In this video tutorial you will see how to Pandora a PSP slim battery. You will need a knife for this. When the normal battery is in the PSP, when you switch it on, it will log on just normal. Now remove the battery, put the knife in the joint of the battery case and move it up and down and slit open the case. Then pry it open and remove one half of the case. Then flip open the flap on the battery and cut off one connection on the battery as demonstrated in the video. Now put the battery back...
FROMAN1115 teaches you how to change your NAT type to Open on your PlayStation 3. On the PlayStation 3, go to Settings-Network Settings-Settings and Connection Status List and write down your IP. Go to your PC and start your internet browser. Type in 192.168.1.1. This will bring up the router settings page. Go to Applications and games and then DMZ. Check the first box that says Enabled. Enter your IP address below and click ok. Your settings have been saved and you can enter a new internet m...
Evan shows viewers how you can use the PlayOn option on your Wii to watch videos on Netflix or Hulu. He starts off by showing how you can set up your wireless network and your connection settings. You will need to do this first if you have never done this before. To get PlayOn you will have to purchase it from the Wii Store using Wii Points. Evan also shows how you can link your internet channel to PlayOn so that you can view videos in just seconds. Watch all his tips and techniques and you c...

Leeann of Hierchiss explains how to turn a TV into an oscilloscope. Turn the TV on and make sure it works. First, unplug the power. Take the back off the television. Cut the four picture wires that attach to the circuit board. Strip the ends of the wires. Tape the remaining wires off to prevent short circuiting. Clamp the red and yellow wires and attach to a 1/4 inch jack which feeds into a tape player. Repeat the same process for the green and blue wires. Plug in the TV to make sure the conn...

This video will show you how to find your own IP address in Windows Vista, which is more difficult and confusing to use than Windows XP was. First, you should go down to the bottom right hand corner and find an icon of two computers, which is your network connection button. Click on the Networks and Sharing selection and find the section which says "View status". After clicking on this, you will find a section which will be labeled "IPv4". The numbers which are indicated after this are the nu...

Slow down? What!?! You've got to love the simplicity when it comes to long drive tips from long drive competitors. The long hitting Jamie Sadlowski shares his simple tip for more power, and it's not what you might think. See how to slow your golf swing down for more power.

This tutorial teaches you how to warm up your cello playing for an audition. By working the "pulling" muscles of your left hand you will create stronger more precise fingers, like "core training" for your hand. When you add these variations you will wake up and warm up your brain, open up new connections by challenging the coordination between your left and right hands. Watch this how to video and you will improve your cello playing with these warm up exercises.

Do you have the perfect timing? Timing your swing is important, but sometimes a clock can do a whole lot more to help your golf swing. By imagining the face of a clock, you can effectively train your body to calculate the proper swing length for shots from various distances. Sound intriguing? Let Doug Hammer, PGA, show you the way. Watch this video golf tutorial and learn how to clock wedge shots.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

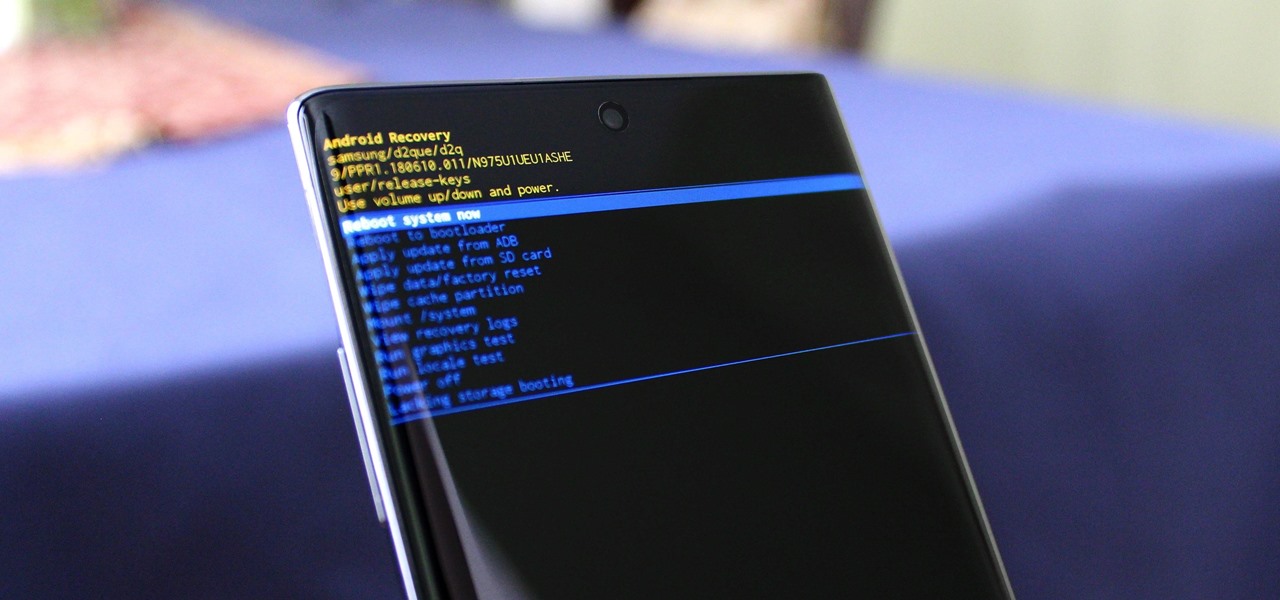
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Whether due to spotty cellular reception or just data that you want to save, popular navigation apps like Google Maps and Waze offer an offline feature that lets you navigate from one location to another in the absence of internet service. Apple Maps also lets you use its service offline on your iPhone, though the feature is not as straightforward as it is on its competitors.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

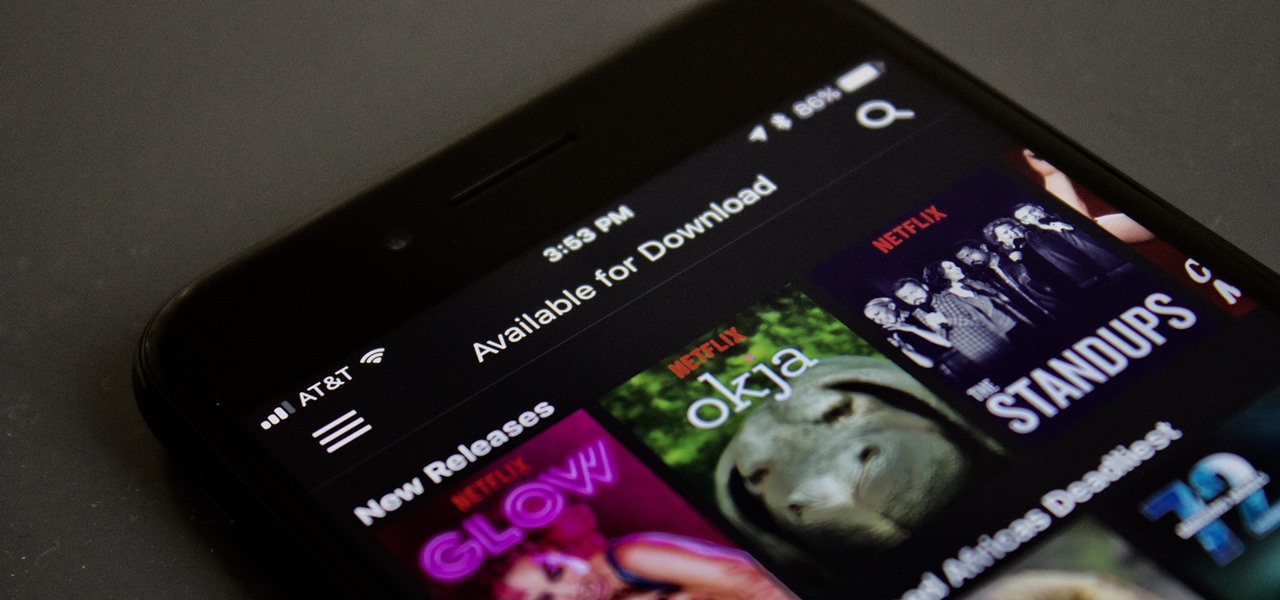
Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

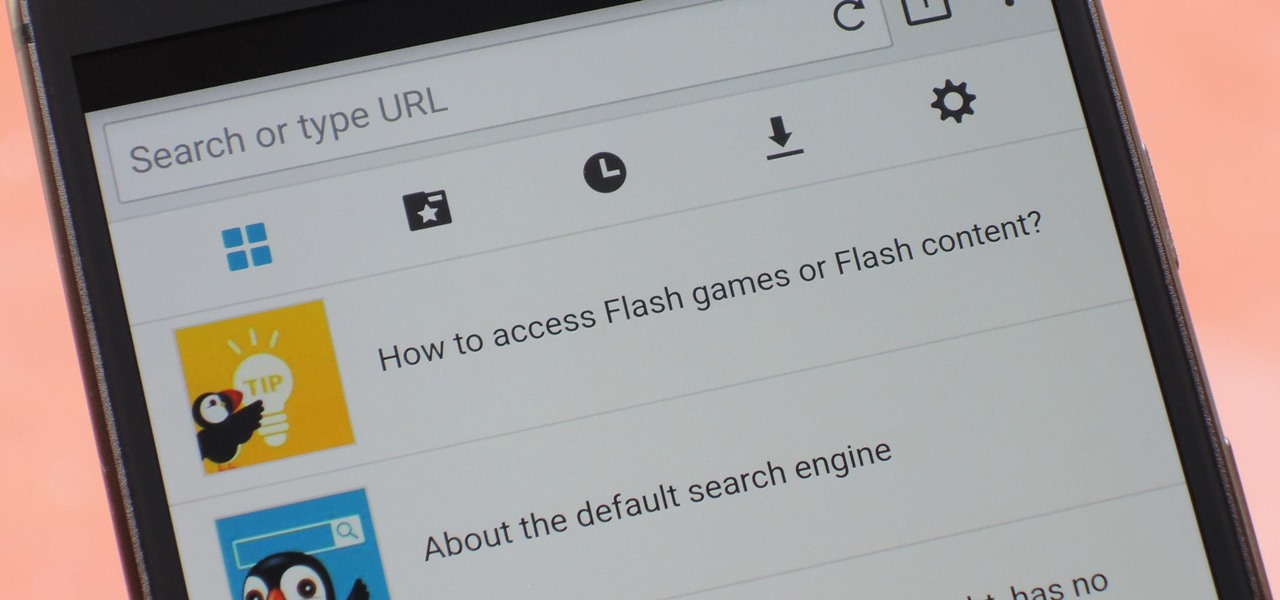
Once upon a time, Flash games reigned as some of the best entertainment the internet had to offer. But then came the smartphone, which quickly overtook this genre with similar games that you could play no matter where you were. If you yearn for the good old days, though, you'll be happy to know that you can still use the Puffin browser to safely play old favorites and discover new gems.

Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth on a daily basis to send and receive (or steal) data, what about the average Joe?

One thing you'll find a lot of in the Windows Store for HoloLens is demos and mockups, but very few projects are as fully realized and fully-functioning as Muralize. Created by Magnopus, an all-female development team, Muralize first appeared in the Windows Store in late-November of 2016, and makes it easy and fun to create real-life murals using a HoloLens.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

Shopping: you either love it or hate it. With a tight budget, shopping can become a huge headache for even the biggest shopaholic. We've all been there, and we've all given in to our impulses and bought something we probably shouldn't have. Yet strolling through the mall doesn't have to require a strong will to keep your credit card from entering a downward spiral. You just need to keep your hands to yourself.

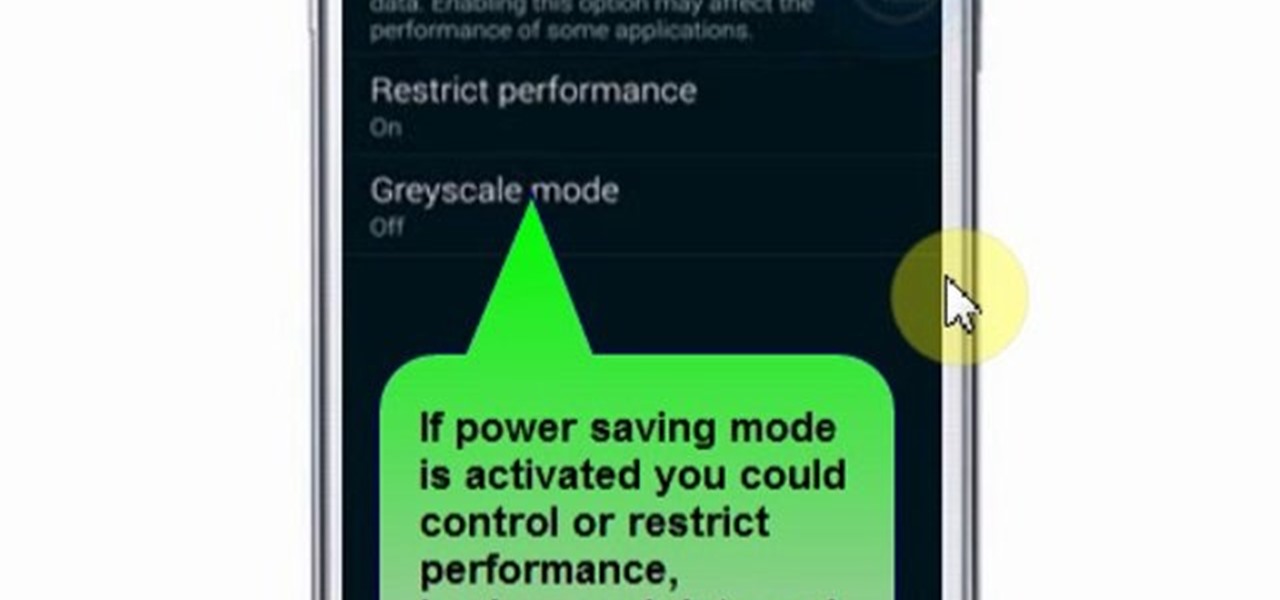
This video will show you how to set power saving mode in Samsung Galaxy S5 phone. Power saving mode will save or extend your battery life. So power saving mode will prevent unnecessary data usage. This mode will reduce screen brightness or turning off vibration and that will save your battery. This mode will control the display color which also saves battery. So this mode will save your internet connection usage and battery life. Follow the video.

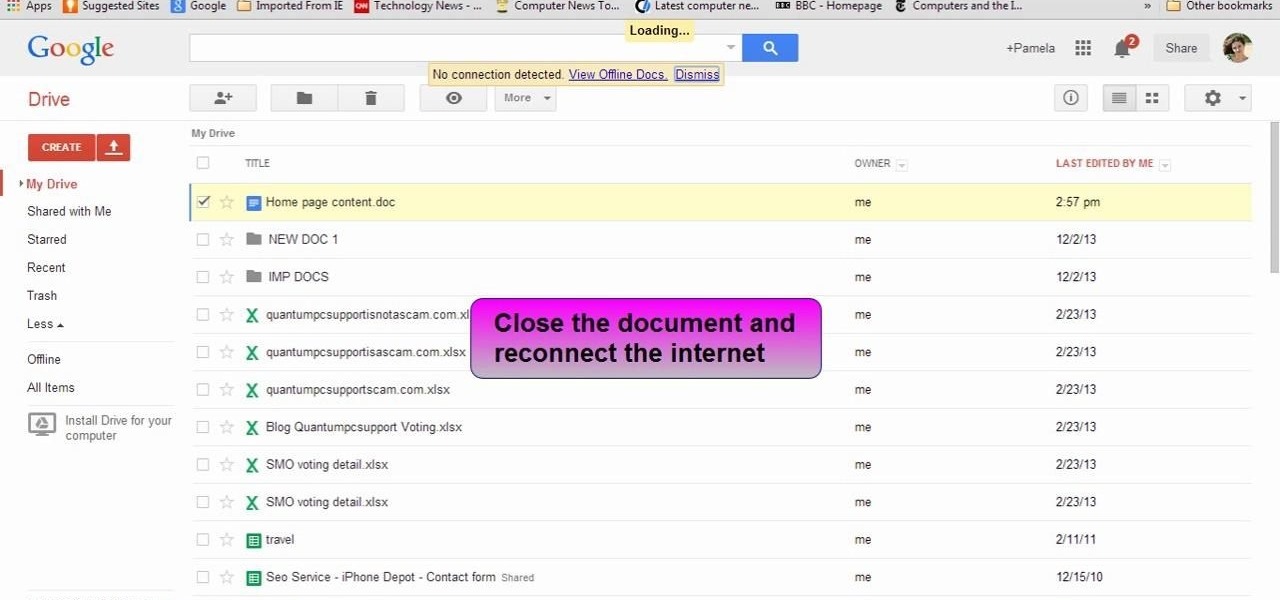
This video will show you how to view and edit Google drive documents offline. You could do this only in Google Chrome browser. If you are editing or viewing a Google drive file and suddenly internet connection is gone, you can still view and edit. You should only download an app for it. It will save your changes offline and will automatically update when you will reconnect with internet. Follow the video and do it in your Google Chrome browser.

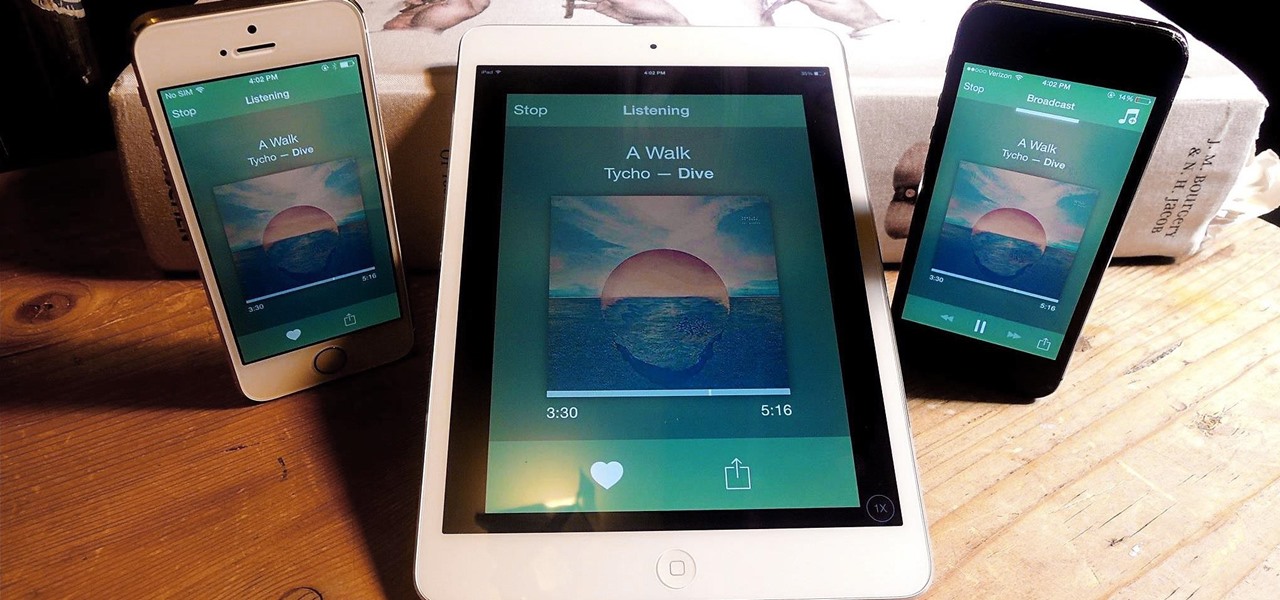
Officially, in order to use AirPlay to stream music from your iOS device, you would need either an Apple TV, AirPort Express, or an AirPlay-enabled receiver or set of speakers. Despite what Apple wants you to think, there is another way to stream music without any of those AirPlay-capable devices—you just need to have two iOS devices (or just one iOS device and a Mac).

Audibly, from iOS developer Nick Frey, allows you create playlists and sync your music across other iOS devices. Like the Samsung-exclusive Group Play or the older Seedio app, you can connect a slew of compatible devices to create a surround-sound stereo of sorts when playing your music.

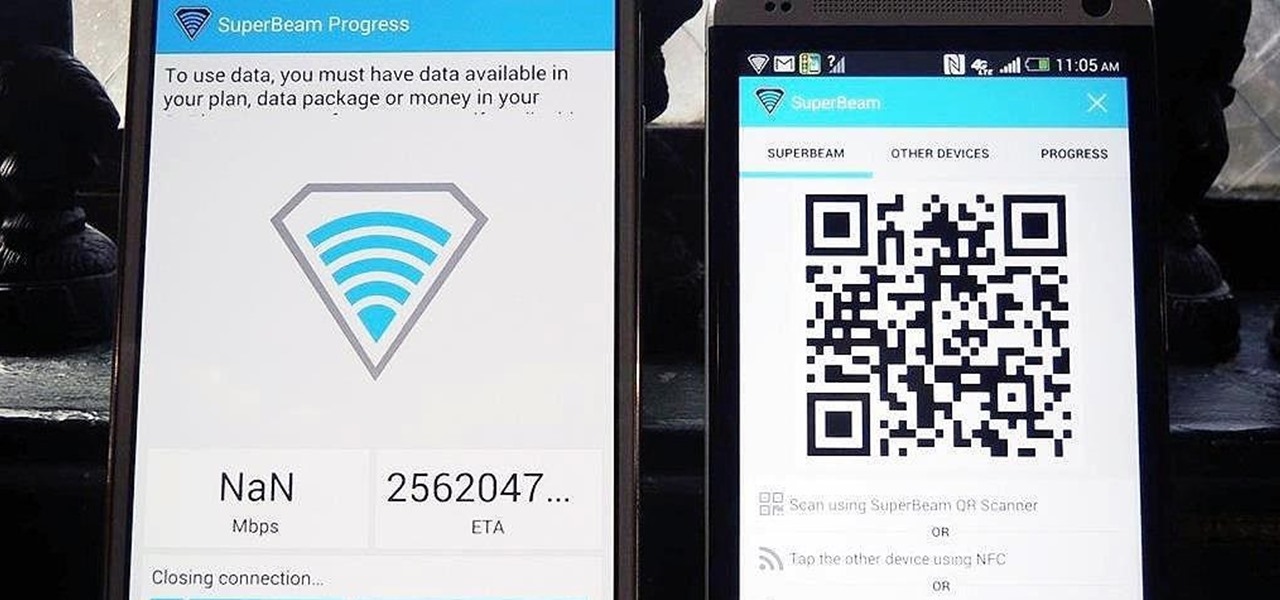
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

When life gets boring, you change it up. A little tweak in your schedule goes a long way in making your existence fresh again, and it could be anything from putting on deodorant to seeing a movie with someone you don't know. The more flexible you are in life, the more dynamic it should be.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

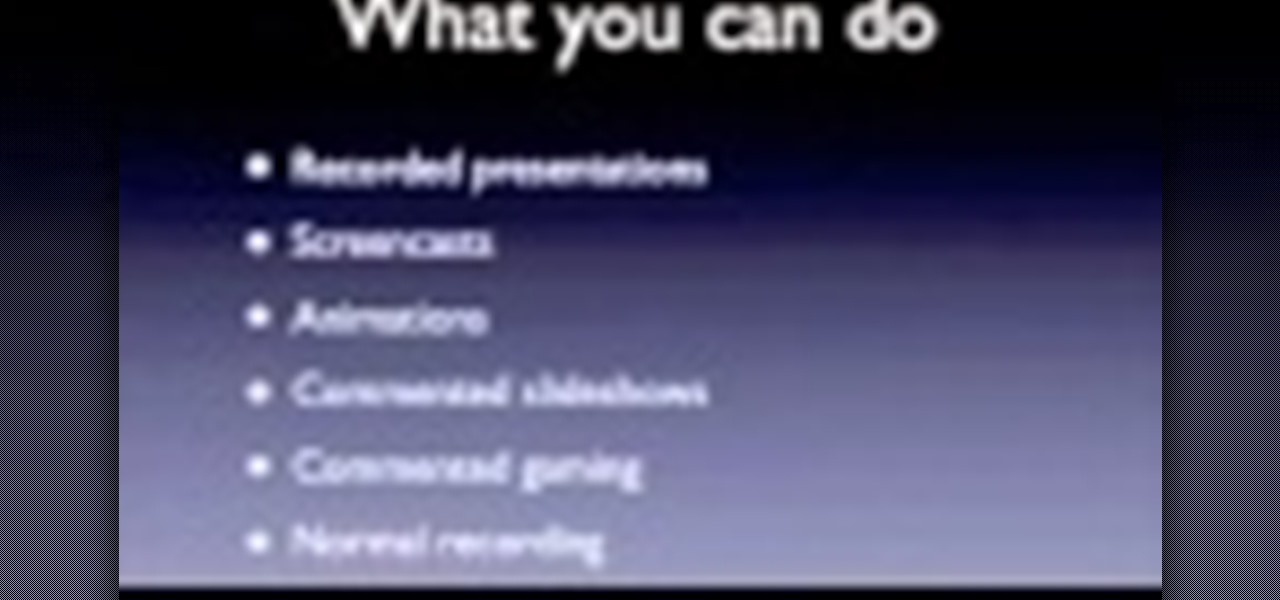
THis video shows you what types of videos you can make, why you should make videos and exactly whant you need to get started.

Need a good way to hold your iPhone up? There are a ton of smartphone stands out on the market, but they can be pricey or just downright ugly—and potentially phone damaging. But like the Une Bobine above, they do have their perks, like movability at almost any angle. But to alleviate pressure off of the connection port, Sharon Vaknin from CNET developed her own flexible iPhone stand—from an old desk lamp and suction cup.