
How To: Play bluegrass guitar
This is a short lesson on a couple very common G-licks used in bluegrass guitar playing.


This is a short lesson on a couple very common G-licks used in bluegrass guitar playing.
A short tutorial on how to use Wordpress and Podpress along with FeedBurner to submit your podcasts to iTunes.

This is a short film recorded to discuss how to do the multiphonics on a sousaphone. For more information on the circular breathing search for didgeridoo movies

The beginning breathing techniques involve short breaths, but a better technique is to use longer phrases.

Introduction to and history of the timbei (shield) and rochin (short spear or halbert), as well as stances and striking points.

Whether you're short on time or just a big fan of Chinese food, stir-fry is a healthy, delicious, and easy meal to prepare. All it really takes is whatever vegetables and meat you've got lying around in the fridge (leftovers are totally okay) and a wok.

Katherine and Kimberly Corp show you how to do the short plank with leg lifts pilates exercise in this how-to video. This exercise is used to develop core stability and balance as well as build a strong foundation for proper push-ups.

Pulleys are simple machines. A knowledge of pulleys can be very useful. This short video shows how to use a pulley to increase the pulling power of a winch. Supports the Force, Work and Energy component of any science curriculum.

Take a lesson from CPGA Professional and Director of the Richmond Hill Golf Learning Centre, Shawn Clement, who shows you how to get the feel for the short chip shot close to the green.

Tired of spending money on short-lived fresh flowers? Floral Guru Jill Slater has oodles of helpful hints on conditioning fresh-cut flowers to keep them beautiful for days—even weeks—longer.

This short video shows you how to make a chicken. It is set to music and includes inserts along the way to demonstrate the key steps.

Yes we know that there's been a huge food revolution (thanks in no small part to Jamie Oliver) championing growing your own sustainable food and eating fresh and well. However, how can you deny that your tongue doesn't salivate when you walk past an In-n-Out?

Learn a short history on swimming and how to do the strokes. Even if you're not an avid swimmer, we recommend watching this... It was made by a fifteen year old! Strokes covered are the butterfly, breaststroke, backstroke and freestyle.

This short video shows the meaning of various key tarot cards. For an initiate this can be a helpful how to video, for others it's an interesting tutorial and a few moments of entertainment.
This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

Before you attempt this firmware install, if you have already installed custom firmware on your PSP this measure might brick it. Don't double install if you have already hacked your PSP.

With the iPhone, it's possible to share URL's you find on the internet with your friends. Take a look at this tutorial and learn how to share your URL's through the iPhone.
With Shortcuts, Apple has designed a way to create your own tools and automations right on your iPhone. And to top it off, your creations can be accessed in a variety of ways, including Siri phrases, widgets, and the Shortcuts app itself. Perhaps even more useful is adding them as custom actions to your Share Sheet and making them available to you system-wide.
Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Video: . Optimize your Marketing with a Mobile Website

This video explains how you can watch YouTube movies and videos on your iPod. First of all you need to open your web browser and do a search for Realplayer (in this case Realplayer version 11). Next, click on the link for Realplayer. You will need to download and run the installation file. Once the installation has run you need to accept the default and then load your web browser (Explorer or Firefox). From here you can choose any YouTube video you would like then add "&fmt=18" to the url add...
Dr.Quillo from Quillo video tutorial is explaining about downloading high quality wav sound files. According to him this is much more efficient, less time consuming and the result is of higher quality than using Audacity or winrec32. He asks us to use internet browser, preferably Firefox. He guides us through the process of downloading various tools like Mediacoder, virtualdub, fast video download through google or any search engine. Mediacoder is a freeway software device which converts .flv...
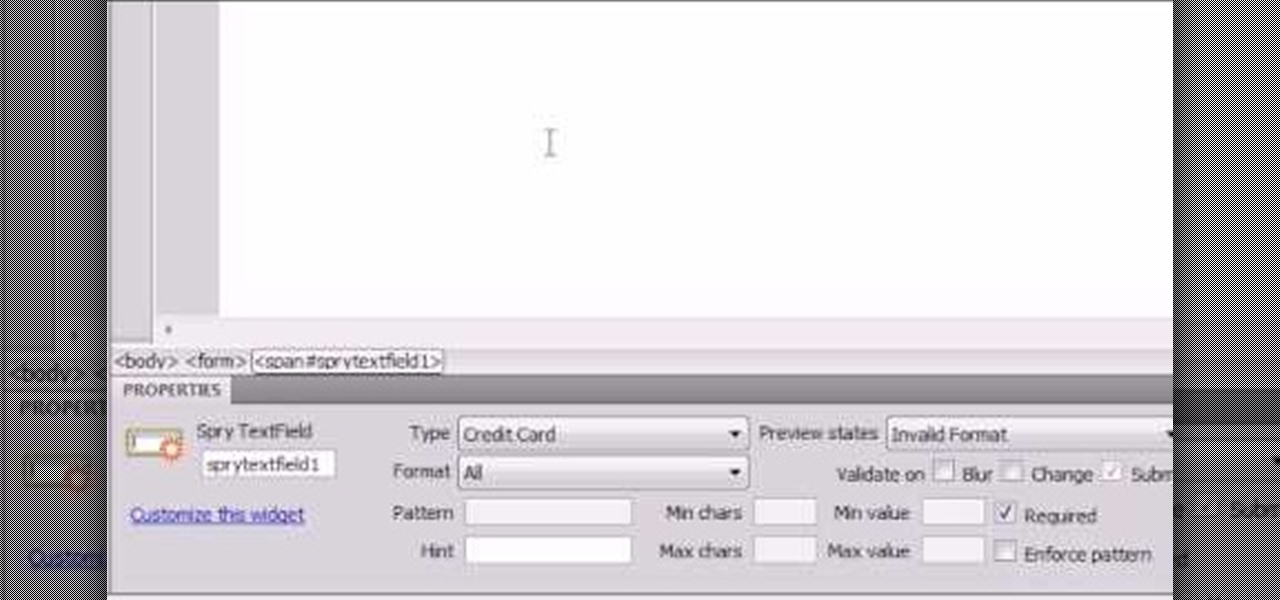
Here the New Boston shows you some tips about using the Spry Validation Text Field. To begin you will go to the Spry Validation Text Field, on Dreamweaver CS4. Looking at the bottom of the page notice the various options that are available for Properties. You find drop-down boxes for Type, Pattern, Minimum or Maximum values, Required, Enforce pattern, Format, Validate on, Blur or Change and Preview States. You can see the types of text available for validating by left mouse clicking the Type ...

Check out this awesome tip from CNET on getting FREE eBooks of the web and onto your Amazon Kindle for easy and cheap reading. They show you the exact process for getting free ebooks for your Kindle, so watch and learn. It's worth it!
This video is about how to download torrent files. The first thing that you will have to do is to open your uTorrent. After opening your uTorrent, open your browser and browse torrent sites that suit you best. Once you have found the site that you like, search for torrent files that you are interested in. Once the results have been displayed, refer to the number of seeds since this increases the download speed. Once you have found the largest number of seeds, click on the title of the file. A...

This is a javascript trick that will work on any website. Just go to the webpage you would like to view go bananas, erase the url from the address bar, insert this code into the empty address bar, hit enter, and enjoy:

Watch this video to learn how to download images from Yahoo using Firefox. 1. Click to open Firefox. 2. Surf or open the Yahoo main website by typing www.yahoo.com. 3. Click the Images tab. 4. Click the Search Box and type the word of the image that you are searching for. 5. Click Image Search tab. 6. Thumbnails of images will appear. 7. Note the name of the file, dimensions, file size and URL. 8. Choose a picture that you like and click on it. 9. The picture will become a bit bigger and will...
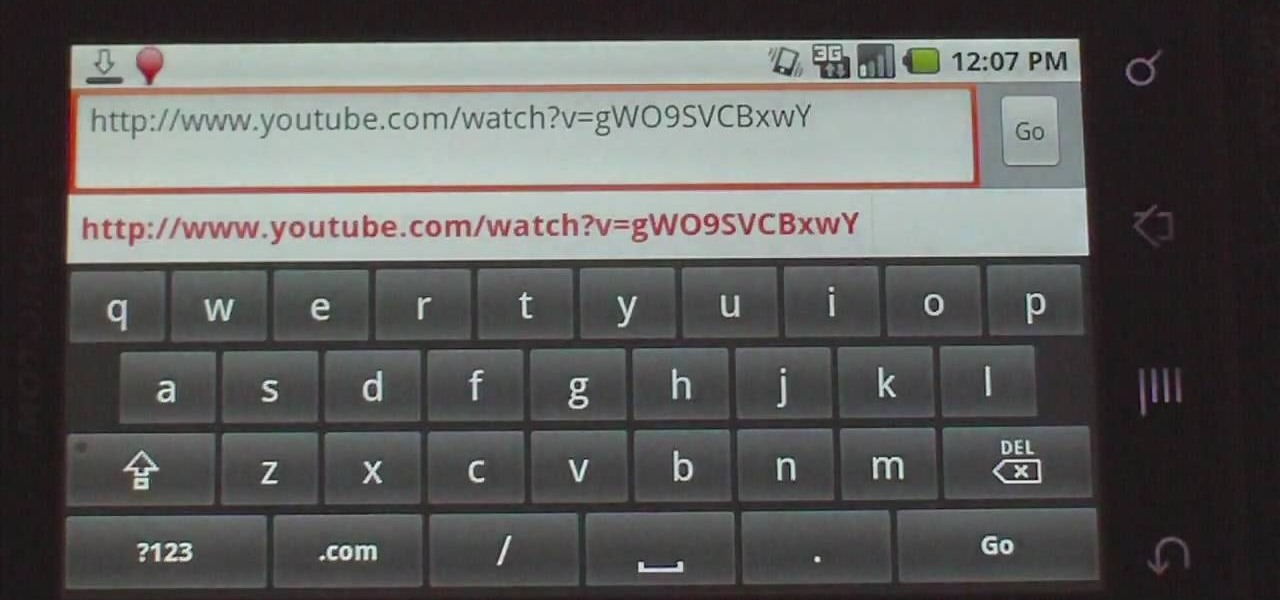
This how-to video explains how to copy and paste text in the browser in a Motorola Droid phone.

Wondering what cat is best for you? If you’ve decided to adopt a cat, learn what different breeds can offer so that you can give your new feline a forever home.
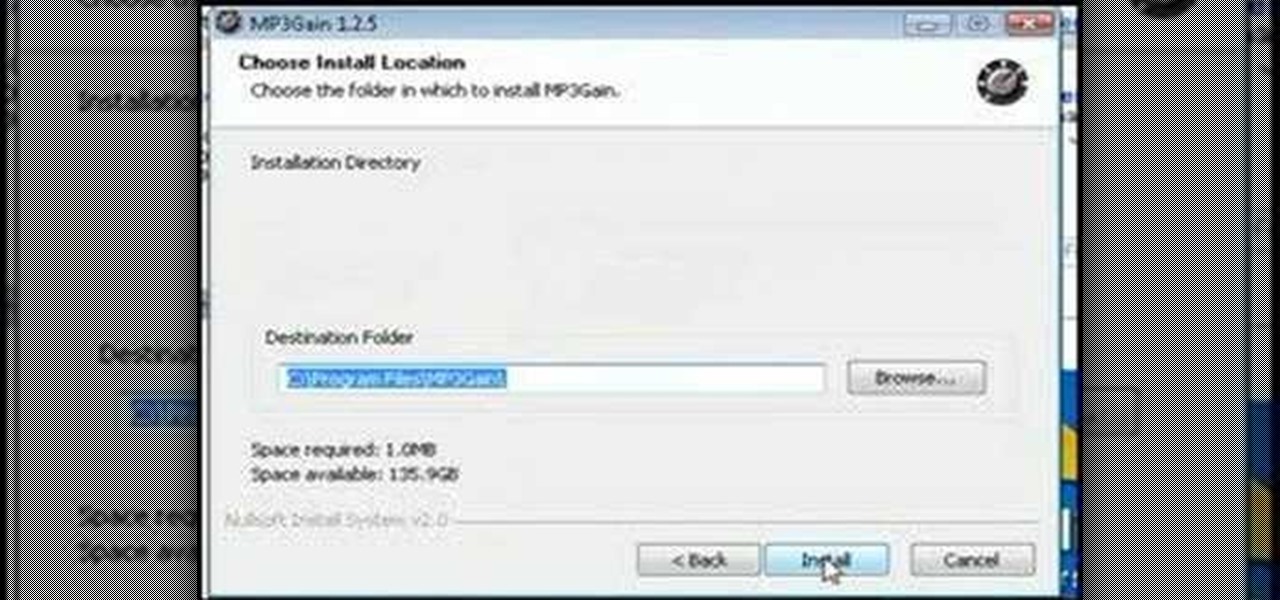
Tinkernut has all the answers when it comes to MP3 music files, and they're sharing a few of their favorite tips to help you build the ultimate MP3 collection! Watch all three of these videos for the best practices to manage your music files.

Poison Ivy is a villainess in the Batman comic books, a seductive femme fatale with poisonous blood and the ability to control plants. She makes excellent inspiration for a Halloween costume. Make you sexier and more beautiful. Hair: Poison Ivy is portrayed as a beautiful redhead, contrasting with the green of her outfit. Buy a red wig or use hair dye to dye your hair red. Body: Purchase a cheap green leotard, bodysuit, or swimsuit, along with 30 or so fake ivy leaves. Using a needle and thre...
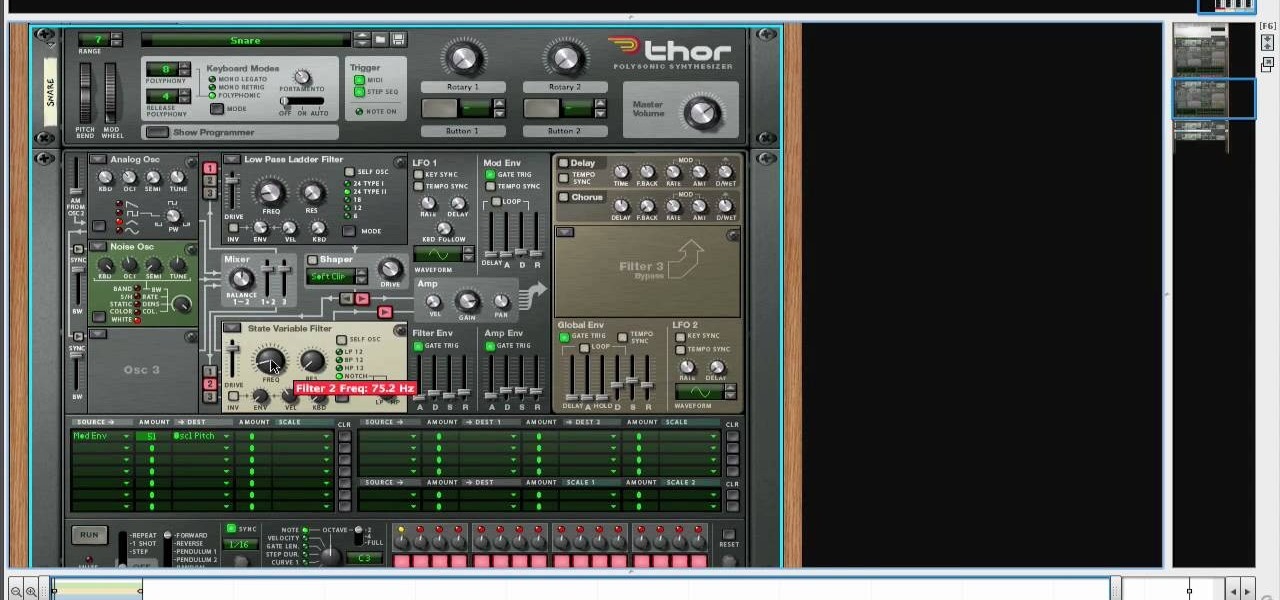
Create drums sounds using Reason's Thor synthesizerYou can use the Thor synthesizer to make a kick, snare, hat and clap sound.Kick:Use the analog oscillator with triple wave form octave3. Set the source to mod envelope 45 destination oscillator 1.Use a very short attack to K and release time. You get the short effect of pitch. Try different oscillator types to get different textures.Snare: Use the same basic patch that we created for the kick. We will keep it as the basis for most patches for...