This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

You no longer have to resort to a third-party email client on your iPhone to schedule messages to send whenever you want. Apple built the scheduling functionality into its Mail app, and it works with any email service you use in Mail, whether that's iCloud, Gmail, Yahoo, Outlook, or another service.
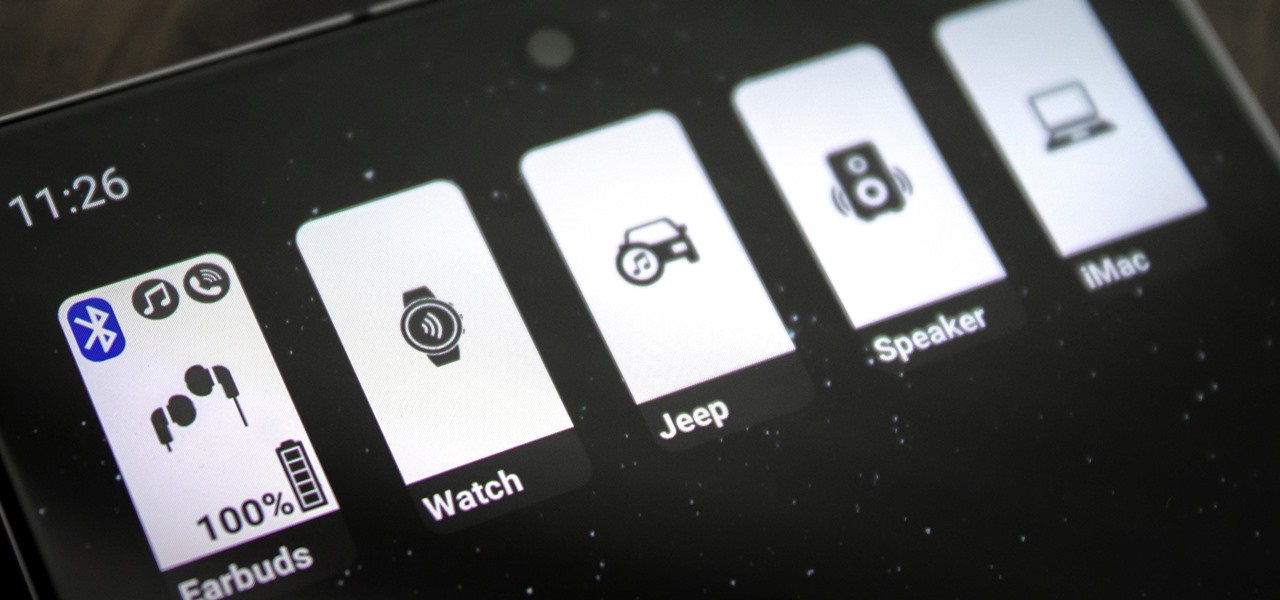
Back in Android 9, Google took away the expanding mini-menu for Bluetooth connections. The way it used to be, you could long-press the Bluetooth toggle in your Quick Settings, then the panel would turn into a fast-access menu for Bluetooth settings. It was a fairly minor feature, but dropping it has made it a lot harder to switch between your various Bluetooth accessories.
Most of you probably hate ads on your smartphone, but they're a part of modern digital life. As long as apps like Instagram are free to use, then we'll need to pay by dealing with posts, videos, and pop-ups trying to sell us stuff. Well, not necessarily, so long as you're OK with a few compromises.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

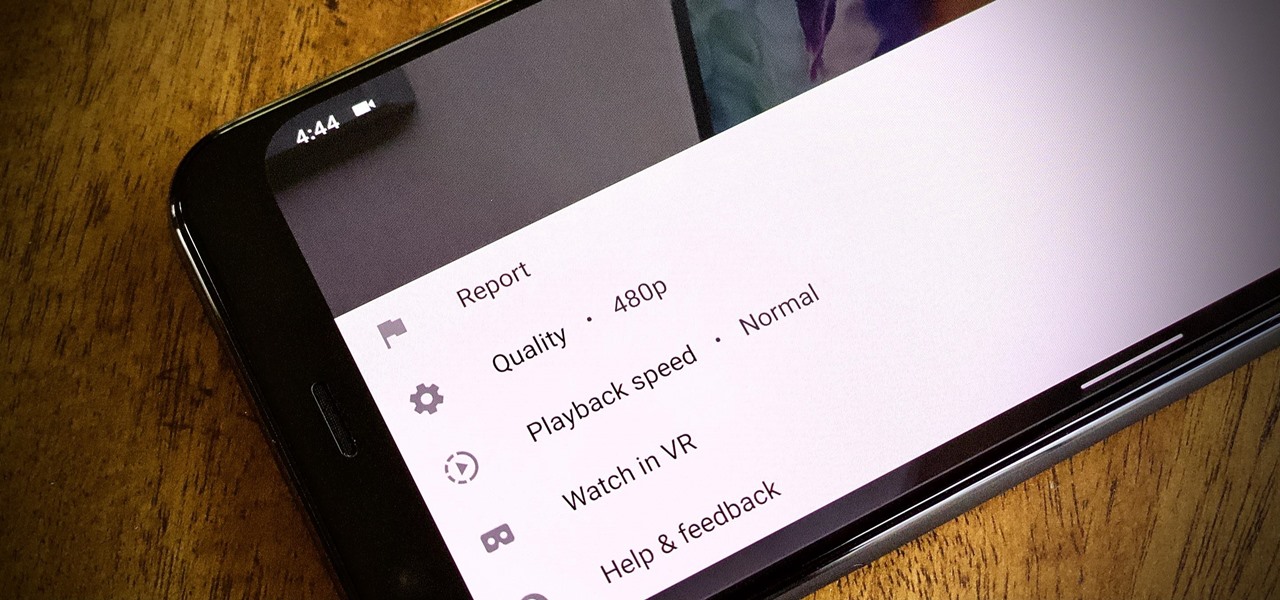
To reduce stress on internet bandwidth during the COVID-19 pandemic that the novel coronavirus is causing, Google decided to set YouTube's default video quality to 480p. That said, even when you could stream at HD quality without adjusting anything, you still couldn't switch the default to whatever you liked. We have a few methods on hand to help you change that.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

The landscape of podcasting has exploded in recent years, with everyone from dedicated longtime podcasters reaching the mainstream spotlight, to traditional media personalities moving from TV, radio, and newspapers to grab a slice of the listening pie. The good news is that the barrier to entry is relatively low, so even if you're not a celebrity or media luminary, you can still get your voice out there by starting a podcast.

We've been predicting the rush of augmented reality wearable makers from China for a couple of years, and now it looks like it's in full swing, with one of the most promising entrants coming from startup Pacific Future.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Despite their awkward appearance, Apple's AirPods have become the earbuds of choice for working out, largely thanks to quality audio without any wires to tangle. However, at $159 to start, they aren't exactly for everyone.

Did Google CEO Sundar Pichai kill Google Glass for non-enterprise users? That's the obvious first question following news that non-enterprise Glass users will no longer have access to Google's core apps after February 2020.

Some people believe that art makes artists immortal, and now one of the best known performance artists on the planet is working on taking that immortality into the realm of augmented reality.

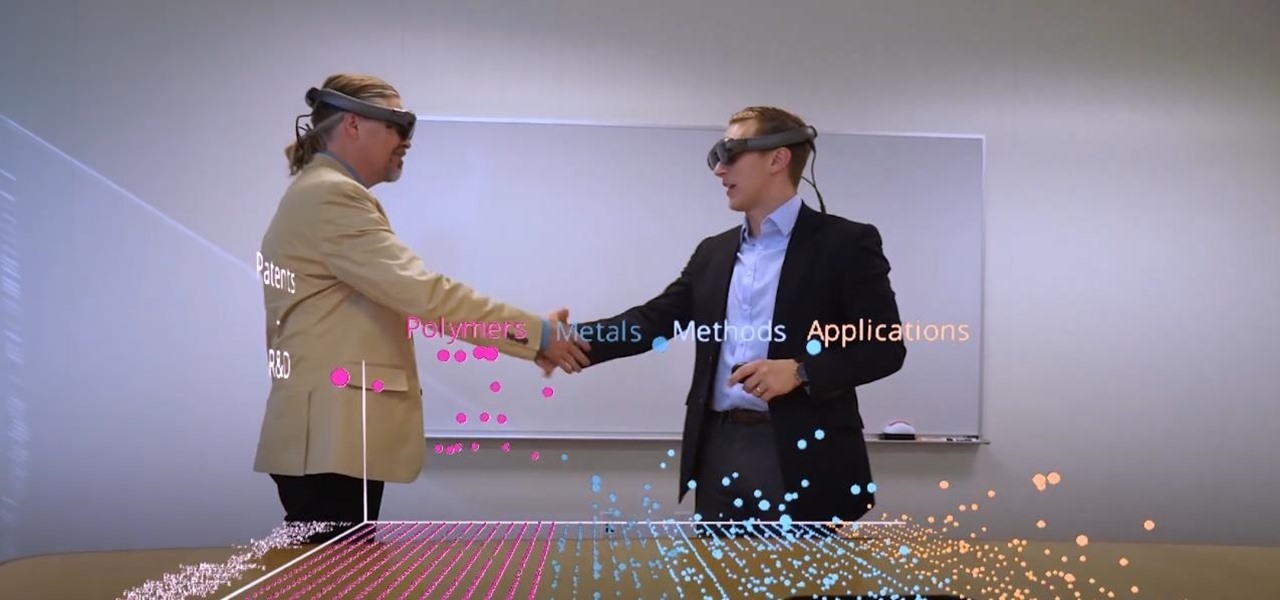
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing.

We have seen Kickstarter-launched wearables before, but this one is particularly unique and may even have you blinking a bit in wonder when you see how it functions.

There have been enough music artists releasing Snapchat AR experiences over the past week to fill a small festival. Count them with me: Bruno Mars. Gucci Mane. Kodak Black. Missy Elliot. Imagine Dragons. Panic! At the Disco.

The augmented reality space is brutal, and that means shifting directions quickly to meet whatever need the market demands.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

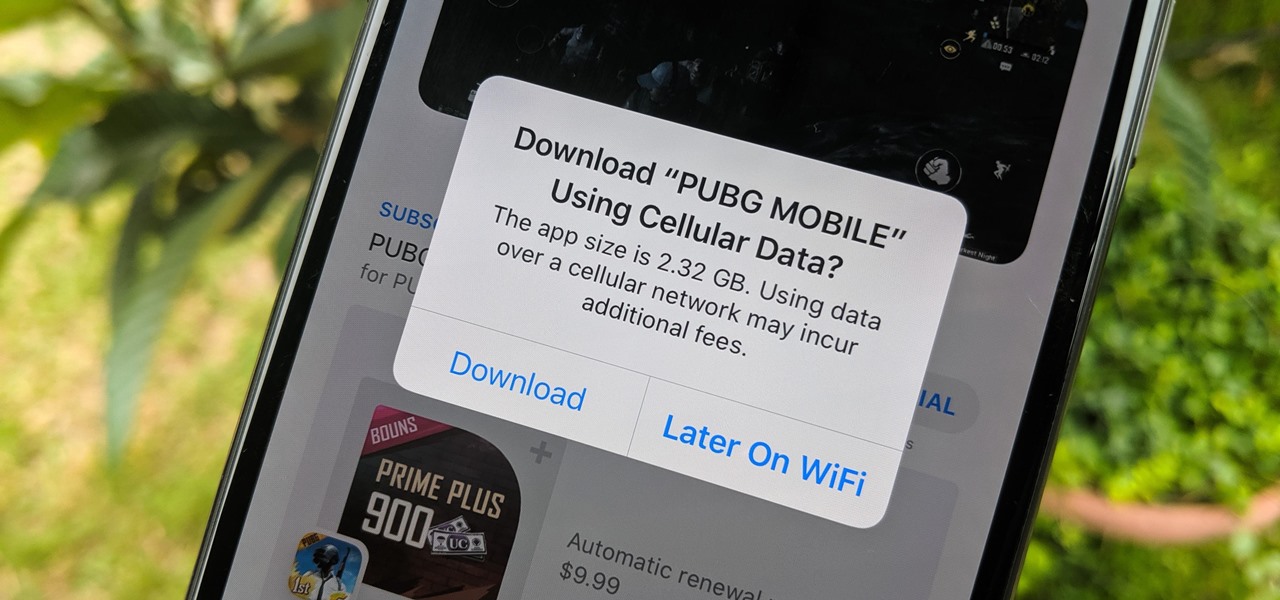
When there's a new game you want to play or app you need to use, but a Wi-Fi network isn't available, you can always download it over cellular data. If the size of the app is too large, however, you may not be able to on your iPhone. But that changes in iOS 13, which finally gives control over cellular data downloads in the App Store.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

If waveguide display maker DigiLens has its way, enterprise businesses and consumers will soon be able to purchase smartglasses for less than $500 — as long as they can supply their own computing and battery power.

With the rapid demise of the 3.5 mm headphone jack, Bluetooth is fast becoming our best option for universal audio. The problem is, with over a decade of it being a standard component, many of us still own a reliable pair of wired headphones that we don't want to gather dust. Well with one tool, you can have your cake and eat it, too.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

On Thursday, Mojo Vision, a startup comprised of former engineers from Apple, Amazon, Google, and other Silicon Valley mainstays, emerged from stealth backed by $50 million in funding for a hands-free augmented reality platform that runs without smartphones, tablets, or other devices.

While many retailers have introduced try-before-you-buy features in their apps, Walmart has gone in another direction by bringing shoppers an augmented reality tool to help them compare products they want to buy.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

The Daily Prophet, the enchanted newspaper from Harry Potter lore, is no longer the sole source for magical moving printed photos.

We've spent years waiting to see what all the secretive fuss was about, and now that the device is in our hands, we can finally begin showing you images of what the Magic Leap One experience looks like.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

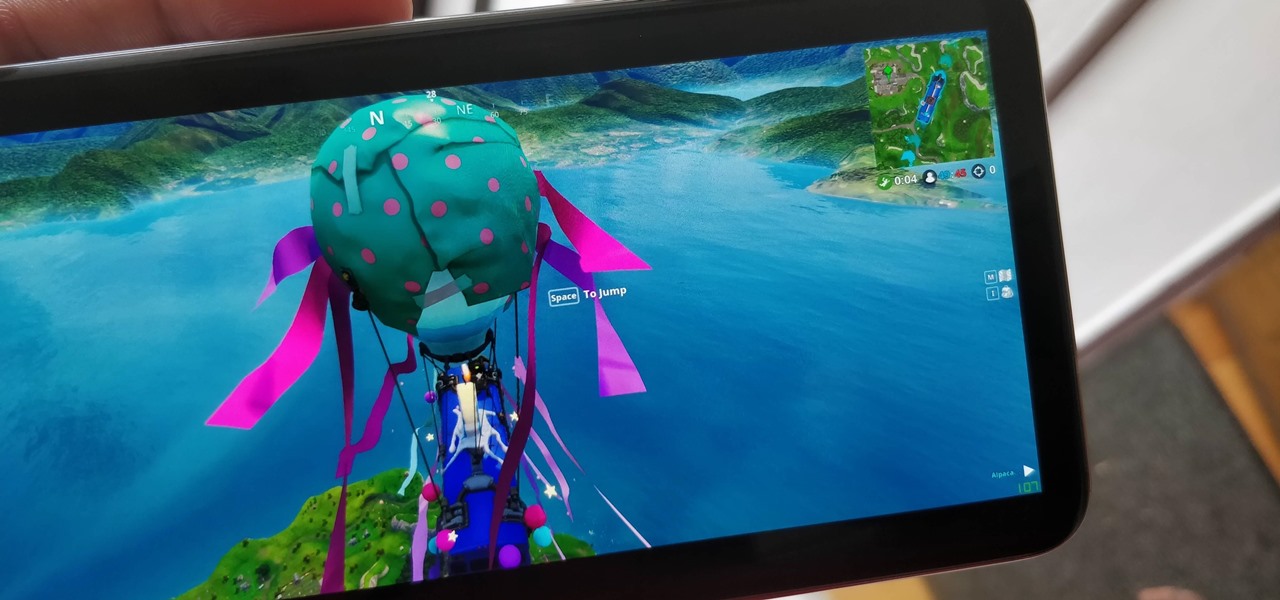
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.