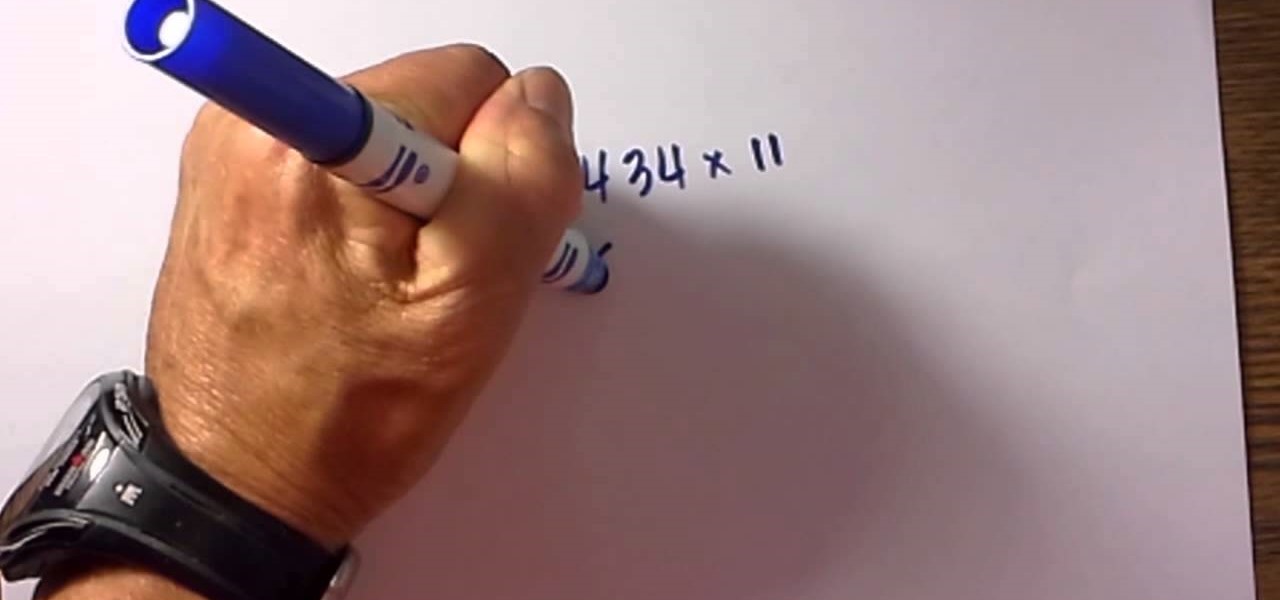Ah, wine. The bouquet fills your nose. The rich finish fills your mouth with soft flavors of oak and raspberries. The wine warms your belly and soothes your mind. Yeast and their biochemical factory help create this feast for your senses. Thanks to a research group from France, we now have a little more information on how that process works and a little more appreciation for yeast's contribution.

These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the lighting throughout your house can be controlled from your computer or smartphone. You could also use artificial intelligence; Simply tell Amazon's Alexa what you want your house to do, and she will do it.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

Mirror, mirror on the wall, who's the smartest of them all? Since Max Braun's Medium post went viral back in January of 2016, smart mirrors have been appearing on tech blogs in all shapes and sizes. Some are technically sound, some incredibly easy, but all are visually compelling. However, we've never seen one with a fully functional operating system and gesture support—until now.

Apple is famous for keeping a tight grip on the look and feel of iOS (a grip so tight it may even change the future of patent law), but the clever folks over at heyeased found some neat tricks to put the control back in your hands.

Koji is a culture made up of a certain fungus (mold) called Aspergillus oryzae, which has been used to ferment rice and soybeans in Japanese, Chinese, and Korean kitchens for centuries. Koji can actually have other involved fungi, but Aspergillus oryzae is the most common, and therefore the names can be used interchangeably. Its end purpose is to enhance the flavor of items like soy sauce, sake, and miso.

There may be no other crustacean with as many names as the crawfish: crayfish, crawdad, crawdaddy, mudbug, Florida lobster, spiny lobster, rock lobster, and freshwater lobster (to name a few). But no matter what you call it, there's no denying that it's a popular delicacy in the South and beyond.

A whole grilled pineapple is the perfect party dessert. It's beautiful, provides a natural centerpiece before you eat it, and can be sliced right on the spot and served with a dollop of ice cream. (Fresh mint leaves and a splash of liqueur on top taste pretty good, too.)

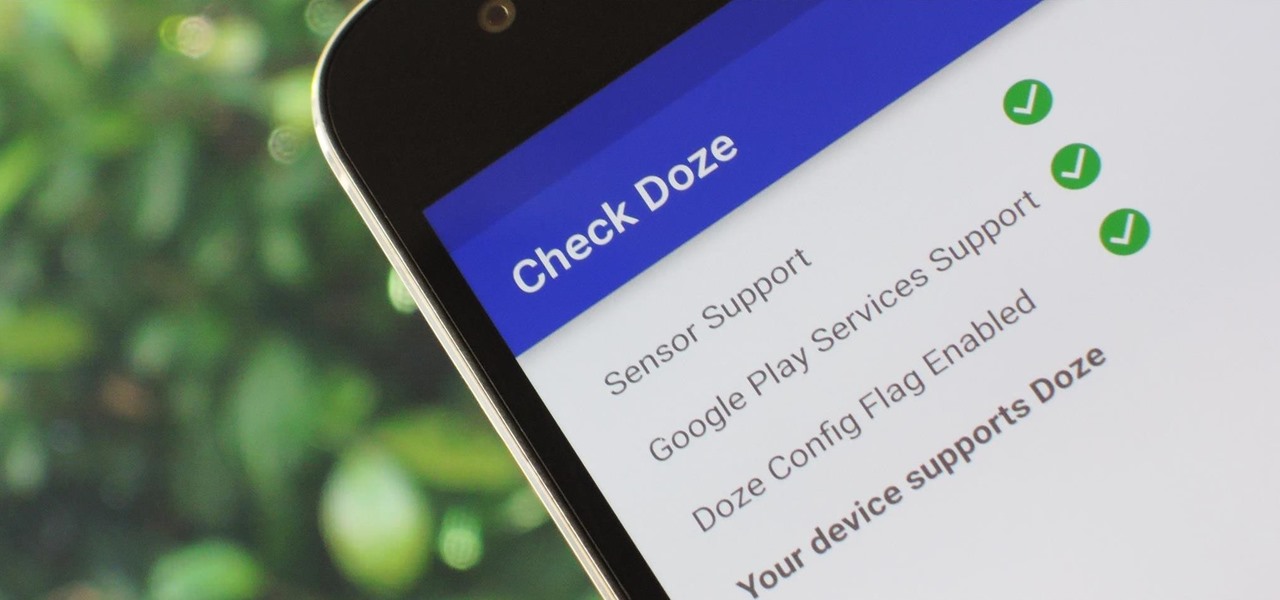
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.

Samsung has been on a tear with its flagship devices since the release of the Galaxy S6; The S6 edge, the Note 5, and this year's Galaxy S7 models have all been met with universal acclaim, and even the staunchest of critics have almost nothing negative to say. Almost.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" there are a few likely causes—and we've got you covered with troubleshooting tips and simple fixes below.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

When roast chicken is concerned, perfection is hard to attain. The reason for this is surprisingly simple: the light meat and the dark meat should be cooked to different temperatures. Ideally, chicken legs should be cooked to at least 170°F, while breasts should be cooked to 150°F. Naturally, this poses a conundrum: how can you cook two parts of the chicken to two different temperatures, without taking the bird apart?

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

When they were purchased by Google back in 2011, Motorola underwent a sweeping change in software philosophy. All throughout the UI on their flagship devices, edgy design patterns were replaced by clean, minimalist interfaces akin to vanilla Android. This philosophy has continued on as Motorola's signature, even though they have since been sold to Lenovo.

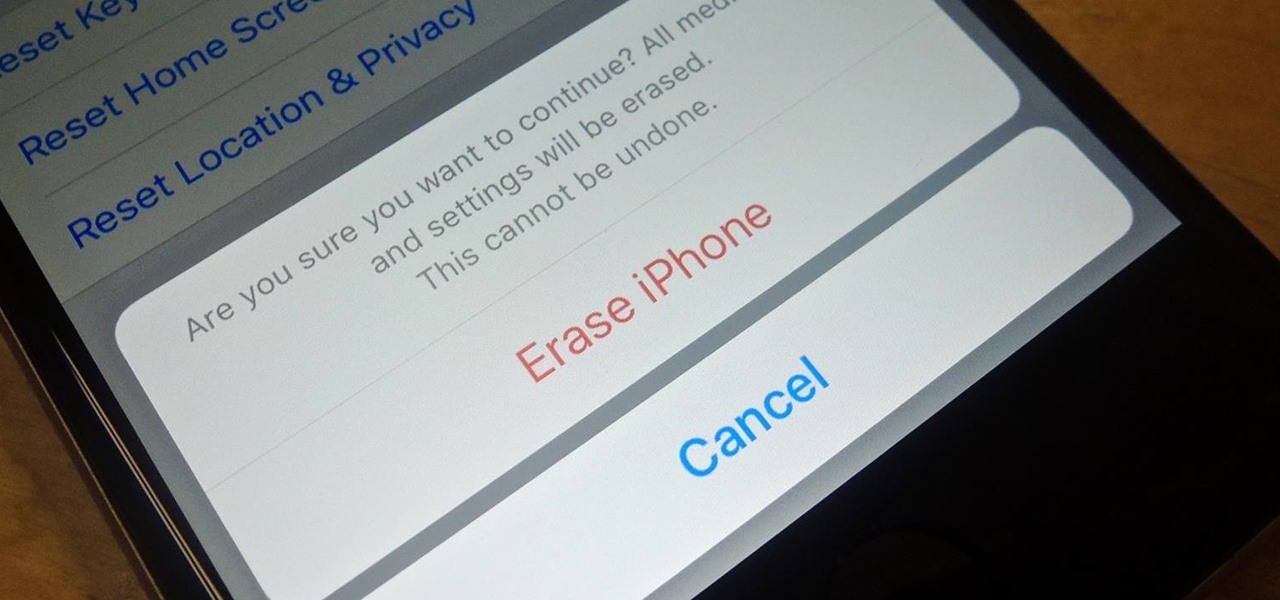
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Hello~ Here is a short video on how to do a simple hairstyle for when you are wearing a Korean Hanbok.

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

With every version bump, Android gets a new Easter egg that can be accessed by tapping the "Android version" entry in Settings. For the most part, these have generally been little animations or live wallpapers that depict the Android code name, but starting with version 5.0 Lollipop, things got a bit more interesting.

Fresh loaves of bread from the bakery are both delicious and often free of the preservatives that come with buying sliced, bagged bread off the supermarket shelves. However, these same loaves of bread tend to become stale much more quickly when sliced. It's quite the dilemma, especially for those who want to avoid throwing away and wasting stale bread (or are tired of turning said stale pieces into breadcrumbs or croutons).

With the explosive popularity of both Thor himself and The Avengers, Thor is an obvious good choice for a Halloween costume. But you don't have to opt for one of the pricey, pre-made costume choices found in every Halloween store in every city. Instead, craft your own in just a few steps, saving yourself money in the process.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.

Yes, with this simple technique you can multiply 2 digit numbers in your head. The video also reviews a really easy method for multiplying larger numbers by 11 in a simple fashion.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

The horizontal dotted icon in your iPhone's status bar serves as an indicator of your device's network strength. And while it does help provide an approximation of how strong your signal is, swapping it out to display an actual numeric value is a lot more precise and can change up the look of your iPhone (or at least the status bar). The process is quick, painless, and you don't even need to jailbreak your phone.

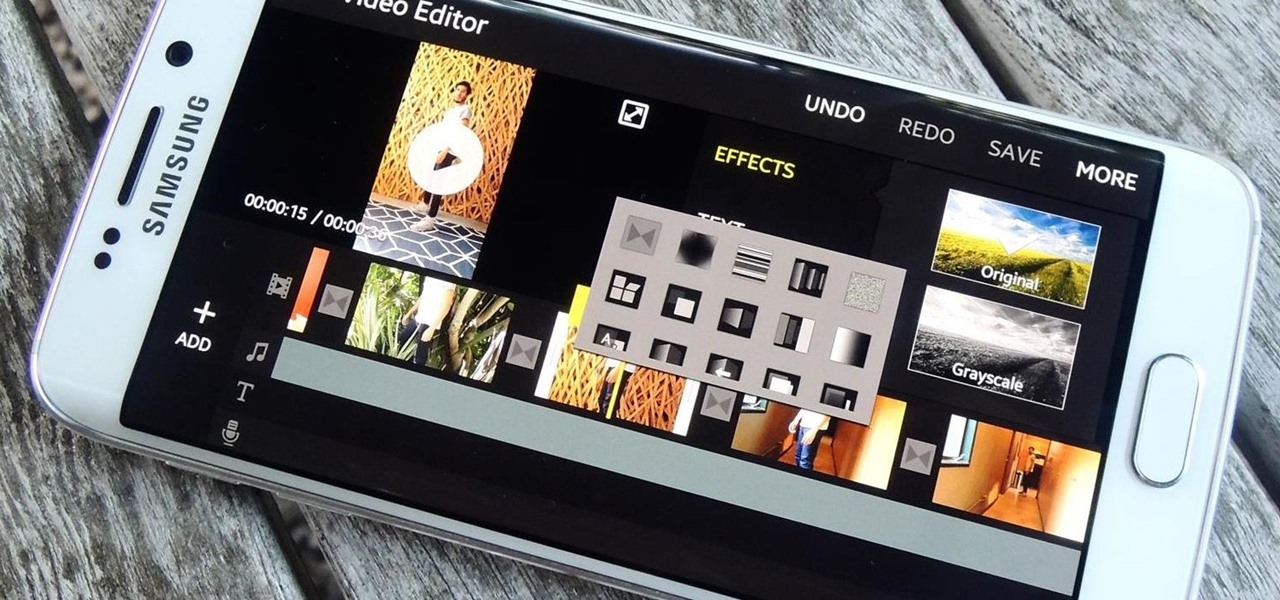
Editing a video by trimming or adding audio is fairly simple on Galaxy devices, but if you want to include other clips or transition animations and really get those creative juices flowing, you might find the standard editing tools limited—unless you know how to unlock Samsung's hidden video editor.

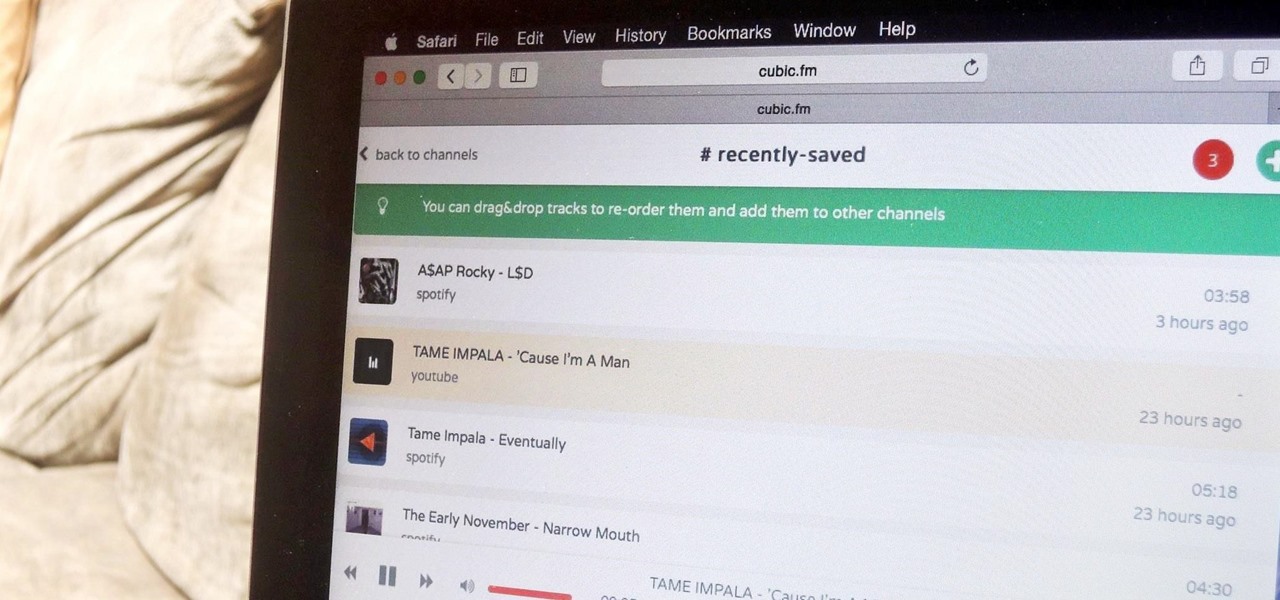
The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App Store.

Is your zipper so loose and just going to separate it? Wait ... wait... there's a way to fix your loose zipper when it's on one side of the track or chain. There's one famous sayings, "keep it simple," so just follow this simple steps.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

How often do you fight with your shower doors? Maybe not literally (although my elbow has smacked the hard glass many times), but when it's time to clean the bathroom, getting a few weeks' worth of soap scum and grime off the shiny, clear surface becomes an insurmountable task. Whether you use a special cleaner and squeegee or a carefully selected wipe, chances are you still battle the streaks and grit left behind. Although it might not make sense to steal cleaning supplies from the laundry r...

Simple household pranks are the best to set up because they don't require much to pull off just stuff you already have lying around your home. So if you're interested in pranking someone but don't want to go all out to get the tools and materials necessary this tutorial is for you.

In this simple tutorial, you'll learn how to easily set up a prank on your teacher in class for April Fool's Day. If you're looking for a simple yet effective prank to pull on your teacher on April 1st, why not try this one? All you pretty much need is black shoe polish and access to your teacher's dry board eraser. The rest is easy.

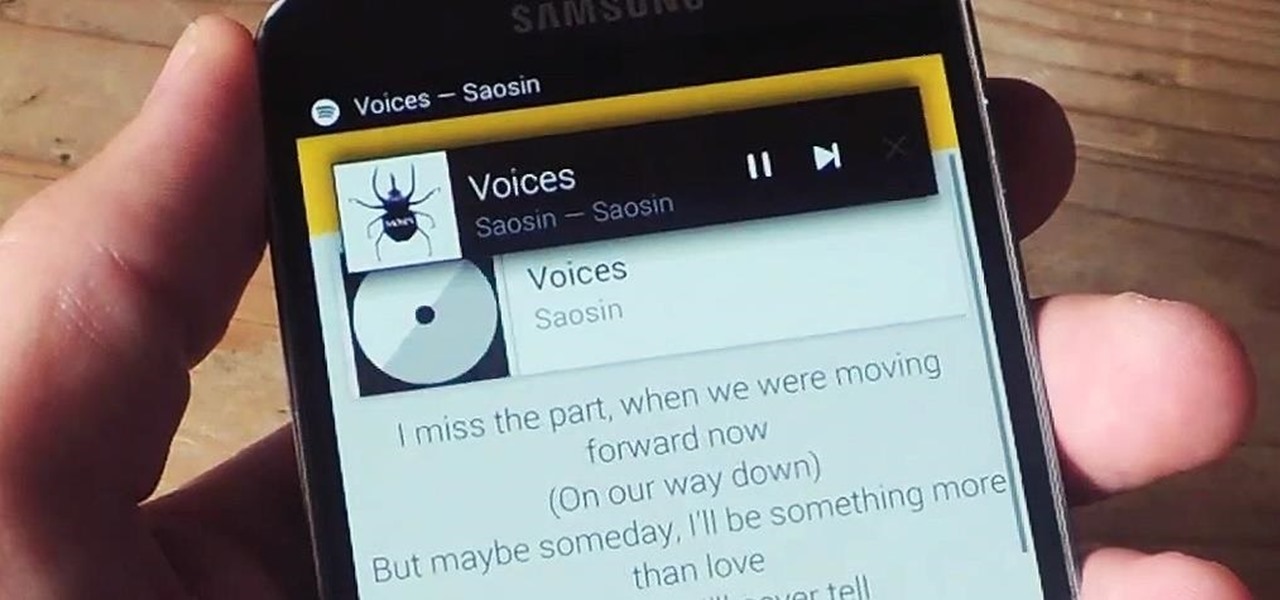
With floating song lyrics displayed over the screen, apps like musiXmatch and Floating Lyrics are perfect for people who want to go beyond just the tunes and delve into a song's message and meaning. And while these floating windows can be convenient, they're not always necessary.

Here's a little booby trap you can try to pull off on a fellow family member or roommate. It's pretty simple even a child can do it, though it'd be hard for them to acquire a condom. Then again a condom isn't necessary as you can substitute it with a balloon. Just follow the simple instructions in the video tutorial provided!