A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Snapchat accidentally—and then intentionally—announced their digital eyeglasses, known as Spectacles, over the weekend. While we'd hoped their augmented reality-heavy platform would result in related hardware, Spectacles unfortunately seek to "reinvent" little more than a video camera.
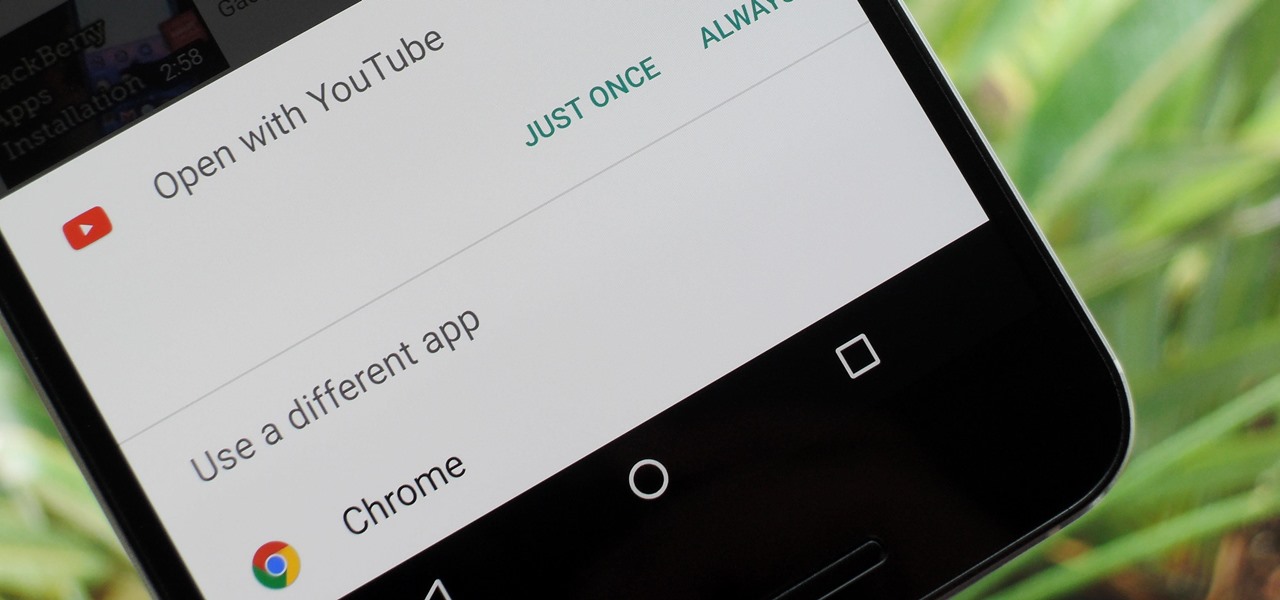
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always."

Unless you had a master of visual effects for a parent, you had to imagine the floor was actually lava when playing the classic furniture-hopping game. With a Microsoft HoloLens, however, you don't have to imagine anything.

LARPing, or live action role-playing, can look a little silly because it requires a lot of imagination to suspend reality. But mixed reality technology like the Microsoft HoloLens can change all of that with voice commands and special effects.
If not the future of computing in general, augmented, virtual, and mixed reality certainly will change the world of gaming. If you want to try your hand at shaping this evolved medium, the Unite Europe conference posted a talk that explains the first things you need to learn to develop holographic games.

Several major web services—most notably Facebook—have horrendous Android apps that occupy way too much space and drain battery life at an alarming rate. Such issues have led to a new trend where third-party developers create minimalist "lite" apps that are essentially the mobile website bundled into a native Android wrapper, freeing up storage space and saving battery life without sacrificing many features at all.

After a relatively short beta-testing period, Pokémon Go is now rolling out to Android and iOS devices right now. If you want to catch 'em all in the real world, your wait is over.

The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.

Google kicked off I/O 2016 by debuting Assistant, a next-level version of Google Now. While you could search the web by voice before, now you'll be able to have a conversational interaction with Google. In short, it's a smart chat bot.

GIFs are awesome, but GIFing from your keyboard is some next-level stuff, and Apple knows this. That's why they've included a way to find and send GIFs in Messages from the stock iOS 10 keyboard. However, iOS 10 is not out for the public just yet, so if you want to easily send GIFs in your messages, you'll have to settle for a third-party keyboard.

Snapchat began rolling out a massive update on March 29th, dubbed Chat 2.0, that gives users a plethora of new features, basically transforming Snapchat into an all-purpose messaging app.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

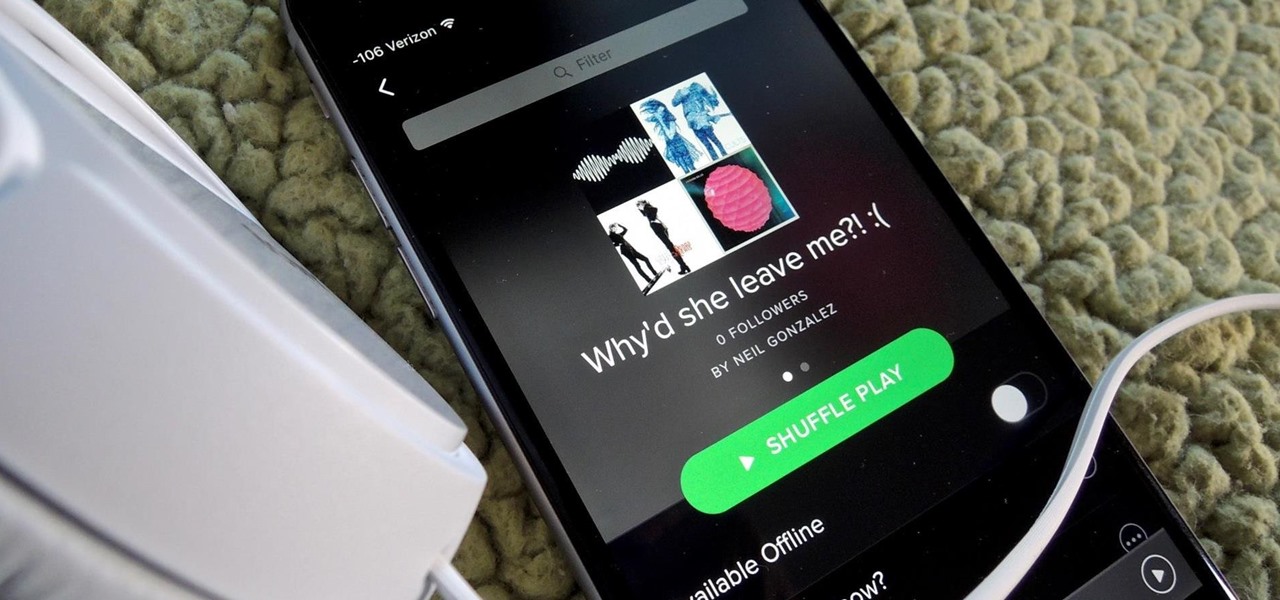
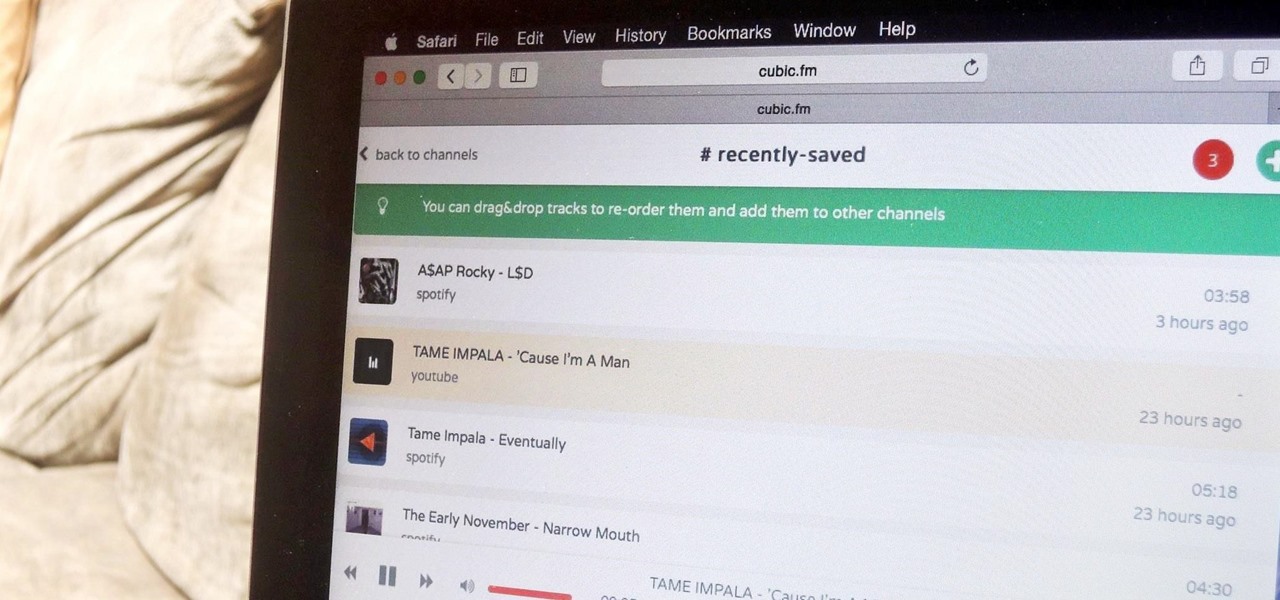
Playlists are more than just a list of songs that you enjoy listening to while in traffic or hosting a party—they're stories that illustrate who you are or your frame of mind at a certain point in your life.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

To help keep sleepy binge-watchers from sleep-"watching," Netflix asks if you're still watching after a semi-short period of time. This means that it could be anywhere from 1 to 5 episodes that you slept through, which is better than 2 seasons, I guess—but it doesn't make it any easier to find out where you left off.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

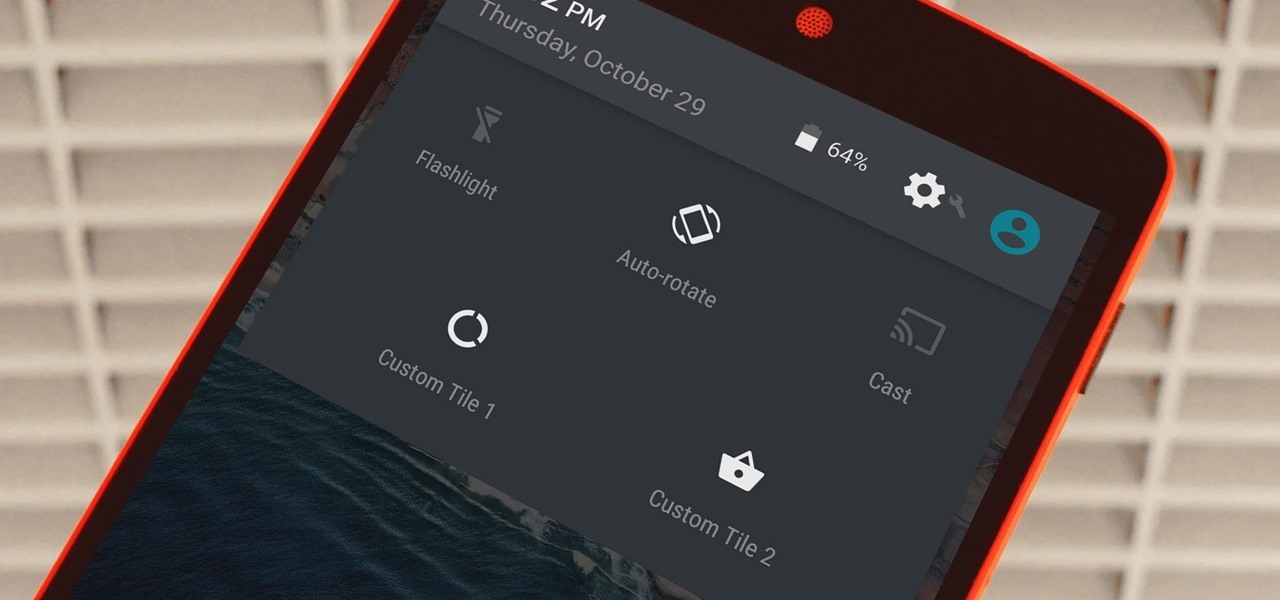
Android's Quick Settings menu is quite handy—just swipe down with two fingers from the top of your screen and you're ready to toggle several different system settings on or off. It got even better with Android 6.0 Marshmallow, since you can even use the hidden System UI Tuner to rearrange and remove your Quick Settings tiles now.

If you're a fan of the Metal Gear video game series, an obvious Halloween costume choice would be Solid Snake, the protagonist of nearly all of the games. However, an even better option would be Big Boss, aka John, Ishmael, Vic Boss, The Man Who Sold the World, and Naked Snake, among many other aliases. He's was once a good man, but better known as the nemesis to Solid Snake. The below costume by YouTube user Erick Zeros showcases Naked Snake in his good era, in Metal Gear Solid 3: Snake Eate...

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Technology can move really fast. Just consider the format for which we consume videos and movies, which has transformed from film reels to VHS to DVD to Blu-ray to steaming with nothing physical at all. But for some odd reason—maybe because it strikes a nostalgic chord or it's just the new hipster trend—VHS is in again. Yes, shaky, grainy, low-quality videos with timestamps are cool again, and I dig it.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

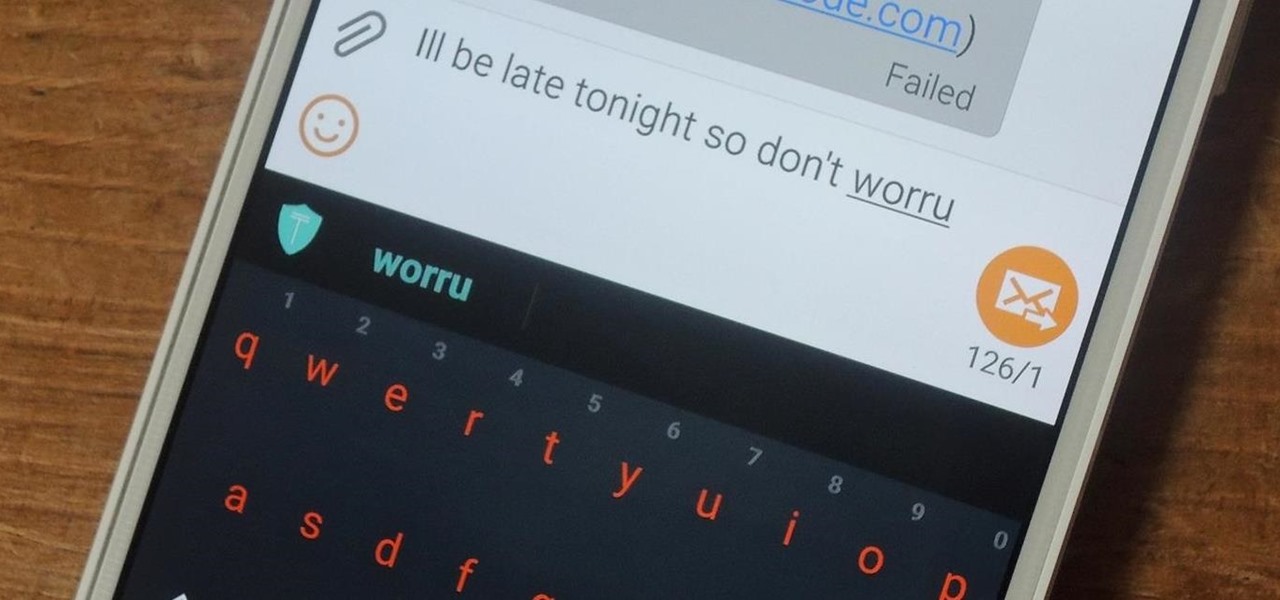
My reliance on autocorrect has made me a horrible speller. I take it for granted that it'll catch all my mistakes, but it only ends up making matters worse (especially when it inadvertently makes correct words wrong). So instead of relying on autocorrect to fix typos, why not try to completely prevent mistakes from happening in the first place?

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

There's a built-in timer feature on the iPhone's Camera app that helps you set up your device, step back, and take a photo before time runs out. This feature is useful when there isn't another person around to take a photo of you, or when you don't want to be missing from a memorable group picture. Unfortunately, timers don't always work well. With a timer, no one can sit behind your iPhone to see if the picture is perfectly focused and framed, but that's where your Apple Watch comes in.

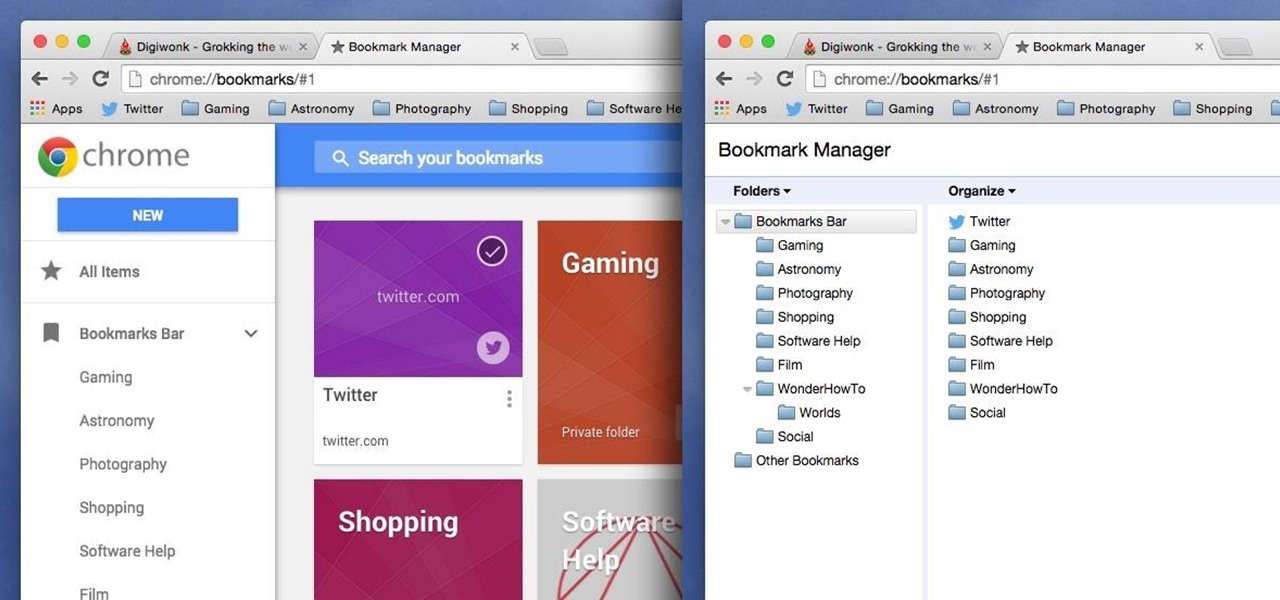
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

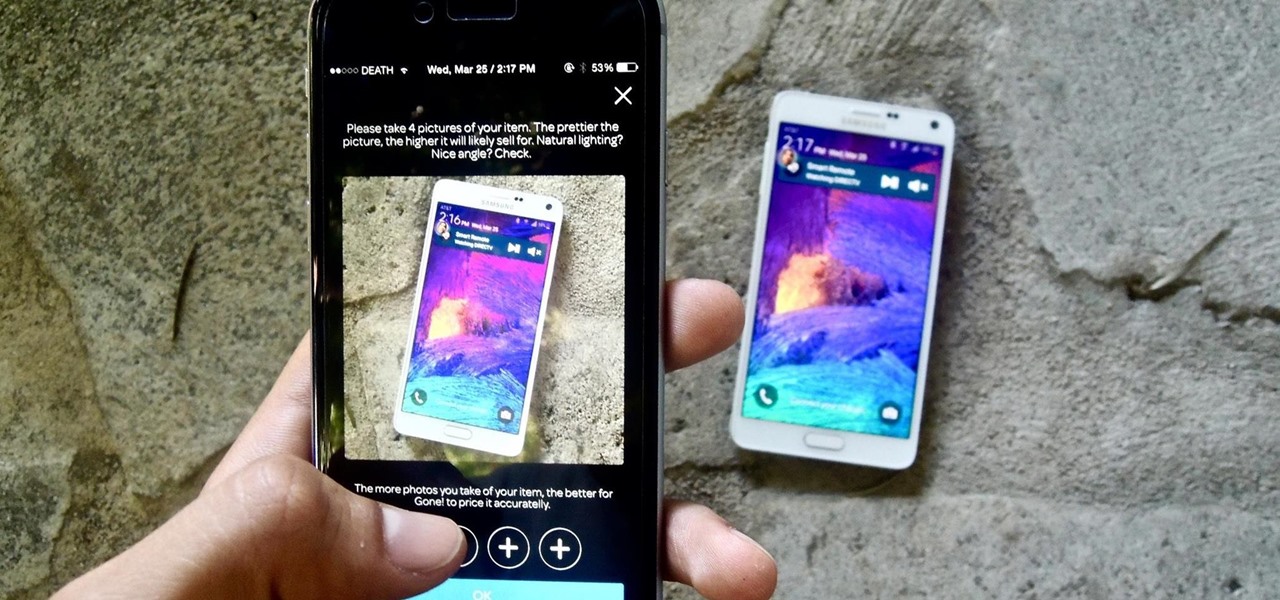
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedback. Craigslist is a little bit easier, but usually requires you driving somewhere to meet the buyer in a public place (if you want to play it safe).

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

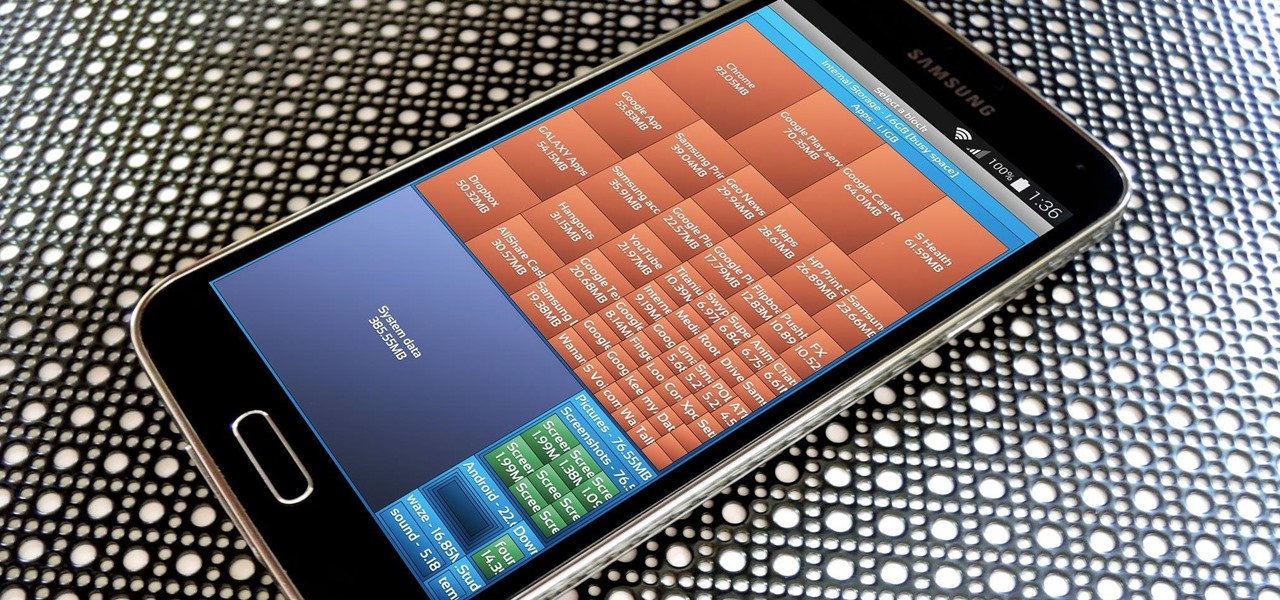
The more we use our smartphones, the more storage space becomes occupied—it's an inescapable fact. But as the data accumulates and chokes off our storage, it can become difficult to identify exactly which files are occupying the most space.