If you have children who are still your dependents and have been living in your household for at least half of the year, and have their own social security number, you can actually get a major tax credit with a simple worksheet. In this video you will learn the requirements for the tax credit and also how to fill out the worksheet and calculate your credit.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.
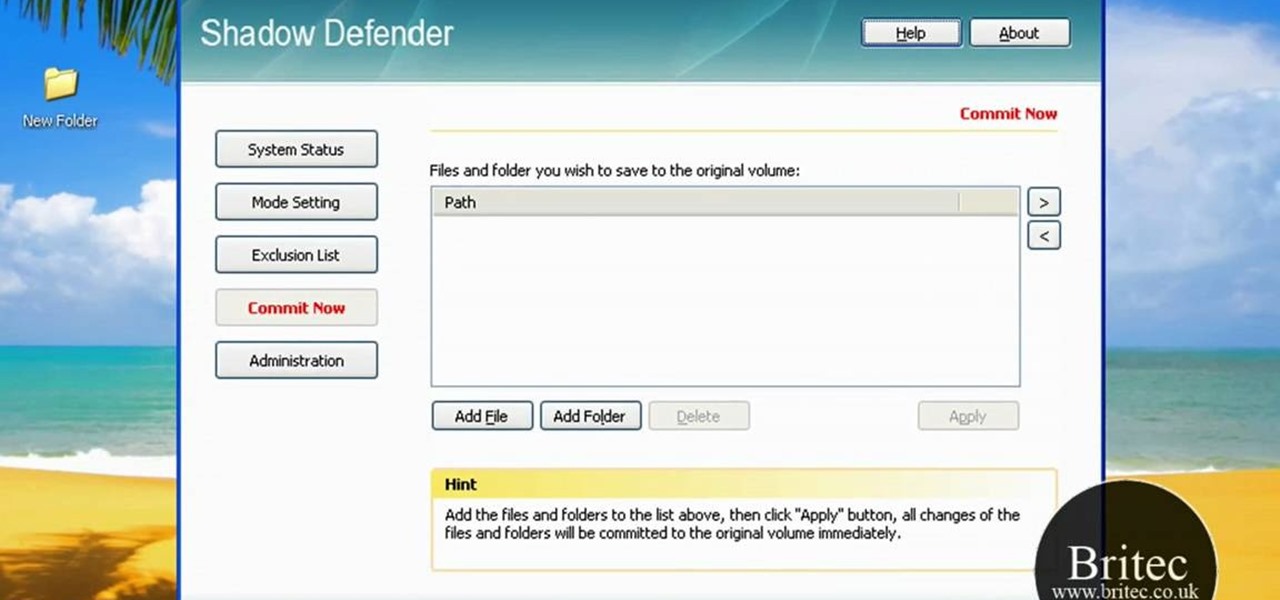
Looking for a security solution for your Microsoft Windows PC? With Shadow Defender, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions on how to get started using Shadow Defender to protect your own desktop computer or laptop, take a look.
hether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 52.5th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about macro security. For more information on how to use macros safely, watch this free video guide.

Take a folder and organize documents based on the actions required. Actions:
What do you do with a password protected WinRAR archive? You hack it - naturally. And how do you hack it? First, download RAR Password Recovery v1.1 RC17 then follow along with this video to crack almost any WinRAR password. So much for security.

Do you sometimes wish you were an only child? Yeah, so does your irritating little brother or sister.

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on an Oracle database. To see how to pop a shell from within Oracle or even perform a port scan from the database itself, watch this hacking how-to.

AccessDiver is a website security scanner. It incorporates a set of powerful features that will help you to find and organize vulnerabilities and weaknesses in your own site. This video tutorial presents a guide to its use. For more information, as well as to get started using AccessDiver for yourself, watch this video tutorial.

In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more

Did you know that field templates can be applied two different ways? And that the two "edit" buttons on the main interface tie directly into how these field templates are used? This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite discusses these topics and how to control such permissions through security roles.

There is a security flaw with any Apple iPhone running firmware version 2.0.2. This flaw potentially gives a person access to your email account and contacts when you have your iPhone locked. This video demonstrates a simple, but impermanent, fix for stopping others from accessing your private information. To protect your own Apple iPhone, watch this tutorial.

Dogs naturally want to have a den, so a crate gives him his own space. Puppies will get security and comfort from a crate. Because a dog will not want to go to the bathroom where they sleep, they won't make a mess in their crate, making it useful for housebreaking a dog. Watch this video pet care tutorial and learn how to crate train a dog.

In this how-to, Gary Rosenzweig of MacMost.com takes a look at best practices for making and storing passwords. You should have a different password for every account, for example, use secure passwords and store them in using a security utility. Learn how to store your passwords securely with this tutorial.

I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

This tutorial gives you a basic overview of how to build a Parabolic WiFi Booster that will increase you router's range as well as narrow the signal path for added security.

Professor of RVing, Jim Twamley talks about lock security and shows you how to replace an RV entry lock.

How to get around your school or home's computer security to view restricted webpages.

So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

This Video demonstrates how to install multi channel (4,8,16) power supply for security camera and CCTV installation.

Watch this video to learn how to make a radio controlled camera rig that can tilt and pan like an expensive security camera. This is an amazing tool for movie making! Stick to your budget.

Here is the movie trailer for "Les Predateurs de la Nuit" Check out Telly Savalas

Look Around in Apple Maps gives you a high-resolution 3D view of roads, buildings, and other imagery in an interactive 360-degree layout. We haven't had anything like this in Apple Maps since iOS 5 when Google's Street View was incorporated. Now, in iOS 13, seven years later, we have street-level views again, only better. But Look Around isn't available everywhere yet.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Until self-driving cars become mainstream, augmented reality might be the next big technology to hit your dashboard.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Classy and practical don't usually appear in the same sentence together, at leaast not when we're talking about hairstyles, but the descriptions certainly apply for this braided bohemian twist look. The French braid, which runs along the side and crown of your head, has a great princessy feel (a la Taylor Swift's favorite looks with its feminine symmetry, but it's also super functional at the same time, getting the pesky hair out of your face. Check out this video to get the how-to.

In this tutorial, learn all about headshots from producer and actress Kathleen Cooke. Kathleen will tell you all about what you need for a great headshot that will work in Los Angeles. From what to wear to how to pose, Kathleen will get you started. Chances are the headshots you have from back home won't cut it in LA, so make sure you have a great set and carry them with you - always!

In this tutorial, actor Shaun Pilkington offers his advice for choosing the best acting classes in Hollywood. LA is a town full of actors and there are many resources available, make sure you pick the best classes and become the very best you can be in your field.

Some watch Prison Break for the nail-biting drama, others tune in for the origami cranes. This video tutorial presents a complete, step-by-step overview of how to make a paper crane à la Prison Break protagonist Michael Scofield using origami, the traditional Japanese folk art of paper folding. For more information, and to get started making your own tough-guy paper birds, watch this arts-and-crafts guide.

Looking to add some fantastical creatures to your paper menagerie? Know how to make an origami crane? Make a sinister dragon (à la Smaug from the Hobbit or Saphira from Eragon) using origami, the traditional Japanese folk art of paper folding. This free origami video lesson presents complete instructions on how to make your own dragons from folded paper. For more information, and to get started making paper dragons yourself, take a look!

Ear muffs are handy for snow days (or in L.A., cold-ish days) and for eskimo dress-up days at school. Learn how to craft your own ear blankie with this tutorial, which shows you a cheap way to make ear muffs out of a coat hanger frame.

You might know that the best way to learn something is from a professional. But you might not have known that there are pro hoola hoopists. There are. And Marawa the Amazing, star of the La Clique cabaret show is one of them. In this hoola-hooping how-to, she'll show you how to get started with the ring-shaped toy.

L.A. Lakers superstar Kobe Bryant shares some tips with TIME Magazine's Sean Gregory on how he puts his best foot forward everytime he steps onto the court. Areas gone over in this video include: The proper grip & shooting form, attack the foot & sell the fake, the pull-up jumpshot, the art of the foul shot, playing to the opponent's weaknesses, getting in character, and stretching.

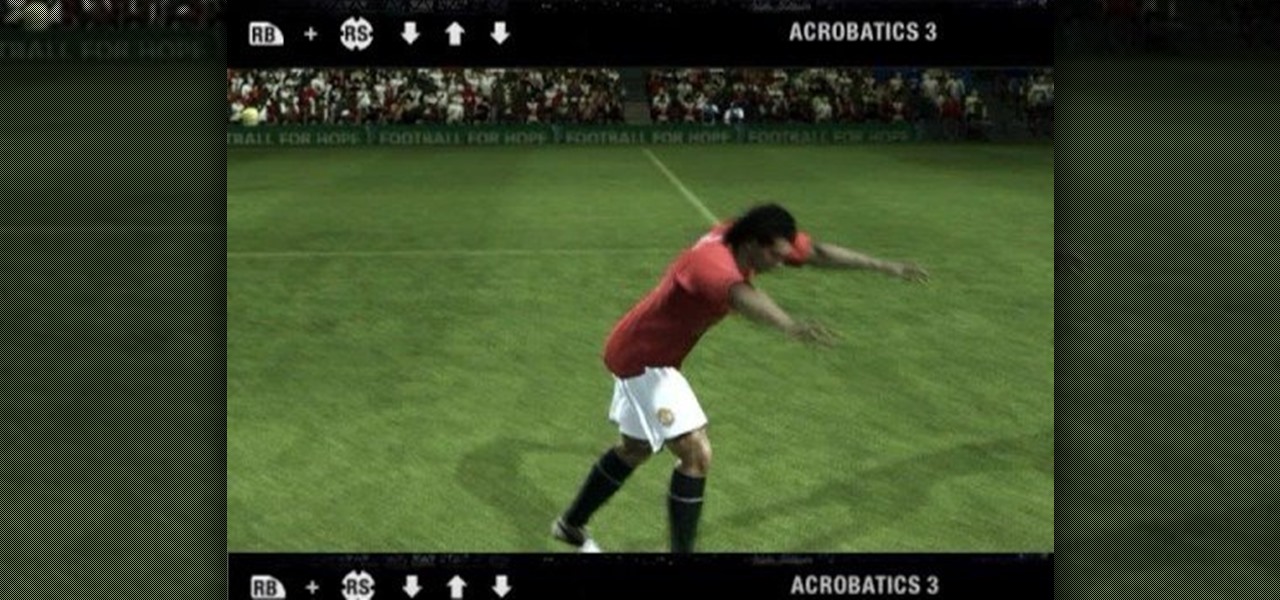
Learn how the do all of the Celebrations in Fifa 09. If you want to know the controls while playing, just go to the pause menu, then to Controls, and then to Celebrations Help. When you score make sure your celebration is that of a winner a la David Beckham. Check out the tricks to doing celebrations like 'Look at Me', 'Low Aeroplane', 'Fist Bump' and 'Acrobatics'.