Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf
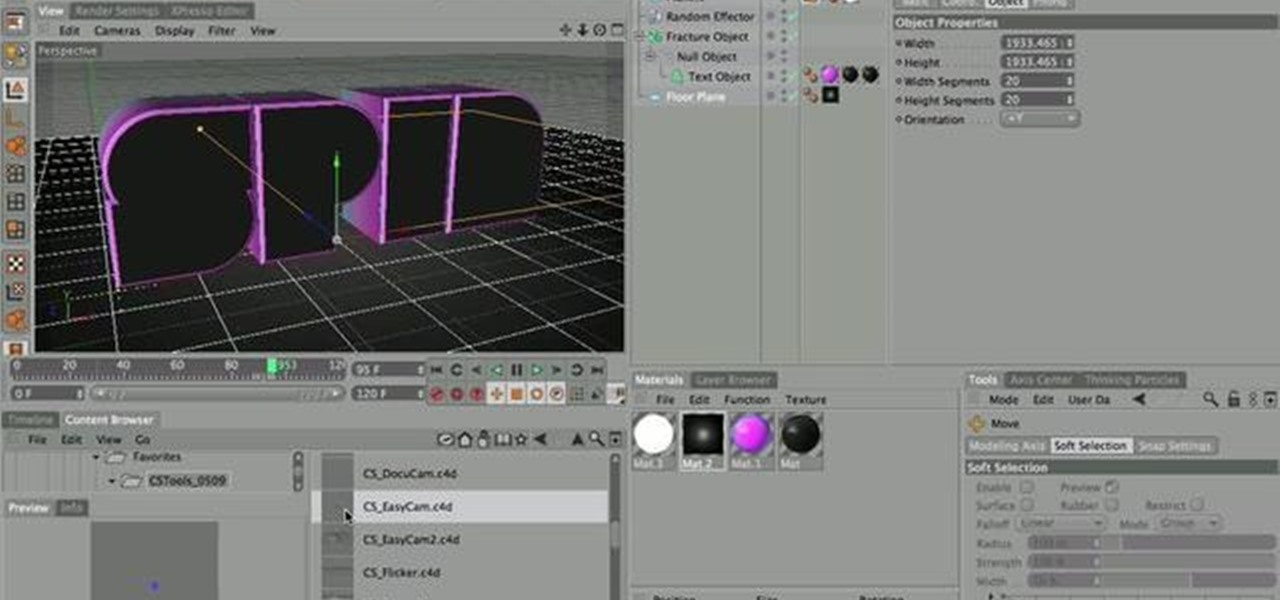
Nick from Greyscale Gorilla demonstrates how to create a very simple spinning logo animation. Using Cinema 4D, Mograph, and Random Effecter, Nick combines different textures and camera angles for a rich, slick finished product.

Make sure your neighbors don't mind before you learn to play the drums with Mr.G. In this new four part series, he is going to teach you how to play the drums. You'll start with extreme basics, including your grip, to learning a simple 16th note full measure. Watch this, if your sick of just "banging", whether it be pots and pans or a proper drum set.

Sure, there's six steps, by why are there eight videos? Well, why don't you just keep reading, or watching?

These are assembly instructions for a simple Knex gun with trigger

Sometimes simple is the best way to do it, and what is simpler than green beans? Well, they aren't THAT simple, but the concept is easy to grasp. Green beans can make a fantastic side dish to any meal if you know how to cook them right. In this video, chef Jason Hill introduces you to a simple, but delicious green bean recipe with garlic and shallots.

Want to turn on Mac OS X's simple Finder feature? It's easy! So easy, in fact, that this Apple accessibility guide can present a complete walkthrough of the process in just over a minute and a half. For details, as well as to get started enabling the Simple Finder interface yourself, watch this helpful how-to.

Golden girl Jennifer Aniston never skips a fashion beat on the red carpet (maybe because she 9 times out of 10 wears black, which we know is never not flattering?), but when she stepped foot onto the red carpet last year at an event, she once again started a "Rachel" hair trend.

MatttChapman shows you how to add a simple dutch tilt to your filmmaking bag of tricks. Tripods conventionally only pan and tilt, but this trick adds an extra dimension. All you need is a tripod and a camera! It's just a matter of messing with the base plate to get this simple dutch angle.

Need a little help with your new Adobe Photoshop graphics editing program? Working with Photoshop can be a bit tough if you don't know what you're doing, so instead of getting out the books, check out this 'no nonsense' video tutorial to learn how to create a simple folder in Adobe Photoshop. Photo manipulating and editing is always tricky, so just watch to see how to create a simple folder, for beginners.

See how to make a simple laser communicator with KipKay and MAKE Magazine! Find out how to secretly shoot your voice across the room in stealth mode on the beam of a laser! Kipkay loves his lasers! A simple laser communication device is the perfect way to talk across the room.

Simple Syrup is used in many drinks as a sweetner and is incredibly easy to make. Ingredients: 1 glass sugar

If you're just getting into woodworking, one of the most simplest and common projects involves making a birdhouse. A birdhouse is a common project that many can build and doesnt require too much work.

The alluring and stylish GiannyL is the DIY fashion design guru of the web. Do-it-yourself has never been so sexy before. Her fashion design video tutorials make new outfits not only hot, but cheap and easy. And recycling and reusing old clothing is not only practical, but eco-friendly.

In this episode of "The Discount Trendsetter Show" the host will show you how to make a simple dress for under $10.00. For this simple slip dress you will need safety pin, elastic, needle, thread, and some cool fabric. No need to hassle with patterns, this easy style can be created with some draping. Check out this fashion how-to video and learn how to design yourself a simple and inexpensive dress.

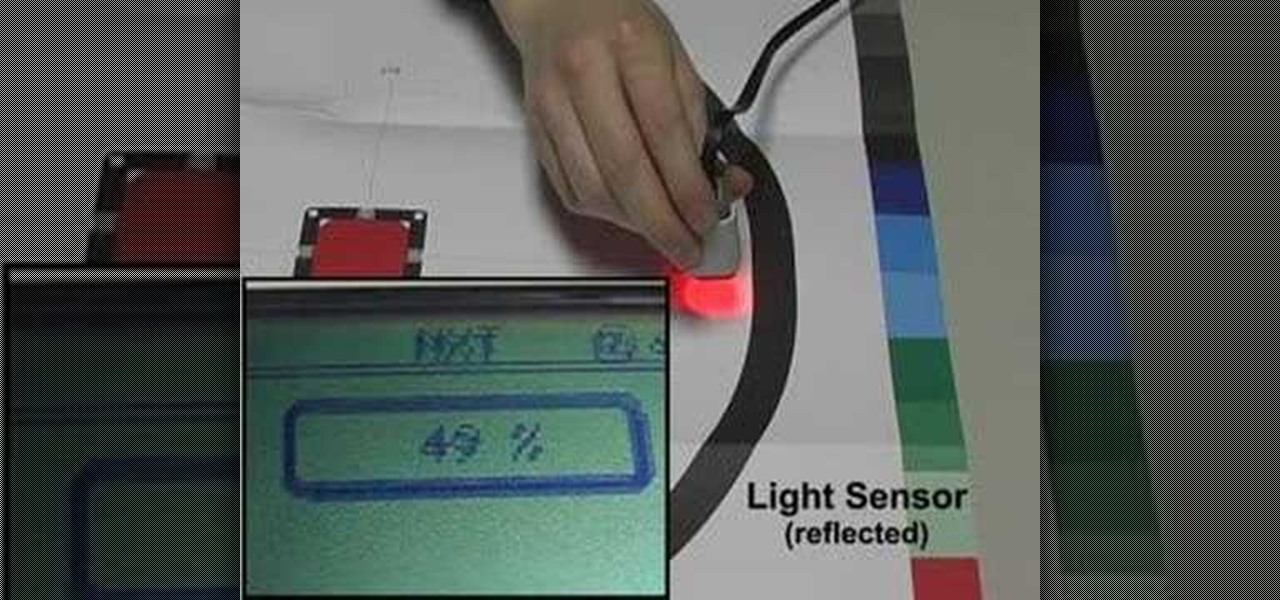
These how-to videos provide an introduction and tutorial to LEGO Mindstorms NXT. Topics discussed are (1) what is included with the NXT robotics kit (2) how to build a simple NXT robot (3) programming an NXT robot and (4) testing an NXT robot. Watch this video tutorial series and learn how to build a simple robot with the Lego Mindstorms NXT kit.

Looking for a way to become centered, focused and at peace? Practice simple meditation techniques with tips from a registered hatha yoga instructor in this free yoga video.

In this four-part video tutorial, Joe Stagner will demonstrate, using ASP.NET, uploading a single file from the client machine to your server.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

training with a head target wall mirror. Learn how to use target mirrors to practice jabs and hooks in this free video for boxers.

Feel beautiful from the inside out with targeted exercises, like these exercises for your feet. This how-to video has a few simple exercises that will strengthen your toes and relieve some foot discomfort. Keep your feet in good shape so you can wear those high heeled shoes all night.