Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.
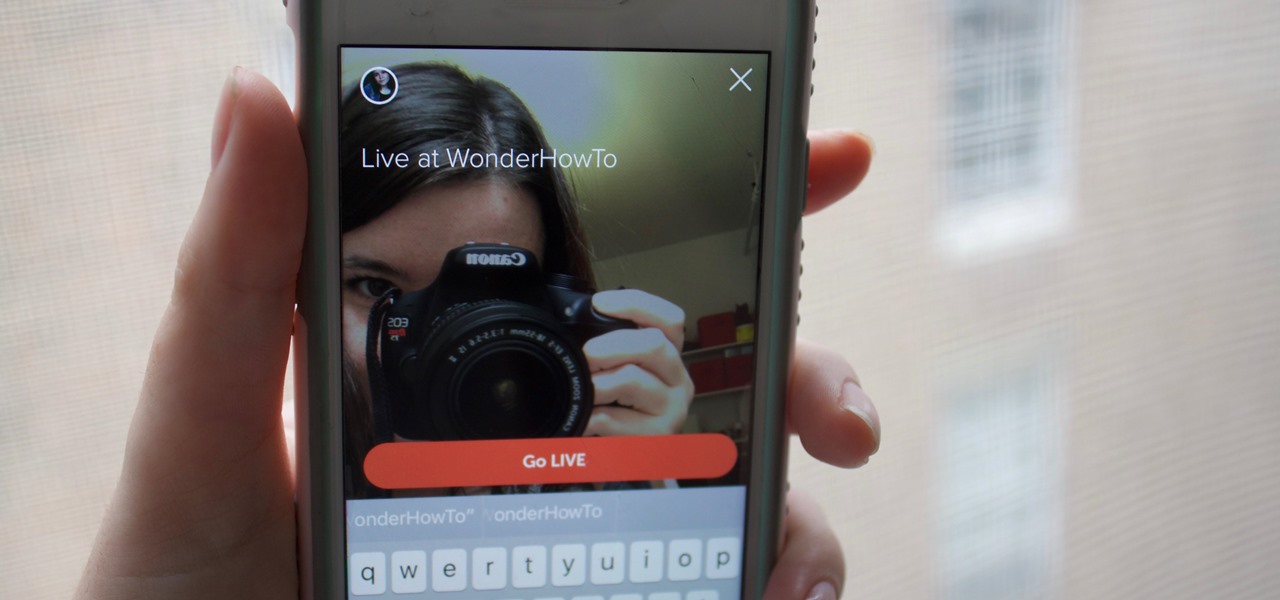
It seems that every major social media platform is adding a "Go live" feature to their apps lately. Twitter, in particular, has been at the forefront of the live broadcasting craze for quite some time now.
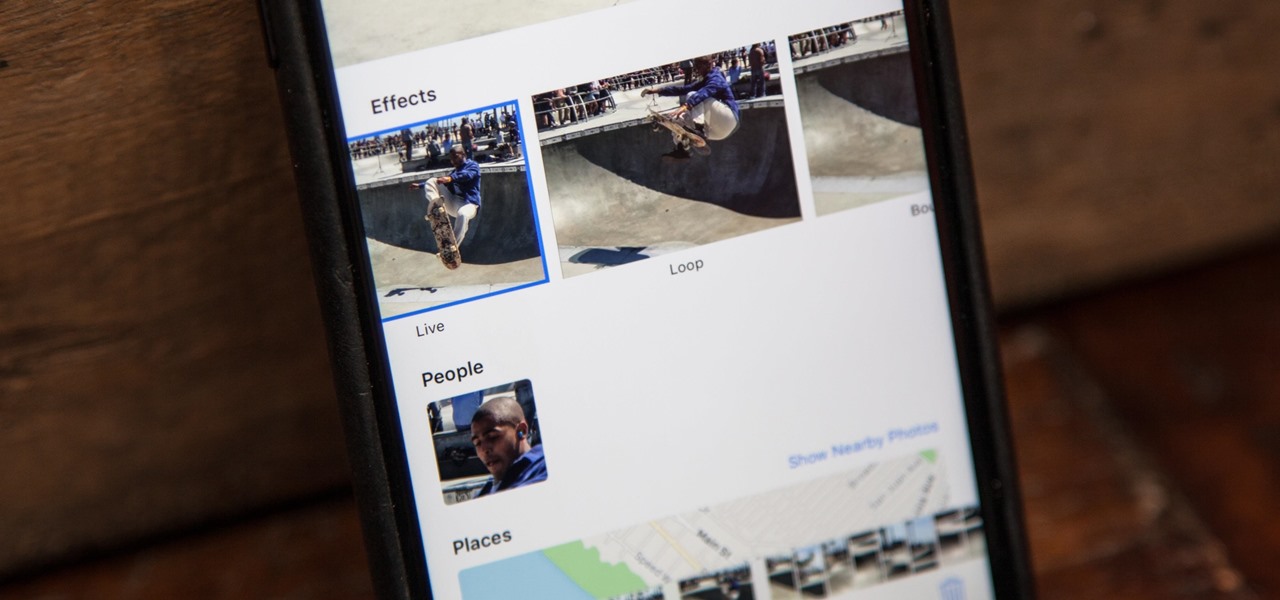
When Apple first introduced Live Photos in iOS 9, it was a big hit for those who had 3D Touch devices — but one thing this cool feature was sorely missing was editing options. Thankfully, Apple has fixed that in iOS 11 by turning Live Photos into a complete package with editing tools and new effects right within the Photos app.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

Running diagnostics on your Android phone can be a very tedious process. More often than not, you need to key in dialer codes to see if your device's hardware is functioning properly, though you can also download apps — but these are often hard to understand for a layperson. When a smaller component like a proximity sensor fails, you're often left with no other choice but to take it to a professional.

Every Tuesday, Next Reality will give readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the Next Reality landscape, and will always know what's going on with new augmented and mixed reality tech and applications.

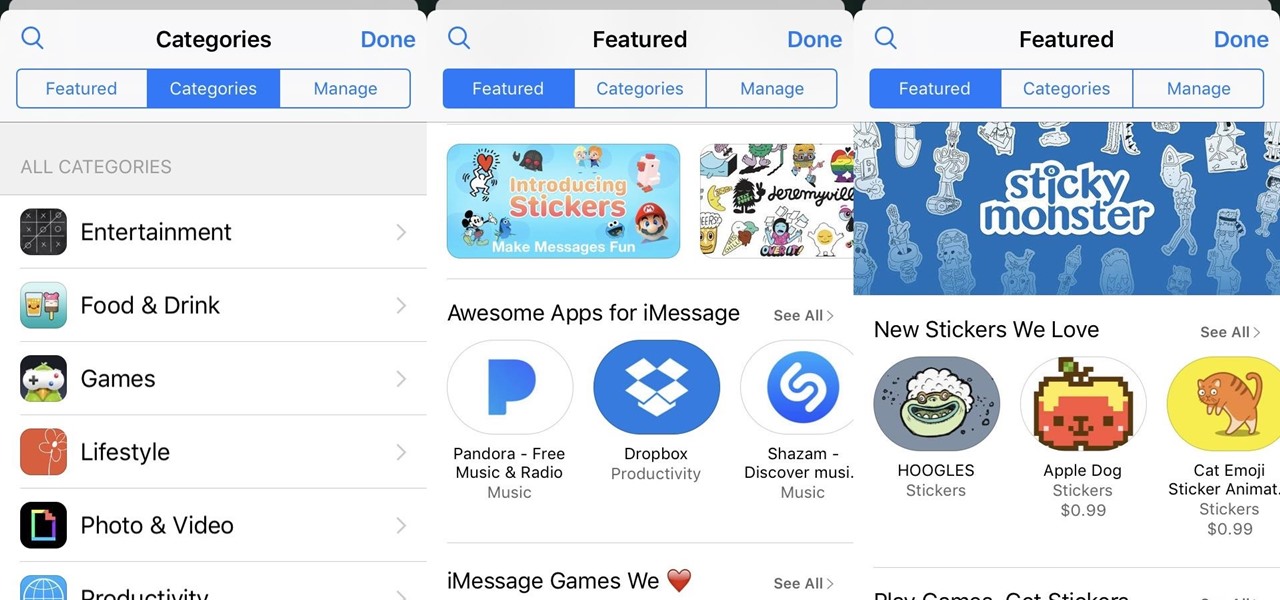
The latest update to iOS 10 brought with it a number of great new features. Of these, the one that will likely have the most impact on people's iOS experience in the long term are the new apps and stickers for iMessage.

Virtual reality holds the promise of electronically visiting distant places we'd otherwise struggle to reach, but that teleportation-esque ability isn't possible without the right content. YouVisit created a platform that makes it easy for almost anyone to create immersive 360-degree experiences so we can map our lives and see the world through the eyes of our fellow humans.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

Let's say you're with friends at a sporting event, music festival, lounge, or some other fun venue, and you want to create a fun split-screen compilation from all the videos you took independently. It's not an easy task, because someone has to get all the video footage and then use a video-editing program that supports split screens. It's a daunting task most people will just skip.

There are two kinds of people standing in the international section of the grocery store: the kind who love Pocky and the kind who don't yet know that they love Pocky because they've never had it.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

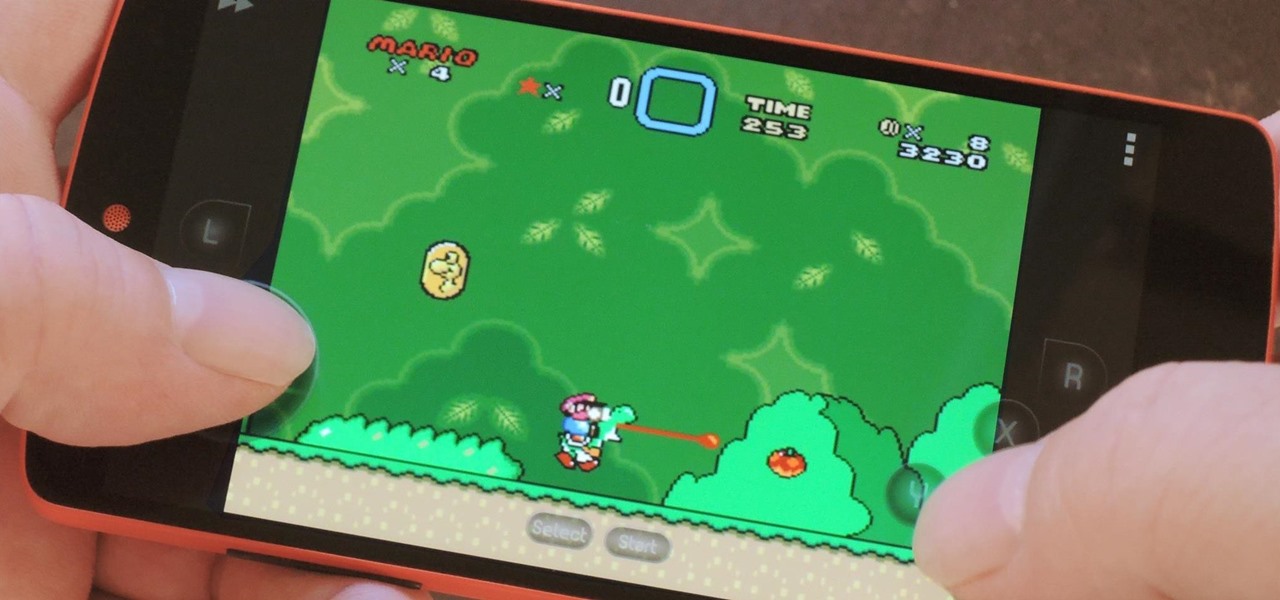
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

Practically every smartphone comes with a built-in camera app, but these apps are generally created by the device's manufacturer. And let's face it, manufacturers are hardware companies first and foremost, so they don't always produce the best software.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

Spotlight, Apple's selection-based search system, received a major facelift on Mac OS X Yosemite. Packed with dozens of new features, such as a central search window and increased app suggestions, the reworked Spotlight was a breath of fresh air.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions.

Eggs are incredibly important to cooks, and not just because they're tasty and a complete protein (many erratic genius/artist types make a point of eating an egg or two for breakfast). Yes, they are great when perfectly poached, scrambled, hard-boiled, and even scram-boiled, but they serve literally dozens of functions when used in recipes, especially baked goods.

Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works.

The new LG G3 is the latest Android flagship-level device to be released this year, and it's ready to give the Galaxy S5, HTC One M8, and the OnePlus One a run for their money. Sporting a gorgeous 5.5-inch QHD display, 3GB of RAM, and a huge 300mAH battery, the device looks great and has tons of power to boot.

Humans in general are great at keeping things about themselves private, from feelings to personality traits. While smartphones and social networks are making these secrets more open, narcissists have and always will love being out in the open with everyone's attention on them.

When Apple recently unveiled iOS 8, many of the newly-added features in their mobile OS seemed eerily familiar to Android users. This is probably because the vast majority of these new features have been available in Android for quite some time.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?

Steampunk music is an oft-debated genre, full of bands playing all sorts of different sounds. While this can make it difficult to generalize about the genre as a whole, it means that the average person is bound to like at least some Steampunk bands. That's why it's a great idea to support some independent Steampunk bands this holiday season by buying their music for yourself, or sharing it with someone else.

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

In this video, we learn how to use uTorrent to download files. First, go onto the uTorrent website and search for what you want to download and in what category you want. After you hit the search button, you will be presented with different things you can download. Click on one of them, then download and save it. Next, you will go to uTorrent software on your computer, and it will download what you just clicked on. When it's finished, you will be able to open your file right away. If you don'...

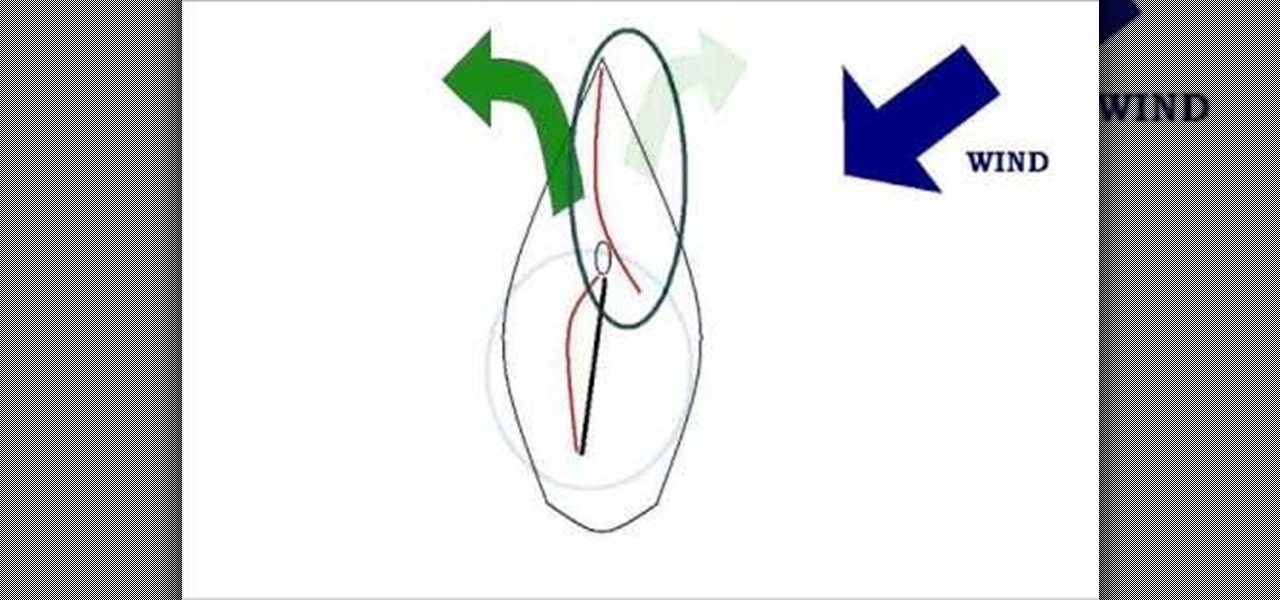
This video talks about the principles of heaving to, which is nothing more than stopping your boat in the water with the sails fully up, without making the boat create much forward motion. There are multiple reasons why you would want to heave to, and one is when the seas are getting rougher and the winds are becoming too strong to safely continue sailing. Watch to learn more about these situations and to see diagrams of everything.

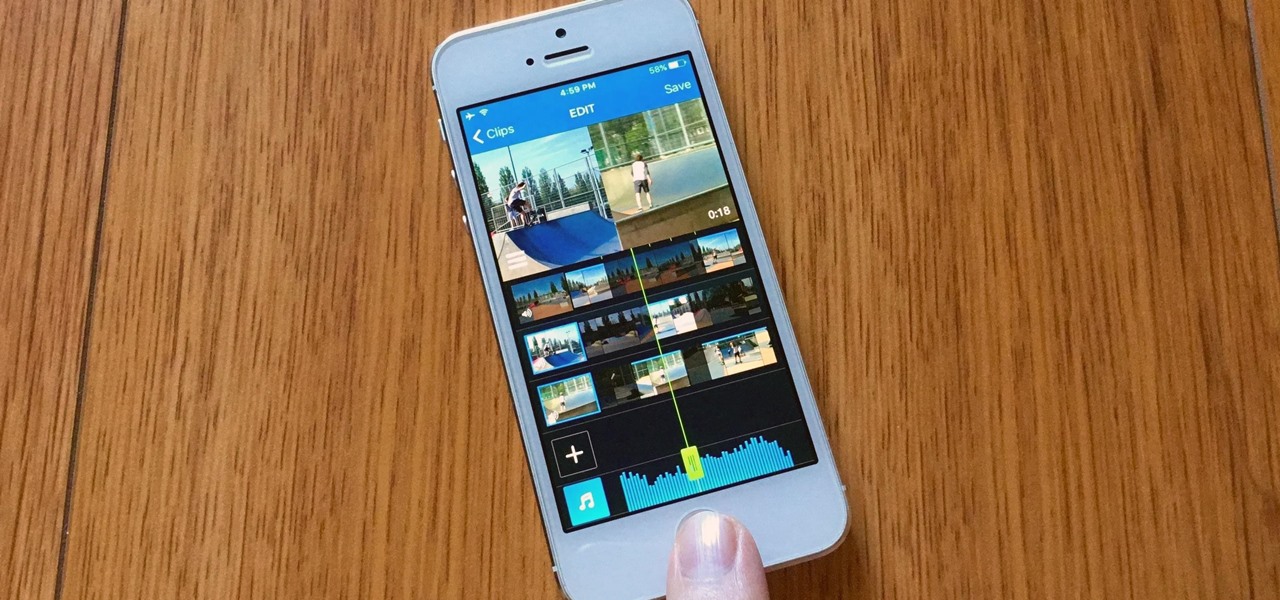
First, after recording the movie open it in IMovie. Make the "rough edits" (removing parts of videos you don't need, and making quick changes). Next, go to Share>Export Final Cut XML. Now an XML file should be on your desktop. Then open up Final Cut pro and edit the audio. If you are adding music, you can open soundtrack and find the music you want, then click and drag it into Final Cut, or send it to Final Cut. Then, make the edits you want to your video until you have it polished into a fin...

In this video tutorial, viewers learn how to use physical exercises to help hit golf balls farther. Begin by using a weighted golf club and swing it several times a day. This will help build muscles and golf muscles. It will strengthen the users swing. Swing the weighted golf club slowly. With a regular club, take multiple swings. Golf muscles are quick-twitch muscles that help golfers develop speed and flexibility. Users can also use two golf clubs to swing. This video will benefit those vie...

In this video Patricia Stark shows how to boost confidence by eliminating negativity. There are a lot of things that you can do to boost your self confidence. If there is any negative people in your life you have to weed them out. Do not listen to their negativity. Everyone has their share of experiences and negativity is the way these people react to them. You need to have faith in yourself and the higher power. When you go home and practice a religion, no matter what religion, your life wil...

Sunny Anderson from the Food Network shares her delicious chili recipe. In a large stock pot she sautés some onions and jalapenos in a little oil. Next she adds some Mexican chorizo and breaks it down with a potato masher. For flavor she adds sliced garlic, cumin, chili powder, cayenne pepper, red pepper flakes and oregano. Next into the pot goes some tomato paste for full body flavor, then some diced tomatoes and a little salt and pepper. Then she adds ground turkey meat, some Gravy Master, ...