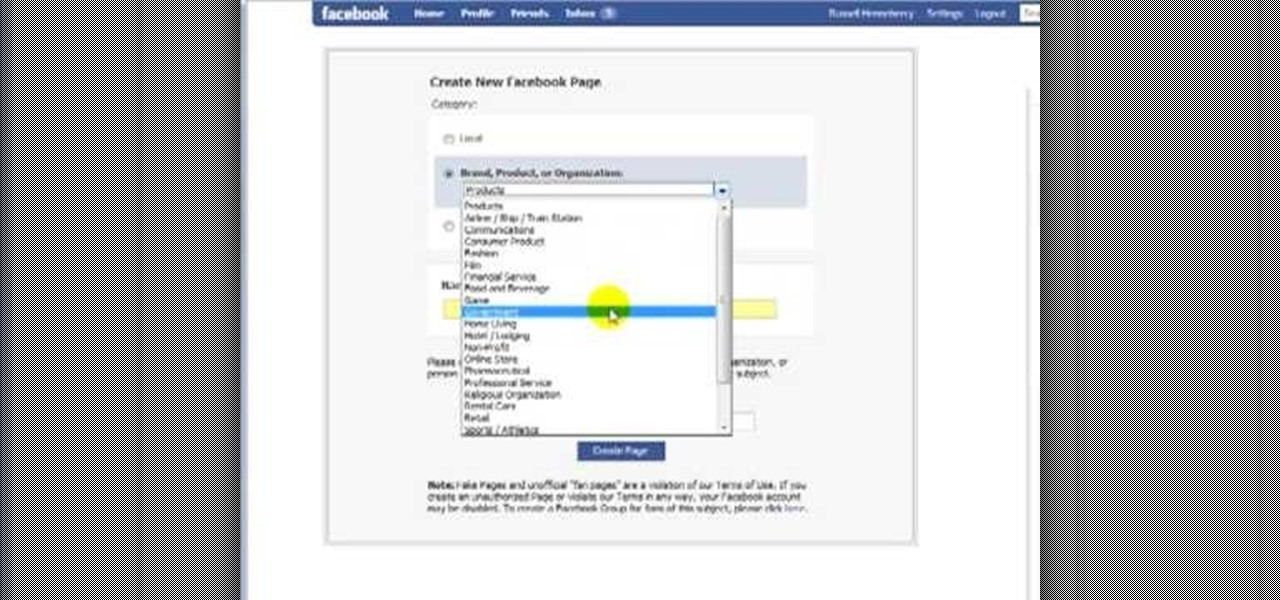
First, you must log on to your personal face book page or create one if you do not already have, but don't log in yet. Then at the bottom of the face book home page click the click here sign within the words to create a page for a celebrity, band, or business click here. Now that you are on this page log in. You will be able to select what you are. Enter name of your website, now select that you are authorize to create this page. You must then enter your electronic signature, which is the exa...
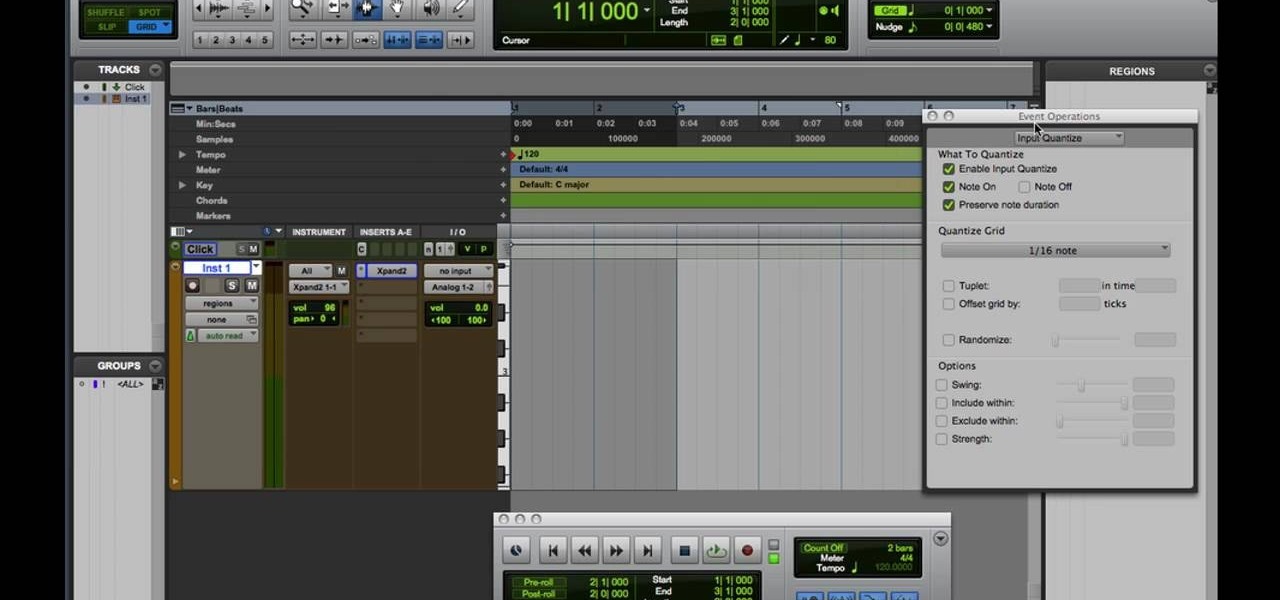
This video shows a quick and easy way to create a drum loop using "MIDI MERGE". A stereo instrument track with expand 2 is used here. First, select a track, expand 2, and select session drums (you can take any other track) for the patch and also create a "click track" which will be available in the track menu. Open the transport window and select "loop playback". In order to create a looped playback, right click on the "play" button and select "loop". This is a loop, so make sure that you do ...

Just got piad? Turn your check into dollar bills by endorsing it at the bank. Don't know how? Watch this.

You don’t have to be a slave to fashion to pick the right shoes for your outfit. Follow these tips for a put-together look.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

"Smells Like Teen Spirit" is a famous grunge song by Nirvana that has a signature rock beat. Learn how to play drums for "Smells Like Teen Spirit" in this free cover songs and drumming technique video lesson.

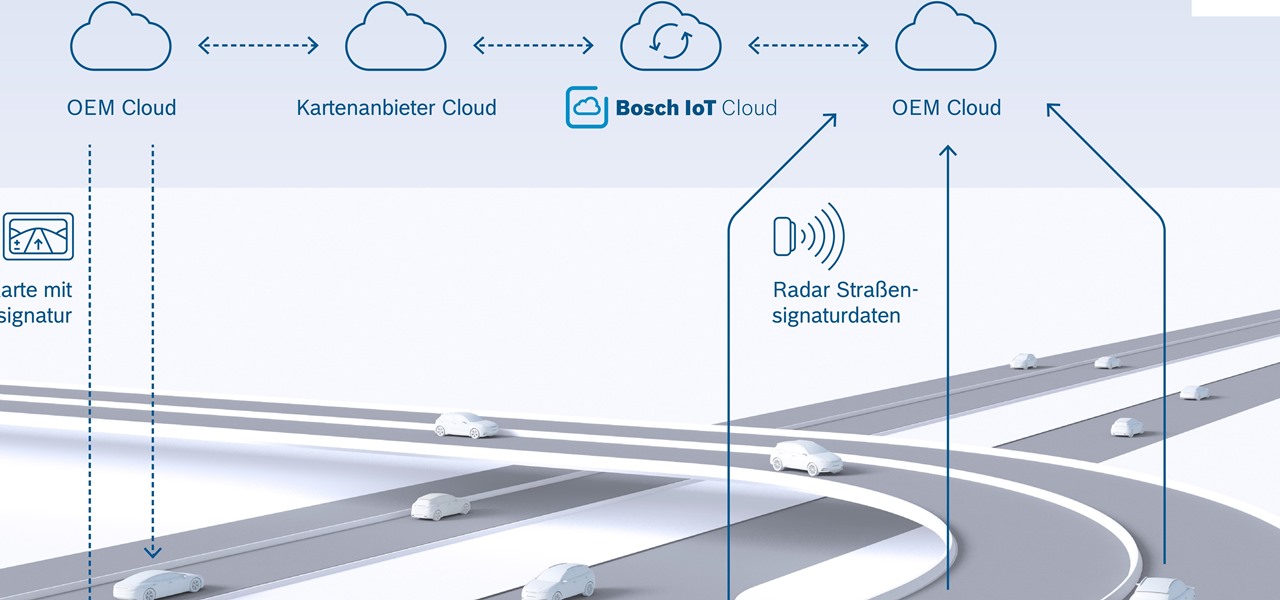
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

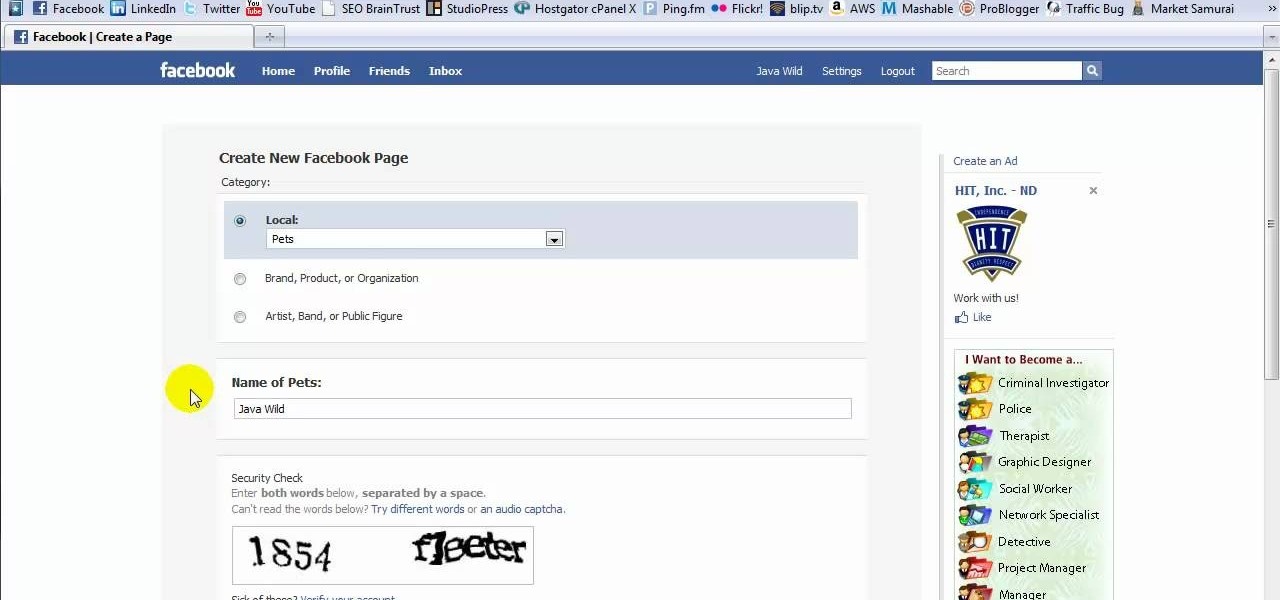
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

Learn how to practice proper etiquette on a BlackBerry, smartphone or PDA. Make sure your love for your BlackBerry or other PDA device isn't making you obnoxious.

Turn your possessions into cash and become an online selling machine. You will need: Something to sell, a computer with internet access, an eBay account, a digital camera, shipping supplies, something to sell,a computer with internet access, an eBay account, a digital camera, & shipping supplies.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

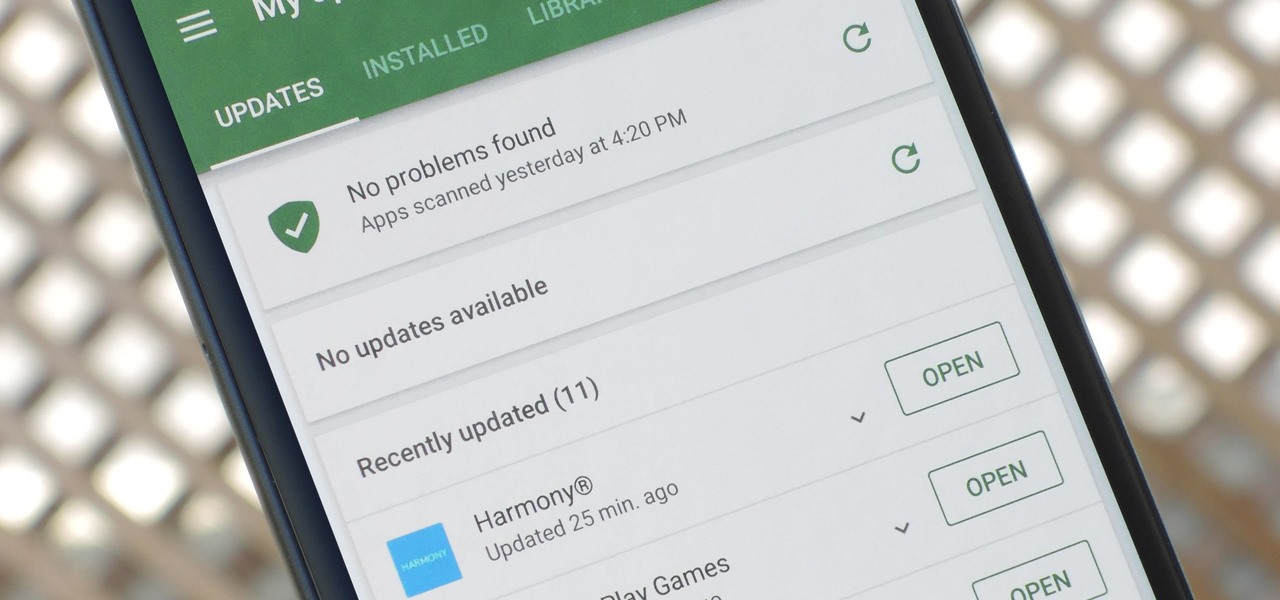
App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Every girl dreams of achieving glamour with ease like the fabulous Taylor Swift. Her signature red lipstick makeup look helps her to stand out from the crowd. Watch this video to learn how you can get Taylor Swift's red lipstick look without looking like a clown.

While it's true that all of the Victoria's Secret Angels were born genetically blessed (and somehow big-bossomed and skinny all at once), at the annual Victoria's Secret Fashion Show even they require a football team of makeup artists and hairstylists.

If you haven't already seen her face plastered in front of every Victoria's Secret store and catalog cover, then you certainly will tonight, when the annual Victoria's Secret fashion show airs. Marisa Miller is one of Victoria's Secret's veteran supermodels. The lady has killer curves, bombshell hair we can only dream of having, and beautiful, sunkissed skin.

Loose waves are the hair signature/calling card of summertime beauty, so indulge yourself in this sex goddess inspired look by watching this tutorial.

Watch this piano tutorial video to learn how to play "In the End" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "In the End" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Faint" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "Faint" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Haruka Kanta," the second Naruto opening, on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play "Haruka Kanta" from Naruto on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Breaking the Habit" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "Breaking the Habit" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "From the Inside" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "From the Inside" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Wake Me Up Inside/Bring Me to Life" by Evanescence on the piano. Instructions include the scale and key signature and chord breakdowns. Beginners and intermediate pianists will be able to learn how to play Evanescence's "Wake Me Up Inside" by watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Yesterday" by the Beatles on the piano. Instructions include the scale and key signature and chord breakdowns. Beginners and intermediate pianists will be able to learn how to play the Beatles' "Yesterday" by watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Let It Be" by the Beatles on the piano. Instructions include the scale and key signature and chord breakdowns. Beginners and intermediate pianists will be able to learn how to play the Beatles' "Let It Be" by watching this helpful how-to video.

Watch this piano tutorial to learn how to play My Chemical Romance's "Disenchanted" on the piano. Instruction includes key signature and scale, chord breakdown, and melody. Pianists of any level will find this instructional video helpful in learning how to play "Disenchanted" by My Chemical Romance on the piano.

This walks you through how to create an animated GIF image file that can be used in websites, as avatar's, as icons, etc. You'll be using Microsoft Paint to create each frame of the animation, and an application called Unfreez (found here) to animate them together.

In this tutorial, you'll be learning the basics of clipping or masking. And how it can be used to apply effects to a signature. If you're starting off with Photoshop, or completely new to Photoshop, This tutorial will explain how to make a clipping mask.

This lesson covers six odd-time beats that are played in the 5/4 time signature. Unlike most rock drum beats, that are played in 4/4 with four quarter notes per measure, these beats are played with five quarter notes per measure. Watch the included video for step-by-step training on how to count and play these unique beats.

This lesson includes six drum beats that are played in the 7/4 time signature. They are all considered odd-time, due to the fact that they aren't counted like popular 4/4 drum beats. The beats are still counted with quarter notes, but include seven in each measure instead of four. Watch the included video for adddition information.

In this video lesson, you will learn how to count quarter notes within the 4/4 time signature. This will lay out a solid foundation for learning other sub-divisions of time, including: eighth notes, eighth note triplets, sixteenth notes, sixteenth note triplets, and thirty second notes.

We've seen how to digitally sign PDFs in Acrobat before. However, in this tutorial not only do Terry White show you how to do it in Acrobat 8 Professional, but he also shows you how to take your signature to the next level with your own picture.

A specialty among select Miami bars, Purple Rain is a sweet martini with a layering technique that gives the drink its signature purple glow. You will need vodka, wild berry martini mix, cherry juice, a shaker filled with ice, a spoon for layering effect and a purple orchid to garnish.

If there was anything missing from the notorious YO app, it was Aaron Paul's character from Breaking Bad, Jesse Pinkman, calling me by his signature catch phrase—you know the one.

While it doesn't come with any iPad models out of the box, the Apple Pencil is perhaps the best iPad accessory you can get. It's a powerful writing and drawing tool with an intuitive design and user-friendliness that makes it easy to take notes, draw sketches, mark up documents, and more. And there's a lot you can do with it — some of which you may not have noticed yet.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.