in your pocket. Spatial Audio outputs sound that appears to come from in front of and behind you, adding a new level of immersion to your streaming video and music apps.
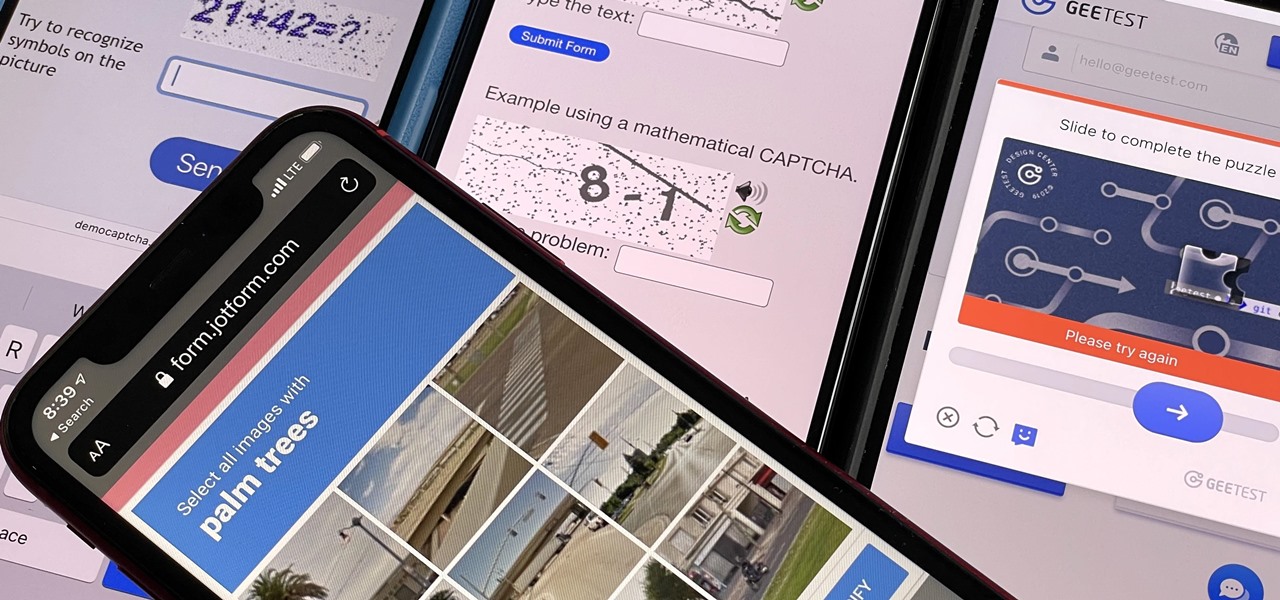
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

The emergence of Microsoft's HoloLens 2 as a cutting-edge US Army tool has focused a spotlight on the marriage between augmented reality and the military.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.
Apple released the newest update for iPhone, iOS 14.5.1, today, Monday, May 3. The update (build number 18E212) is the first since iOS 14.5, which Apple made available one week earlier on Monday, April 26.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.
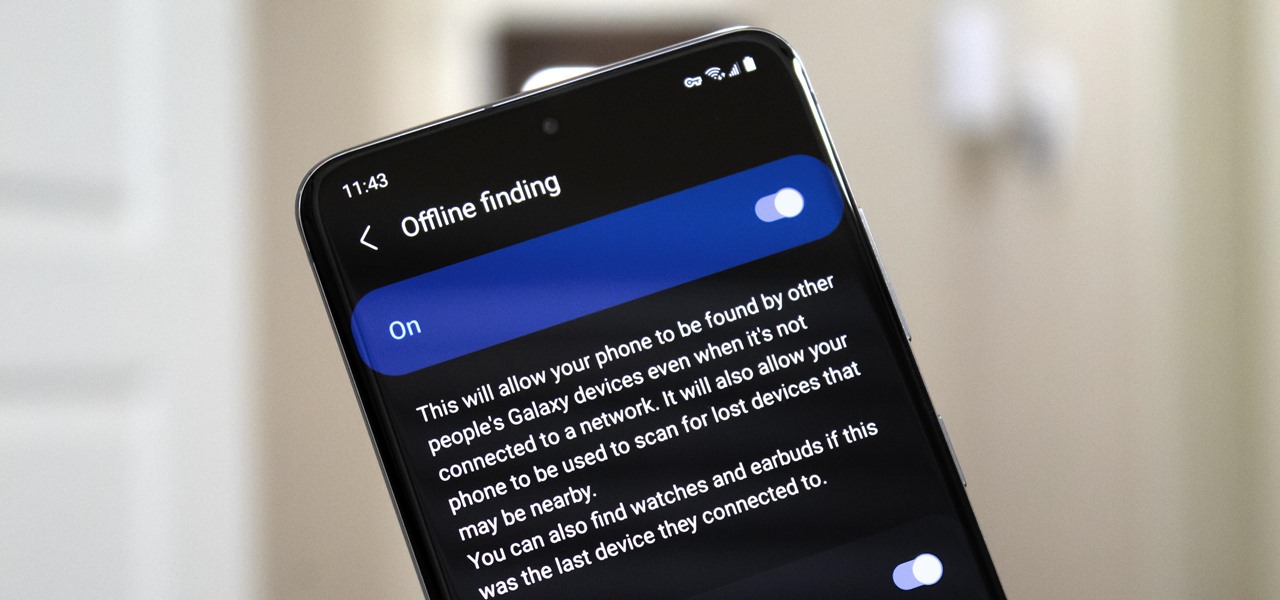
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.