It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.
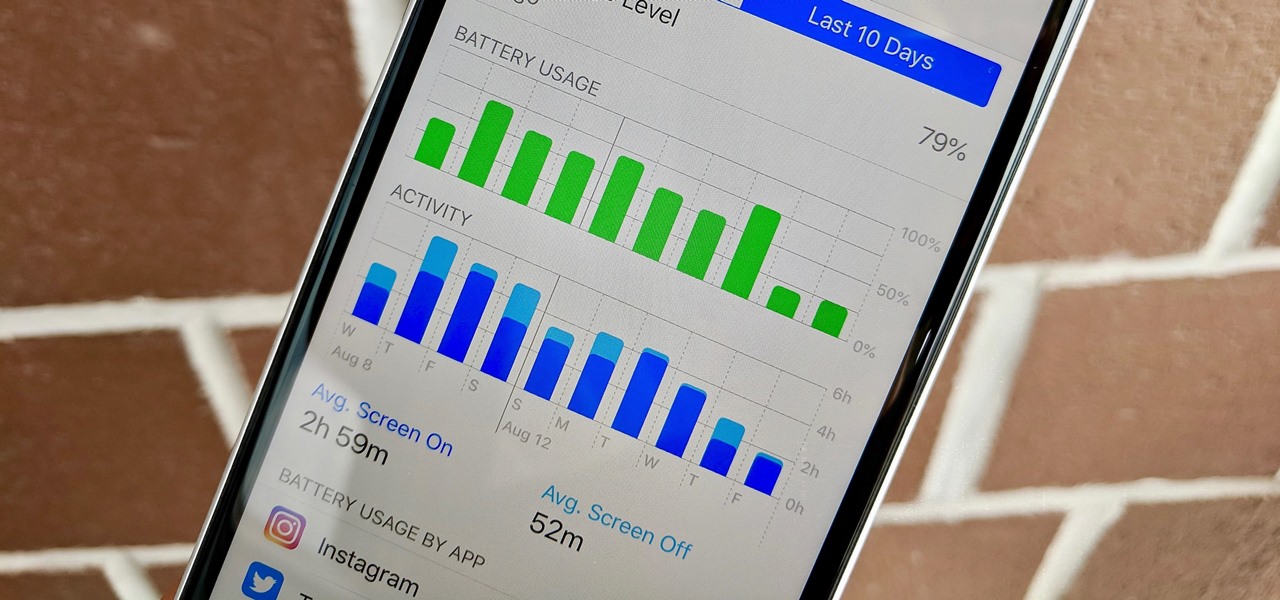
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Magic Leap CEO Rony Abovitz doesn't engage in tweetstorms often, but when he does, those tweets are bold, exceedingly confident, and there's usually a strong takeaway regarding what the company is or isn't doing. But on Thursday, Abovitz's latest tweetstorm sent an unusually flustered message: We promise, the magic we're telling you about it better than anything you've seen on video.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

One of the best gifts that someone with an iPhone can receive is a paid app, hot new movie, bestselling album, gift card, or anything else in iTunes, Books, or the App Store that costs money. Even if it's a small $0.99 game that you heard a friend talking about, a gesture like this can go a long way. Gifting apps and media is now easier than ever, even if you don't have an iOS device yourself.

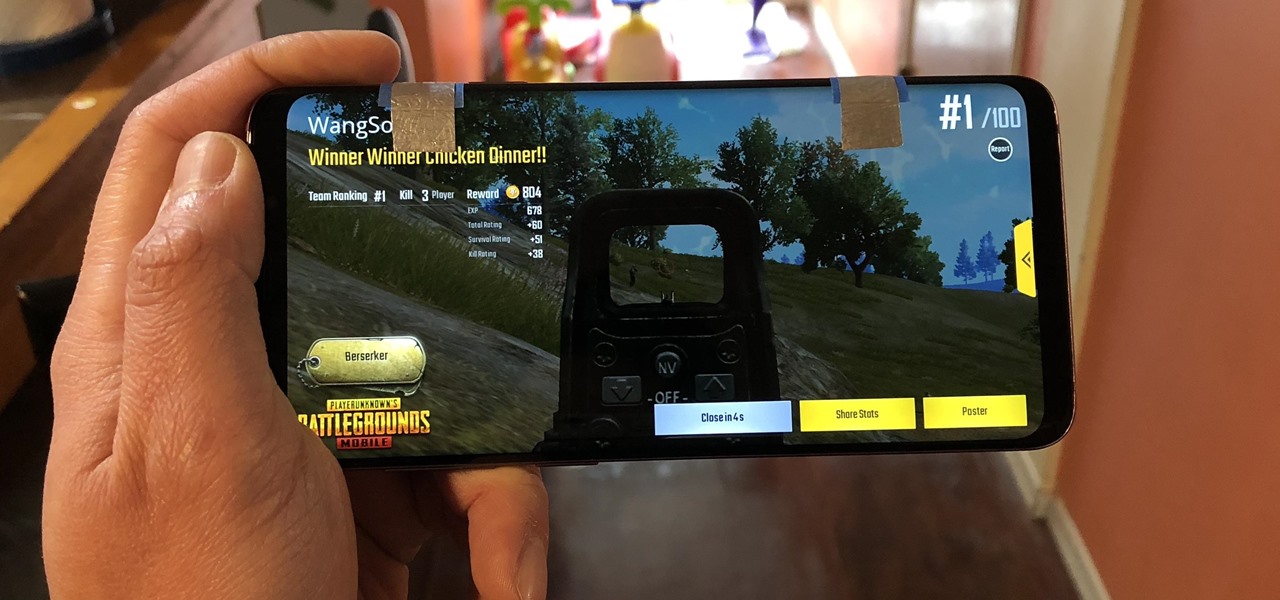
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

Samsung hopes to make a splash with the new Galaxy Note 9 to make up for the underwhelming sales of its signature Galaxy S9 series. This flagship is a radical departure from its predecessors — it's now optimized for gaming and paired with the most advanced S Pen stylus to date. Here's everything you need to know.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

Sure, emojis are all the rage, but there's not an emoji for every emotion or feeling just yet. That's where emoticons come into play, emoji's older typographical sibling. Unfortunately, emoticons can be hard to type out, easy to forget, and ASCII art, in general, can be pretty time-consuming to create from scratch — but there's an easy way to forgo all these issues — make keyboard shortcuts.

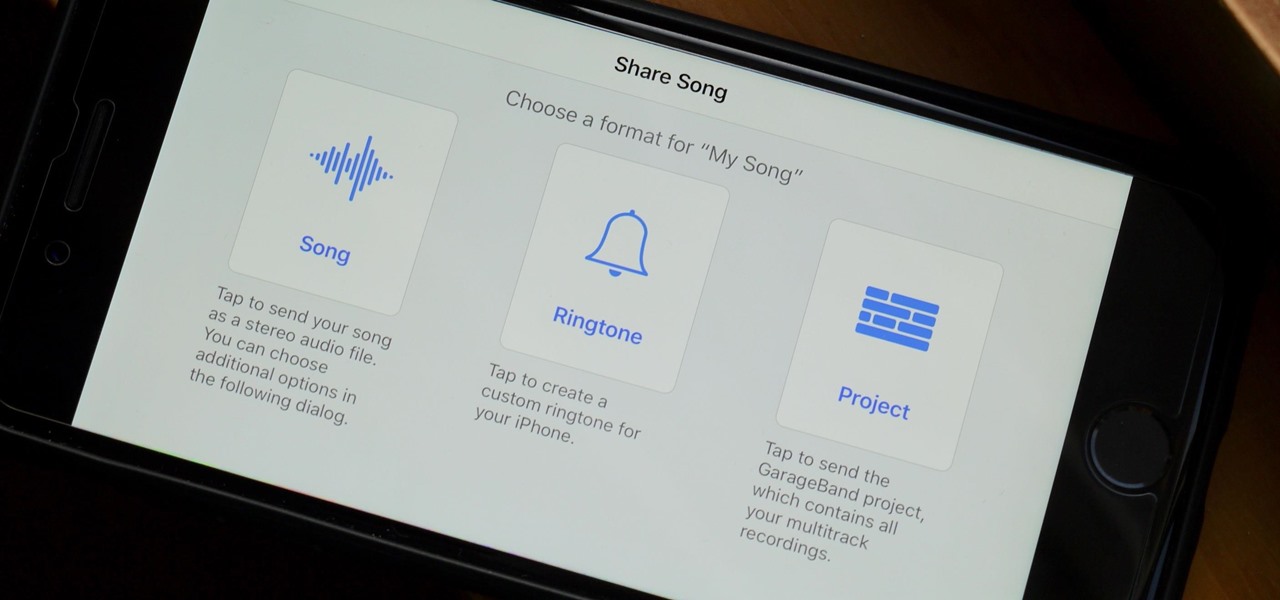
When you make an awesome song or beat that you're proud of in GarageBand for iOS, one way to show it off is to turn it into a ringtone or alert tone for your iPhone. That way, anytime you get a phone call or a notification, your musical creation will sound off, and everyone around you will hear it in all its glory. Plus, it's way cheaper to make your tones than to buy them off of iTunes.

Nintendo set the internet ablaze Wednesday night with two big announcements. First, Nintendo revealed that the Switch's paid online service will begin in September (boo), but it was the other report that really got fans excited — Mario Kart is coming to your iPhone.

When OnePlus announced the 5T, many were disappointed that it wasn't shipping with Android Oreo. To curb some of this disappointment, OnePlus quickly introduced an open beta for both the 5 and 5T and promised that each would receive the official version by Q1 2018. Well today, OnePlus has met this promise and pushed the OTA out for the official stable version of Android Oreo.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

Get Out absolutely tore up the record books this year. And the wildest thing about it? It did so with the most ordinary looking characters and props ever (hence the shoestring $4.5 million budget). Which makes it a godsend for the time- and cash-strapped come Halloween. With Get Out, Jordan Peele is the first (and only) African-American writer-director with a $100-million film debut under his belt. The film is also the _all-time highest domestic grossing debut based on an original screenplay ...

Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you have a guaranteed hit for cosplay or Halloween.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Apple has something big in store for consumers in 2017 to mark the 10th anniversary of the iPhone. One major surprise is that Apple has decided to forgo on releasing a 7S in favor of a redesigned iPhone 8 and 8 Plus. To further commemorate its 10-year milestone, the Cupertino-based company has released the very exclusive iPhone X, garnering much excitement in the process.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

I think I hate this game. I don't really see how you can play more than 15 minutes of Tap Mania without smashing your head into a wall. You do nothing but tap. Tap, tap, tap. At least they got the name right.

When Google announced YouTube Red — a paid monthly subscription service that disables advertising, among other perks — many of us thought "just use an ad blocker." But it isn't really that simple.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.