How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.
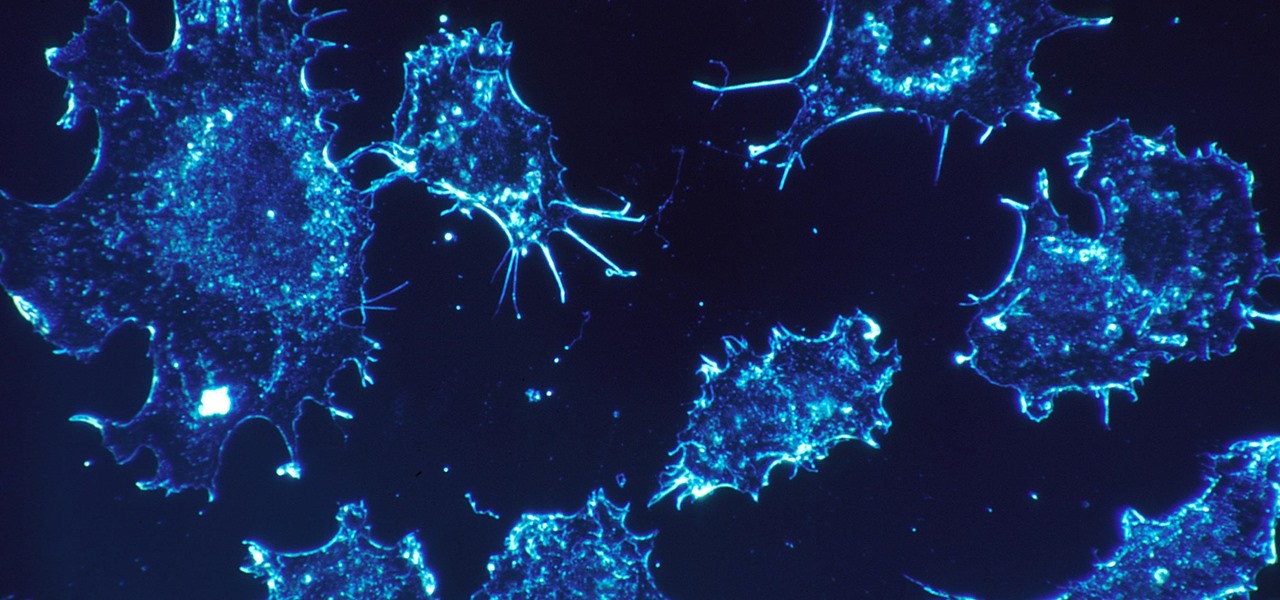
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Drug-resistant bacteria have made curing some infections challenging, if not nearly impossible. By 2050, it's estimated that 10 million people will be dying annually from infections with antibiotic-resistant organisms.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Halloween is only a few short weeks away, and most people are scrambling to get their costumes together before the big night. The secret to a great getup is all in the details, and including your pet in the fun can be exactly what you need to take your costume to the next level.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

In China and Japan there exists a special zodiac quite different from that which we have in the states. The Chinese zodiac consists of twelve animals, each animal representing one year in the constant twelve year revolution.

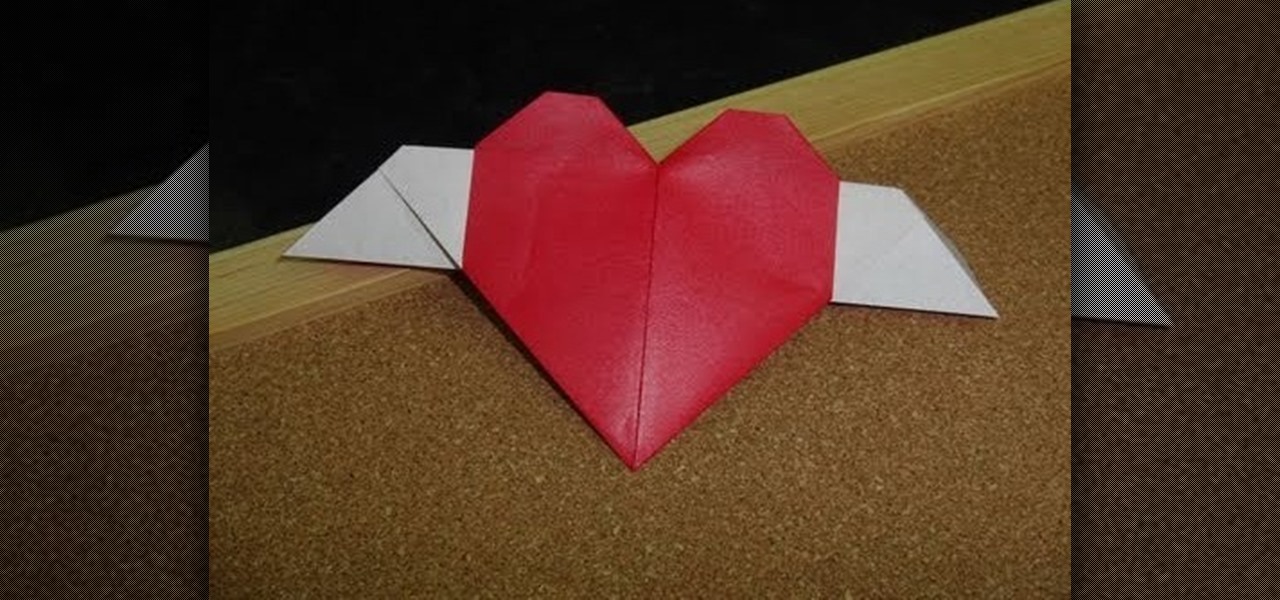
Show your amor that his love makes your spirits take flight by crafting this beautiful - and amazingly simple - Valentine's Day origami heart. Teeny white wings grow out from the sides to give it that Cupid charm.

Whisper sweet nothings to your amor by crafting this simple and quick origami message card, which features a heart seal. It's a delightful way to package a loving, amorous sentiment and can also hold tiny trinkets of your affection.

An elegant, formal hairstyle that's appropriate for everything from weddings to cocktail parties to work isn't as hard as it sounds to style. In fact, all you have to do is watch this video for simple instructions.

Knitting, ladies and gents, is not just for grannies who have too much time on their hands. In fact, knitting is fun and quite addicting once you get the basics down.

Time to get your fold on people! This clear and concise how-to shows you what you need to do to create this simple, origami cat. A nice top down shot lets you see every bend and fold to make this paper cat come to life.

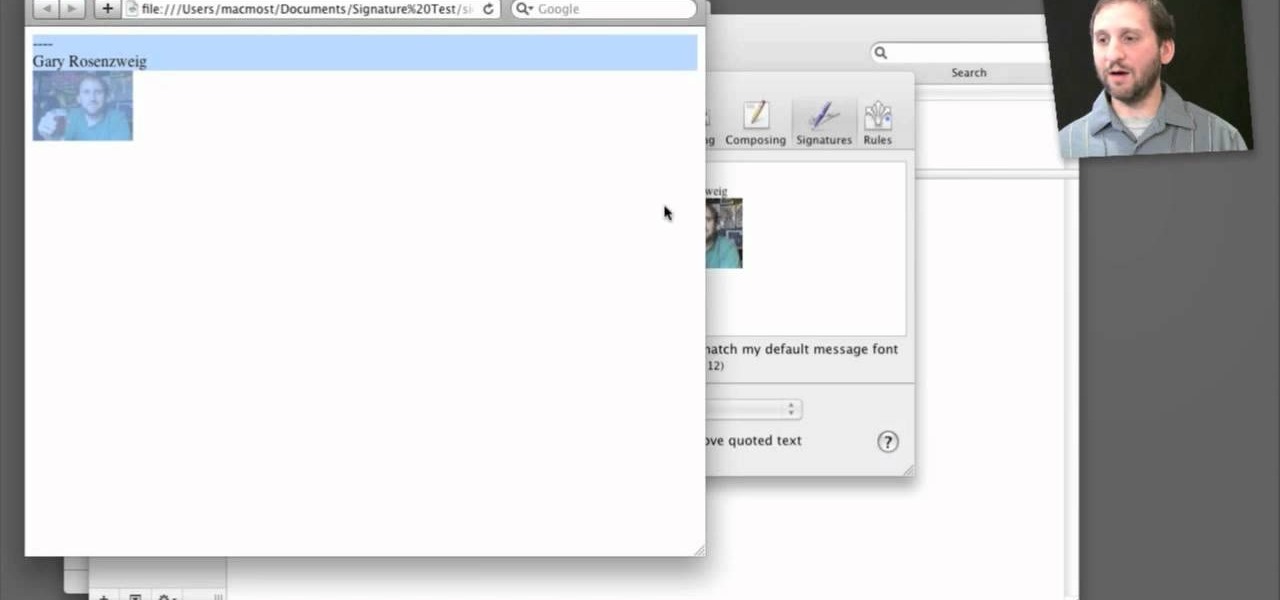
Looking to spice up your email signature a bit? Why not add an image? This simple how-to shows you an easy way to take advantage of some simple HTML embedding so you can add an image to your Apple mail signature.

Know someone who's full of hot air? Grab them and make a heat motor with this cool home science experiment with Mr. G. When air is heated, it rises. This experiment uses that natural law to create a simple, spiraling heat 'motor'.

Get into the Christmas spirit this holiday season by crafting! But don't worry - we're not talking about super complex and time-consuming crafts like crochet scarves or those fugly Christmas sweaters your grandma used to knit for you.

Are you sitting in class the last day before holiday break, simply dying over how long each minute is before that last bell rings and you get to head to Big Bear? Pass the time (though obviously do so discretely) by crafting these simple origami t-shirts. Each t-shirt is folded from a monetary bill, which we're pretty sure you have in your pocket.

A high waisted skirt is one of the most flattering skirts you can wear. Because it's cinched in directly at the smallest part of your midsection - your waist - you automatically get an hourglass figure silhouette.

Need a simple dish to prepare for Thanksgiving that's not time consuming but will still make a big, flavorful impact at your dinner table? Then deviled eggs are the perfect recipe for you.