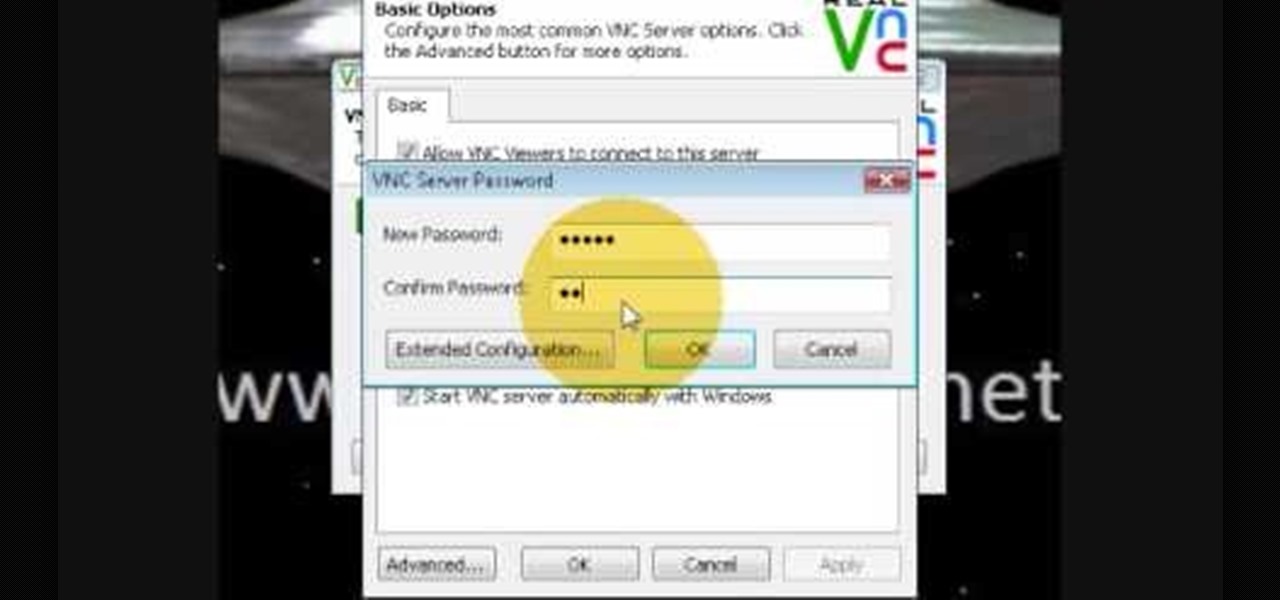
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

In a 2010 Toyota 4Runner, you can connect your phone to the car via Bluetooth. To do this, make sure the car is stopped. Then click the info button next to the navigation screen. Press "Phone" and confirm that you want to connect a new phone. Press "Add New". The car's system will begin searching for Bluetooth devices. Make sure that your device's Bluetooth feature is on. When prompted, enter the code on the car's navigation screen into your phone. A message that says "Bluetooth connection su...

Eric Scott demonstrates on how to use a pendulum to connect to the spirit. You can get any pendulum you have or use the custom made light plastic pendulum about five and a half inches long which may help to get your response very quickly.

Most use wireless computer mice these days for their computers, but there are still people stuck on wired optical mice, especially in an office environment. Those people are our targets. As pranking someone's computer may be frowned on, peripherals are fair game, and this prank from Kipkay takes their wired optical computer mouse and turns it into a foul-smelling smoke machine.

Ever heard of the Blink Card Trick? Well, it's an easy way to impress your friends, without having to know much about card tricks. Learn how to perform this card trick, step by step, in this tutorial.

Thanks to Apple's awesome user interface, it is extraordinarily easy to set your default printer. Instead of guessing which printer your document printed to, be certain of where it is every time.

Make life easier by printing to your nearest PC printer the first time, every time. You Will Need

Watch this video tutorial to learn how to play the Google language computer prank on a coworker. Change your colleague's Google settings with this easy prank, and watch their head spin!

Your garden hose can give you many years of good service if you treat it right. Learn how to properly care for your garden hose with this gardening how to video.

This pilates how-to video illustrates the Lateral Flexion exercise of the Side Leg Series. It is obviously a great exercise for lateral flexion and balance.

Learn how to do cable bar pull down triceps. Presented by Real Jock Gay Fitness Health & Life. Benefits

Covers installation of BMW X5 Subwoofer system for X5 00-06 (E53). Part 1 shows removal of original subwoofer (if present). Part 2 shows accessing the OEM amplifier and battery. Part 3 and 4 show amplifier connections. Part 5 shows amplifier power and ground for the subwoofer system. Part 6 shows fuse install, first amp sound test and amp mounting. Part 7, the final part, shows rear hatch assembly and final amplifier tuning.

If you have a limited mobile data plan on your iPhone, you know how tricky it can be to stay within your given allotment. Large app installs and updates, 4K resolution videos, and photo backups can waste precious data resources in no time. And apps like Apple News, Facebook, Mail, and Netflix eat data like it's candy. But you can nip the problem in the bud by restricting data hogs from your cellular network.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

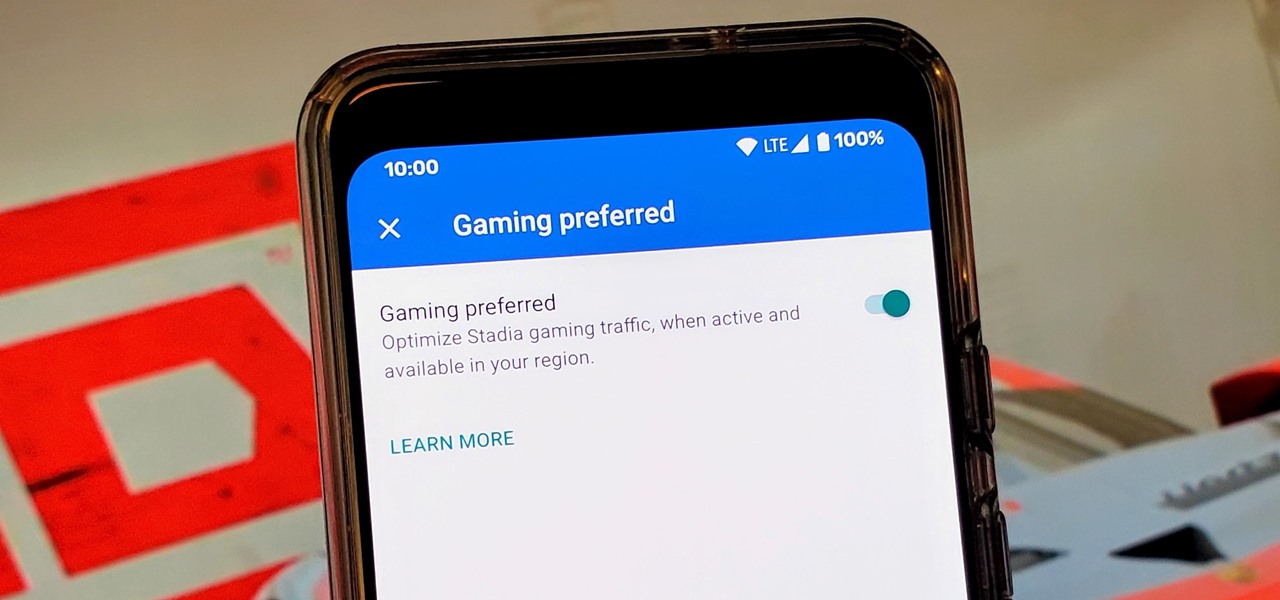
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Compared to the original AirPods, Apple's second-generation AirPods have better battery life, Hey Siri support, a more stable connection, faster switching between devices and call connections, less latency for gaming, and an optional Wireless Charging Case. If you plan on preordering the new model, you might want to skip the Apple Store and opt for Amazon instead to get it at your door quicker.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

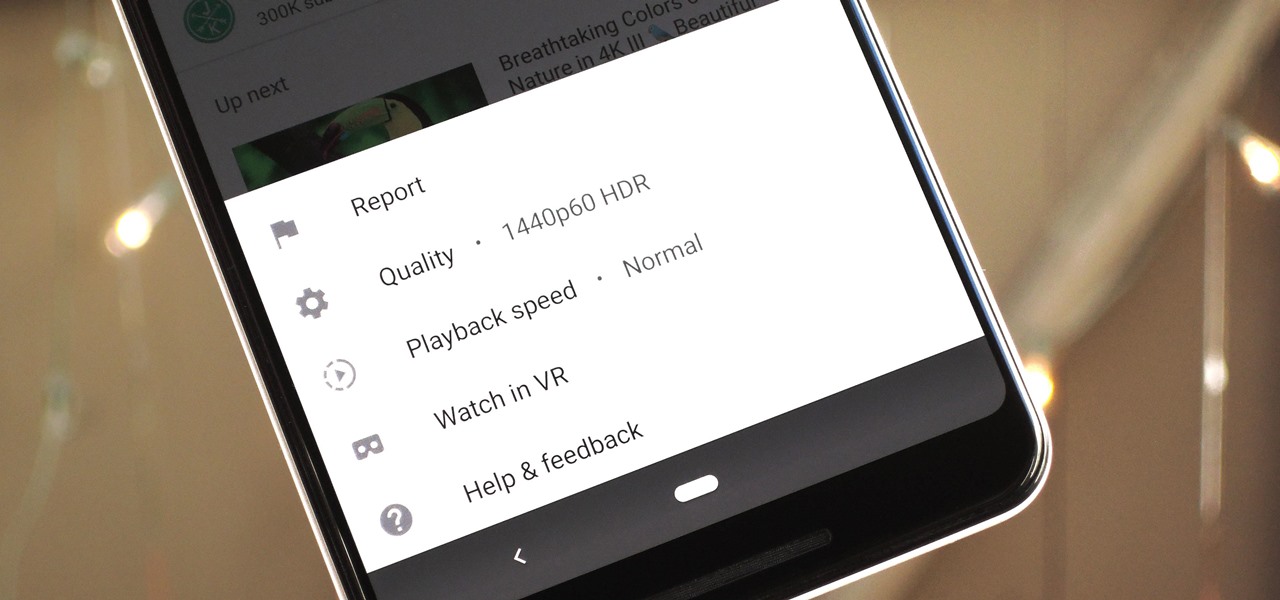
The YouTube app will default to 480p playback when you first open a video. It's supposed to switch to your screen resolution a few seconds in, but this isn't always the case. The regular YouTube app doesn't let you change this behavior, but like most things with Android, there is still a way.

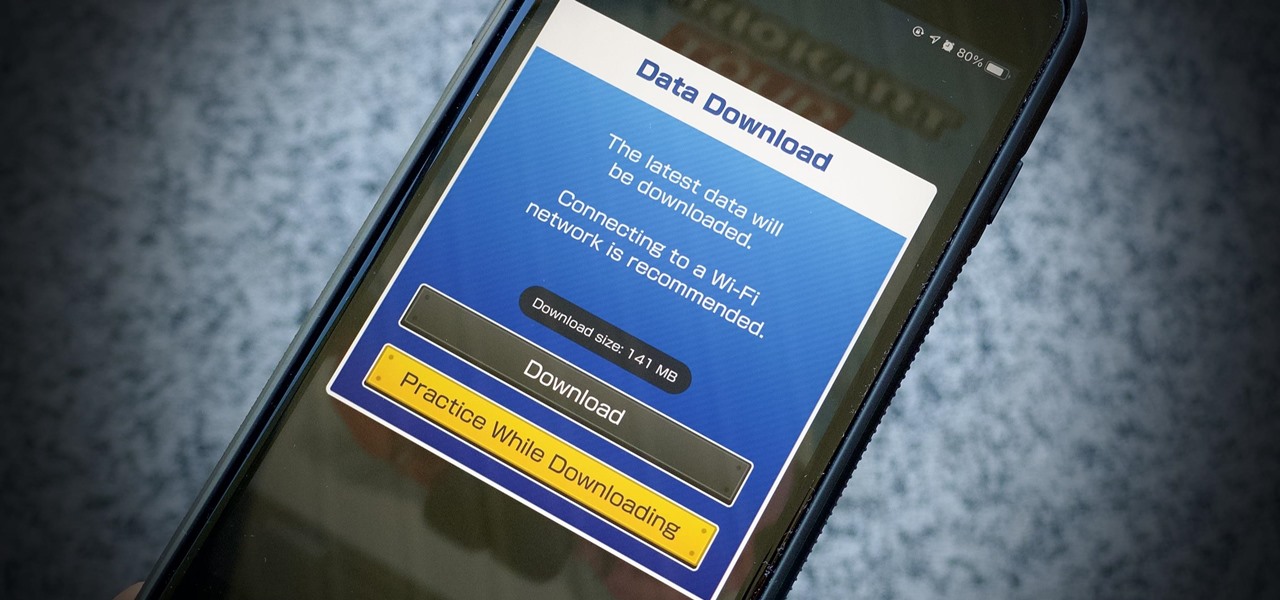
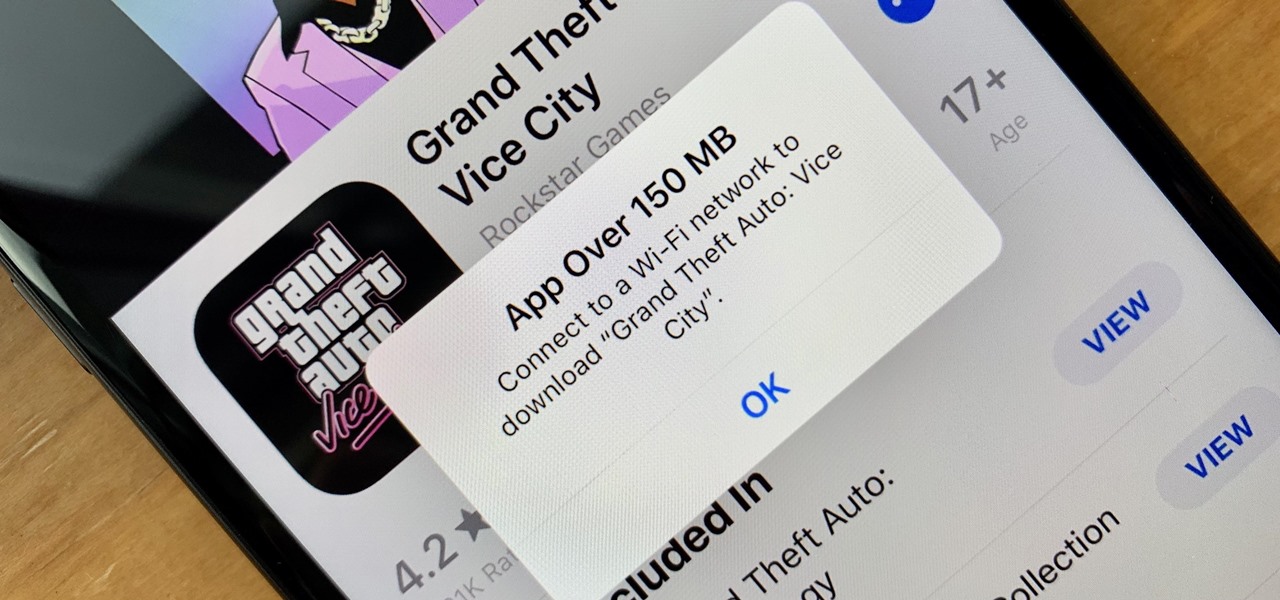
These days, cellular connections can be just as fast — if not faster — than traditional internet providers. That, coupled with the prevalence of unlimited data plans, means less worrying about hopping on a Wi-Fi network to download something. However, try to install an app or update over 150 MB, and your iPhone will insist you switch to Wi-Fi. We don't think this is very fair, so here's a way out.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

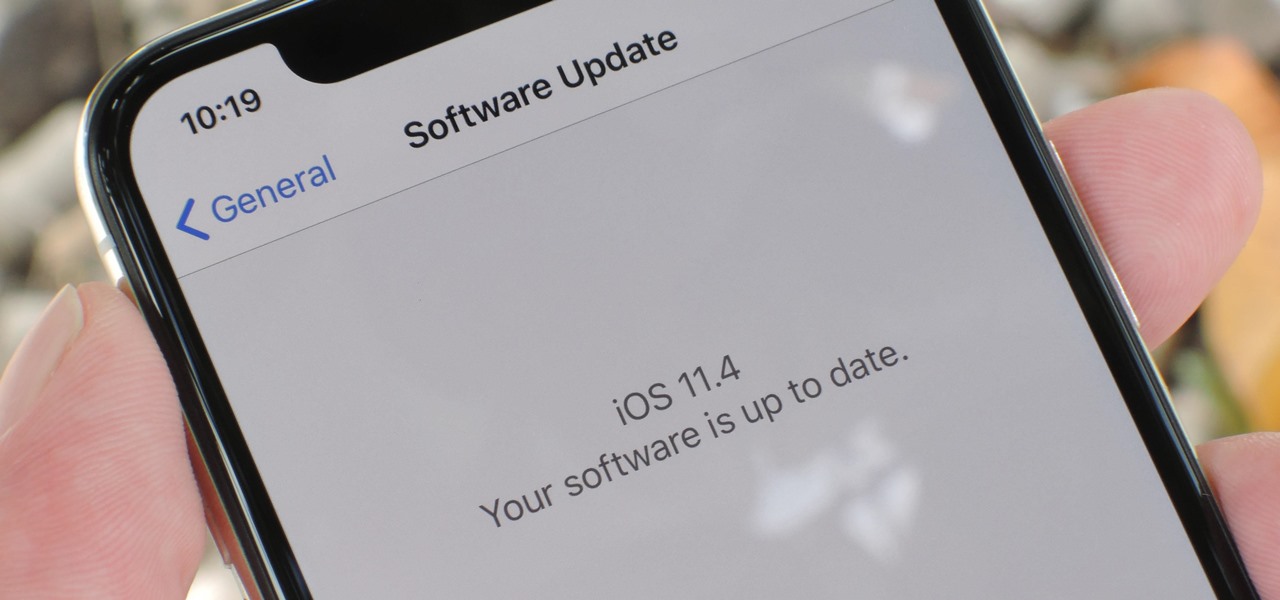
Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.

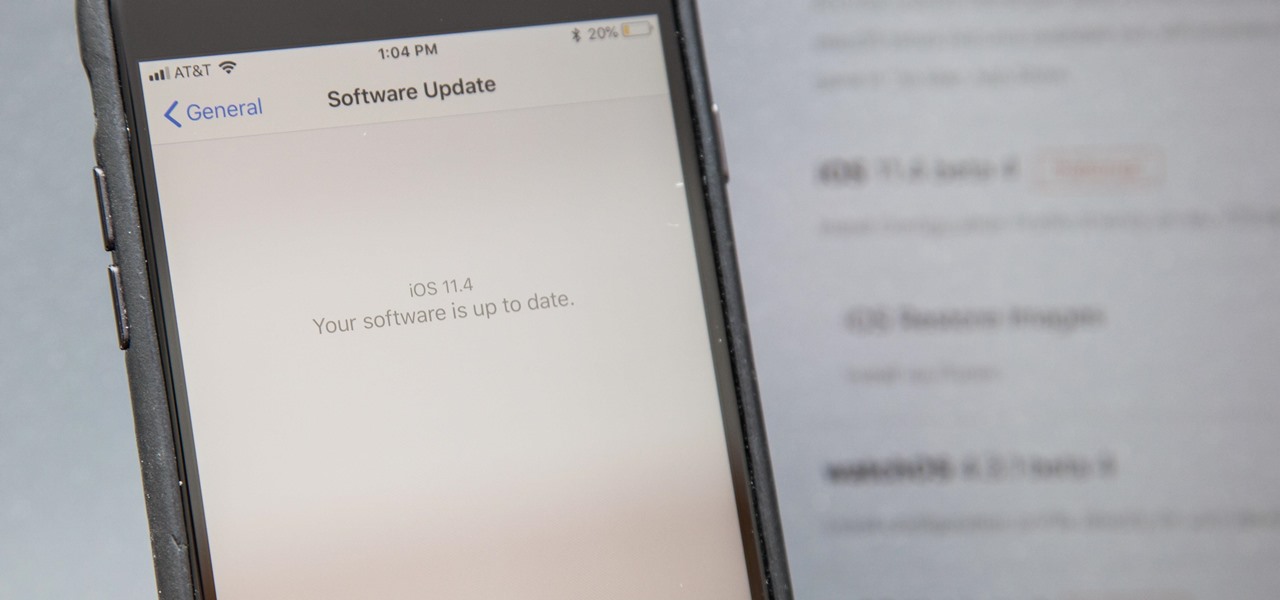
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.

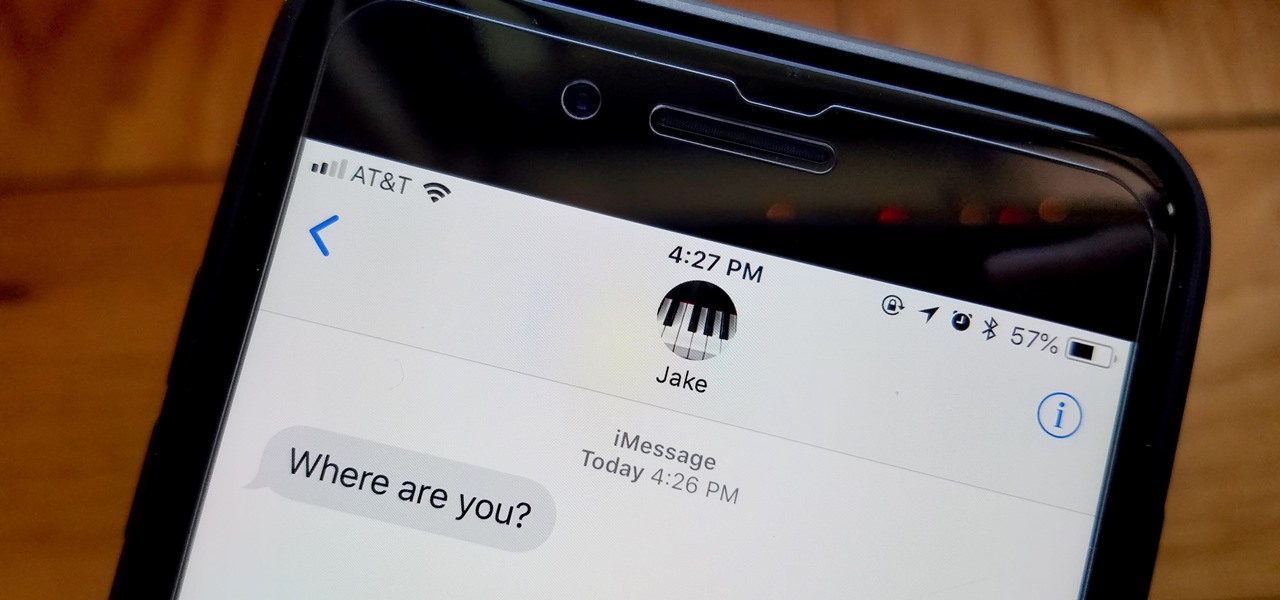
You're at the bar, but your friend can't find you. You could call them, but that wouldn't feel very 2018. Instead, let your iPhone do the talking. Right in the Messages app, you can easily send your friend your current location — all without interrupting the friends you're hanging out with.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of a standard phone. But if you're willing to dig a little deeper, there are ways to go full Immersive Mode on your S9 for good.

Many Samsung fans were excited when the Galaxy S9 kept the 3.5 mm headphone jack. While this is a rare delight in 2018, you also have the option for high quality audio playback over Bluetooth. When used with compatible headphones, the S9's new Bluetooth audio codecs can greatly improve audio quality.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

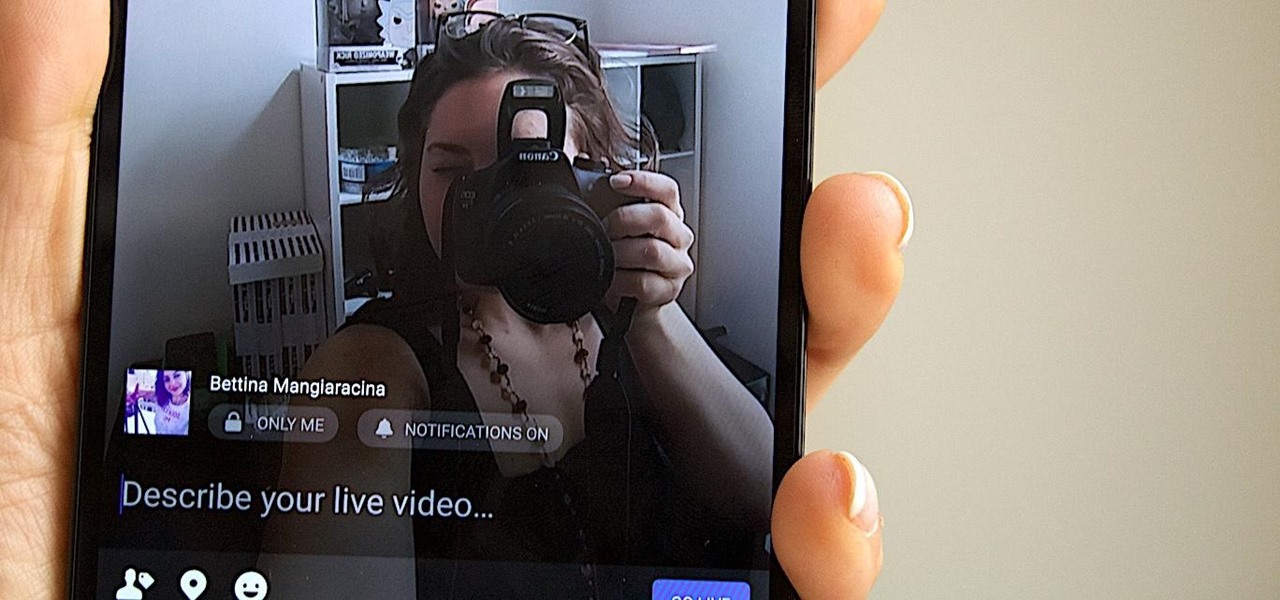
It looks like "going live" is another thing we all have to figure out how to do to remain relevant in this very Facebook-driven world. But why would you ever want to go live? That's really up to you.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.