This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

Connecting your devices with a cable is the fastest and most reliable way to transfer files between them. Now that most Android devices have either USB Type-C or a Micro-USB port that supports USB OTG, phones are capable of importing media files directly from a camera using a simple (and cheap) adapter.
Way back, life on the range was tough and unforgiving for a HoloLens developer. Air-tap training was cutting edge and actions to move holograms not called "TapToPlace" were exotic and greeted with skepticism. The year was 2016, and developers had to deploy to their devices to test things as simple as gauging a cube's size in real space. Minutes to hours a week were lost to staring at Visual Studio's blue progress bar.
Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone.

Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?)

Augmented reality could come in very handy for those of us prone to losing things—namely, our wallets. Pixie Technology, a company from Los Altos, California, has developed a way to locate your lost wallet and keys using AR technology and tracking chips, a platform they call the "Location of Things."

Facebook is aware that Snapchat is killing the social media game amongst the youths, which makes sense, because in 2017, video is king in social media currency. Facebook has continually shown that Mark Zuckerberg and crew seem to think the best strategy to keep up is to simply copy them.

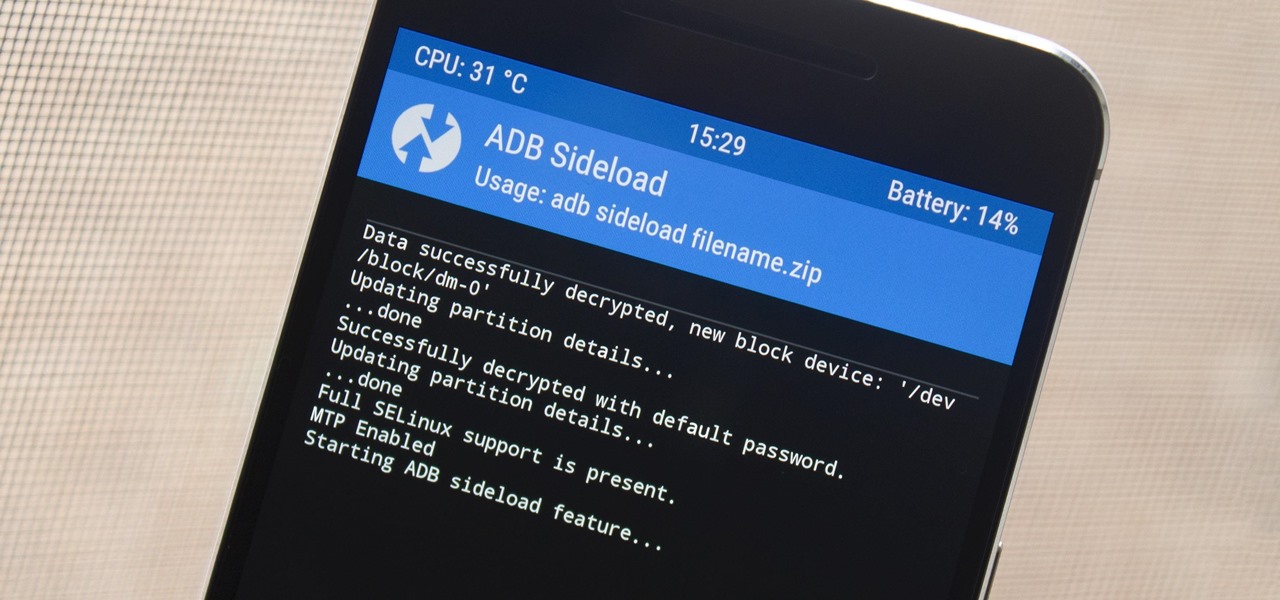
If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

Some studies have shown that vitamin D supplements help fight respiratory infections, but some haven't. A new study published in The BMJ clarified the confusion, and identified a group of people that might be better able to fight off colds and flu with vitamin D supplements.

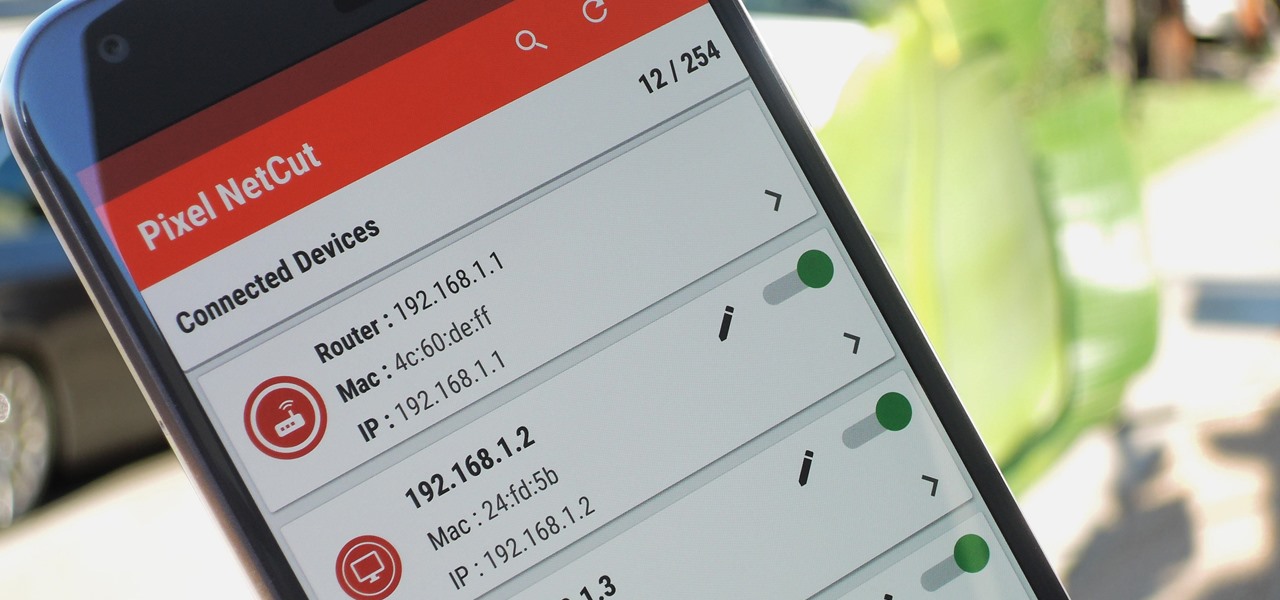
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

There's no question about it—Skype is one useful program, but has always been lacking in the mobile department. On your desktop, Skype works just fine and all of its options are available for usage. However, the same cannot be said for Android. On Android, you can't even change your status to "Away" or "Invisible."

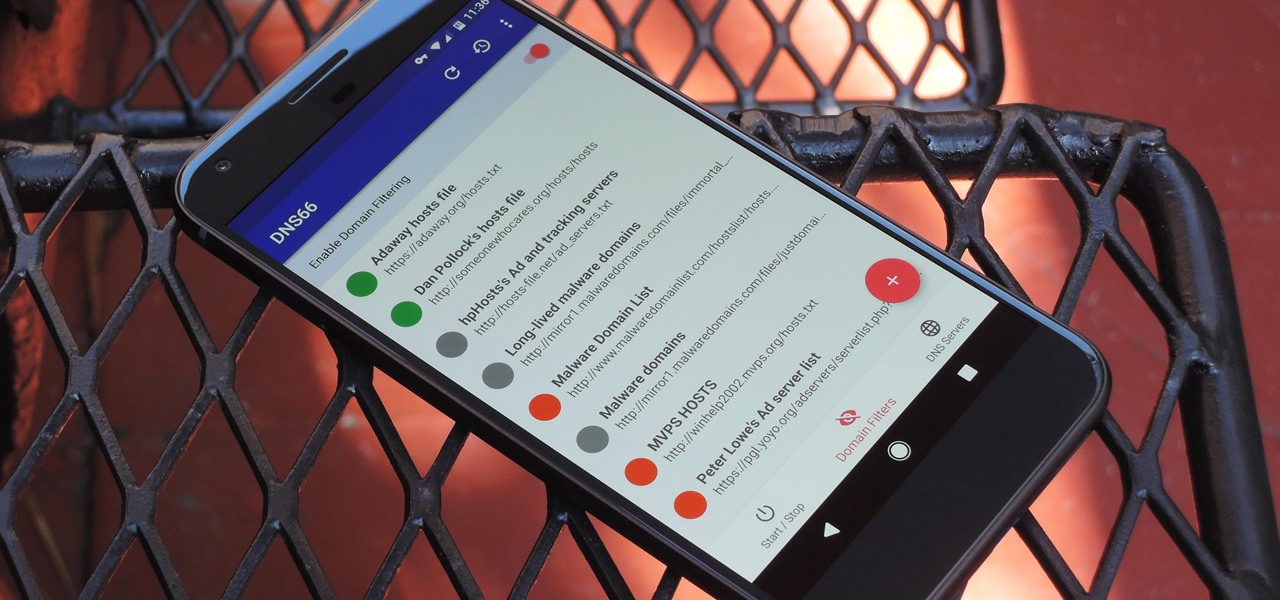
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

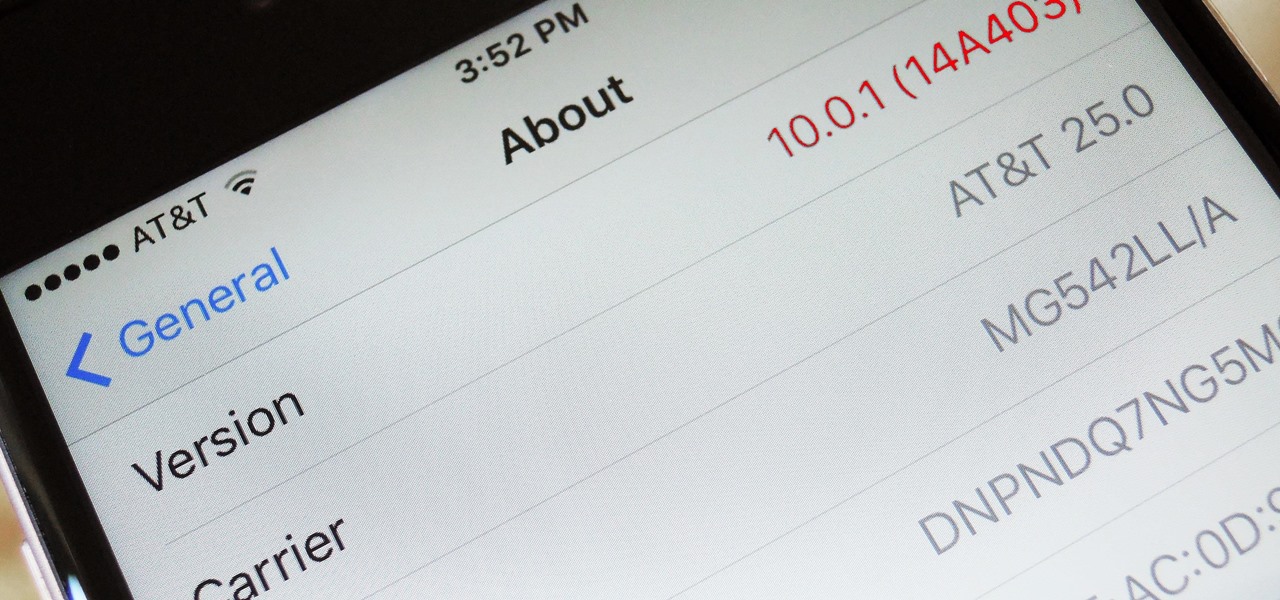
Uh oh. With millions of devices already sold, Apple's latest blunder is bound to upset the owners of some of their brand new iPhone 7 Plus phones.

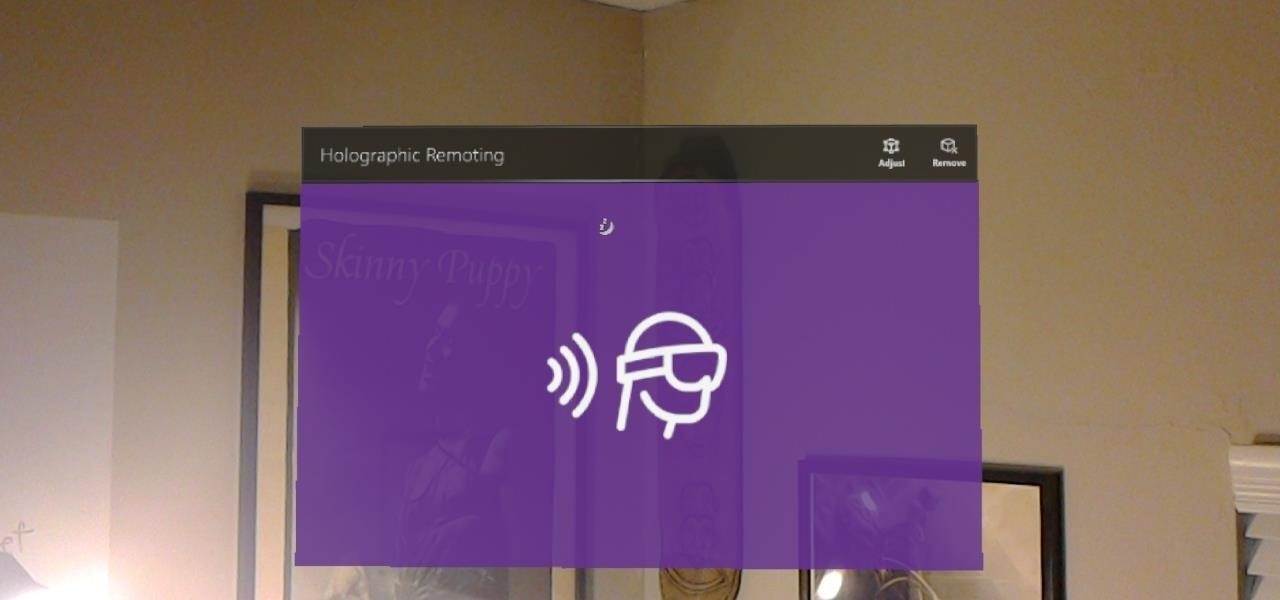
In the world of analog synthesizers, hitting a key, twisting a knob, or sliding a fader makes a beautiful musical (or not so musical) sound and can be an amazing and downright satisfying experience. Now it's about to get even more satisfying, if you add Microsoft's HoloLens into the mix as a means to twist those knobs virtually instead.

When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

From fungi to foie gras, the weird ingredient cocktail game across the nation is growing by leaps and bounds. We had our hesitations about trying some of them out, and especially about attempting to make any ourselves, so we did a bit more research and realized the flavor profiles aren't as unfathomable as one may think.

Google's new cross-platform video chat app, Duo, is finally making its debut today, following a long waiting period that began in late May. The app was heavily teased during the keynote speech at Google I/O, but was not made available for download until now, so any early hype Google managed to whip up has died down quite a bit.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

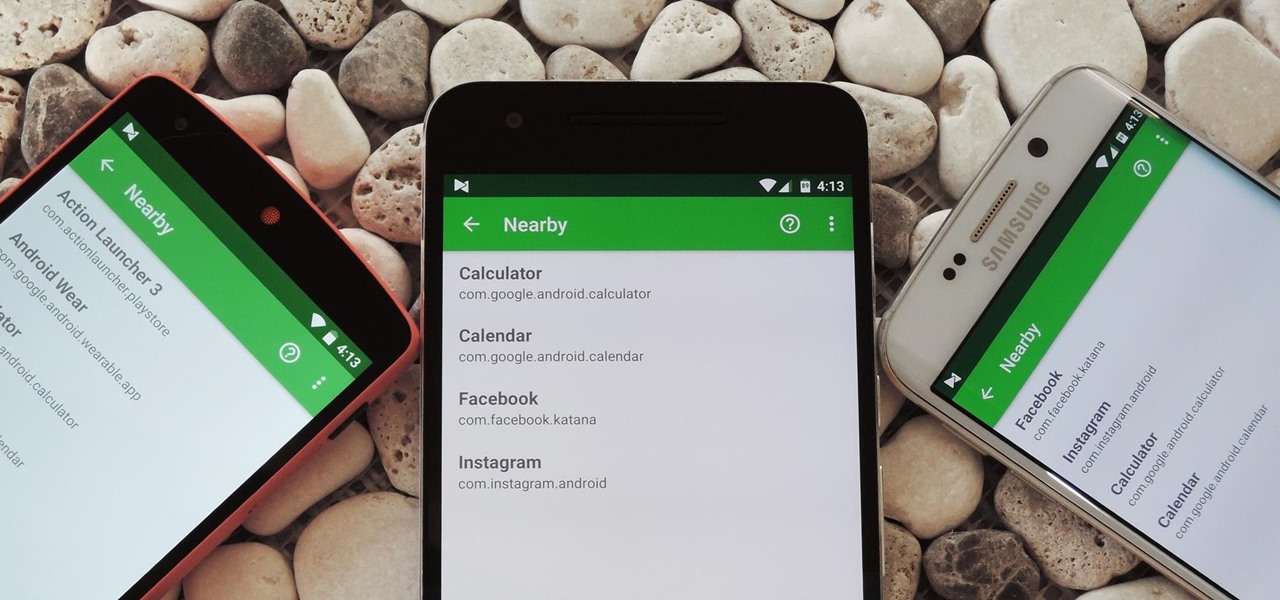
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

An accelerometer/gyro goes onto an Arduino board and transmits the angular motion of the skateboard via Bluetooth to a virtual reality game I made for Android phones and Google Cardboard.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

There are myriad wrong ways to cut an onion, a few right ways to cut an onion (including this one)... but only one ultimate way to dice onions, and that's what I'll be sharing with you today.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

The increased sophistication of smartphones and apps have allowed us the luxury to never leave our homes. Everything from coffee to food to dry cleaning can be delivered straight to your door without ever leaving your couch, which can can be a godsend during the winter months when you'd rather not risk leaving your warm bed. But during the summer, you gotta ditch the comforter and go enjoy outdoors.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.