In this cardmaking tutorial, I share my love of paper flowers to make a double aperture card, using Anna Griffin papers and handmade flowers. I show you how I add the flowers symmetrically. This idea for a card looks stunning and the double aperture idea could be used with other nesting dies. Step 1: Items Used
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?
If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.

Learn how to paint nails perfectly - with nail hacks every girl should know, with my SuperWowStyle Nail Art Videos!

The best kept Indian hair growth secret shared! Learn how to grow hair long and fast & naturally!

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Cant find a smooth textured metallic polish? Check this quick & easy way to make your own metallic nail polish at home!

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

After my hard drive crashed recently, I lost everything. Old college essays, half-written stories, short films, and most importantly, all of the photos that I had saved from the past five years... all gone.

Have you ever been using your computer when a friend randomly decides it's time to start up a text message conversation? You usually have to stop what you're doing on the desktop, then go pick up your smartphone and respond to the text. Then, if your buddy replies with another message, you have to juggle back and forth between your mouse and keyboard and your handheld device.

Apple designed Find My Friends in 2012 as a means for better-connecting with friends and family. It's pretty useful for scenarios when you need to keep tabs at an amusement park or to get a live ETA when your buddy is coming to pick you up from the airport. You can even share your location with others so they can track your whereabouts as you go about your day.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun and cheap prizes that no one needs—boy, do you want them.

For most of us, the primary reason we capture videos on our iPhones is to post on one of the various social media platforms out there, like Facebook, Instagram, Snapchat, or Twitter, providing instant gratification by receiving a proverbial nod from our followers.

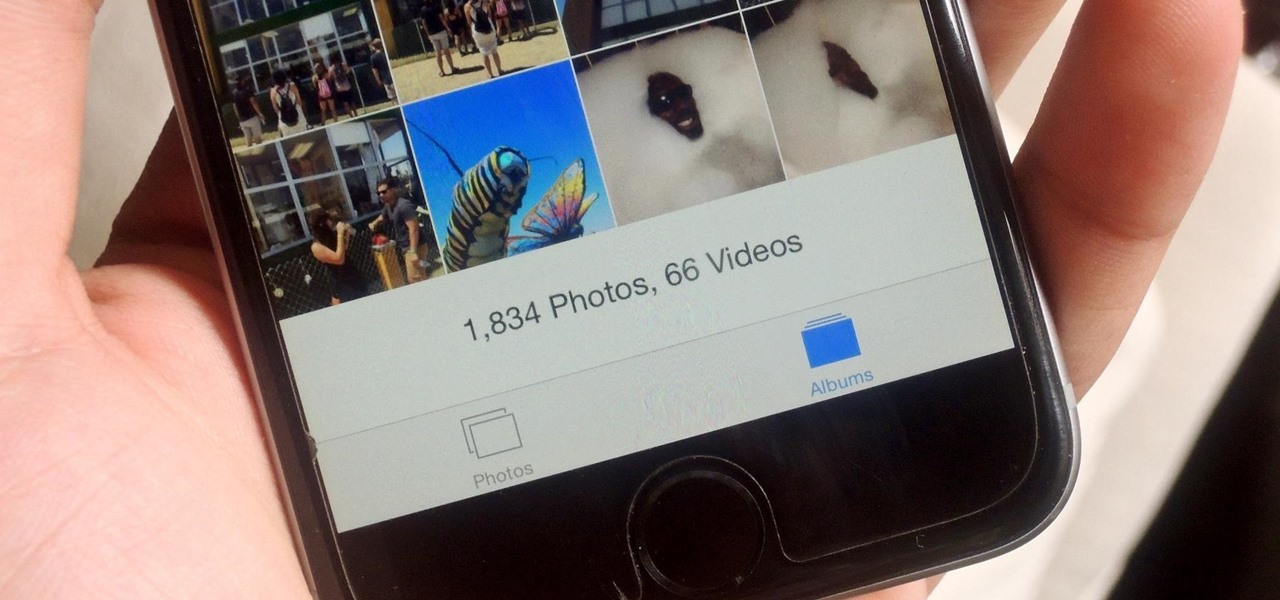
If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone gets lost, stolen, or damaged.

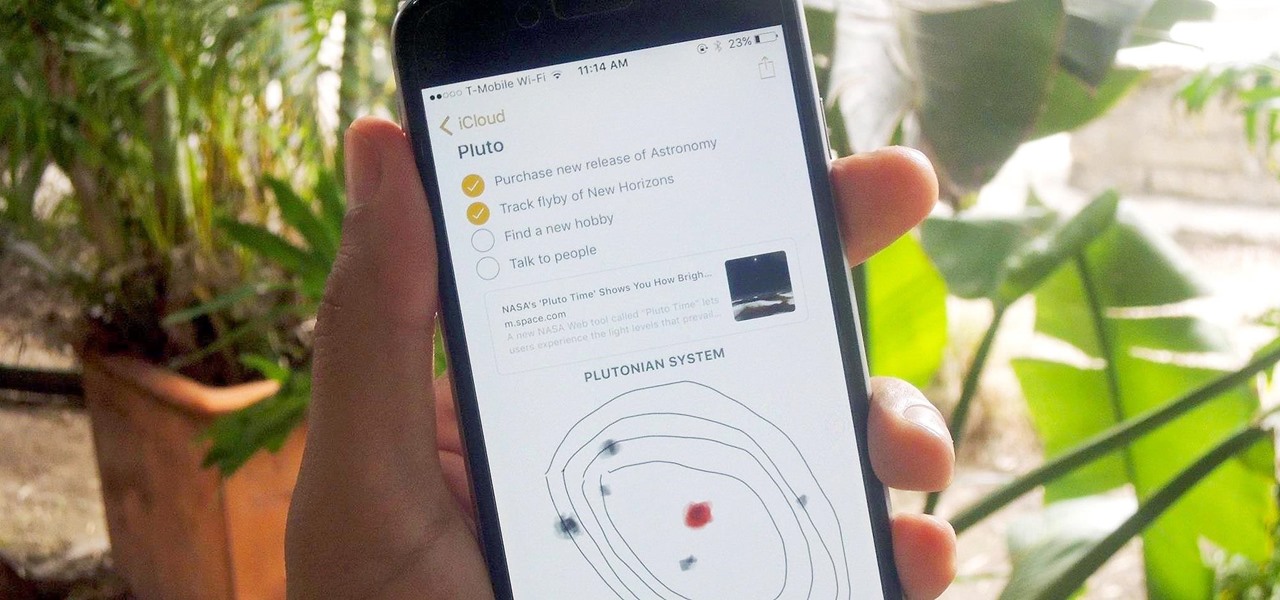
Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files from Safari is almost impossible unless you're jailbroken.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

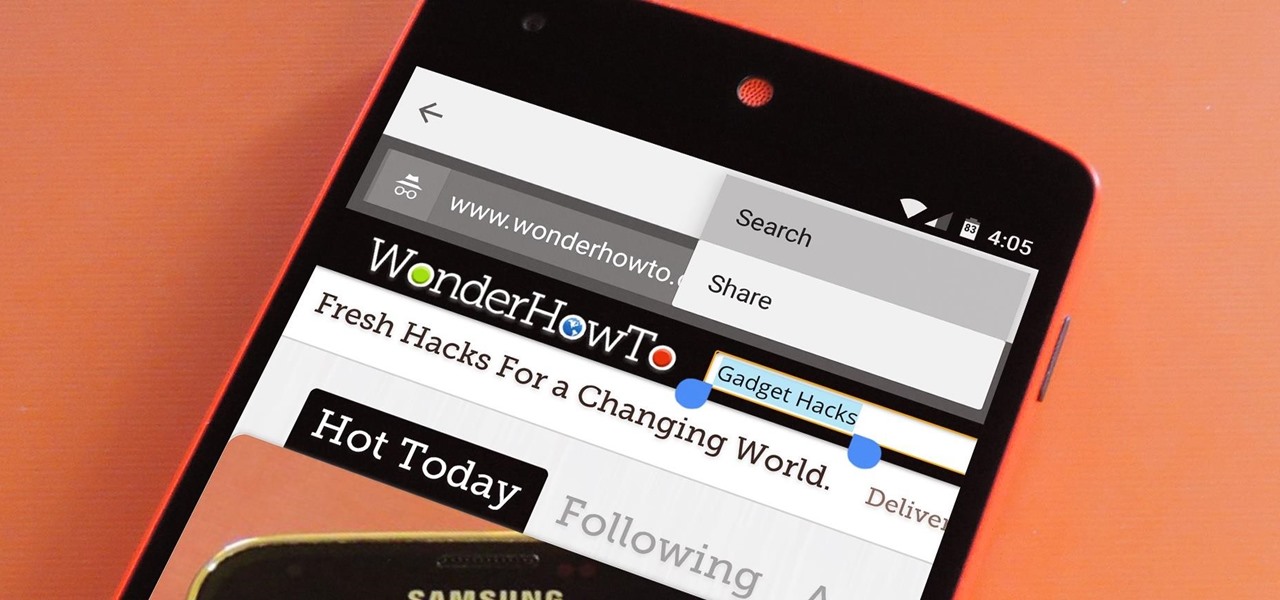
For some odd reason, the Chrome Browser on Android doesn't allow you to search selected text when you're in Incognito Mode. This must have been an oversight on Google's part, because the feature is definitely present with the browser in its normal viewing mode, allowing you to highlight text and quickly perform a Google search.

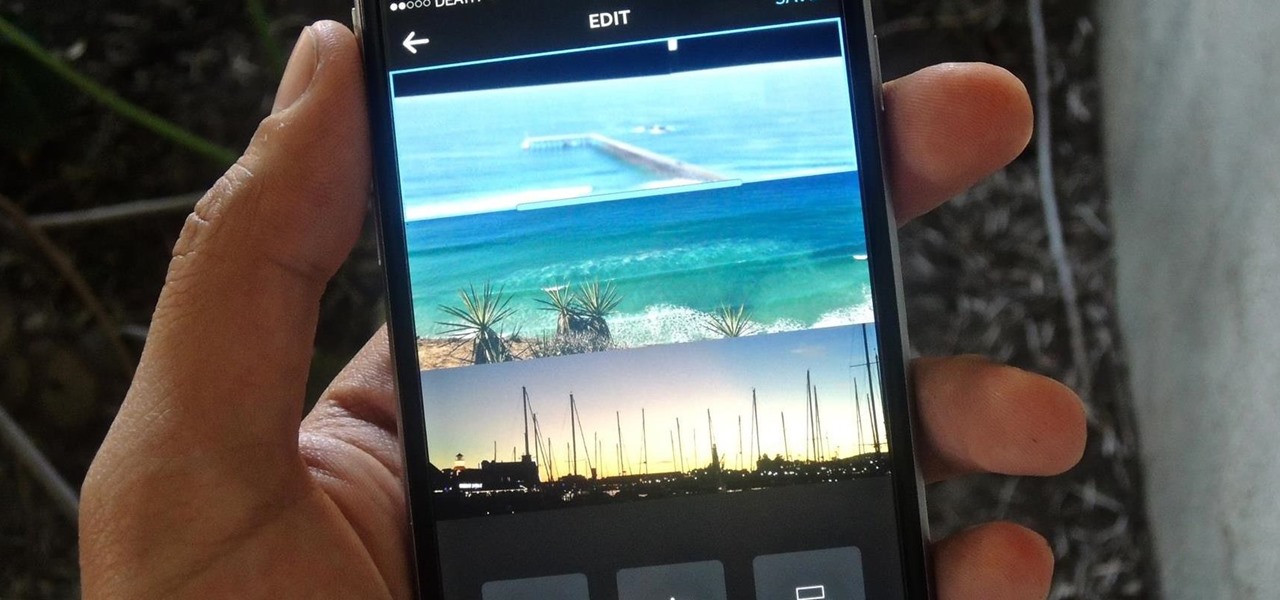
If you're one of the many that likes to upload collages to Instagram, the Facebook company has a new tool for you. Instagram released a brand new app in March called Layout to help facilitate the process of creating photo layouts to post onto social media or just share with friends.

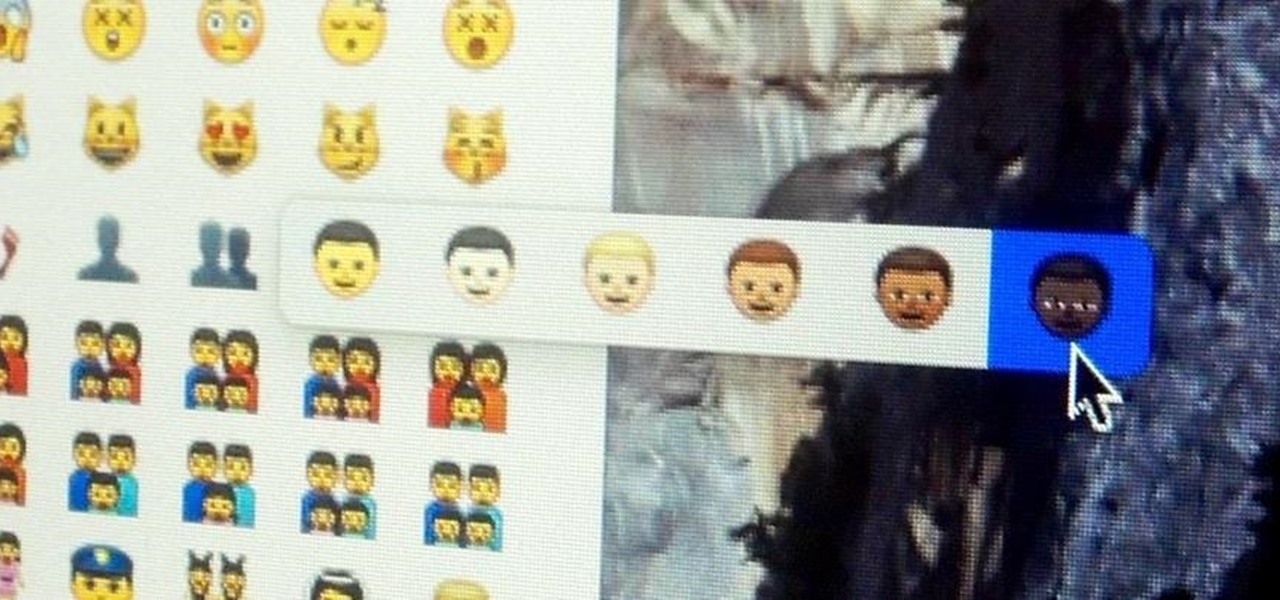
Apple just recently launched its 10.10.3 Public Beta for Mac OS X Yosemite, and while it comes with mostly bug fixes for 10.10.2, it also includes a brand new Photos application that's meant to replace iPhoto and Aperture, as well as the inclusion of more diverse emojis.

While shortcuts to your Camera and third-party apps like Snapchat are great for capturing fleeting moments, it still takes a few seconds to open them and snap a photo. That means you could potentially miss a great shot if you're not quick enough. But now there's a super-fast way to capture and send photos without having to waste time unlocking your device.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

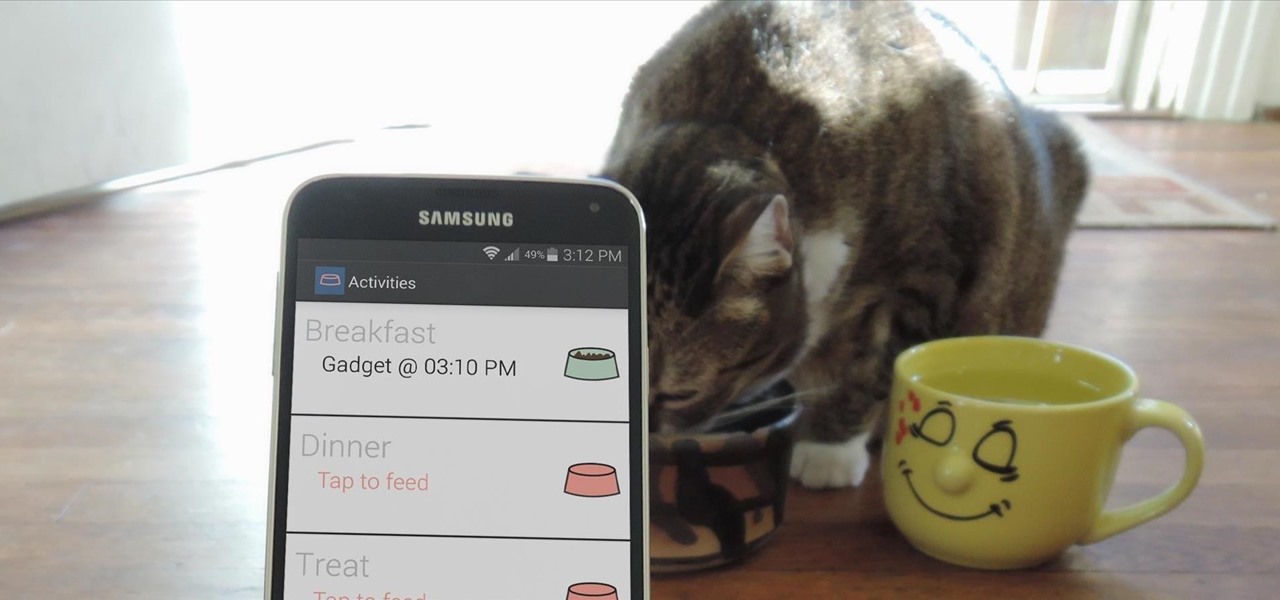
Pets are one of the biggest sources of joy in life, but keeping track of their daily activities can easily become a chore. When you have a roommate or spouse that also likes to feed the cat or walk the dog, miscommunication can lead to double-feeding or an under-exercised pet.

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...

It's time to step up your selfie game, especially if all of your selfies tend to have the same vapid look and feel. There are plenty of techniques for better selfie-taking, and I've already shown you a few iPhone tricks, like making yourself look thinner and using hand gestures to get situated better. Now I'll show you how to give your followers something to really "like"—celebrities.

Sony's latest flagship, the Xperia Z3, comes with some pretty high-end hardware, but what really draws me to it are the aesthetics of its ROM, Xperia UI. Even though my HTC One M8 can still go toe-to-toe with the Z3 in a performance matchup, there is something about Sony's UI that is simply missing from my HTC.

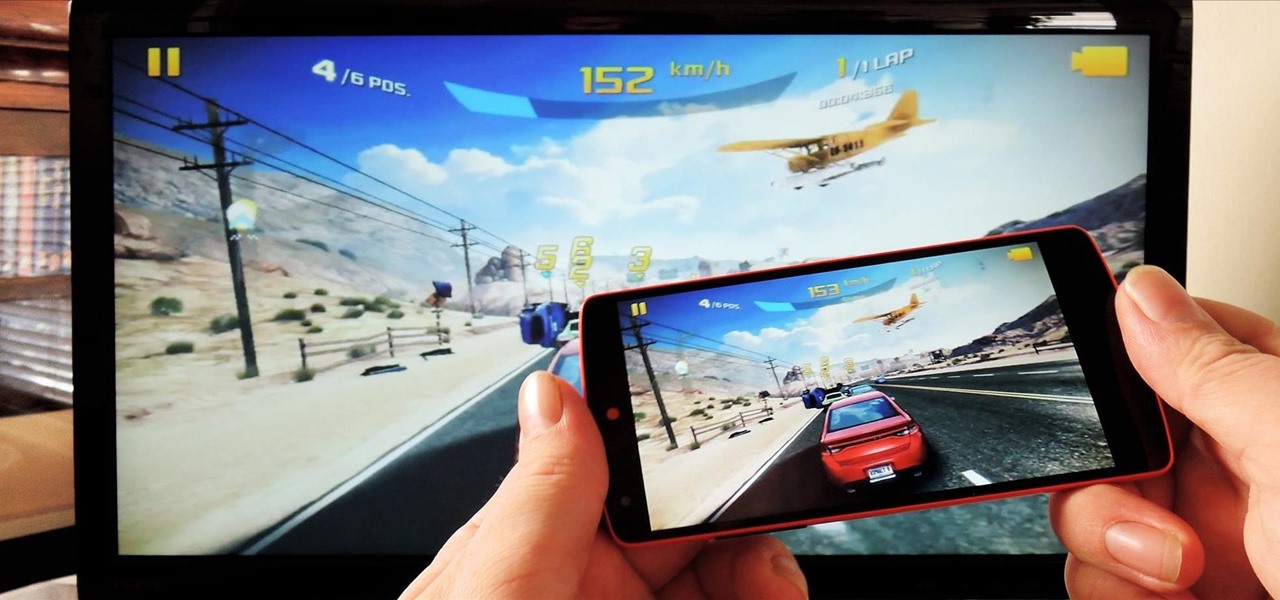
Broadcasting your gameplay for others to view has recently become a phenomenon with the advent of Twitch.tv. While computer-based gaming is well represented these days, streaming of mobile gameplay has been virtually non-existent.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

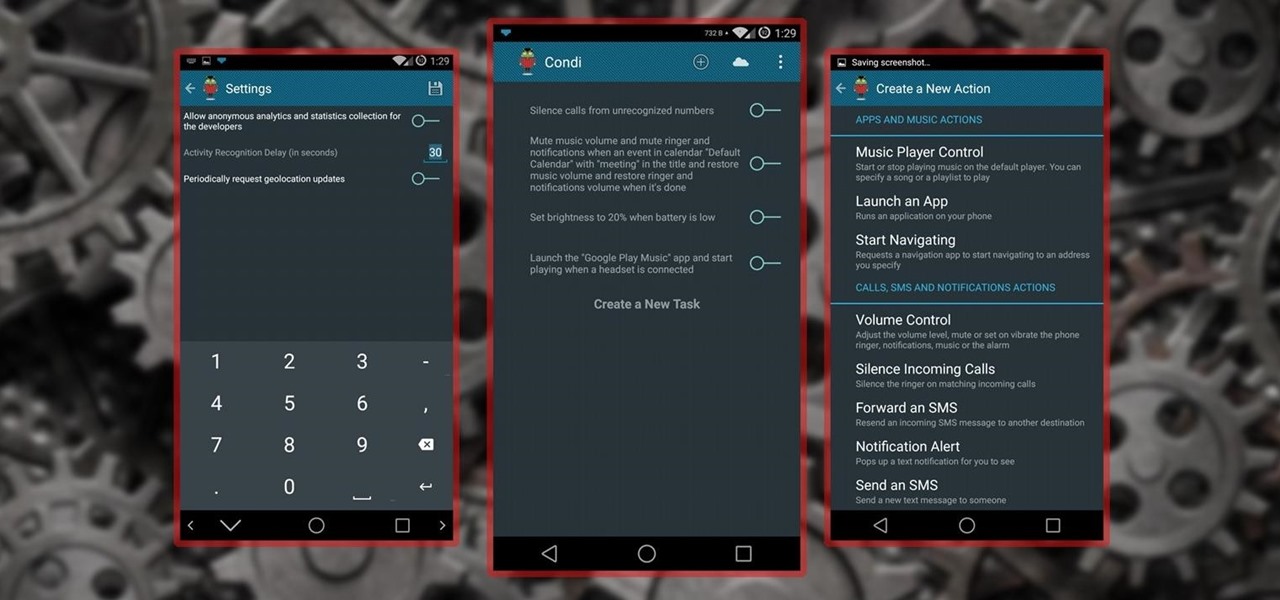
No matter whether you're a seasoned Android veteran, or just starting to get into the scene, you have probably heard of Tasker, the king amongst all the various automation tools available.

The Galaxy S5's fingerprint scanner feels like something straight out of a sci-fi movie. Giving you the ability to lock your device without having to fuss with a PIN or password every time you go to use it, the feature is definitely one of the device's main selling points, especially now that you can use it to unlock individual apps.

With over a million apps and counting, it's not exactly easy to browse the iOS App Store to find fresh and interesting new apps for your iPad or iPhone. Even rummaging through the featured apps and games isn't easy.