Apps that save your passwords have been around for quite a long while. But apps that complete the entire login process automatically? Now that's a different story.

How many times do you misplace your phone? Once a day? Twice? As much as you may hate losing your phone, it always seems to happen, and finding it isn't very easy if you left it on silent mode.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

Stock Android has come with lock screen widget support for a couple of years now, ever since the days of the first Ice Cream Sandwich build. But for some reason, Samsung decided to remove this feature in the Galaxy S5.

Want to learn how to make Peppa Pig with Play-Doh? Here is our attempt on showcasing a tutorial on how to make Peppa Pig with Play-Doh.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

To-do list and reminder apps are a dime a dozen on Google Play, so trying to find the right one for you could take hours as you sift through hundreds of similar apps and widgets. Well, search no more, as we've found one of the most well-designed and easy-to-use reminder apps out there.

Your beloved Samsung Galaxy S3 is nearing the end of its life cycle. Sure, it can do most of what newer devices can, especially if you were lucky enough to receive the KitKat update, but your diminishing battery and scratched up screen have seen better days.

Whether it's bad timing, or some trying-to-be-funny photobomber, it sucks having a photo ruined by someone or something getting in the way. While you can always retake the photo, it's simply impossible to capture the moment you intended, no matter how much restaging you do. But with an HTC One, there's no need to retake anything, as we have access to built-in features that will remove those photo intruders.

Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left these two aesthetic features hidden away. Luckily, with root, you can easily enable them with just a few quick edits.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

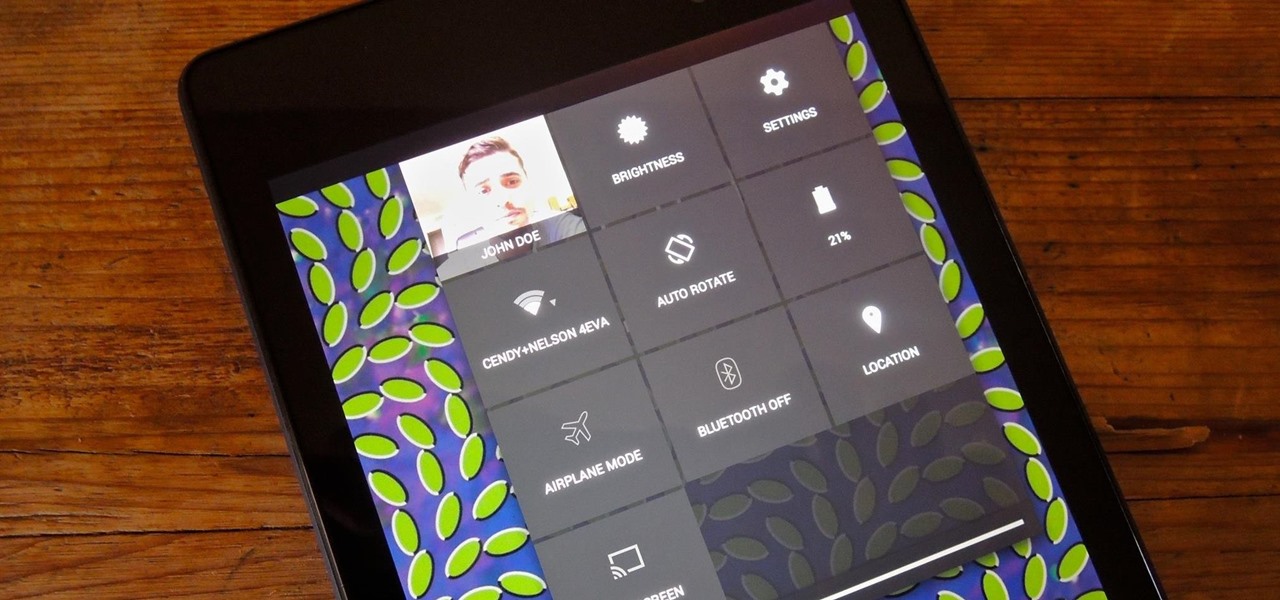
Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

Notifications, while certainly helpful, can at times be overbearing. There are banners plastered every which way on your smartphone for almost every application. While many of the notifications can simply be swept away or turned off, the same can't be said of persistent notifications.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Midway through 2013, a popular custom ROM called Paranoid Android introduced their multitasking feature "Halo." Bubble-style notifications inspired by Facebook chat heads pop up near the top of the screen, and you simply tap on them to bring up the app in a floating window.

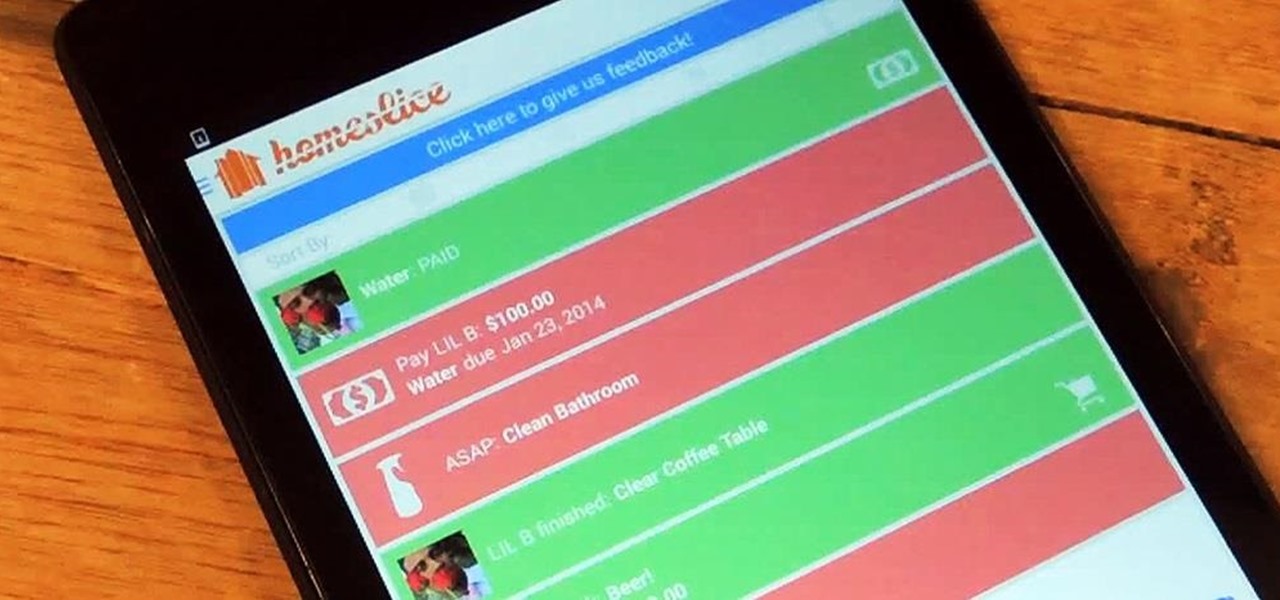
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!

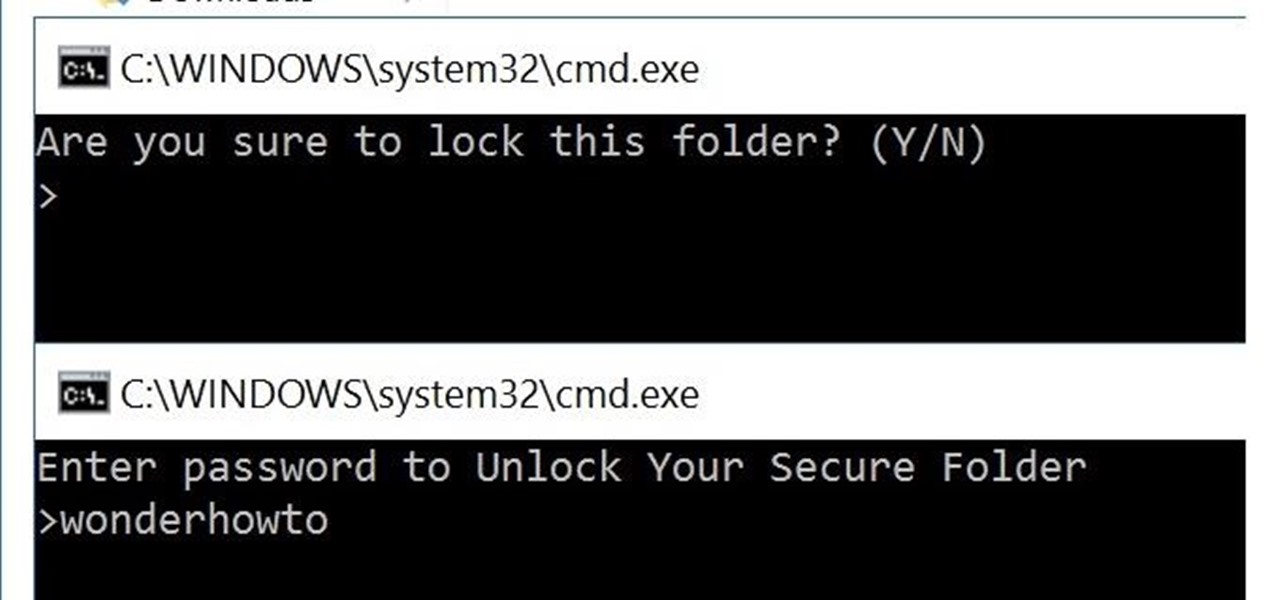
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

A great aspect of using Android is having the ability to change and tweak aspects of the user experience to your liking. You can easily change things like home screens, widgets, and icons on your Nexus 7 tablet, but also core system settings if you want, like volume settings. Most stock systems come standard with a "15 step" volume control. That means simply that you have 15 levels from mute to the loudest volume settings. Whether your an audiophile or just someone who wants a little more con...

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

What is your Samsung Galaxy Note 2 running? More than likely, you're still rocking Jelly Bean 4.1.2, which is already pretty outdated. My grandma uses 4.1.2.

There may only be a few hardware buttons on your Samsung Galaxy Note 2, but when they're not working, your phone might as well be a doorstop. A few years back, I was texting while walking to class and a student on a bicycle crashed into me. My phone was flung thirty feet—straight into a puddle. I picked it up and checked for damage, but everything seemed okay. The biker apologized profusely, but nothing was wrong, so I told him not to worry about it and proceeded to class.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

You know that moment when you finally figure out something, but you figured it out years after you really needed it? Don't you freaking hate that?!

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

Whether you're at work or in class, there are times when using your phone is unacceptable, regardless of that subtle yet sudden twitch in your arm that arises every time you hear the vibration of a text message.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

I can definitely say that my MacBook is one of my best friends, but I was still very disappointed when I realized that the only game my laptop came with was chess. For starters, I'm not very good at chess. I haven't even beat the computer once, which really grinds my gears. But, it has come to my attention that chess isn't the only pre-installed game on my Mac—there seems to be some hidden gems that I simply wasn't cool enough to know about. For some of you, this may be old news, but for me, ...

Being politically correct on social media sites is super boring. I've had my fair share of rage tweets and angry Facebook posts with some colorful wording, but sometimes using and F-bomb just gets the point across better. Now that Facebook is pushing out their new Graph Search, it might be time to clean up your profile. FaceWash is a web app that searches your Facebook profile for common bad words. You will need to give the app permission to access all of your wall posts (or course). Once acc...

Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

At first glance, the iOS home screen looks nearly identical to the original release back in 2007. Though those experienced with the evolving iterations of iOS will tell you that the features have changed. Furthermore, with the App Store continuing to explode with (lets face it) better options than the stock software, these included applications are only causing clutter across the springboard.

With presidential voting going down on Tuesday, November 6th, voters are beginning to anchor down on their choice for president. But with the way the media works, this may be difficult for some people because the news sites they listen to give conflicting and sporadic information on the candidates.

Did you buy your new iPhone 5 without a contract? We'll, if you bought it from Apple, AT&T or Verizon, you can have it unlocked pretty easily. Why Have It Unlocked?