
The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.
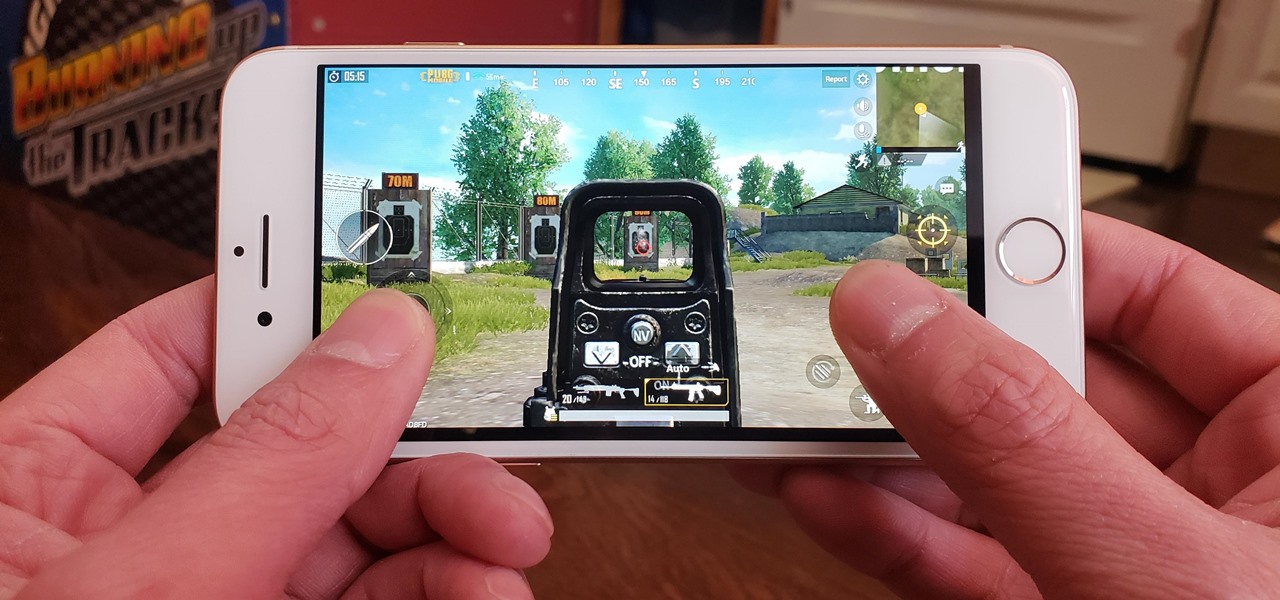
PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that today's devices are capable of doing far more than beeping at 7 in the morning.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Video: . This Video will Show you how to Season and Clean

Here is a video that shows 90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.)

90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.) By forming your target material into an efficient ball, you will be able to start a fire even with very small lenses. Like less than an inch across small. The finer the individual fibres, and the more densely they are packed, the more effective is your ball of smigtin (smoulde...

Sony is ready to get into the micro-console gaming fight, with its PlayStation TV set to debut this fall.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Watch these four videos showcasing some certain tactics to use when playing your troubling games of chess. See if you can come up with the answers before he does.

Just because Valentine's Day is over doesn't mean you should slack off the romance department. While it's oh-so-easy to just pull on your Victoria's Secret boyfriend sweats, tuck your hair into a quick ponytail, and pig out on Doritos and dip on a Friday night with your boyfriend, it's quite a pleasant surprise if you put some effort into your look.

Paracord, or parachute cord, is one of the most versatile ropes out there. Originally made for parachute suspension during WWII, it is now used for everything from tying knots during a camping trip to weaving sturdy bracelets as a fun DIY project. The tutorial featured in this video is the latter.

You don't need to spend an hour on your hair before you hit a club or go on a date to look absolutely ravishing. In fact, even if you start out the day in your PJs and don't decide until the last minute to go out, you can still look great with one of these simple updos.

A New Year, a new you. At least that's what most of us promised ourselves when the clock struck 12 and 2010 transformed magically into 2011. While not all our New Year's resolutions are easily stuck to, such as dieting and exercising six times a week, you can update your look to look your best. Check out this makeup tutorial by Michelle Phan to learn how to create a simple and clean look.

Before you begin on your kawasaki origami rose folding, you should probably master the basics first. Namely, if you're interested in folding floral projects, then it's best that you start with a simple project like this one.

You'd never be able to catch a real hummingbird and keep it as a flitting, beautiful pet, but you certainly can call this origami hummingbird your own.

On a budget during this holiday season? Don't fret; you can gift literally dozens of people without breaking the bank by giving them chocolate bars. No, we're not talking about just handing Aunt Sue a Reese's Pieces.

At its core, Valentine's Day is about giving and getting sweet treats. While one could argue that the same idea applies for both Halloween and Christmas, on Valentine's Day these sweets are packaged in the most adoring, lovey dovey ribbons and wrappings.

OK, so visitors are coming to your website and they're even leaving comments! Now, with some simple PHP array programming you can find out what browser and OS they're using. This tutorial shows you how to create a simple and efficient user agent sniff script to get the information you want. Sniff, sniff. Is that Chrome running on OS X I smell?

If these aren't the most adorable cupcakes we've ever seen, then we don't know what's cuter. These extremely simple sheep cupcakes are made from frosted white icing and marshmallows then iced with a chubby sheep face.

Curly hair is gorgeous (Taylor Swift is one fine example), but for many girls, curly hair can be unmanageable. That's because naturally curly hair tends to be on the thicker, coarser side.









































