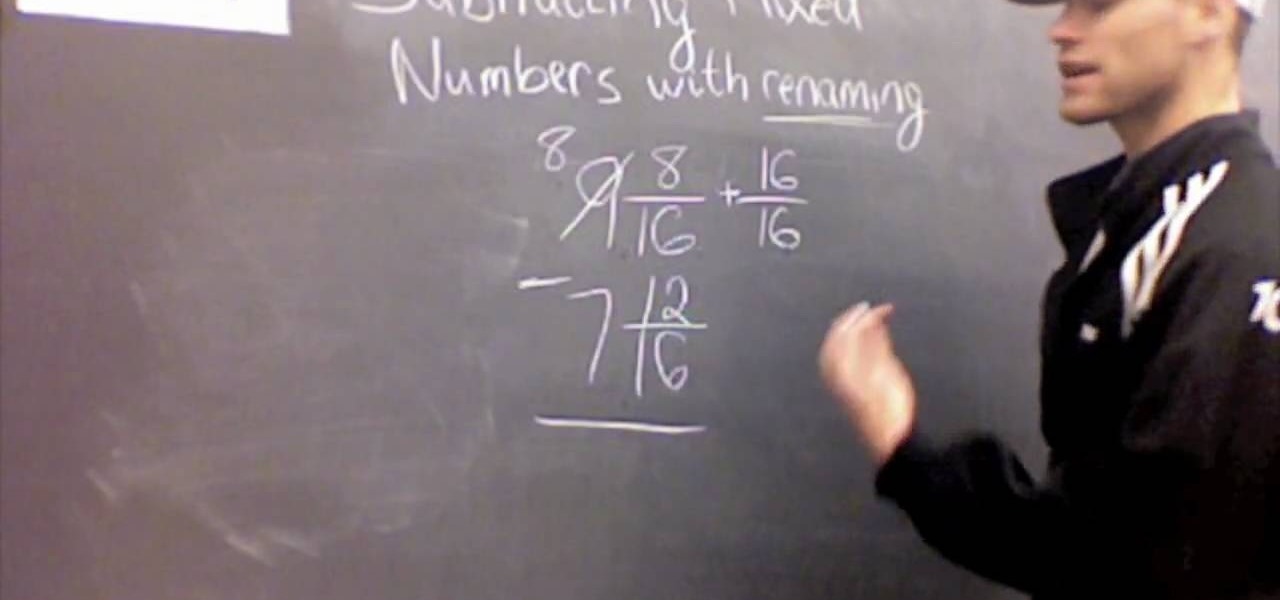This video is about deriving the area of a circle of radius 'r' using polar co-ordinate. First, we draw a circle and its radius 'r'. Then draw another radius close to it, so that it forms a small triangle-like figure. To find the area of the complete circle, divide the circle into similar small triangles. The area of each triangle is given by half the product of its perpendicular and the base. We give the angle between the two radii as d?. We get the area of the small triangle by substituting...
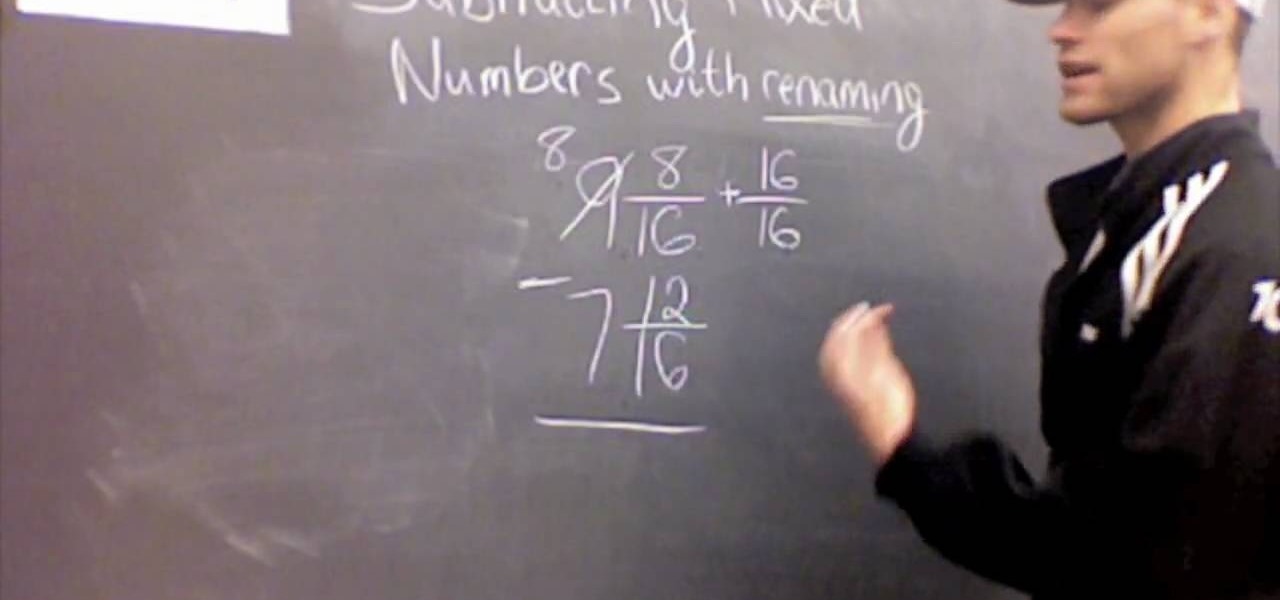
This video is about subtracting mixed numbers and renaming. 1. Start on the right side of the problem.

This video demonstrates how to clean a wood burning stove. Cleaning the wood burning stove is a rather uneasy and untidy task. But this video has good advice and simple to follow steps to simplify the task, in a clean way.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

Can you be too lazy for video games? That's how I feel sometimes. I want to play the latest PlayStation has to offer, but I can't be bothered to get out of bed. As if Sony read the minds of lethargic gamers everywhere, the company has released an amazing thing — PS4 Remote Play allows you to play your PS4 on your iPhone, no TV required. The best part? It's 100% free.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Augmented reality experiences for consumers, for the most part, are relegated to mobile devices at present, but creation and development of those experiences is still a province of desktop computers.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

With Google's release of Poly API on Thursday, the search giant has found a way to simplify the workflow for AR creators by enabling the ability to integrate its 3D object search engine Poly directly into an application.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

There's a popular new trick in the fishing community and that's tying a braided line to a fluorocarbon leader line. To do this, you'll need to know the proper knot, and this video will show you how to do it. With this method you will reduce some of the problems of twisting and tangling with using braid right up to your lure. Check it out. The braid helps absorb some of the pull on the line, so see if you can feel it when you go to land the big one!

This video will show you how to tether your Samsung Messager 2, (the MetroPCS phone) to your PC to use as a modem for internet access. This will allow you to use your cell phone as your internet connection point, meaning you'll connect to the net for the cost of your cell phone's data plan. You will need your Samsung USB cable, a PC with Windows 2000 or higher, all current drivers for your phone and PC, and you will also need to head here to get the Samsung PC Studio program. This is part 1 o...

If your iPad, iPhone 4 or iPod Touch is already on a tethered jailbreak, this is the tutorial on the new Redsn0w release for all you experienced users. An untethered jailbreak is a type of jailbreak where the device does not require rebooting with a connection to an external jailbreak tool to power up the iDevice. Jailbreaking allows users to get root access to the command line of the operating system, to download otherwise unaccessible extensions and themes, or install non-Apple operating sy...

Someone has just smashed the side mirror off your perfect Nissan Altima that you parked on that busy road you know you shouldn't have parked on anyway, so now it's up to you to repair it— unless you want to pay an overpriced mechanic, who will charge you for parts, labor, and whatever else he thinks he deserves. If you're up for repairing your side view mirror by your lonesome, for cheap, then this video by Richpin will show you the exact steps required to fix your Nissan Altima's side mirror...

This video by repairs universe shows viewers how to replace the battery in the 2nd Generation iPod Touch. The tools you will need for this project include safe-open pry tools and a small phillips head screwdriver. To begin, remove the screen by releasing several clips that hold it to the frame using the safe-open pry tool. Run the tool between the case and the glass along all edges. Gently pull glass off and pry off the digitizer. Next, remove the small screw in the upper corner, lift up the ...

Make sure you're getting the best experience from your Blu-ray movies on your PS3 by optimizing your PlayStation 3's audio, video and display settings. Scott Lowe for IGN, shows you step-by-step, the exact process for an enhanced Blu-ray experience.

Circuit bending an audio device typically involves removing the rear panel of the device and connecting any two circuit locations with a "jumper" wire, sending current from one part of the circuit into another. Results are monitored through either the device's internal speaker or by connecting an amplifier to the speaker output. If an interesting effect is achieved, this connection would be marked for future reference or kept active by either soldering a new connection or bridging it with cro...

It's good to know the IP address of your computer. With this information, you can track your computers usage online, and will also know how to change it if you want to surf unnoticed. This tutorial will show you exactly how to find the IP address of your PC, so you will never be lost again. There are a number of programs that require your IP address, for example if you are setting up an external device like an XBox live to your Internet connection, you will need to make sure the IP address is...

Syncing your bluetooth earpiece to your BlackBerry device can be tricky. But pairing your bluetooth enables BlackBerry with your earpiece is actually quite easy. Best Buy has answers. The Best Buy Mobile team explains how to connect a Bluetooth earpiece to your mobile device. See how to access connections set-up on your Blackberry and also see how to wear a Bluetooth headset.

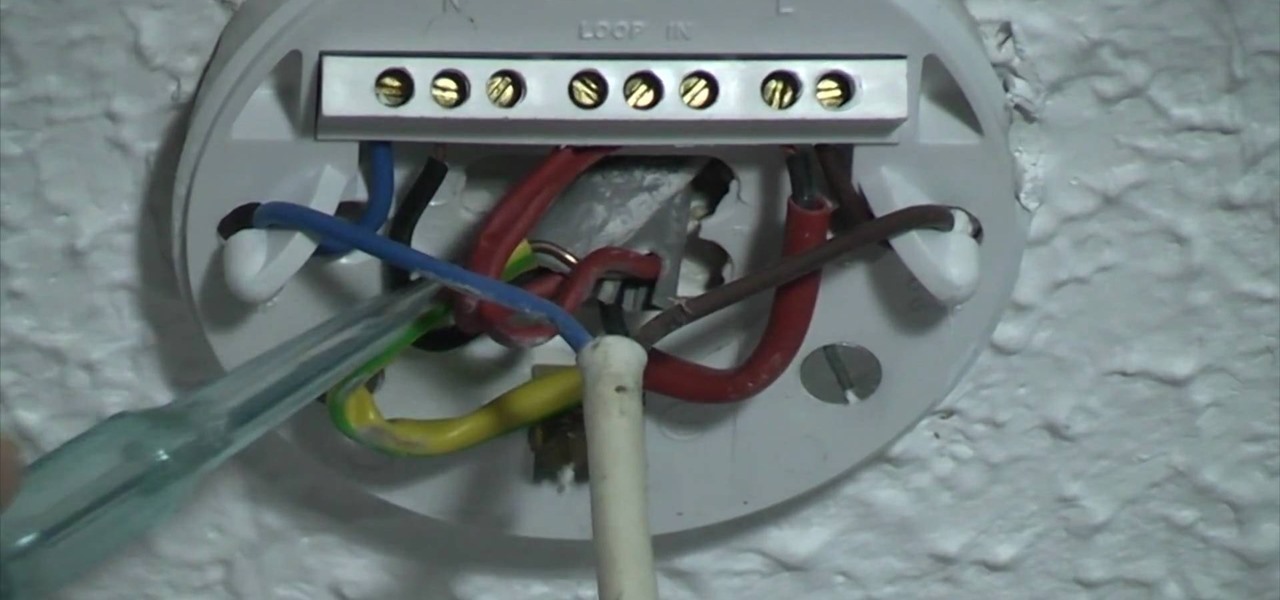
Modernize your home with a new ceiling light fixture. That old, traditional ceiling rose with the decorative chandelier or light fitting might just not look right anymore, with all of your modern furniture and appliances. The best thing… replace it.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to broadcast live online.

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

Learn to make your own super effective bass traps and acoustic panels with materials from your local hardware store, just by watching this home audio video tutorial.

In this soaring demonstration, deaf percussionist Evelyn Glennie leads the audience through an exploration of music not as notes on a page, but as an expression of the human experience. Playing with sensitivity and nuance informed by a soul-deep understanding of and connection to music, she talks about a music that is more than sound waves perceived by the human ear. She illustrates a richer picture that begins with listening to yourself, and includes emotion and intent as well as the complex...

In this clip, you'll learn how to speed up the Internet connection on a PC running the Microsoft Windows 7 operating system by using custom external DNS servers. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Having a backup sump pump is integral in making sure your basement is always protected from water, and if you have the Basement Watchdog battery backup sump pump system, this video will show you the complete installation procedure. Find out how to build a pipe connection to the discharge pipe, install check valves, connect to the backup system and more.

In order to work a quadratic equation, you should, first, try to simplify it. Try to move your variable to one side of the equation and the numerical values to the other. For example, in the equation 3n + 5n 2 = 0, you should try to move the 2 to the other side, by adding a positive two to both sides. Then, you should add together the like variables. This will give you 8n = 2. Then, you will need to divide both sides by 8. The answer will be n = 2/8. The quadratic formula is ax2 + bx + c = 0....

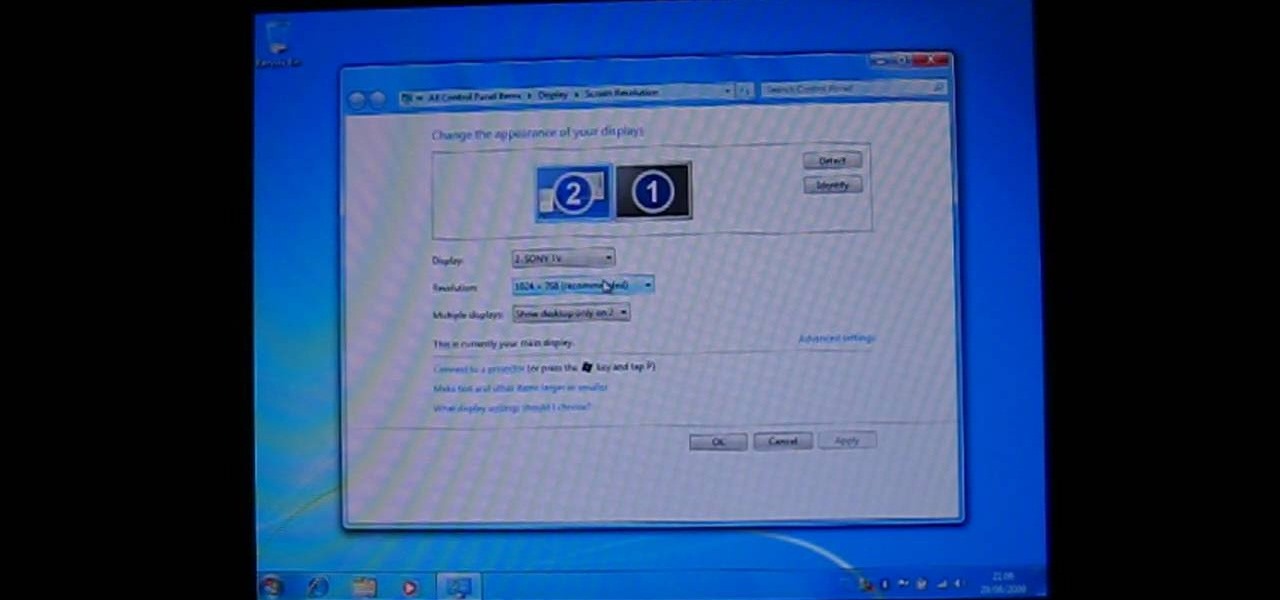
This Windows tutorial demonstrates how to connect a laptop with an Intel graphics card to a TV using the VGA port output in the laptop and a VGA cable.

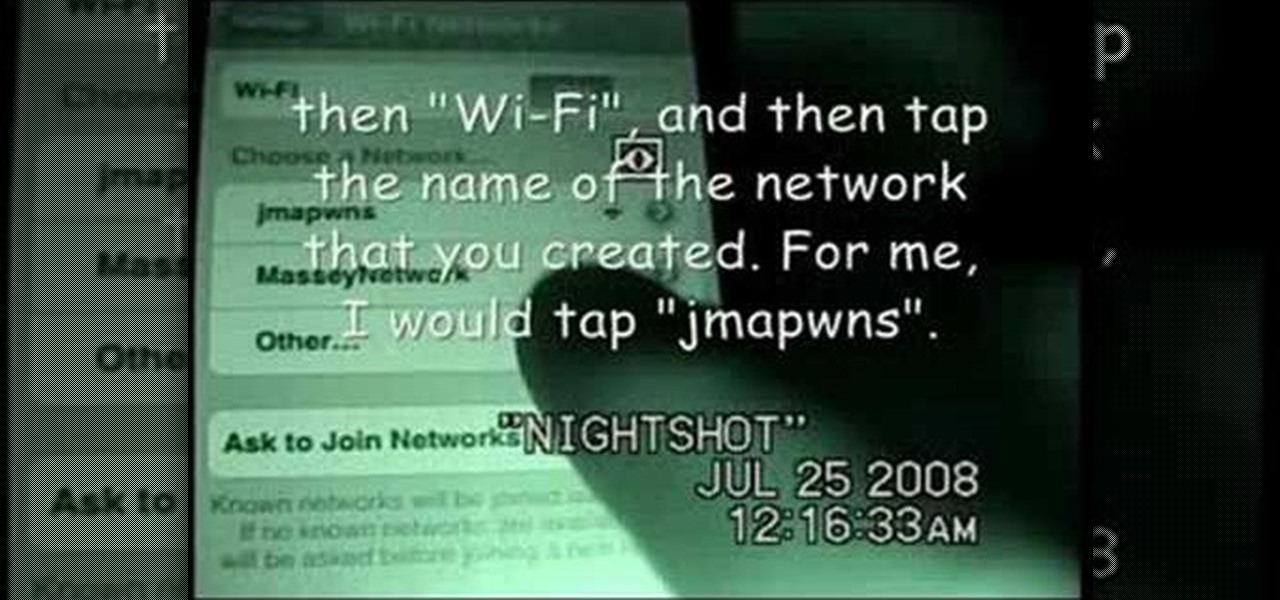
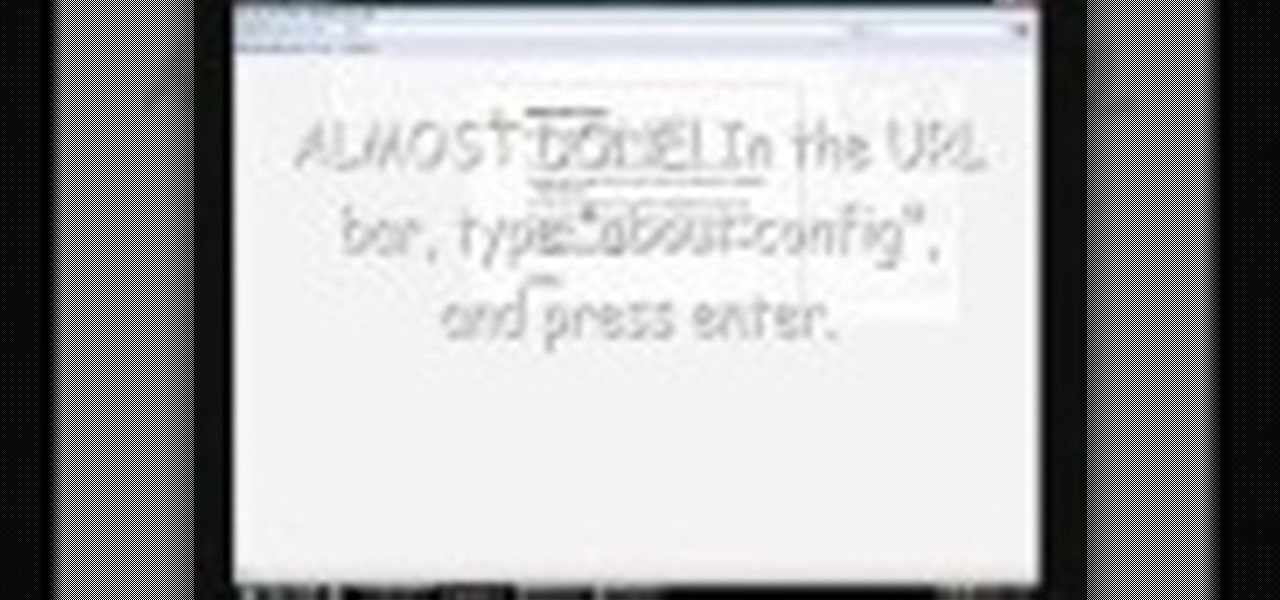
If you have T-Mobile and haven't quite figured out how to get MMS working with it on the iPhone, check out this video. This tutorial will cover activating the iPhones original MMS feature to work with t-mobile. This feature also allows you to share your iphones internet connection with other computers.

Need some IBM Lotus Notes help? Well, check out this video tutorial to learn how to connect to a Lotus Domino Server from Lotus Notes. This is a very quick connection to the Lotus Domino Server from Lotus Notes. Easy to follow.

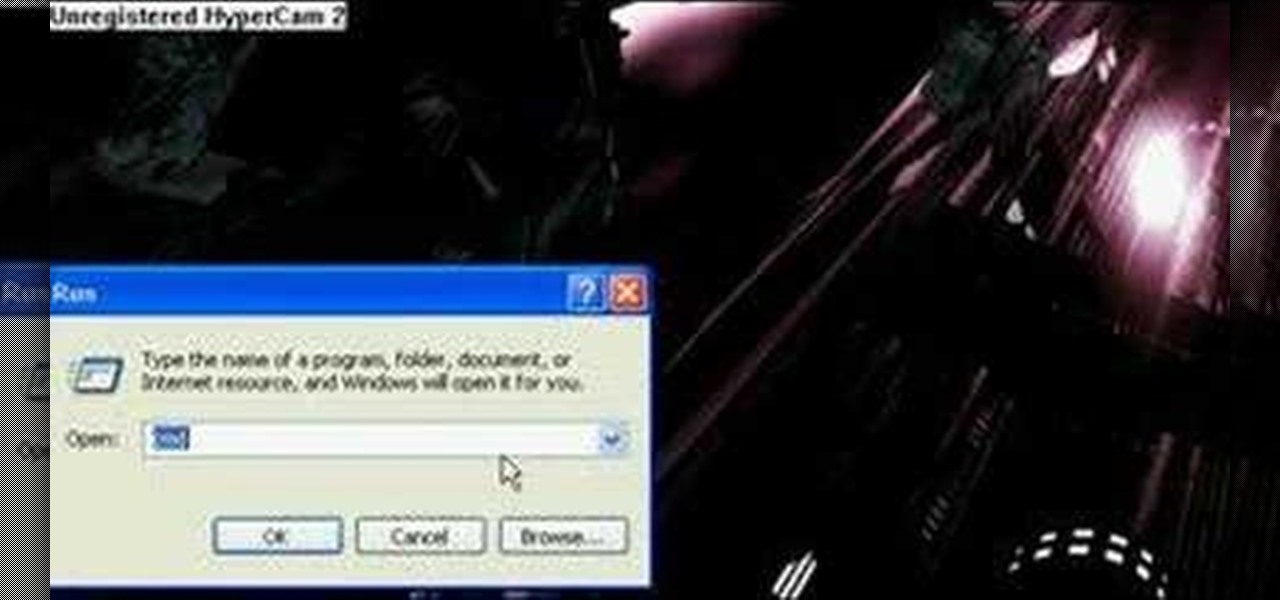
This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration steps required to properly tether an iPhone 3G in Windows XP so that you can use its EDGE or 3G internet connection on your PC, for free.

This video will show you how to tether an iPhone 3G in Windows Vista so that you can use its internet connection on your own computer!