Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Acne sucks - or, more correctly, acne oozes. Which is why it's so important to take care of your skin with oil-reducing, calming products. Most anti-acne medications you can buy are severely drying and irritating, meaning they can cause the adverse effect of making your skin compensate by producing even more oil.

Is your Christmas tree looking a little too "I got everything from Target" generic? Then it's time you learn some decorating tips from interior designer Rebecca Robeson.

Do you play an intensive sport, like soccer or football, that requires you to be able to not only run quickly towards a target area far away, but also to be able to catch a flying ball with precision that far away? Then you'll benefit from the speed and quickness training methods presented in this video.

Imagine… your friend is drinking an ice-cold soda out of his/her styrofaom cup, and everything's fine, until… it's starts leaking everywhere! It could be utterly hilarious, or disastrously evil, depending on who your target is.

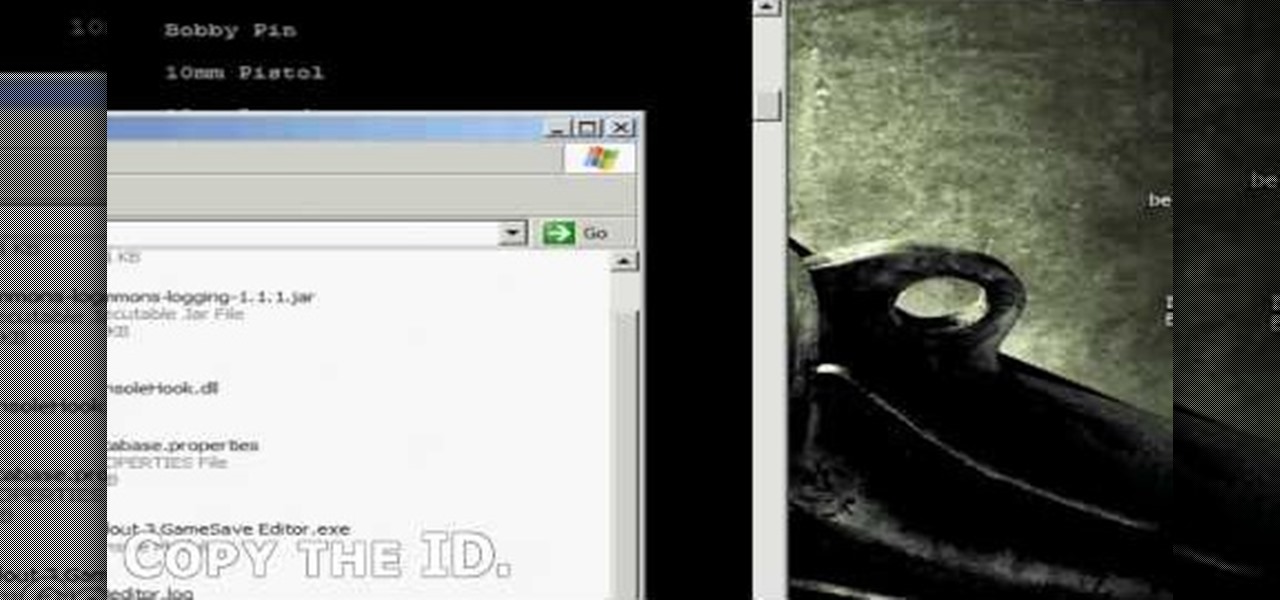
Fallout 3 is one of the most popular and biggest (content-wise) games on the XBox 360, and has thus become a popular target for hackers to mod. This video will show you how to mod your Fallout 3 saved game from the XBox 360 version using some FREE software. This does not include Modio, the popular for-money save game editor that many hackers use. Here are the files:

Four time abs is an excellent exercise for working the lower abdominals and abs workout. Try this out to tone your lower abs, which typical crunches can't get to.

Learn how to create a character rig when animating 3D models in Blender. Specifically, this clip addresses the following topics: Bone creation, splitting and re-parenting. Weighting with bone heat, mirrored weight painting and posed weight painting. IK setup, bone roll, and pole targets. Advanced foot rig with control to pivot off of the heel, toe, ankle or ball and control to lift the toes. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or...

Despite what the name may imply, triceps kickbacks don't involve kicking of any sort. Rather, this tricep-sculpting exercise move involves getting down to a near squat position and bringing a dumbbell forward and back, keeping the shoulders stead and down.

Lock and load! In this Xbox 360 tutorial, you're taken for a nifty little ride by the guys at Achievement Hunter. The main target: an easter egg. And not just any cool easter egg, it's one that puts you, somewhat, in contact with another zombie basher from a different game, Dead Rising. Yes, in this Left 4 Dead 2: The Passing, easter egg hunt, you'll be reading a little message left to you from the man himself, Frank West. So sit back and prepare for the worst. Enjoy!

Brooke Burke and Autumn Calabrese walk the viewer through a super-effective, targeted butt workout, doable in your living room in only 5 minutes. The first exercise, a "Heel Press", is done from your hands and knees. Keeping your head in line with your spine and your belly button tucked in, press one heel toward the ceiling, then bring it all the way into your chest. Brooke recommends 15-20 reps on each leg. The next exercise, "Crossovers", builds on the Heel Press. After pressing your heel t...

This is footage from B.F. Skinner's psychological tests on shaping behavior.

improvement and repair tips such as how to repair drywall or sheetrock, how to float drywall, how to replace door trim, and how to fix a window in this free home renovation video guide series.

If you have a toy you love SO much, this video will show you how to create a simple mold so you can duplicate it! This simple how-to tells you what you'll need to get cloning today. This video will also tell you what can and can't be cloned.

Get rid of your water-wasting sprinkler system— but not entirely! Keep your landscape and garden maintained by converting those sprinklers into eco- and pocket-friendly drip irrigation. In this how-to video, Paula Mohadjer from the Cascade Water Alliance explains how you can easily convert your sprinklers into a drip irrigation system.

A little fruit-flavored gelatin can go a long way in the prank department, especially on April Fool's Day. So, if you've got a friend or loved one who's addicted to their smartphone, make them squirm with this jiggly jello prank.

This beauty video demonstrates how to do fast and simple Urban Decay makeup.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Another major retailer is putting all its chips in on the relentless rise of selfie culture. Sally Beauty is rolling out kiosks to try-on "some of its best" hair dyes in 500 of its stores throughout the US. The in-store augmented reality-powered kiosks invite you to view yourself on video, overlay a punky (or otherwise) hair color, and snap a selfie on the screen to share your #glowup with friends.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

After parting ways with Papa John's, the National Football League has drafted Pizza Hut as its official pizza purveyor, and the company has hit the field with an augmented reality game to entertain hungry football fans.

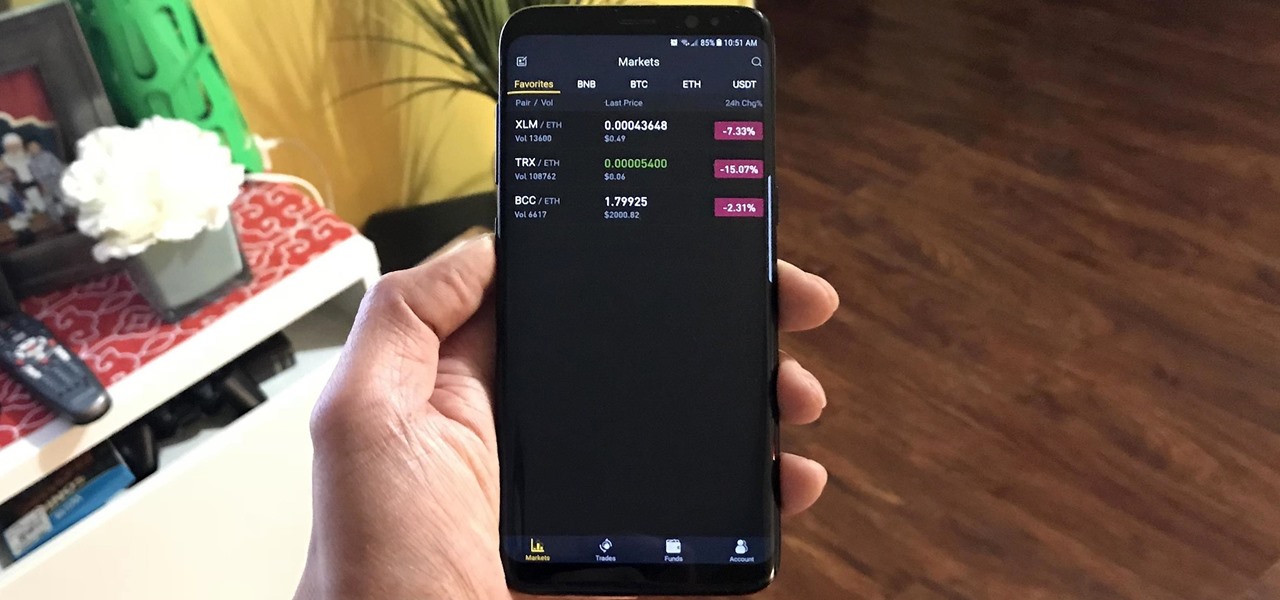
With the sheer number of alt-coins that you can buy and sell on Binance — Ripple (XRP), Stellar (XLM), and NEO to name a few — keeping track of coins you're interested in is a hassle. But with the tap of a button, you can mark trades and alt-coins that are on your radar for quick access on your Binance account.

Android's share intents system is great in theory, but the execution can sometimes be frustrating. When you tap the "Share" button next to a link, app, or file, you see a list of apps you can share that item with. But it seems like every time you use this function, the list of apps is in a different order — especially when it comes to the Direct Share targets at the top.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.