This dish is perfect for dinner for two. You need two beef tenderloin fillets with the silver skin cut off, ½ package of phyllo dough, 8 oz of mushrooms, 1½ cup green onions, 2 tbsps of olive oil, 1 tbsp of butter, ¼ cup of parsley, and 2-3 tsps of lemon juice, salt and pepper, Hollandaise sauce. Pan fry the beef for a minute or two on each side if you like it more well done. For the mushroom filling, use fresh mushrooms. Chop up the mushrooms finely. Chop up green onions. Use a little bit of...

This video explains how to make a spider roll. First, spread the rice for the spider roll. Make sure that the top and bottom edges have a thickness of 1/8 inches without rice, so that it won't squash it out when rolling. Then add some toasted sesame seeds. Place the rice patty vertical, with top edges empty, and place the deep fried soft shell crab into it. The claws and legs should be outside of it. Put some crab sticks, avocado and some cucumbers onto it and roll with leaf lettuce so that i...

Kate Hemmings on The Crafts Channel shows that covering a cake isn't as tricky as you may think. You will need a type of icing that rolls out, such as fondant icing. Ideally, you will want to have fondant icing with glycerine, and so the Pettinice brand is excellent in this case. If you use this icing, you will not encounter problems with cracking of the icing when you try to shape it over the cake.
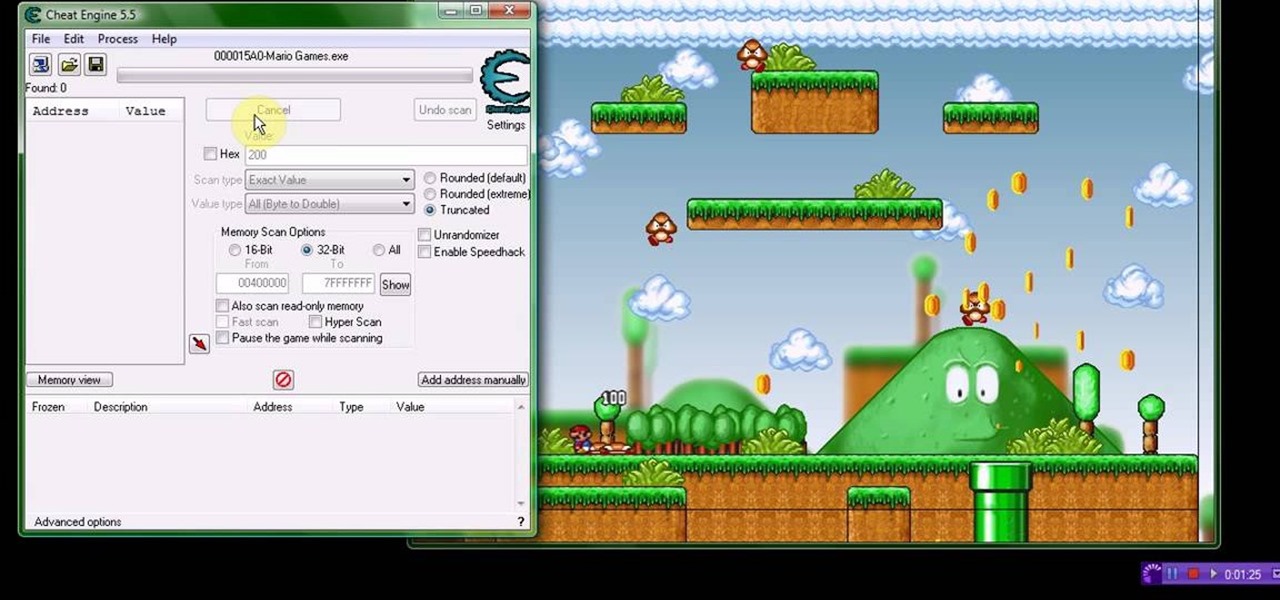
Mario hacks, cheats, glitches. How to play and hack the flash game Mario Games. Watch this video tutorial to learn how to hack Mario Games with Cheat Engine 5.5 (09/30/09). Download Cheat Engine.

Commercial hair conditioners aren’t just expensive, they’re loaded with chemicals. Why don’t you whip up something more natural at home?

Check out Systm's calibration lesson to make your HDTV a great as it was intended. PCMag's HDTV expert, Robert Heron, teaches us top notch HDTV calibration tricks using tools anybody can afford!

Sick of the same old taco? Well, mix it up and try a unique cross-cuisine take on the Mexican taco. Everyone can enjoy the unique flavors of Korean inspired kimchi in the personal size and hand-held qualities of a taco shell.

It might seem like an inconvenience but it is important to take the time to find out what has caused your oil light to come one in your car. You may just be low on oil or you may have a more serious problem but ignoring the warning will only lead to further damage.

You’re on a mission to make the perfect fried egg and inevitably a little piece of eggshell falls in. Your egg is not ruined. Just take a larger portion of the shell and dip it against the escaped shell. No, more surprises in your breakfast.

Check out this interesting video tutorial to see how to take apart a paintball torque loader. Basically, you're just going to tear the torque loader's shell apart to get inside. It's as easy as lifting and pushing the opposite sides of the paintball torque loader shell.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

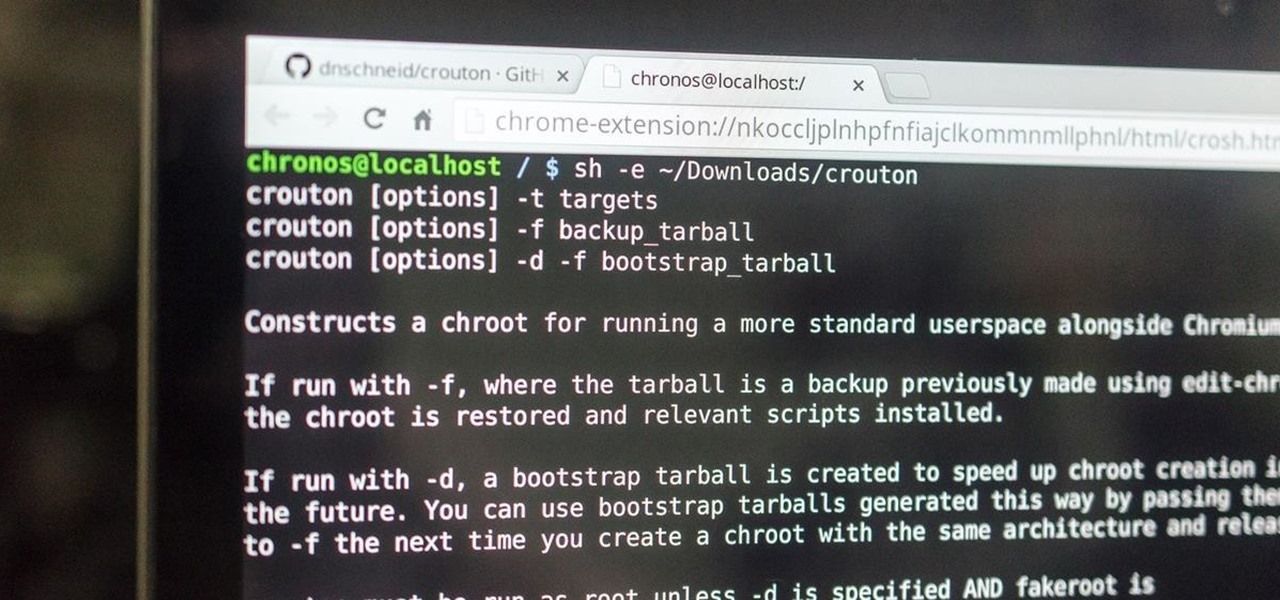
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

If you want to make clothes for your cat, you're on your own. As I recently said in this article, cats will just totally flip out if you make them wear things. Your dog may also flip out, but I've found them to be more tolerant, personally.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Twice baked potatoes are great but for Thanksgiving why don't you try twice-baked sweet potatoes! Ingredients you will need:

In this tutorial, we learn how to make a double-crust apple pie. First, bring apples, apple cider, brown sugar, cinnamon, and nutmeg to a boil in a pot. Then, add in a mixture of corn starch and apple cider. Mix this in, then set aside and let it cool while you make the dough. Roll your dough out and then place into the pie plate and pack down. Pour your apple mixture out into the center of the pie shell, then brush the excess dough with water so the top crust adheres better. Push the top cru...

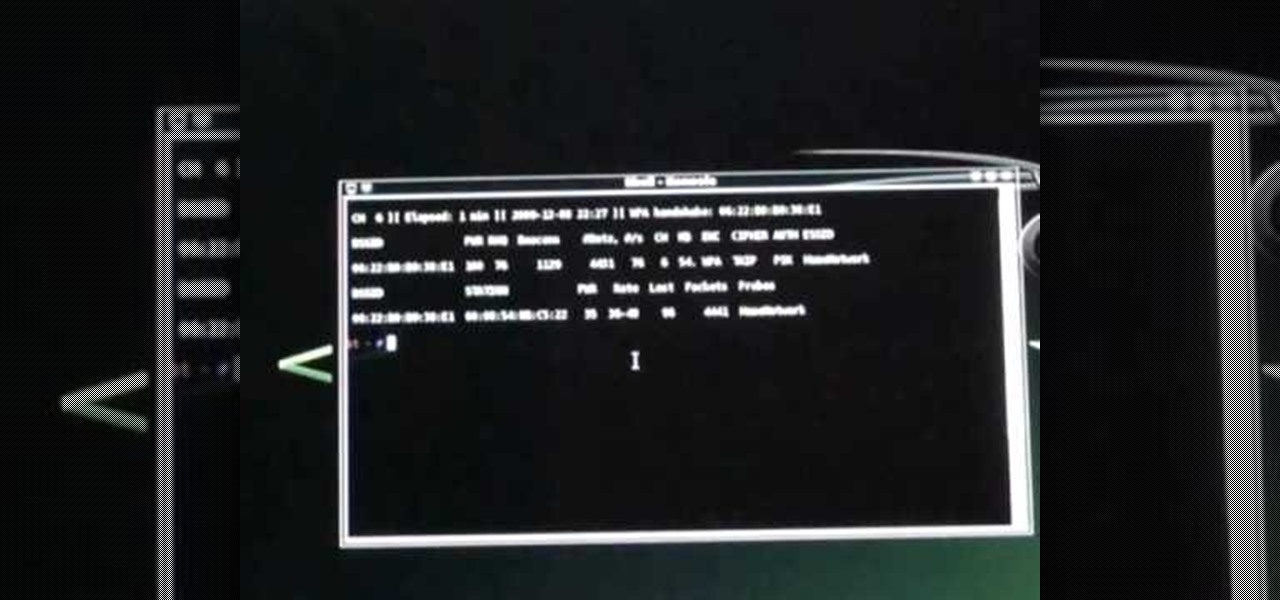
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

BettyCrockerTV shows viewers how to make pull-apart football cupcakes! First, you should cook cupcakes, and then arrange the cupcakes on the platter. Start with three rows of three cupcakes. Next add two on each side! Then add one on the end to finish this off. Now it should look like a football. Now to frost, you should not frost each cupcake. Instead, pipes frosting on to all of the cupcakes in the shape of a football. It should take 2 cups of frosting. Now, after piping frosting onto the c...

Paul demonstrates to viewers how to properly set up a turntable. Each turntable has the same basic parts, so this tutorial should work for most users. There are several components: the platter is the part that spins and it has a slip mat on top. The tone arm is to the right and it has a head shell and stylus cartridge (needle) mounted on the end. The queueing lever is at the base of the tone arm and it raises and lowers the tone arm base. There is also a VTA (Vertical Tracking Angle) adjustme...

In this video Krazyboy shares his method of creating a spiritual bath. Krazyboy suggests that while spiritual baths are often known to help cleanse the soul, you can also imbue it with an intent (such as love, luck, success). The idea behind a spiritual bath is cleansing and white. A nice feature of spiritual baths is being able to customize it, including ingredients that feel right to you. To begin, fill a large bowl about half way with holy water/new moon water/spring water. Next, add a cou...

This video demonstrates how to prepare Potato Salad and Deviled Eggs. To begin making potato salad, peel and cube potatoes. Try to make sure they are all the same size. You will need 8 potatoes. Add potatoes to boiling water. Don’t overcook. Drain and chill in the refrigerator.

This video presents how to connect to your iPod Touch or iPhone using SSH (Secure Shell) without using Wi-Fi connection.

Unexpected guest? Families coming for dinner? or Just in the mood of some soul food? Chicken and dumplings, this fast track version will take few ingredients and little time. This two part tutorial will never have you doubting "whats for dinner?" ever again.

Betty shows you how to prepare a hearty but healthy grilled chicken sandwich. Watch as she breaks down a really simple recipe.

Craving key lime pie? Make one at home! Who knew those tiny little limes could make a pie with so much flavor? Your friends will love this easy to make, tart treat. Learn how to make a homemade key lime pie with help from this instructional video.

In this video, Patty Marino aka "the garden girl" shows us the right way of making stuffed grape leaves.

Wash your face and make sure there are no oils or lotions. Use a toner or a makeup primer which you can purchase at drug store. Pull your hair off of your face with a headband. No hair should be near your face, ears or nape of neck. This is the oil undercoat for use with the 'Kabuki Oshiroi' Shiro-Nuri (Doran) face paint. It is softened in the hands and then rubbed over the entire face or other areas to prepare the skin for the white face makeup. This is the stiff wax used to flatten out faci...

When it comes to used cars, it’s hard to make lemonade out of a lemon. So don’t get stuck with a piece of junk in the first place.

There's a simple reason this tangy bread is famous – it's delicious! You Will Need

There's no exact science to achieving high-school popularity. But you definitely don't have to throw half your class under the bus to get there.