When shooting a shotgun, you don't really have to aim--just point and shoot. Whether you hit what you're shooting at depends on how well you did your homework. "Patterning" your shotgun allows you to choose exactly the right brand of shells, size and type of shot and type of choke required for the game you're pursuing. Set yourself up 40 yards from a 30-inch circle target, and bring along several brands of shells in various shot sizes. Use some form of rest like sandbags on a table or a rolle...

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

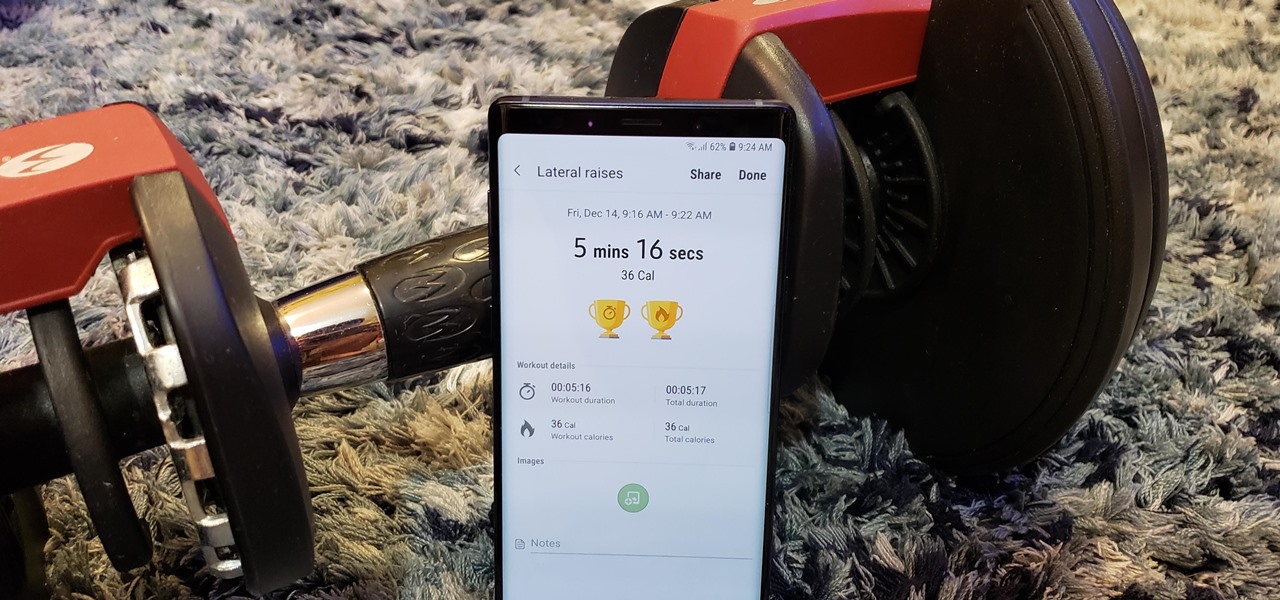
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Virtual reality headsets aren't new, but they may be something you or someone on your holiday shopping list hasn't experienced yet. If you're going to dive into the world of smartphone-based virtual reality, the best time to do it is during Black Friday when all the good sales are going on.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

You don't need to invest in fake hair - AKA hair extensions - to look like you have a head full of enviable voluminous, thick hair. In fact, all you need to do to create buxom hair looks is a few tricks, and a few hairstyles targeted towards making your hair look fuller.

Baking soda is like a miracle in a box. Whether you need to clean a doggy doo doo stain on your carpet, need to deodorize your refridgerator, or need an all-natural face scrub, baking soda has a cure for it all.

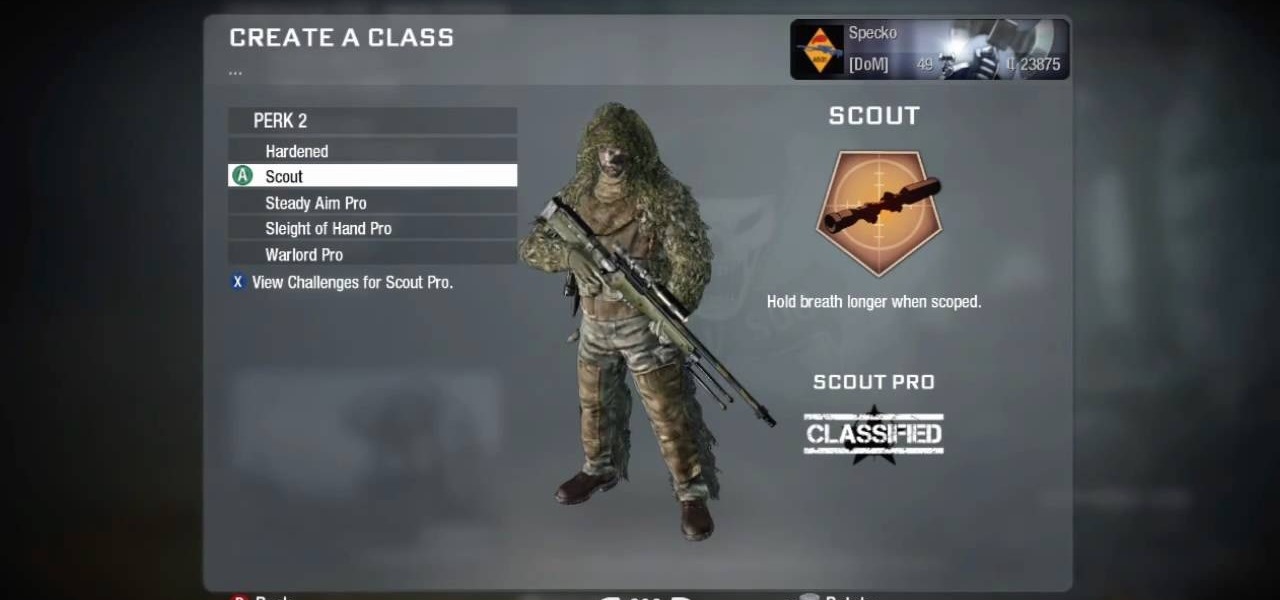
Sniping is a good skill to pick up when playing war games, since it allows you to kill enemies with great accuracy at long range. You'll need to find good spots with decent cover that give you access to enemy targets without revealing your own location.

Love the idea of a superhero MMO, but prefer the feel and controls of a first person shooter? You can actually set up your controls and targeting system in the game to make the interface behave more like your favorite FPS!

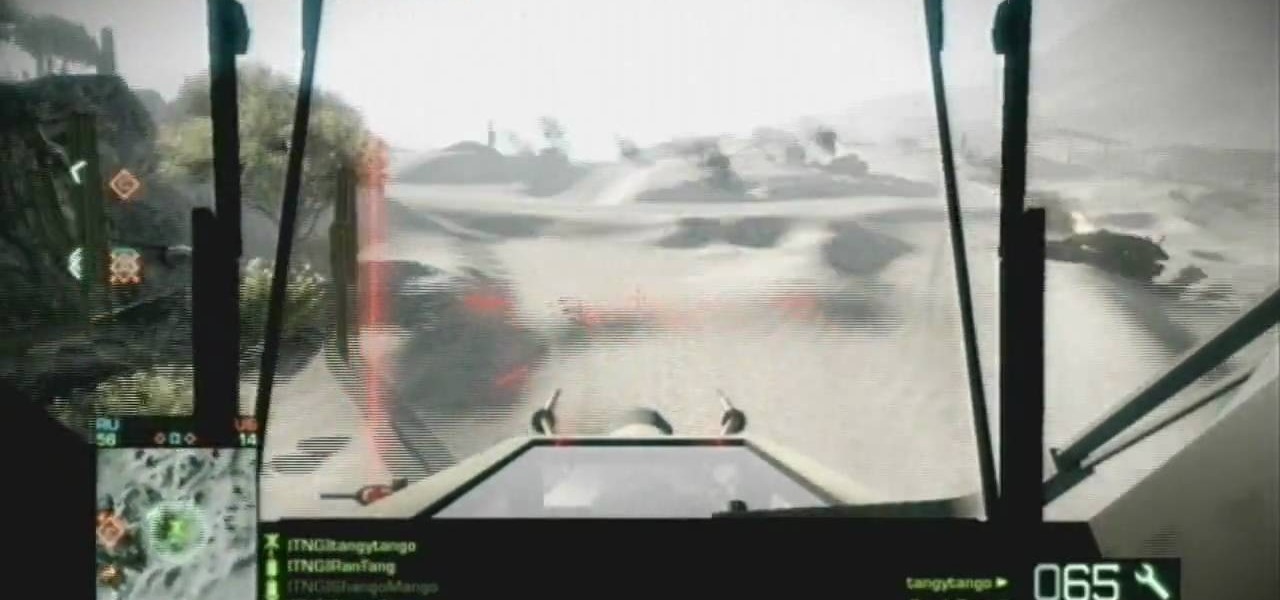
The helicopter in Batttlefield: Bad Company 2 is really powerful, but really pwning people with it requires a lot of technique. This video for advanced BC2 flyers will show you some cool tricks for improving your game, including how to utilize a copilot properly and how to prioritize your targets.

Target your shoulder girdle with this effective Pilates arc routine. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete instructions, give this free exercise video a gander

If you want to make a movie with zombies, or the apocalypse, or the apocalypse and zombies, then you are going to have to learn how to create a really haggard-looking, disease-ridden face out of makeup. This video will show you how to do it using Rice Krispies, among other things. The end result is terrifying, and sure to scare your audiences or trick-or-treating targets into doing what you want (buying theater tickets or giving your candy, respectively).

Score those famously fit football player shoulders by watching this video, which teaches you how to perform a pull up exercise.

Title says it all you have to make the cotton buds more loose on the paper to make it explode. This is a how-to on making ammo for your paper launchers and projectile guns. This ammo explodes into cotton buds when it hits its target. Very cool effect.

The roundhouse kick is a kickboxing staple maneuver. Learn the skills of kickboxing in this video on competitive kickboxing moves. When performing a kickboxing roundhouse kick you should start from fighting position, keep front foot ready to pivot, the back leg comes out at 45 degree angle, and then go all the way through the target. With this how to video you can incorporate the roundhouse kick into your kickboxing routine.

Lateral hops and forward lunges combos combine elements of strength, endurance, and agility. Learn how to perform lateral hops and forward lunges properly from a professional trainer in this workout tutorial. When doing lateral hops and forward lunges you should use both feet, hop laterally over target, work in lunges and alternate exercises. With this how to video you can incorporate lateral hops and forward lunges into your workout.

Try out a stability ball for core muscle exercises and to change up any workout routine. Learn how to use stability balls in this exercise tutorial. When using a stability ball you should target core muscles, keep back straight, abs tight, and tone core muscles. With this how to video you will be able to use a stability ball for a more effective workout.

Check out this instructional kickboxing video that demonstrates how to do a low kick, or a shin kick. A shin kick is a painful kickboxing move to use. Learn the skills of kickboxing in this video on competitive kickboxing moves.

The uneven push-up targets the pectorals, triceps, deltoids and core muscles. In this fitness tutorial, SSG Ken Weichert, Army Master fitness trainer, teaches you the proper way to do the uneven push-up exercise. Try to do regular push ups after performing this exercise. You will notice your form for the regular push ups are much better.

The dive bomber push-up is an advanced push-up format that targets chest, arms, abdominals, back and legs. The dive bomber push-up gives a whole body workout in one exercise. Learn how to properly do the dive bomber push-up with this fitness tutorial.

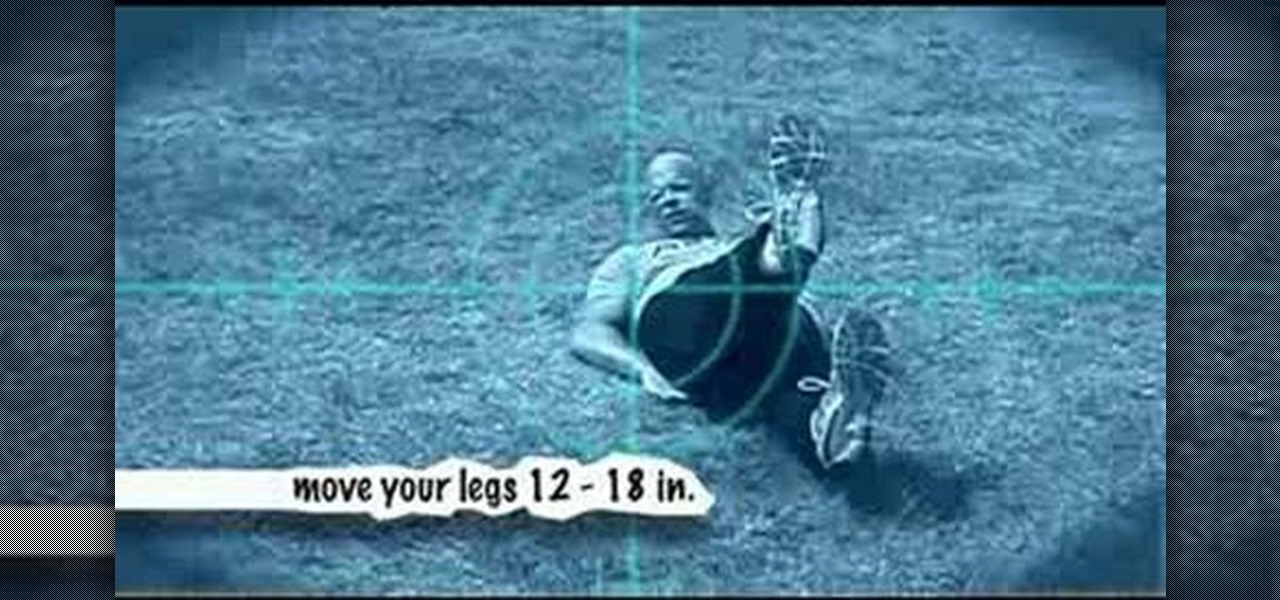
Want to get great abs, thighs, and a butt all by doing just one exercise? Then save time while still getting awesome results by doing the flutter kick exercise, which involves kicking your legs one on top of the other while keeping them at a 45 degree angle.

Donny Gruendler, a faculty member at Musicians Institute, has become and expert at performing with backing tracks, manually triggering samples, and playing with loops (both live and in the studio). In this installment from his video tutorial series in which he discusses the fundamentals of playing with loops, Donny provides tips for complimenting a drum loop (and thus avoiding "target practice").

Skittles is an old European target sport that is very much like bowling. Discover how to make home made skittles with just a tennis ball, glue, empty water bottles, water, paint, and newspaper. Watch this kids activities how to video tutorial to get ideas for a great rainy day kids activity.

Short Plank is derived from original pilates exercises in order to teach proper abdominal and torso support in the push up position. The exercise in this how to video will strengthen your core, strengthen your shoulder girdle stabilizers and target the deep muscles of the abdomen and spine to protect your lower back. Watch this fitness tutorial and you will be toning your body with the Short Plank pilates move.

This video tutorial goes over methods for defining the topology of an organic object in Adobe Photoshop. This is helpful as a planning stage before you begin your 3ds Max 8 digital 3D modeling to make sure that your have proper distribution of faces and your target mesh will deform nicely. So, if you're using Autodesk's 3D Studio Max for awesome 3D graphics, this could help you out with Photoshop topology.