In this tutorial, Bert will show you quickly how to use a bunch of different layers to create a ray gun shooting and exploding it's target. It will help if you already have some Photoshop knowledge for this one.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

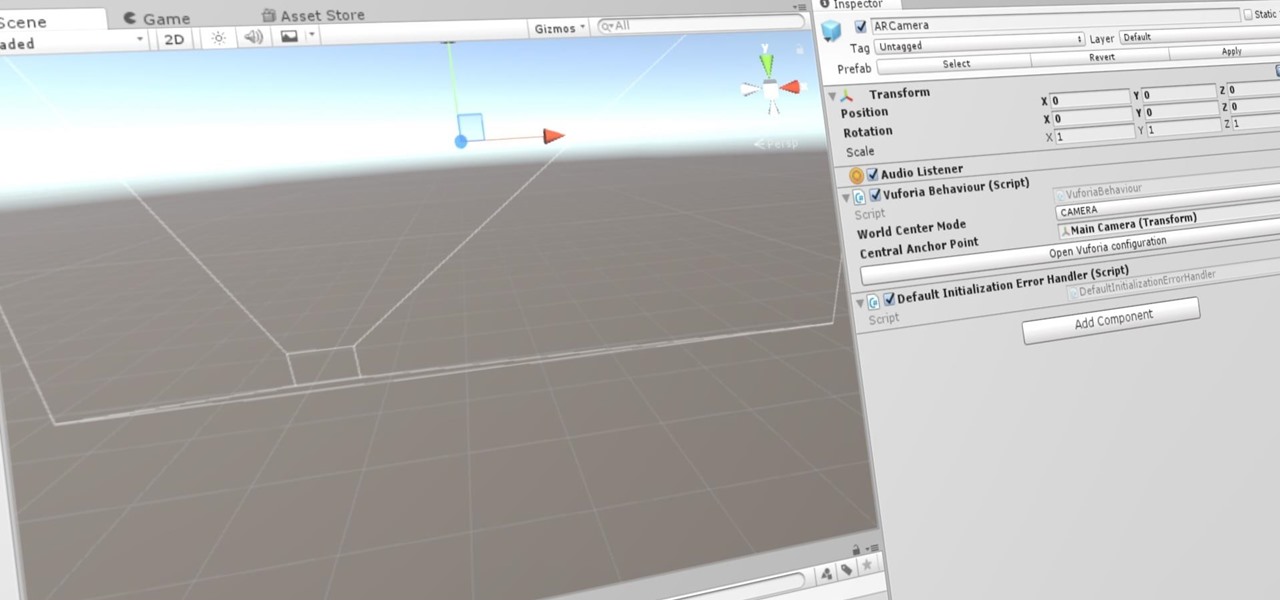
Now that we've set up Vuforia in Unity, we can work on the more exciting aspects of making physical objects come to life on the HoloLens. In this guide, we will choose an image (something that you physically have in your home), build our ImageTarget database, and then set up our Unity camera to be able to recognize the chosen image so that it can overlay the 3D holographic effect on top of it.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

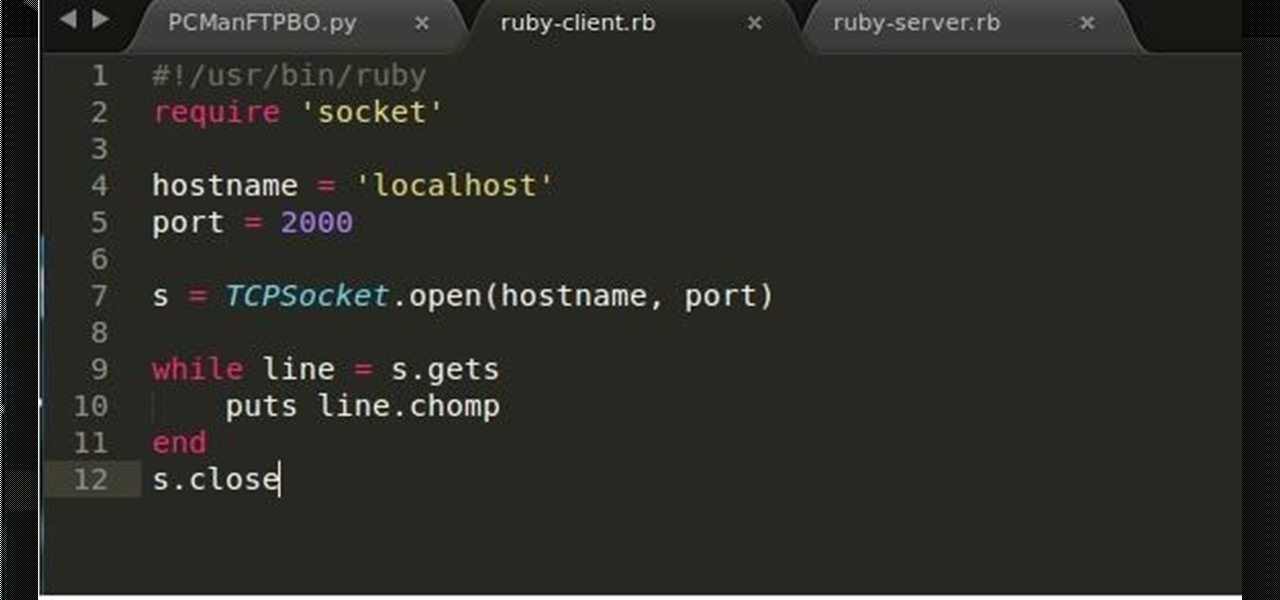
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

This is just a heads up that thieves are now using GPS fitness apps to target people. Thieves are using popular GPS fitness apps such as Strava to find out where you live where they will then come and steal your bikes.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

In this how to video, I discuss three different exercises that have really helped me to tone my waistline. Although you cannot specifically target different fat deposits while dieting, it is still important to perform these exercises to give your core and waist that aesthetic look. These exercises have given me great results, but a solid diet and a good training program is also extremely important to sculpting your body. Enjoy!

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Software needed: Voodoo motion tracker, virtual dub and blender

First of all you have to understand that this exercise is very versatile and you can actually target different areas of your chest just by twisting your wrists. First of all lie down on the bench and hold the dumbbells in your hands. You can do this upper chest exercise to build your upper chest muscles using dumbbells. Now bring your dumbbells down and then again take them up. While bringing your dumbbells you have to twist your wrists towards inside such that your palms are facing away from...

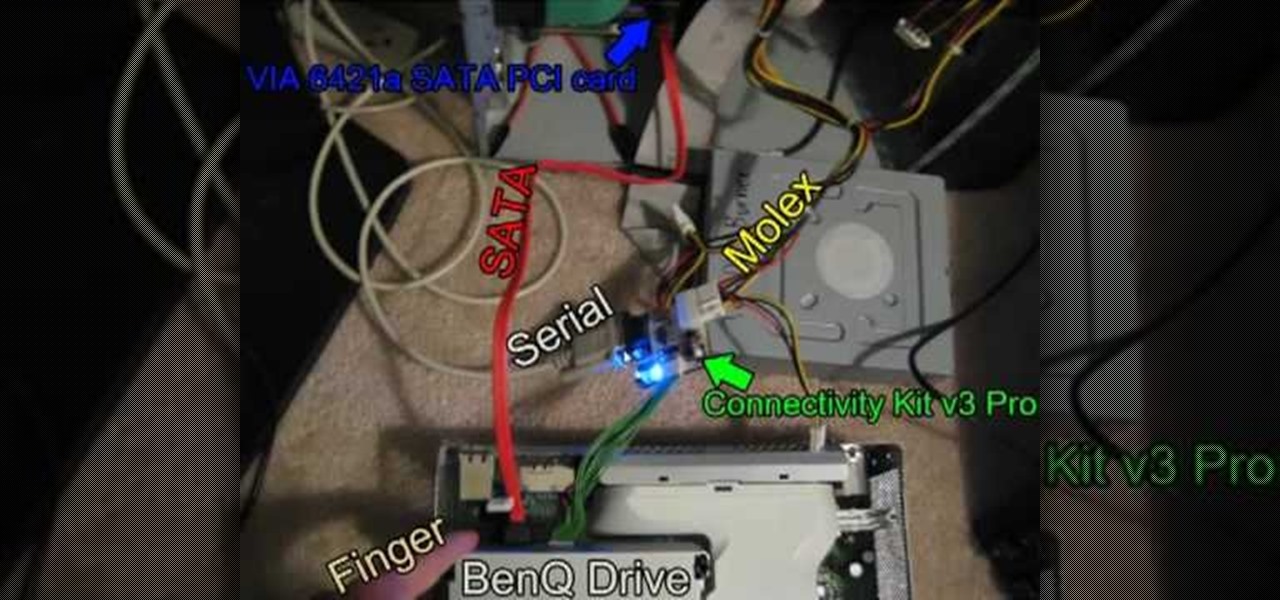
In this Video Games video tutorial you are going to learn how to flash the Benq VAD6038 Xbox 360 DVD drive. This video will show how to do this with the connectivity kit and the jungle flasher. You will need a compatible card for this. VIA 6421a SATA PCI card is probably the best card. Install the VIA card and make the connections as shown in the video. Before you power on the connectivity kit, install the port IO 32 drivers and also the USB drivers for the connectivity kit if you are using U...

You can organize your closet with simple drawers and shelves or racks that you purchase at a discount store such as Target. Outside of your closet you can have drawer space (use transparent drawers) by labeling your own drawers with large labels that you have written the contents of the drawer on and placed this at the front where it will be visible. The drawers can be divided into short sleeved sweater tops, long sleeved sweater tops, tanks, vests, short sleeved tees, long sleeved regular to...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...

Here's a quick and simple booklet that can be made out of two sheets of paper. It's great paper craft for a school project or just fun. All you need is paper and scissors. Fold both pieces of paper in half hamburger style. Use scissors to cut knotches into your fold. Fold your other piece of paper hotdog style. Follow the rest of the instructions, assemble and you have a quick and simple paper booklet.

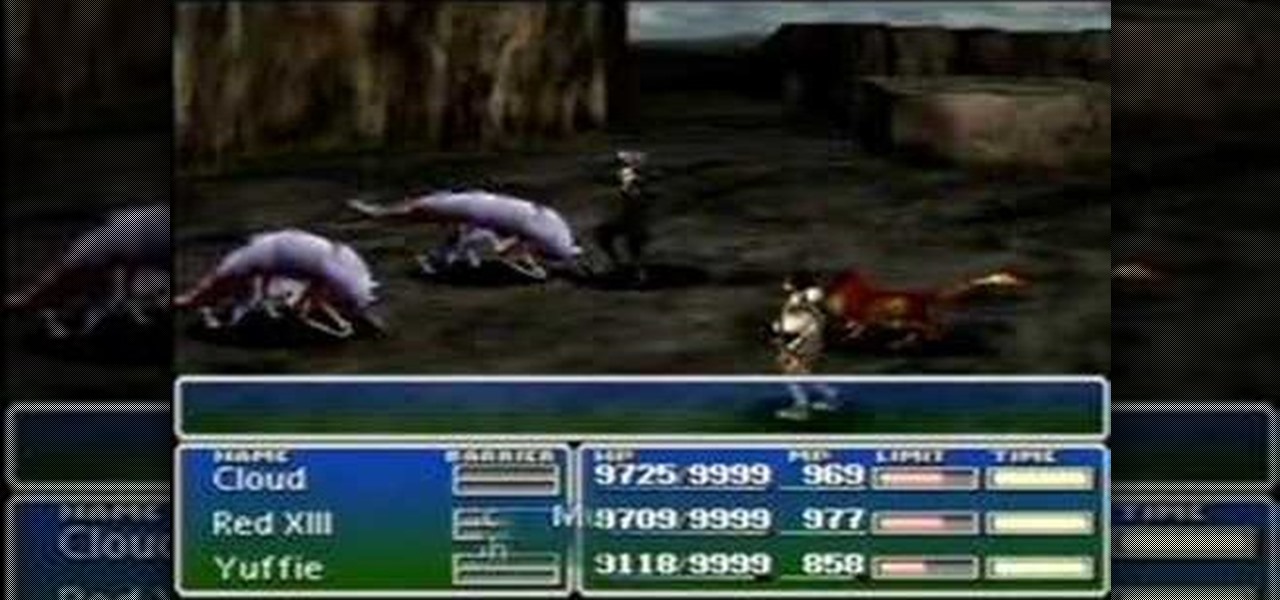
In Final Fantasy VII, it's possible to max out vitality without any store-related progress needed if your strength stat has already been maxed. Take a look at this video and learn how to max out vitality simply by targeting an enemy called "spiral".

Have you ever had the urge to throw a ball at someone, but knew you could never do it? Regardless if for merely a gag or out of frustration, we all have that someone we would love to use as target practice, but know fully well we can't purposely try to hurt another person. Well, we have the solution here...

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Smartwatches are an excellent way to keep track of our smartphone's notifications as well as our own fitness. However, these devices are not usually cheap. If you'd rather not pay a premium for a piece of wearable technology, check out all the Black Friday deals on smartwatches — we've got all the best ones listed right here.

Our smartphones have outlived the Walkman, iPod, and even stereo systems, to some degree. So it makes sense to treat your iPhone or Android device to a quality pair of headphones, whether you're a hardcore audiophile or just an everyday music lover. This doesn't come cheap, of course, so why not buy them on Black Friday?

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

There's a good chance that an iPhone is on one of your Christmas shopping lists, but these things are uber-expensive now, making it hard to justify as a holiday gift — even for yourself. That's what Black Friday is for, though, which can help you save a little bit of cash on an iPhone purchase — or at least, give you something in return to help you get even more holiday presents.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...