People have been transforming mud into art, aka pottery, for thousands of years. This is not a new phenomenon, but often the finished product has a certain utilitarian aesthetic, such as a bowl or vase.

Selecting text on a touchscreen device has always been a major pain point. Those tiny little arrows that let you adjust the selection area are always too hard to actually adjust, making precision all but impossible. Then there's the issue of some apps not even allowing text selection in the first place, so the entire experience is basically a big mess.

Super Mario Bros. is one of the most renowned games in history. It helped resurrect a dying video game industry in the mid-'80s and still remains one of the best-selling video games of all time—one reason why the new NES Classic Edition is so popular and impossible to get these days. Its simple story of a plumber trying to rescue a princess resulted in a video game empire for Nintendo.

Apple's Live Photos is a cool feature that lets you turn ordinary pictures into a GIF-like animated photos. However, these images have some pretty big drawbacks: they live only in the iOS universe and can be shaky without a tripod.
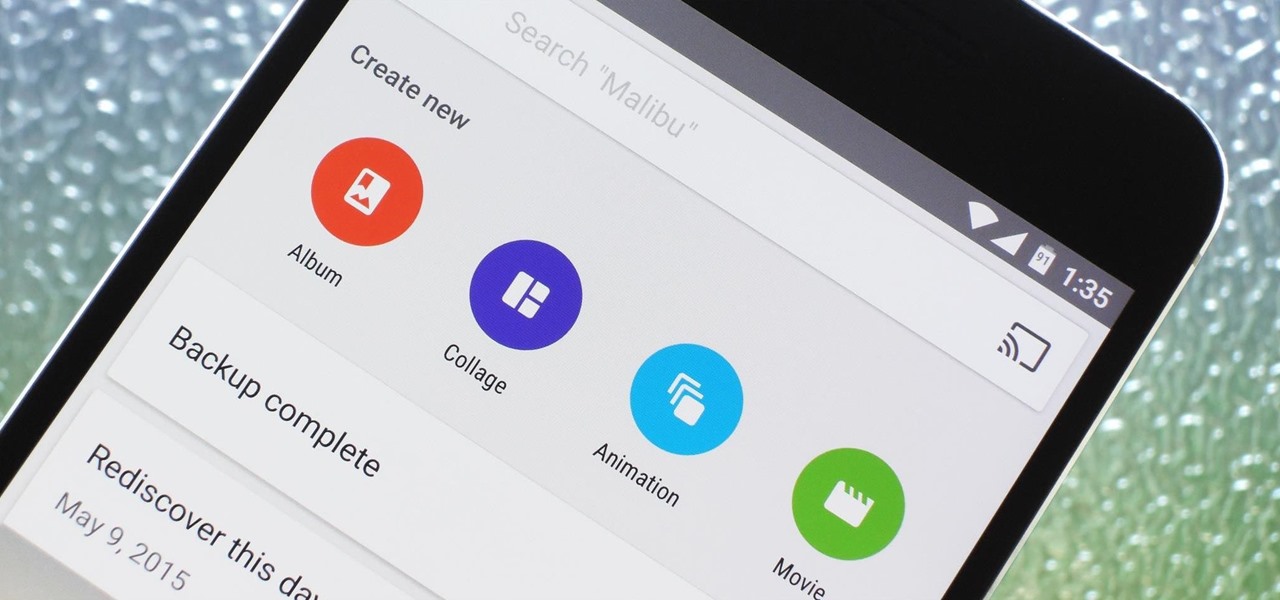
Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

The morning started out like most of them do: I was hungry, and it was time to chow down on some breakfast. However, this particular morning had me craving something besides the usual milk and cereal.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

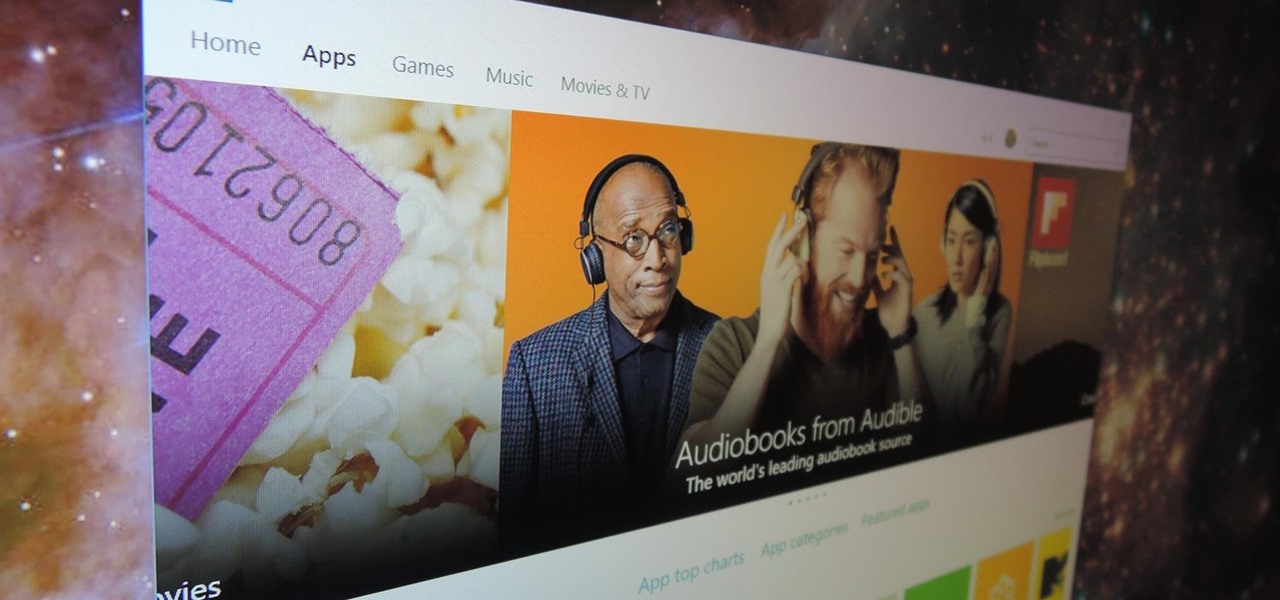
Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

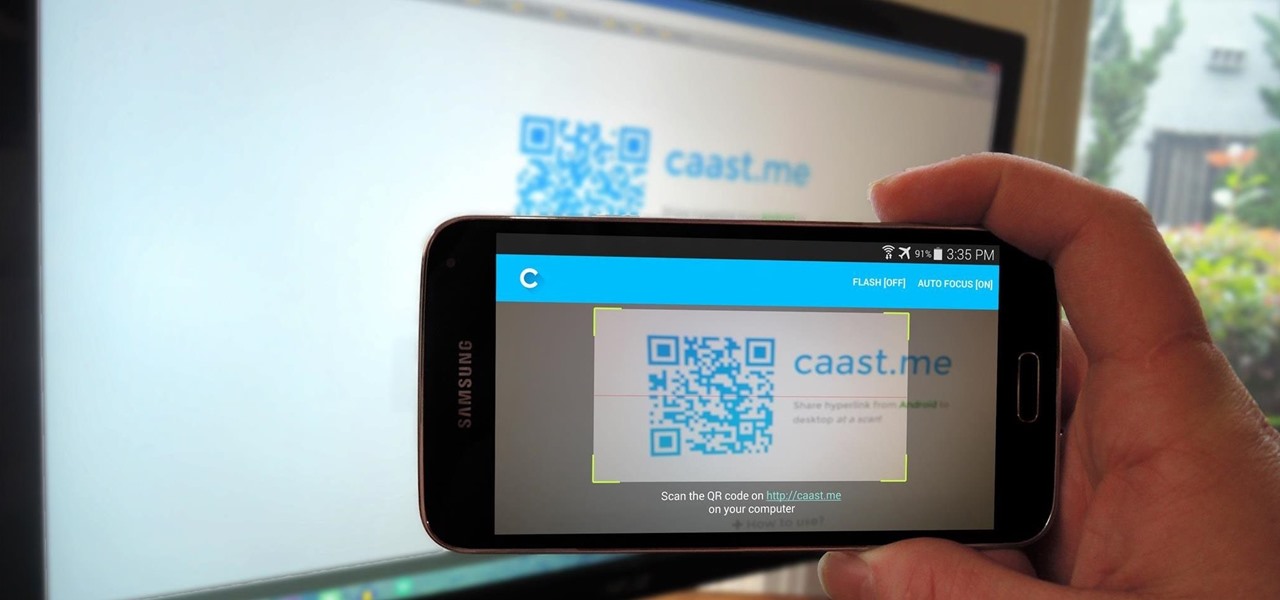
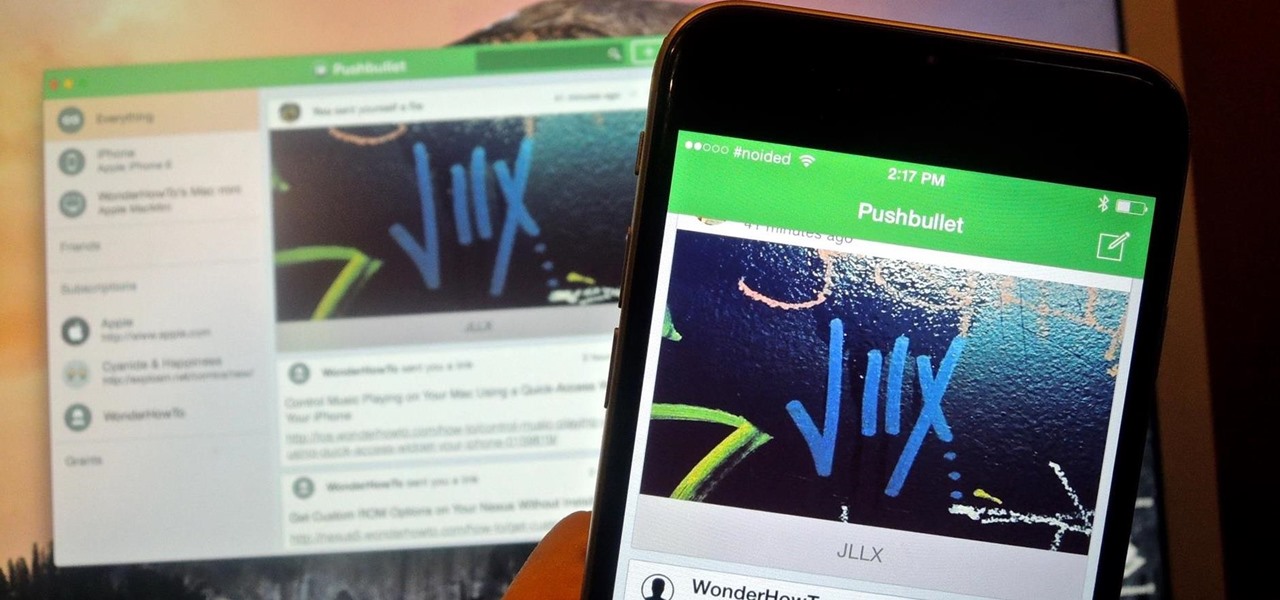
In today's world, we're constantly switching back and forth between all of our internet-connected devices. A PC may be great while you're at your desk, but the living room couch is tablet territory, and nothing beats the portability of a pocket-sized smartphone while you're on the go.

With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

Finding the right mix of custom ROM, kernel, and tweaks for my OnePlus One has left me flashing every new release I come across. This has led to many hours going through thread after thread trying to find the latest and best software out there for my phone. While I do enjoy the hunt, I would rather have a centralized location that covers all my bases, so that's why I have started using OnePlus One, an app by Alex Inthiaano.

Can't stand seeing your Facebook news feed full of peoples' good news and awesome accomplishments? Those oversharing friends are, in a sense, hampering their great news simply by sharing it. If you hold back and keep your accomplishments from friends, you might find even more success than if you'd shared with your support network.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

One of the Note 3's best features is Multi Window mode, which allows users to display more than one app on the screen at the same time, taking advantage of the large and high-resolution display.

Most people's fascination with social media these days is the instant gratification that can come with it. Whether you post an image on Facebook, Instagram, Snapchat, or Twitter, a minute or two later your phone will receive a notification informing you of a buddy or two who liked it.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

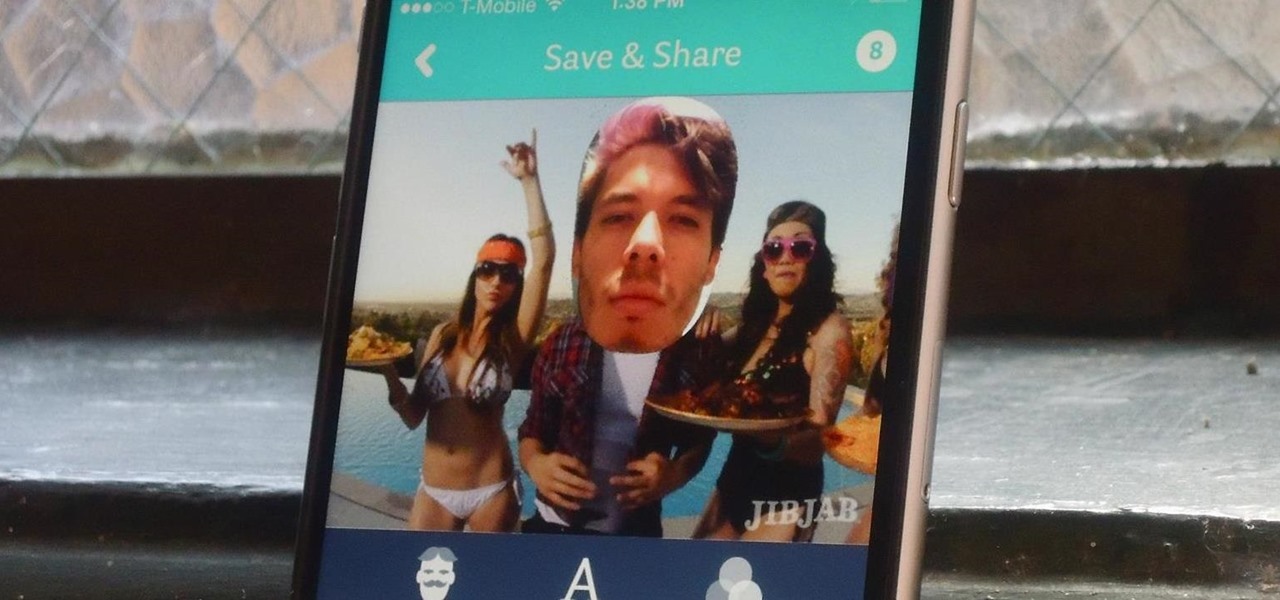
JibJab may not ring the bell, but you've probably seen one of their personalized videos. Using your own images, JibJab will place you first-hand into silly and usually musically-inspired videos that you can view online. Currently in beta, JibJib has made it's way to iOS in the form of personalized GIF creation. And if you're wondering, "why the hell would I want this", trust me, you'll love creating GIFs starring your and your friend's faces. Check out the guide below to get the app installed...

Apple's newest mobile operating system, iOS 8, is out for the general public, and we've got a rundown on the best new features you can use on your iPad, iPhone, and iPod touch. While there's not a huge visual change as there was from iOS 6 to iOS 7, there's still plenty of cool new features in iOS 8 to be excited about.

If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

Your heart is constantly work for you, yet you think nothing of it—and Samsung wants to change that. They stuck a dedicated heart-rate monitor on the Galaxy S5, they're putting one in the upcoming Note 4, and they're bound to slap one in every Galaxy device thereafter.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

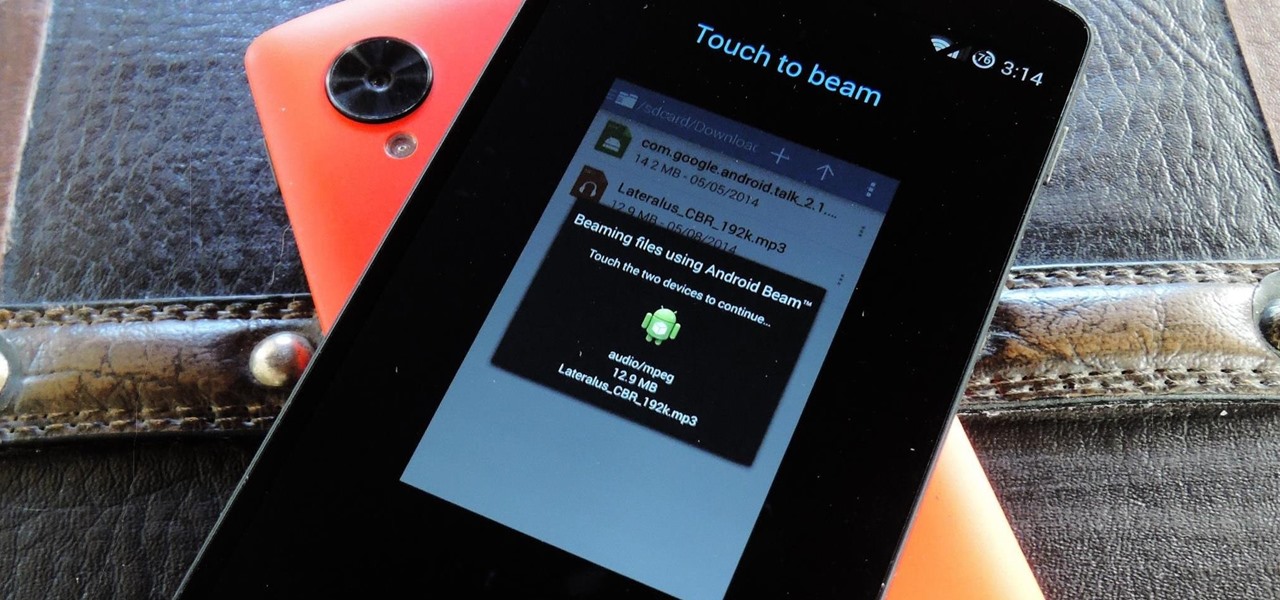
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

Popular photo-sharing service Snapchat has released a major update to both its Android and iOS applications today, bringing secretive chat messaging and live video chatting.

I can't begin to tell you how many times I've forgotten a special day or event. Once, I even showed up to class where everyone was turning in essays while I sat there empty-handed. Important dates sneak up on us. Especially one-time events we just can't wait for, like the release of a new movie when we count down the days, minutes, and hours.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

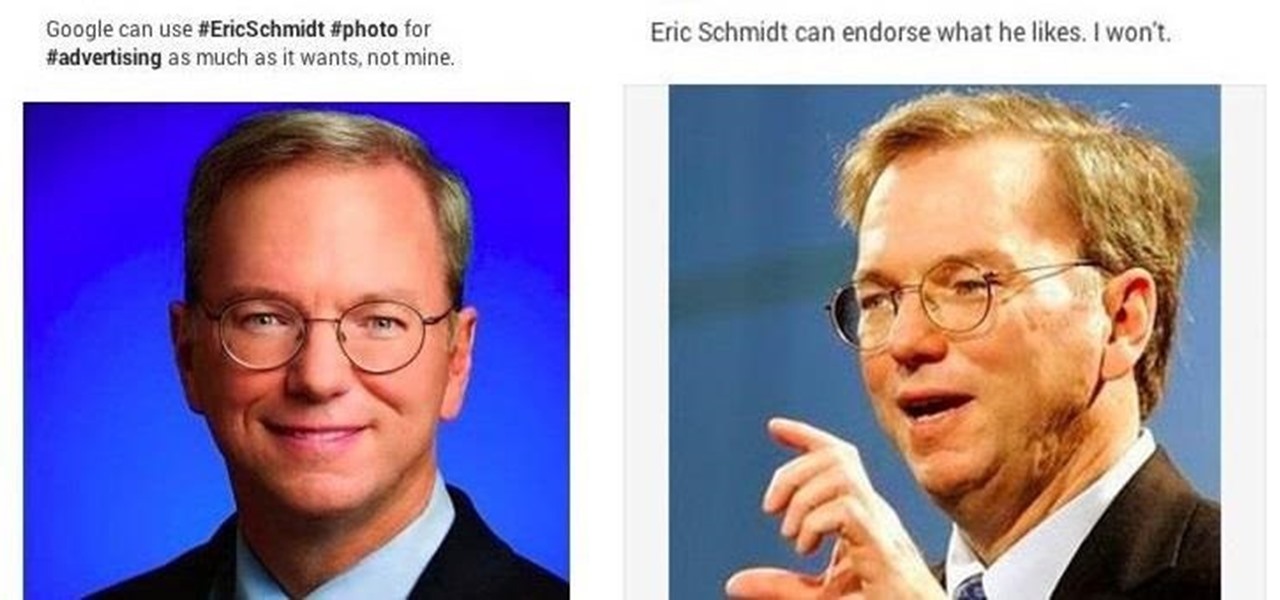
Every time you Google something or click on an ad in a YouTube video, Google gets paid. They are estimated to make well over $100 million a day, and I honestly think that's low-balling it.

I know it's a very first-world problem, but I really can't stand it. Email was invented to speed up communications between people across the world, even just across the office, yet when I'm on my super awesome iPhone running iOS 7, I have to go back and forth between my gallery and my email to send more than five photos at one time.

Writing longhand may boost learning and goal achievement, but that doesn't mean squat if you don't have pen and paper on you.

Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

In an effort to appease iPhone fans eager for an NFC-equipped device, an option that is available on many other smartphones, Apple created Passbook, their version of a digital wallet.

If you have a Mac, you've probably been anticipating the release of OS X Mountain Lion. If you have multiple Macs, you've probably been dreading the long process of downloading and installing it on all of them. Here's how to create a bootable backup disk and save yourself some time. Before You Start

First off—Happy Independence Day! Since it's the 4th of July, let's make this week's roundup short and sweet, so you can all get back to your holiday festivities.

Use your myTouch 4G to beam videos and music to your DLNA-enabled devices! In this clip, you'll learn everything you need to know to use the Screen Share feature. Whether you're the proud owner of a T-Mobile myTouch 4G Google Android smartphone or are merely toying with the idea of picking one up sometime in the near future, you're sure to be well served by this brief, official video tutorial from the folks at T-Mobile. For complete instructions, watch the video!