Windows 8 and its new Windows Store have simplified the process for uninstalling and cleanly deleting applications from your computer. Removing applications in older versions of Windows required a few more steps: My Computer -> Control Panel -> Add or Remove Programs -> Find the Program -> Click Uninstall.

Ever wonder how to make an engine out of soda cans? Not even sure if it's possible? These videos will show you how to build a working Stirling engine out of cans and other general materials. Here it is in action:

This is a cool little trap that me and some friends came up with while messing around with TNT and redstone on a big platform in the sky. The reason we called it the 'Roof Lever Trap' is because it utilizes the ability to place levers on the bottom side of blocks, which was introduced in Minecraft 1.3.1.

A great regular character in all kinds of fantasy and science fiction art. There is always a rock monster. I go over my version. I love the variations on this kind of creature. If you like how to draw fantasy videos, or art videos, or drawing videos. This is a good source. Watch how I draw it in the video below.

Today, books in PDF are quickly accessible on the Internet, whether free or paid. You can easily read them on your computer or mobile device, but some still enjoy a printed version they can hold in their hands. Printing PDF volumes is a quick and easy task, but the only problem is binding them into a sturdy book, especially when they're pretty thick.

At one point in time, Tesla coils were actually used for things like wireless telegraphy and electrotherapy, but as technology advanced, they shifted to a slightly more enjoyable purpose—entertainment. What's even more entertaining than using a Tesla coil? Building your own. One of the best portable Tesla coils out there is this mini acrylic version by Daniel Eindhoven, aka TeslaCommander. It's made almost entirely of acrylic plastic, minus the steel sphere, and copper wire and tubing. When t...

Apparently it is possible to reduce 64,000 possible Master Lock padlock combinations down to just 100. The entire process is clearly illustrated in the below how-to from Mark Edward Campos. For an enlarged version, click here. Looking for something a little more interactive? We have loads of lock-picking tutorial videos. Here's one that demonstrates the same method (math as opposed to shim) outlined in the above illustration.

If you've used PowerPoint in the past, you're probably used to version available on Windows, but you can do even more in PowerPoint 2008 for Mac. There are tons of new features that slideshow builders will love, but sometimes you can never know about them unless someone tells you about them. The Microsoft Office for Mac team shows you all the great features in this how-to video.

Apple released the first developer beta for iOS 13.5.5 on Monday, June 1. The update comes on the same day Apple released iOS 13.5.1 to the public, which patched the unc0ver jailbreak, and 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, in addition to other new features.

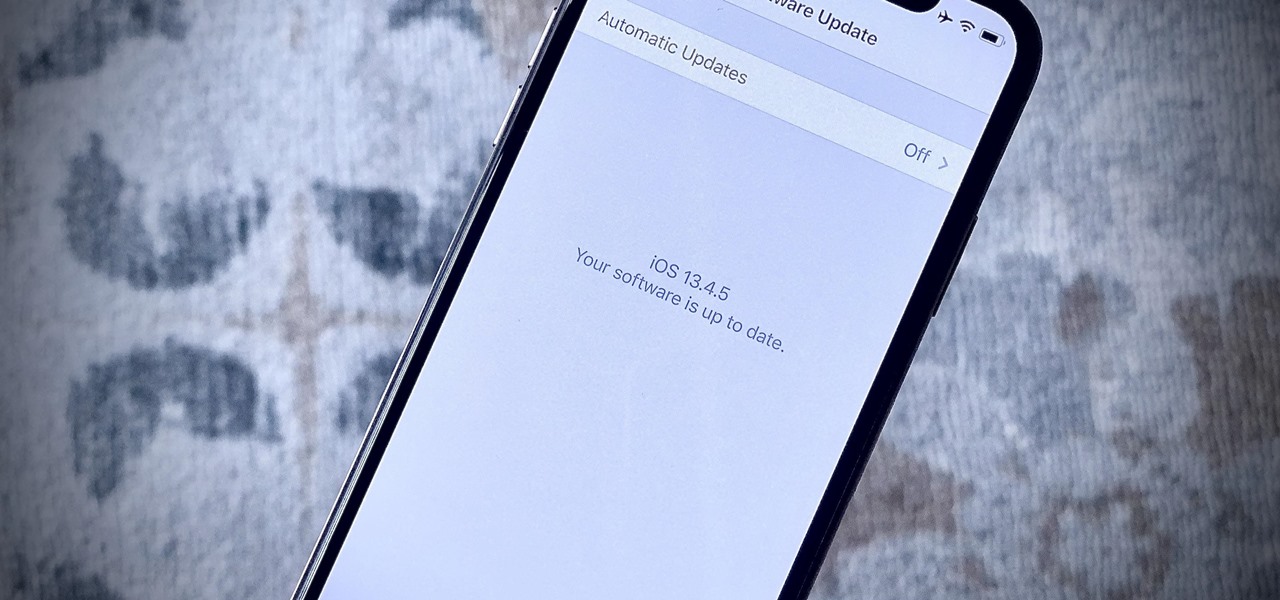
Apple just released the first public beta for iOS 13.4.5 today, Thursday, April 16. This update comes one day after Apple released 13.4.5 developer beta 2, which itself arrived just over two weeks after 13.4.5 dev beta 1.

Some of the oldest art on Earth was created 36,000 years ago on the walls of the Chauvet Cave in France. However, these days, physical access to the cave is restricted in order to preserve the site.

The sky is the limit when it comes to augmented reality, but Snapchat's latest innovation is keeping its AR platform grounded.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

The international profile of augmented reality startup Nreal continues to quietly rise thanks to gradual updates and various strategic branding opportunities.

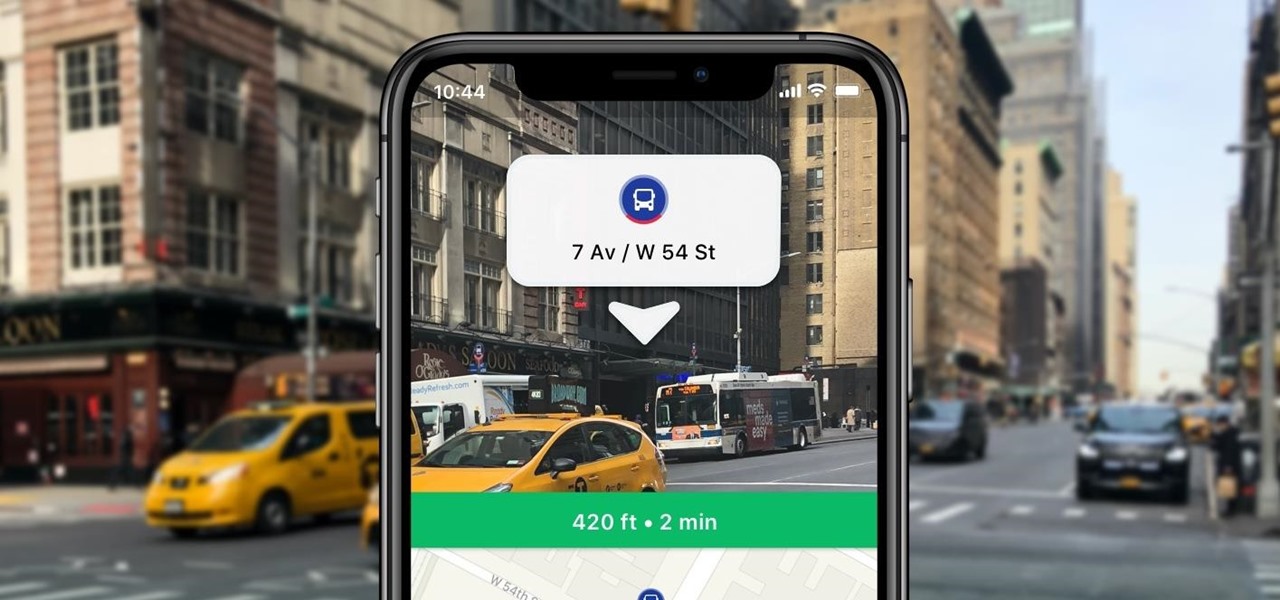
As helpful as it is, Google Maps isn't the only mapping app with augmented reality walking navigation anymore.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

The developer who gained notoriety for his What Disney Are You? augmented reality filter on Instagram is striking again while the iron is hot.

While "Baby Yoda" from The Mandalorian threatens to overshadow it, Star Wars: The Rise of Skywalker arrives in theaters next week, which means it's time for Disney and Lucasfilm to ramp up its promotional strategy.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

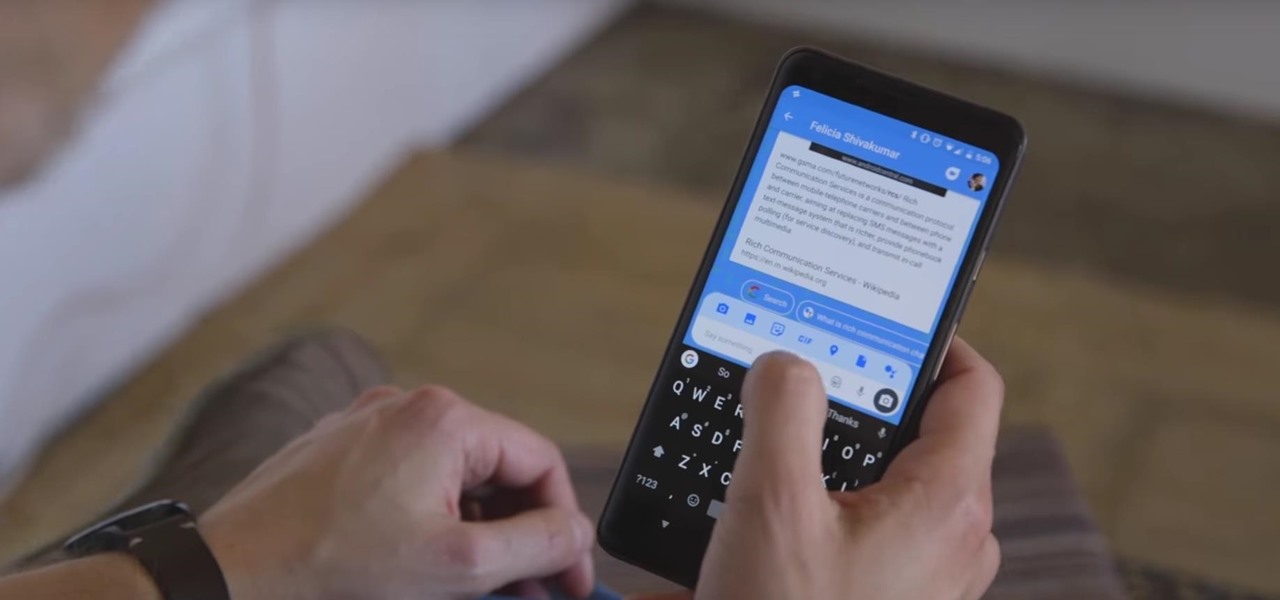
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

If you need to know whether you are really a Hufflepuff or a Gryffindor, then it's time to get yourself an augmented reality sorting hat.

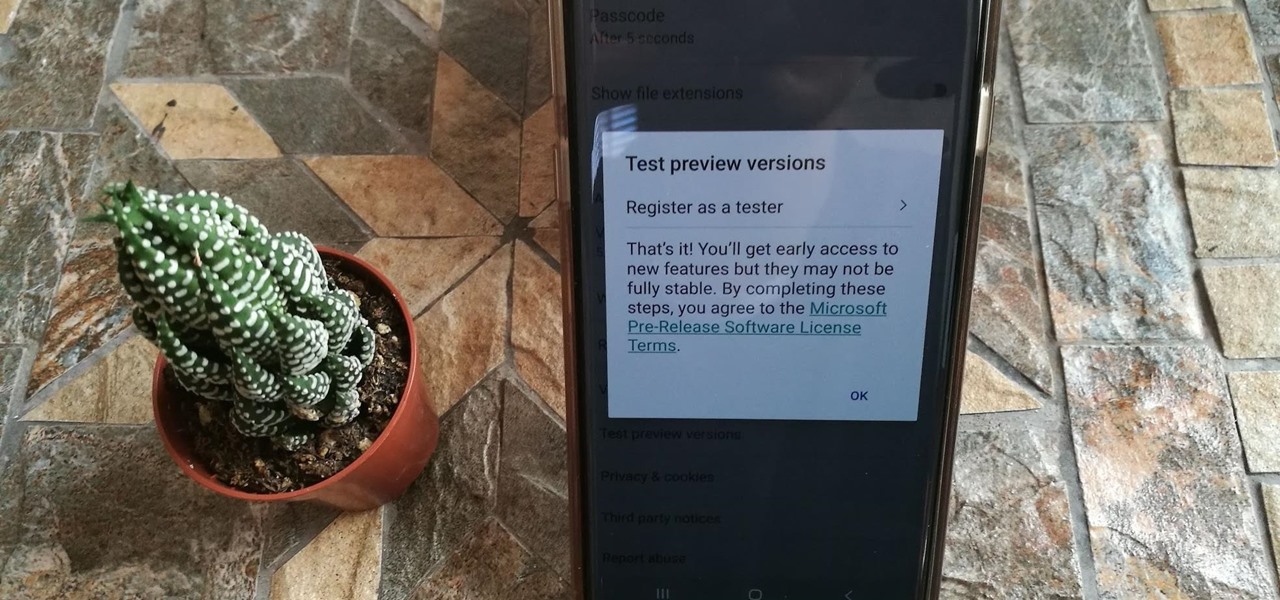
OneDrive has some really cool features, like being able to lock your files with a fingerprint. If you want to be on the forefront of these new features, you can sign up to the OneDrive beta testing program to get new feature before anyone else.

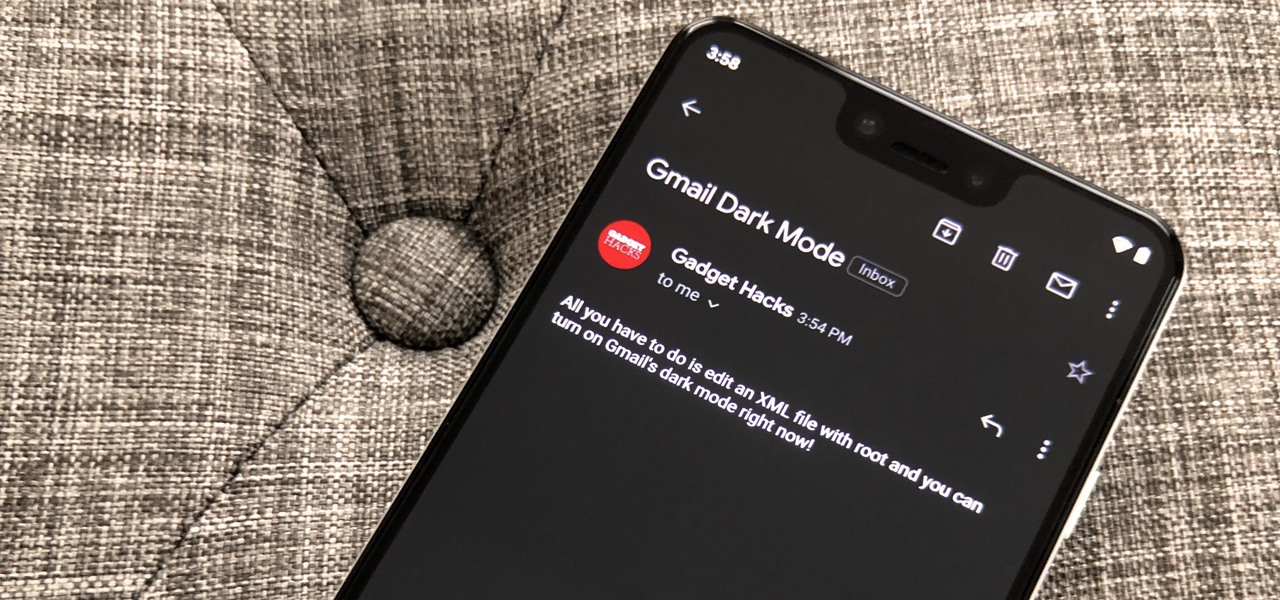
Dark mode is finally rolling out for Gmail on Android. But this is a Google product, so you already know it'll be a while before the server-side update hits most devices. Sideloading the newest APK doesn't work, neither does switching accounts. But if you're rooted, you can enable dark mode by modifying a simple XML.

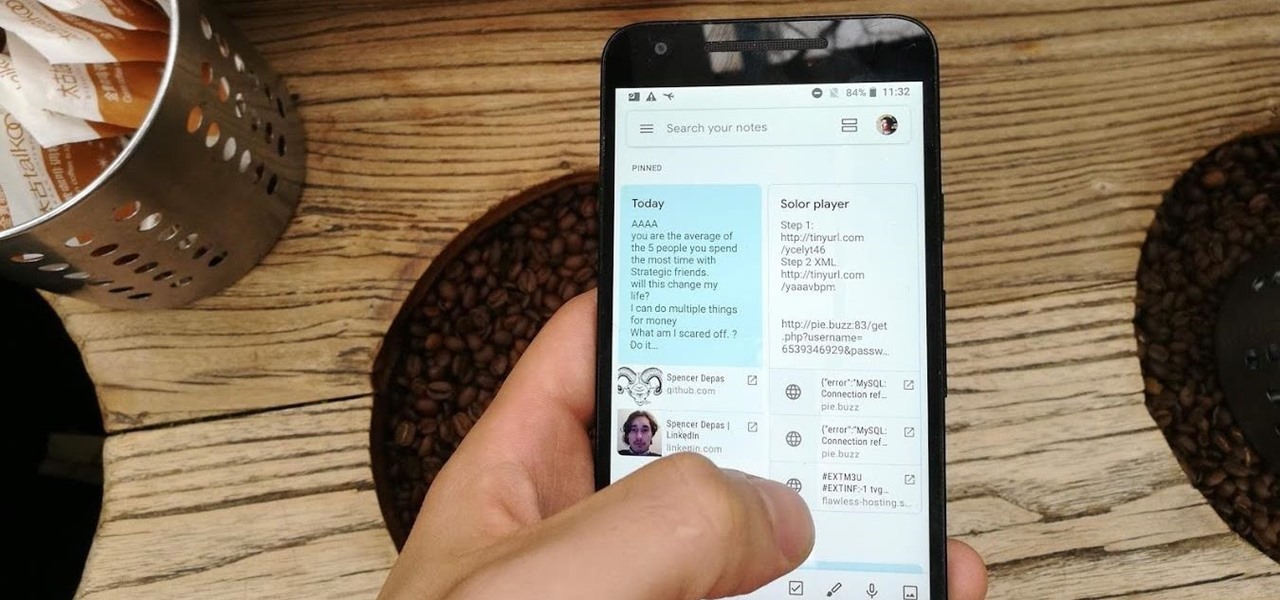
Disabling clunky, revealing link previews on Google Keep can serve multiple purposes. You know, those expanded versions of the same URL you pasted into your note, except duplicated, tacked onto the bottom of your note, and showing a preview picture. Removing these can help optimize your productivity formula.

You know the drill. You need answers, and your friend has them. The problem? It's way too late to text them. Maybe they have Do Not Disturb enabled. Perhaps they don't, and you wake them up, ruining their entire Monday. Don't be that friend. Instead, send a message silently with Telegram.

The mystery surrounding Overture, an app that showed up in the Magic Leap World app store along with the latest Lumin software release, has been cleared up.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

Google Keep now has a dark mode. If your device is running Android 10, it kicks in automatically when you turn on the system-wide dark theme. If your device is not running Android 10, you will have to manually switch on dark mode for each app, including Keep. The benefits of dark mode include increased battery life, reduced eye strain, and improved readability.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

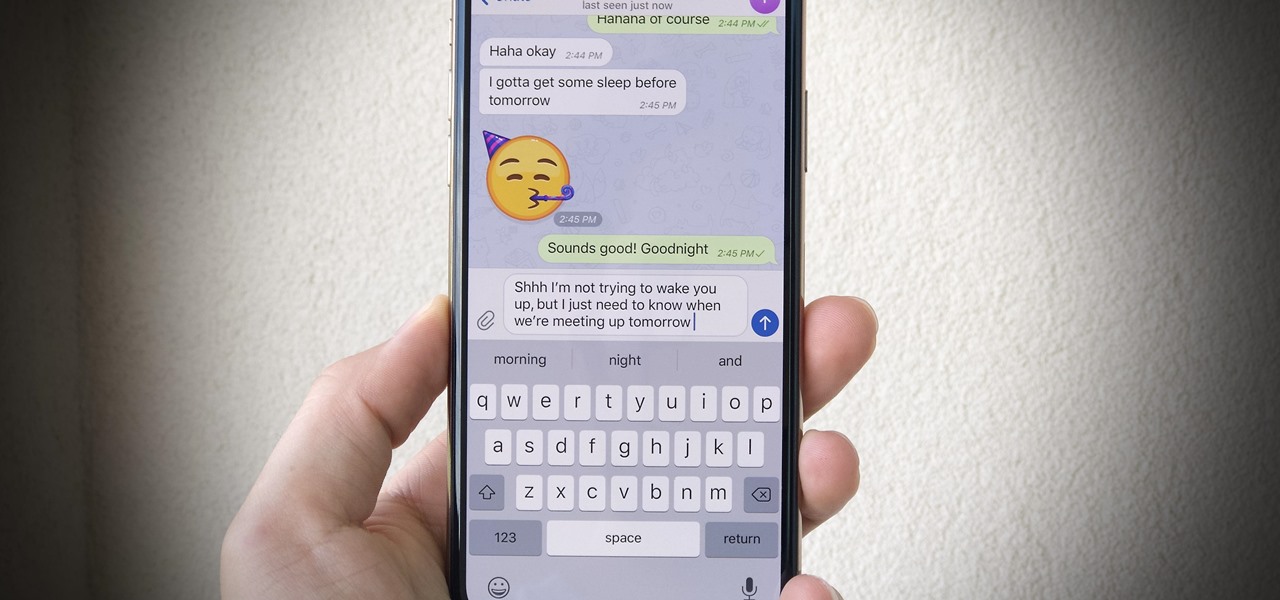
Message effects in iMessage lets you add a touch of flair to otherwise bland communications. With the feature, you can complement a birthday wish with a stream of balloons, send a congratulatory text along with a shower of confetti, or make the chat bubble slam itself in the thread. If you're on the receiving end, however, they may be distracting and even jarring.

If you don't want the large and permission-hungry Facebook app on your phone, the perfect solution is to create an app icon for the Facebook mobile site on your home screen. The website version of Facebook doesn't run background tasks, has no distracting notifications by default, you won't be giving Facebook as much data, and your phone's battery life will be improved.

If you've been putting off upgrading your iPhone or iPad, you might want to start shopping for a current-generation device to take advantage of the latest capabilities in ARKit 3.

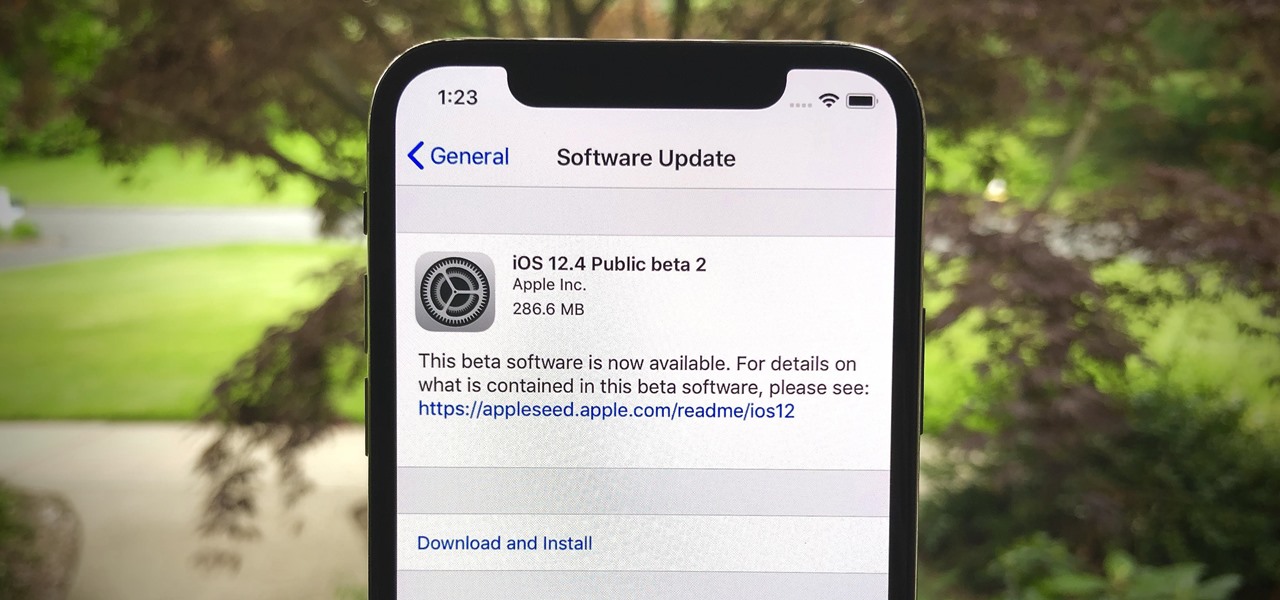
Public beta testers, you're in luck. Apple just released the second iOS 12.4 public beta today, May 20. The update comes five days after the release of the first developer beta for iOS 12.4 and seven days after the release of iOS 12.3. Public beta 2 and dev beta 2 were both released at the same time, something that doesn't happen often.

Many native New Yorkers, like myself, get a chance to visit the famed Statue of Liberty during school trips when they're a child in grade school. And if you're not lucky enough to be born in the city, you have to make a special trip to the monument as a tourist.

Fresh off of shipping version 2019.1 in April, Unity has already dropped the beta of 2019.2, and it has a bunch of new AR Foundation toys to test.

On Monday, the Microsoft Build conference kicked off, showcasing a series of demos that went off without a hitch — except for one big one.

It turns out that the video Magic Leap released earlier today was indeed a teaser for the public release of the Game of Thrones experience for meant for all Magic Leap One users.