
How To: Hair Chalk
In this video, we show you how to add some green to your hair (or any colour for that matter) using chalk. It is simple and won't damage your hair or your clip-in extensions.


In this video, we show you how to add some green to your hair (or any colour for that matter) using chalk. It is simple and won't damage your hair or your clip-in extensions.

Video: . Step 1:

Warm water is an essential part of life that we sometimes tend to take for granted. Over one billion people, or roughly one-seventh of the world's population, have no access to hot water.

Cassette tapes, much like the boombox, Walkman, and record player, aren't used much anymore. With the ability to put music on our smartphones, most of us don't carry tapes or CDs around because it now seems inconvenient.

Nachos are one of those foods that are really hard to hate. Cheese, salsa, guacamole, sour cream...what's not to love? They're a favorite at Mexican restaurants, concession stands, and even inspired their own kind of cheese, so what's the downside?

These three videos will show you how to build a rustic, distressed kitchen table. I'll be walking you through the process of selecting some recycled timber from a junk pile, and with a little care and some simple joinery techniques, transform that waste timber into a distressed timber kitchen or dining table. In fact, you could use the table for whatever you wanted really.

How to adjust a sliding door. Sliding doors are great when they are sliding but can be a real pain in the bum when they don't. Today's video will concentrate on adjusting the wheels to help alleviate some of these annoying issues. It doesn't matter if it's a robe sliding door, a closet sliding door, a glass sliding door or a patio sliding door, the principle is still the same. Obviously there can be other factors like the sliding door track or the sliding door wheels being in a state of disre...

A spectrometer is a device that splits light into all of the different colors it's composed of that can't be seen with the naked eye. It does this by using a prism to refract or bend the light. Jeffrey Warren over at Public Labs created a tutorial showing how you can make your own video spectrometer and create spectra like the one pictured below. Any guesses as to what the subject is? Believe it or not, that's what whipped cream looks like when viewed through a spectrometer. You can do this w...

Hello! Today I would like to share the process of making your own natural marigold cream. The product does not contain any (artificial) chemical elements and therefore can be called natural. Step 1: Ingredients

The man in the video shows us how to peel an egg open in 5 seconds by slamming the egg down on the counter (not to hard but at a sufficient speed) and rolling it for a bit then peeling it off with ease. As shown with the comments on the video's page, this task is not as simple as the title states. It takes a lot of practice to crack the egg just right without smashing it, but if done correctly, gets you that perfect, out of the shell, hard-boiled egg. This video teaches you that practice make...
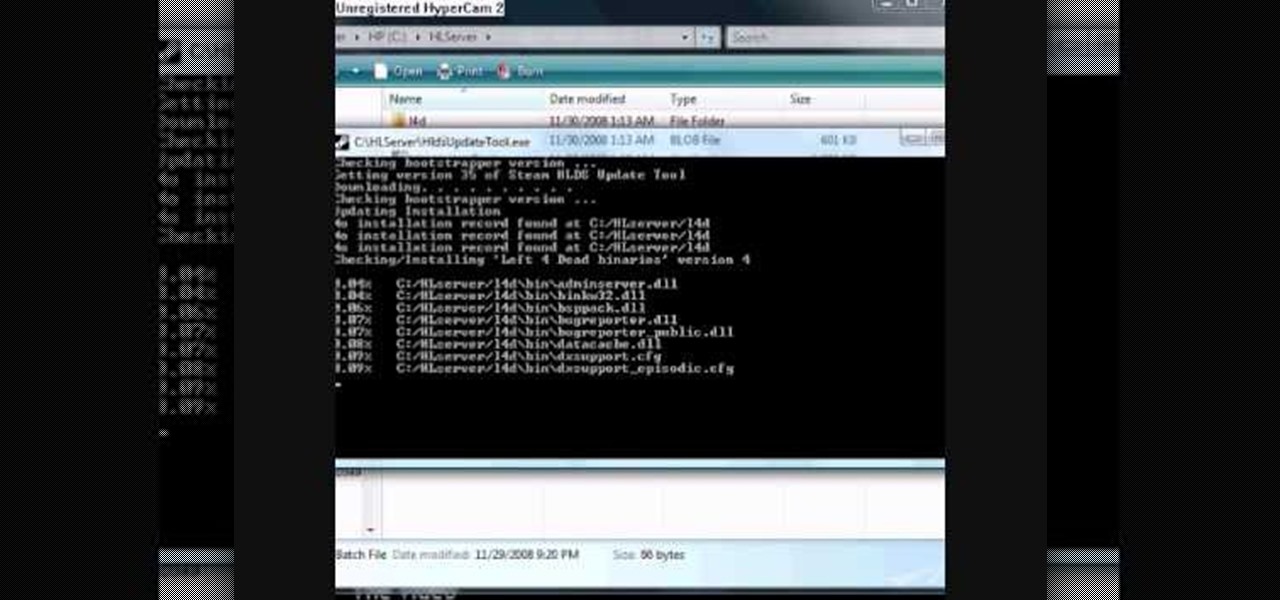
If you don't want to shell out the money to rent a dedicated server in order to host a Left 4 Dead game server, follow this tutorial on how to create one on your home computer. Keep in mind that if you intend on letting other people play it, you will need a fast connection to prevent lag.

Forget the takeout food tonight, watch this how to video and learn how to cook a delicious Korean cod fish recipe. Make a cook "Jeon," a traditional Korean food breaded with flour and eggs. There are many kinds of Jeon, but this one is made with cod fish.

Chicken noodle soup is a very comforting dish, but sometimes you need something a bit heartier. In this video, Betty shows us how to make her favorite chicken noodle casserole. This dish is bursting with flavor and very filling. The casserole is perfect for a chilly winter evening or anytime you need some extra lovin'.

Chicken breasts are a popular dinner dish, and in this tutorial, Betty shows us how to make them yummy AND healthy! Try this flavorful recipe at home and impress your family and friends.

Lamb shanks are very easy to cook. Take 6 lamb shanks and put them in a bowl. Put some olive oil, salt, pepper, rosemary, and thyme on them. Make sure you coat every shank with the seasoning as you turn the shank in the bowl several times. Put them in the oven for 30 minutes at 450 degrees. While the lamb shanks are cooking. Use a saucepan on medium to medium-high setting and heat 2 tablespoons of butter in it. Put some diced celery, carrots, and onions into the pan and saute them in the butt...

Yep Kitty Litter, but DON'T FREAK OUT! Read or watch the video before you make any assumptions. This mask is perfect for oily, dirty, large pores skin! If you need to detoxify your skin, this is the best mask to use, and you can make it right at home! Use this once every 2 weeks. You should deep cleanse your face once every 2 weeks to remove impurities. Unscented Kitty Litter is made out of Clay, Bentonite clay to be excat. Bentonite is clay that is is rich in minerals and it comes from volca...

This is a metallic sparkily super fun look inspired from Twilight the vampire movie! This is what you need: Eyes, Bare Essentials- Platinum, Twiligth Coastal Scents - neutral palette, Urban Decay - oil slick, MAC - frost pigment, MAC ~ black track, Bare Essentials ~ sparkle mascara & MAC- pro long lash. Cheeks: MAC ~ dainty. Lips: Duwop ~ Venom gloss tulip. Where this to tomorrow's midnight showing of the movie TWILIGHT!!!

Home alone and craving something sweet to much on? Here is a quick way to make a chocolate cake in five minutes. All you need is: cake flour, sugar, cocoa, oil, milk, egg, and a mug. Watch this how to video to see how to bake it in a microwave.

Learn to cook a whole goat on the grill with this how-to video. Season it with olive oil, pepper, thyme, rosemary, and sea salt for a Mediterranean style recipe. Place it on the grill or the smoker and let it cook until its nice and tender. Make a butter, dry white whine, rosemary, and pepper mix to baste the goat with. Enjoy!

In this cooking tutorial, Better TV shows you how to lighten up a recipe without sacrificing the taste. Watch this how to video to learn how to prepare halibut fish by baking it in parchment paper. You will need: Parchment paper, string, West coast halibut, tomatoes, olive oil, garlic, Fava beans, white asparagus and sugar.

You only need oil and your hands. Some soft music helps to relax the client.

Watch this instructional video to learn how to cook a Sicilian pizza. All you need is flour, yeast, olive oil, salt, water, tomato sauce, and cheese. This food is mouth watering.

Watch this instruction video to learn how to make spinach tortellini soup. All you need is garlic, extra virgin olive oil, diced tomatoes, chicken stock, tortellini, and spinach.

Those smooth oval shells just seem to jump right out of your hands. When an egg hits the floor it is a gooey mess but not need to use an entire roll of paper towels trying to pick up the pieces. Cover with salt and the mess and be swept up after only a few minutes.

This interesting video is subtitled with instructions on how to make a Kawasaki rose origami. 1) Make mountain fold and 2 valley folds, as indicated, along guide lines.
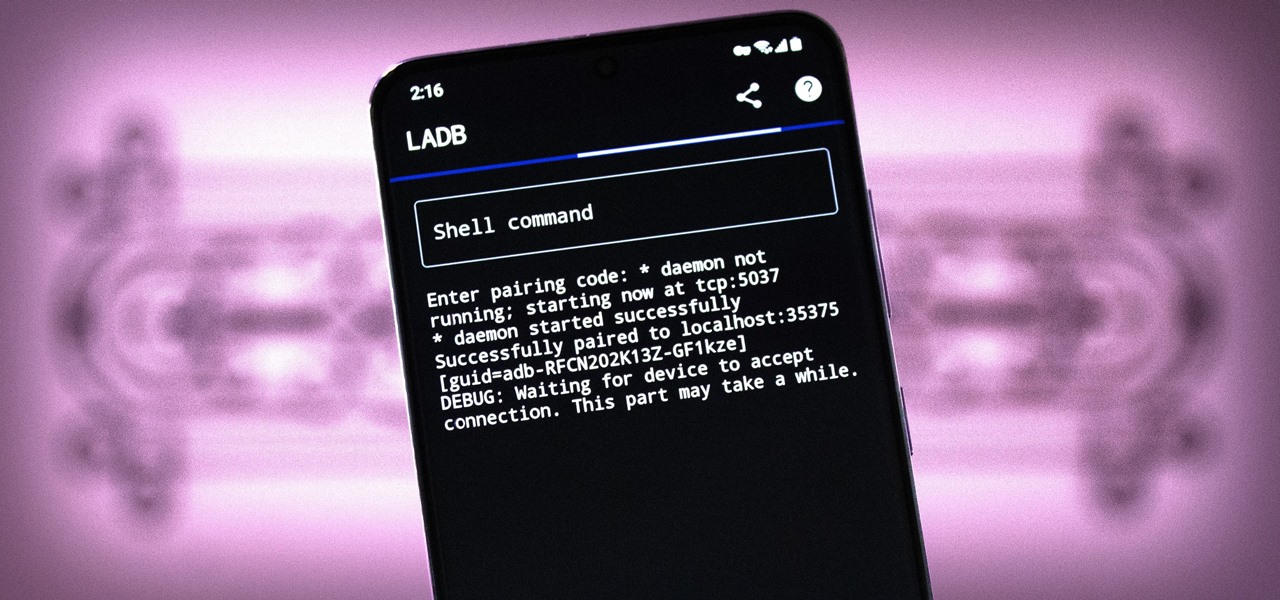
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.
If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

When we were kids, snacks on-the-go or in our lunch box were often Kellogg's Nutri-Grain cereal bars. There were flavors like strawberry, blueberry, and our beloved apple-cinnamon.

Rice is one of those incredibly versatile pantry essentials that you can make in bulk and then freeze for later use in a quick meal during the week. It keeps well in the fridge and freezer, and there are an endless number of ways that it can be used once thawed—from rice bowls and salads to stir-fry dishes.

The thought of peeling tomatoes for pasta sauces and soups has long been an overwhelming idea for us, one we often steer clear from when reading recipes or searching out new dishes to create. Even the methods that are supposed to speed up the peeling process (like roasting, poaching, and freezing) are more work than not.

En papillote may sound like a difficult French cooking method you'd never use at home, but don't be fooled by its fancy name—it's actually a really easy way to cook food that is moist and flavorful, and all you need is some parchment paper and your oven.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Regardless of where you happen to live in the United States, you can always count on Caesar salad being on a menu nearby. The restaurant may be top dollar or a humble diner, but this ubiquitous salad prevails in every region and at every price point.