
Cryptocurrency for the Hacker : Part 2 (Currency for Hackers)
Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.


Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

A few months ago, my friend Sarah appeared at a party bearing homemade liqueurs—amaretto, hazelnut (e.g. Frangelico), and vanilla liqueurs, to be exact. Her cool factor, which was already quite high, jumped up a few more notches—as did the overall energy of the party. (And that's why we call her 'Game Time.')

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Welcome back, my budding hackers!

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

If you have a custom recovery installed on your Nexus 5, you're able to flash custom ROMs and lots of other cool Gadget Hacks. But when it comes time to receive and Over-the-Air (OTA) update directly from Google, having a custom recovery installed can be a fairly big hindrance—and for the upcoming Android L release, you're going to want to alleviate that.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my aspiring hackers!

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

How to make simple macrame earrings with beads ..

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Very simple knitting stitch.

A very simple way to cast on!

Video: .

A very simple method of making a Harebell flower!

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.
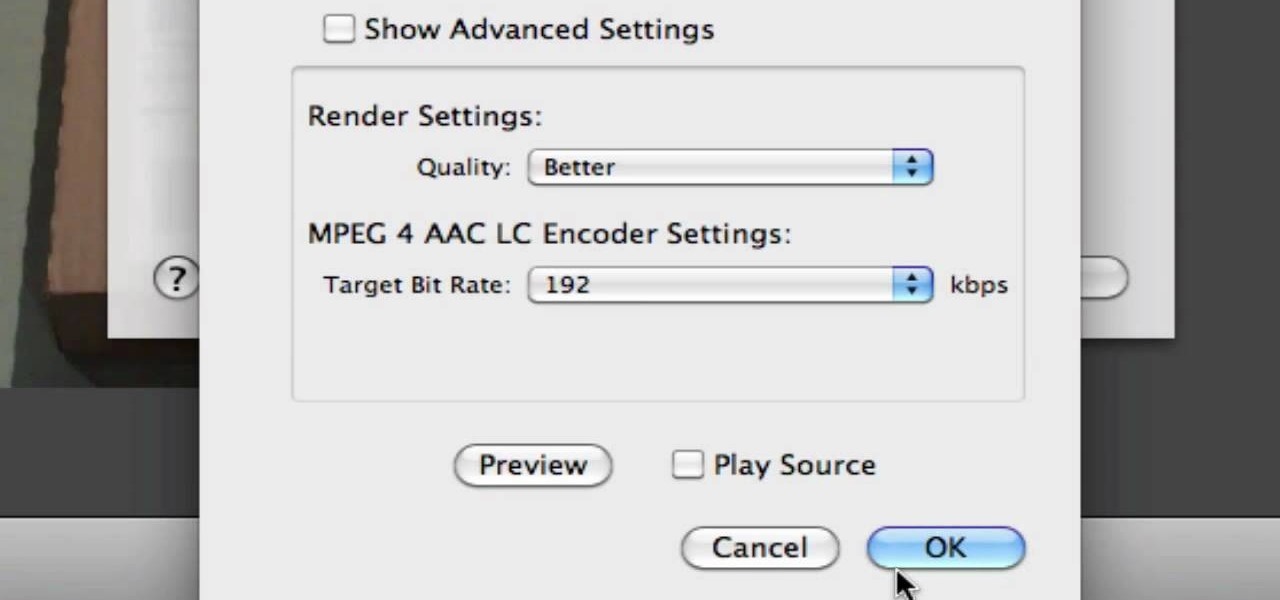
In this video from AppleGenius0921 we learn how to export videos using Screenflow in HD. Launch Screenflow, make sure you're editing is complete and go to File, then Export. A window will come up asking the name you want to save it as and where you want to save it. Make a good title that is relevant to your video. Now click customize. Then click settings. Now go to compression type and double click H.264. Set the quality on Best. Click OK and use no filter. Now go to size and click 1280x720 H...
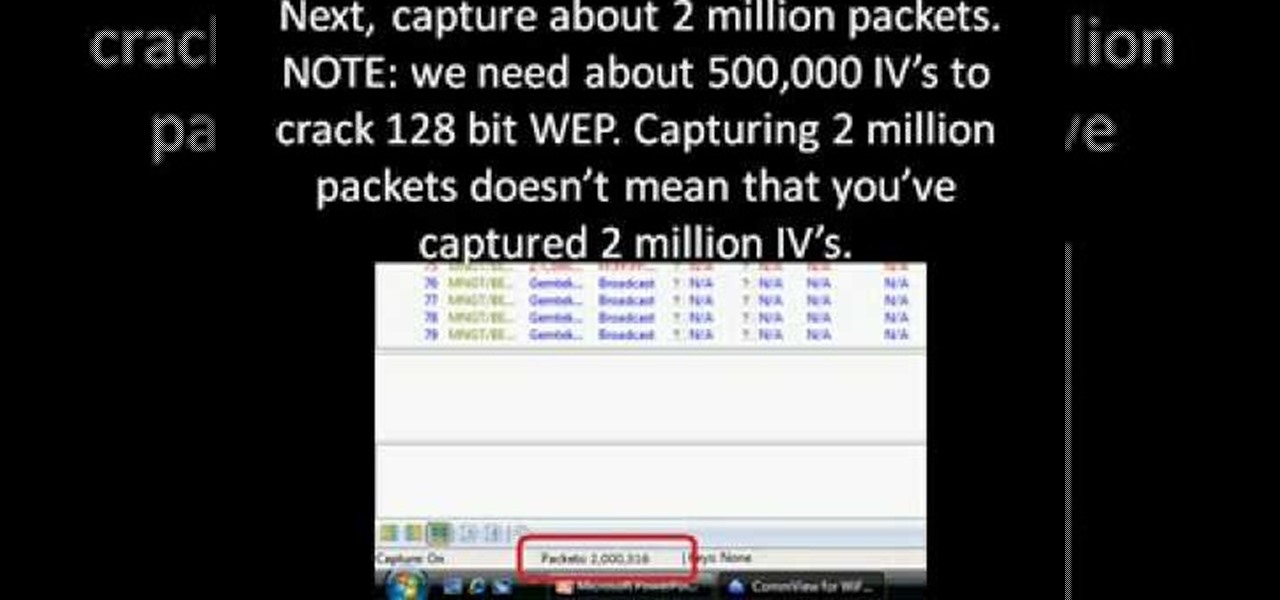
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

In this Business & Money video tutorial you will learn how to make a successful curriculum vitae or resume. This is the first step in getting your dream job. A well written CV captures the interest of the person who is reading it. Think yourself as a product and the CV is a piece of paper that is going to sell you. Don't be afraid to sell your skills and abilities. If you don't do it, nobody else is going to do it for you. First thing on top is to put your name; centered and bold. Then leave ...

Almost 125 million people worldwide suffer from what is known as psoriasis, the skin disease that's marked by red, itchy, and scaly patches that are hurtful, if not visually god-awful. There can be a little hope though for psoriasis sufferers. Though you can treat and control psoriasis, characterized by dry scaly patches of skin, the progress is often erratic and cyclical, so be patient and consistent in executing these steps.

Speeding tickets are one of the worst things a driver fears on the highway, aside from wrecking, of course. But you can get home safe without getting a ticket. You just need to keep your vehicle off the radar by following these stealthy driving techniques.

In this edition of ClubHouseGas, with host Casey Bass, basketball coach Chuck Melito shows us how to shoot free throws. He shows us how to work on both the mental and the physical approach to free throw shooting. A right-handed shooter should place his right foot at the center of the basket. A left-handed shooter should place his left foor at the center of the basket. Then it's important to get balanced, so you're not leaning to one side or another, or more weight on one foot than the other. ...
John Roy demonstrates the tutorial to view or retrieve layouts that ens with .swf. SWF files can be viewed by pasting the url in the address box.

The video presents "How to start your own Clothing Line Business". The steps include getting the financing, designing the prototype outfit/s, producing the line of clothing, promotion and sales. A good way of financing for a small business such as this is to sell your idea to family, friends and even colleagues. Research and prepare the business plan for your clothing line and be passionate about it in your presentation to convince them to fund your business. The next step is to get the produ...
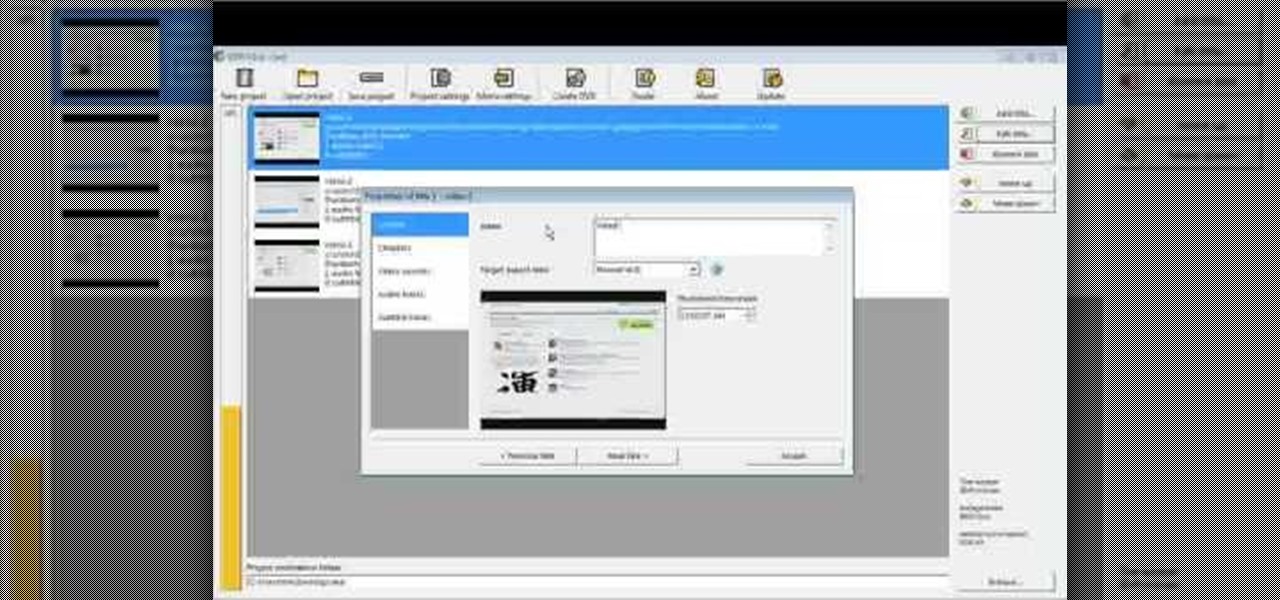
This video tutorial from Foreclosureresearch presents how to burn video files to a playable DVD using DVD Flick application.First you need to download and install free software called DVD Flick.You can find it at DVD Flick.Once it's installed, run the program. First thing to do is to set your Project Settings. Click Project Settings from top menu. From Project Settings window you can name the project, select Target size (size of your DVD), Encoder, Thread count, DVD format, bitrate, playback ...

This video demonstrates how to throw a simple clay pot: a flattened salt holder. In order to throw this simple clay pottery piece, you will need: clay, a pottery wheel, and water.

In this how-to video, you will learn how to create a simple terracotta clay wall hanging vase with a pottery wheel. Begin by throwing a piece of clay on the pottery wheel. Now, make a circular shape with the clay. Next, widen the shape and then make a bowl shape inside. Now, bring the shape up so that it is elongated. Keep doing this until you get to the desired shape. Now, narrow the base of the clay. Make sure that the width tapers smoothly. Now, refine the top and inside of the clay. Take ...

Golf Link demonstrates how to identify whether your golf swing plane is correct. The swing plane is the path described by the golf head that controls the direction that the club head is traveling through when it impacts the ball. An on plane swing will have the club head directly traveling towards the target at the point of impact. That and a square face will make a straight shot. If the swing comes inside or below the plane, it will produce a hook shot or a push shot. A swing that comes outs...

You can manipulate the AF fine-tune on your Nikon DSLR in order to optimize the sharpness and resolution of your lenses. This is a great tool for achieving the highest picture quality possible.