In this video Chris Pels shows how to create an MSBuild project that orchestrates the execution of the aspnet_compiler and aspnet_merge utilities for an ASP.NET web site. First, learn the fundamentals of the compilation process for an ASP.NET web site and the role of the two command line utilities. Next, see how to create an MSBuild project file and the primary elements such as PropertyGroup and Target. Then learn the details of how to execute the aspnet_compiler and aspnet_merge utilities fr...

A hooking knee strike is legal in Thai boxing, not kickboxing. Learn the skills of Muay Thai in this tutorial on competitive kickboxing moves. When performing the

All day we use our calf muscles when we walk, run, and climb stairs. As a result calf muscles are popular massage targets. Learn the art of giving massage in this diet and health how-to video.

Pilates is great for strengthening and toning the body. This piltes how-to video illustrates the Single Leg Stretch exercise. It targets the transversus abdominus, rectus abdominus, obliques, scapular stabilizers and hip stabilizers.

This Pilates Side Bend exercise is used to enhance lateral mobility of the spine. It primarily targets the transversus abdominis, obliques and scapular stabilizers. Attention should be paid to the abdominal contraction to maintain rib connection and prevent the hips and shoulders from rotating. The cervical spine should stay aligned with the thoracic spine.

This pilates how-to video illustrates the Pilates Spine Twist exercise. This exercise is great for spinal rotation.

This pilates how-to video illustrates the Obliques exercise. This exercise is great for rotation, flexion and strengthening pelvic stability.

This pilates how-to video illustrates the Obliques Roll Back exercise. This is a challenging rotational pilates exercise for athletes and advanced clients.

Make a do-it-yourself shoe! This video sewing tutorial shows how to put together Simple's first DIY shoe. Watch and follow along to sew and assemble a hand-made shoe from Simple.

Firebug is an essential Firefox extension for web designers and developers. You are able to quickly target any element on a page to see the markup, the CSS, the layout, and the DOM in an instant. Not only can you see all of this juicy information, you can edit and see the results directly in the browser window. This makes Firebug the go-to tool for debugging CSS trouble. Also indispensable for Javascript programmers. So all you Internet website designers out there, pay close attention to this...

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

All Kohl's wants for Christmas is Snapchat augmented reality. In conjunction with a holiday pop-up hosted in New York City from Nov. 7 through Nov. 10, Snapchat ran a sponsored portal lens available to targeted Snapchat users in the AR carousel. The experience gave users the ability to virtually transport themselves to the pop-up.

If the name Leroy Jenkins elicits a reaction from you, then you are old enough to remember the iconic title World of Warcraft from its heydey (whether or not you actually played the massively multiplayer online role-playing game).

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Earlier this year, rumors began to swirl regarding Apple's upcoming iPhone SE 2. They predicted an A10 processor and a glass back for wireless charging, all at a price point at least $150 cheaper than the iPhone 7. While it wasn't poised to turn heads like the iPhone X, it would have been a reasonable upgrade for many users looking for a more budget-oriented Apple device.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Samsung has kept us busy with their Android 8.0 Oreo beta testing program for the Galaxy S8, and most recently, the Galaxy Note 8. As the beta continues to receive new updates, stability has improved continuously, and new features keep on creeping in for both devices.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

The augmented reality feature in Pokémon GO is one of the key components that draw people in to the popular Android and iPhone game. Indeed, there's nothing quite like the sight of a Pokémon standing around in an otherwise uninteresting parking lot.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

There may be worse feelings than sitting around waiting for food delivery, but I don't want to know what those are. Especially when your local delivery guy misses your address for the eighth time. But soon, Domino's Pizza will take that stupid human error right out of the equation in the form of a robot that's only 3 feet high.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Hello friends. This is actually my first how to.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Hello everyone! Hope everyone having good day!! I wanted to share an easy way to locate an appropriate exploit from the EDB, get it compiled, and run it all from inside the terminal.

If you're trying to get a new iPhone 6 or 6 Plus, we know you've been struggling to find one, and we're here to help. With Apple's preorder numbers topping 4 million in the first 24 hours, it was nearly impossible to get one during the first wave.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

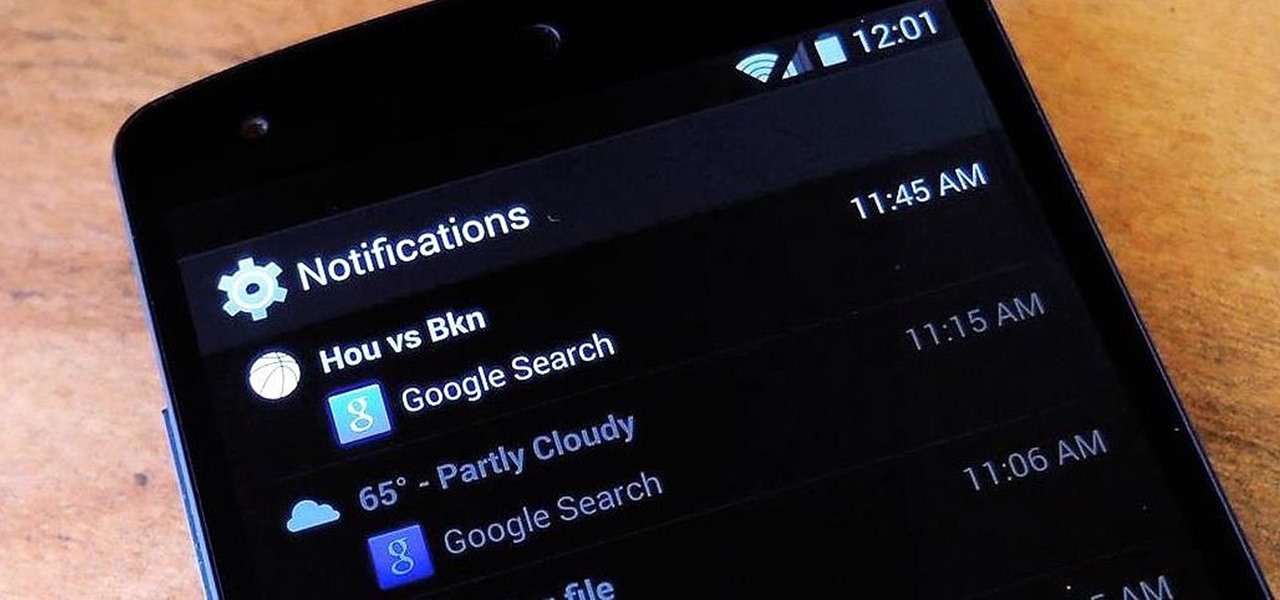
Have you ever been a little overzealous in dismissing notifications on your Nexus 5? Perhaps you missed your target and swiped away the notification you meant to read later. Or maybe you simply hit the "Clear All" button when you really meant to tap the button that switches to the Quick Settings tiles.