Social media is constantly evolving, and as a result, we're now capable of sharing much more than we were even just a few years ago. Television, on the other hand, continues to hold strong as one of America's favorite pastimes.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.
Practically every kid in the '80s would rush home after school to put in some time on the first-gen Nintendo before their parents got home. Games like Super Mario Bros. and Super Smash Bros. were synonymous with fun times, and to this day, call up a wave of nostalgia amongst Generation-Xers.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.
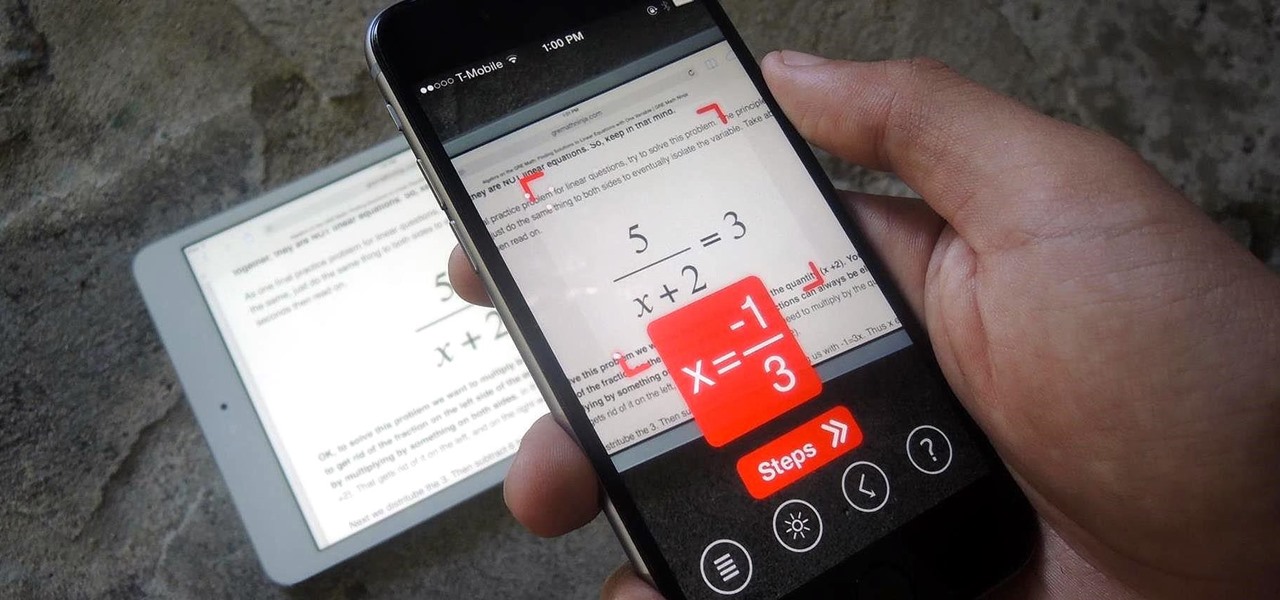
Math homework isn't the easiest thing to get through quickly, no matter how prepared you are. Knowing your stuff simply won't cut it. Going through dozens of equations in one sitting could take up hours of your time. Even when you finish, there's always going to be that one problem you couldn't solve, which could take hours itself to finally get right.

Whether if it's to play games or watch Netflix or YouTube, children love using our smartphones and tablets. As an uncle of many, I don't mind my nieces and nephews using my gear, but I do mind them opening apps they have no business being in, like my photo gallery or messaging app.

Without much notice, Spotify launched Desktop Open Beta a few weeks ago, a program that allows anyone to download, test out, and provide feedback on the latest beta version of their desktop application for Mac and Windows.

Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.

The Galaxy S5's camera is amongst the most capable smartphone shooters on the market. With a 16-megapixel sensor that is capable of recording 1080p video at 120 frames per second, the stat sheet was officially stuffed when Samsung brought this device to market.

With hundreds of pictures accumulating on my device, it's a daunting task to devote time to sorting through which are worth keeping and which I should discard. Not all of the images on my device are winners, so the losers not only take up space, they make it difficult to find the good ones as I wade through the crap.

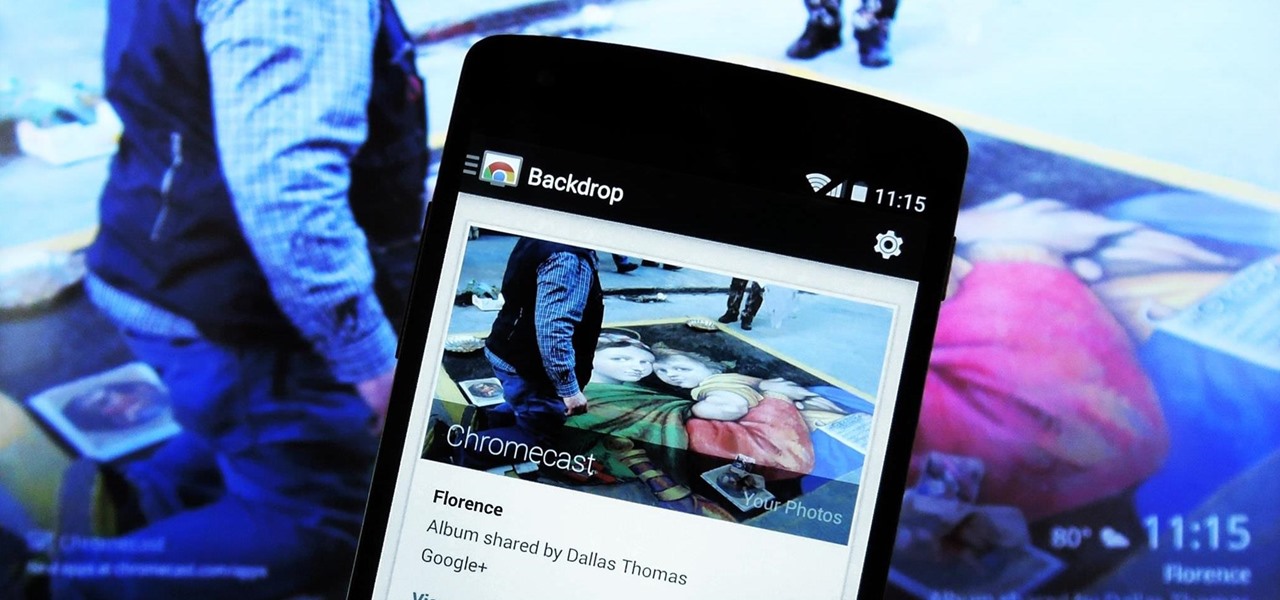
It's been a long-awaited feature since being announced at Google I/O in June, but Backdrop for Chromecast has finally started rolling out. With an update to the Chromecast app for Android and iOS, users will be able to personalize the background images that appear when Chromecast is idle.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

How many times have you witnessed a beautiful moment that you would have loved to capture on film, only to watch it slip away as you struggled to unlock your phone and open your camera app?

In the past few weeks, the internet has been abuzz with nightmarish horror stories of Comcast's questionable decision-making and downright terrible customer service. The central theme of many of these disputes with the nation's largest cable provider is that without evidence, the conglomerate will refuse to acknowledge its mistake and place the burden of proof on the customer.

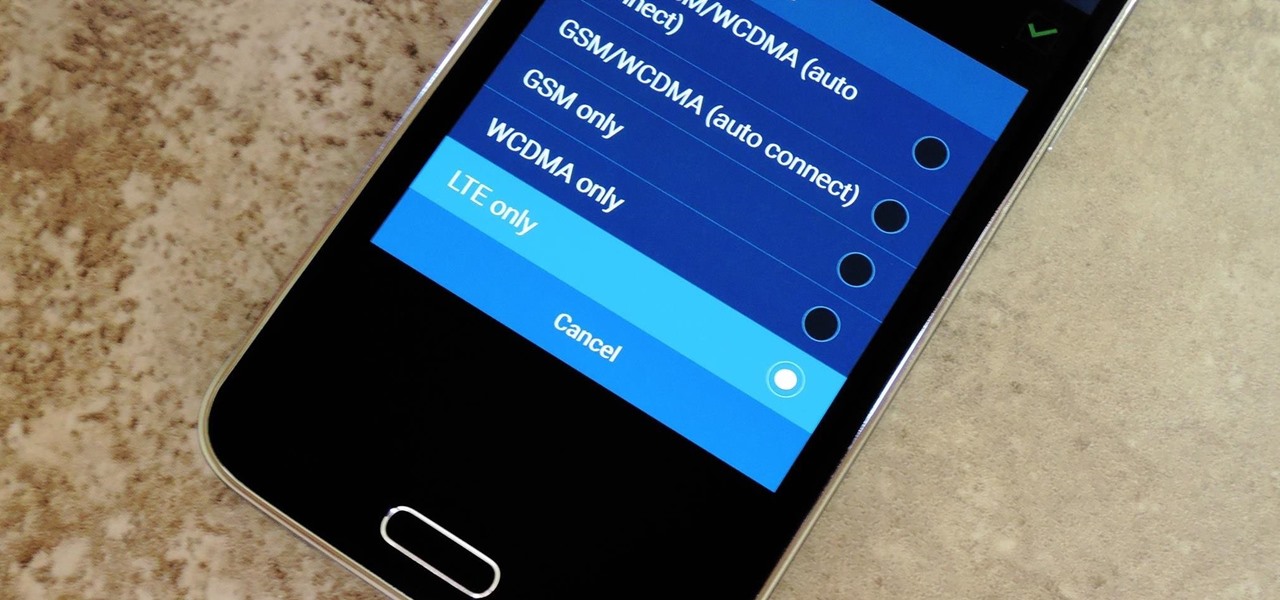
Even with the highest-tiered data plan available, there are times that your phone or your carrier might downgrade your connection to 3G or even lower. This usually occurs when you've made a phone call, or you've switched cell towers while traveling.

Apps that save your passwords have been around for quite a long while. But apps that complete the entire login process automatically? Now that's a different story.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Stock Android has come with lock screen widget support for a couple of years now, ever since the days of the first Ice Cream Sandwich build. But for some reason, Samsung decided to remove this feature in the Galaxy S5.

Want to learn how to make Peppa Pig with Play-Doh? Here is our attempt on showcasing a tutorial on how to make Peppa Pig with Play-Doh.

While their merger with Microsoft has lead to a seemingly complete halt of new device development, some Nokia employees are still hard at work to bring new software to the table.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Whether it's bad timing, or some trying-to-be-funny photobomber, it sucks having a photo ruined by someone or something getting in the way. While you can always retake the photo, it's simply impossible to capture the moment you intended, no matter how much restaging you do. But with an HTC One, there's no need to retake anything, as we have access to built-in features that will remove those photo intruders.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

Notifications, while certainly helpful, can at times be overbearing. There are banners plastered every which way on your smartphone for almost every application. While many of the notifications can simply be swept away or turned off, the same can't be said of persistent notifications.

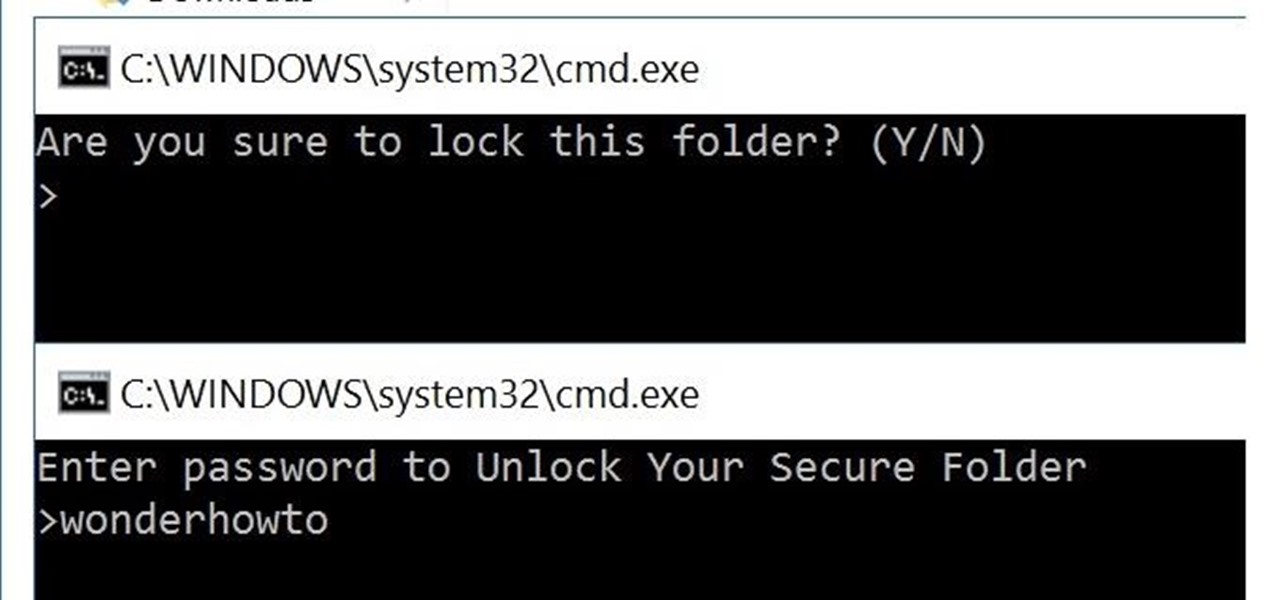
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

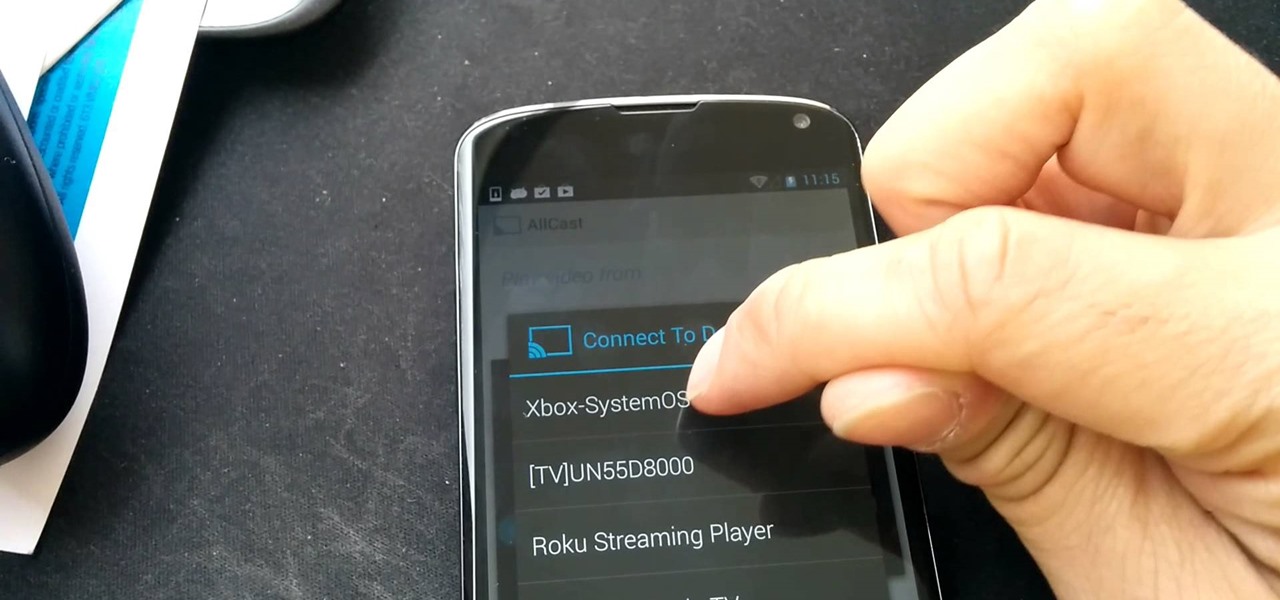
Seriously?! That's what a lot of people are saying when they found out that their Xbox One doesn't have a native streaming media player. When a new system is introduced and lacks features that the previous system had, it really pisses people off. The Xbox 360 allowed people to stream music and video files from a flash drive, as long as it was formatted with the Windows FAT32 file system.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

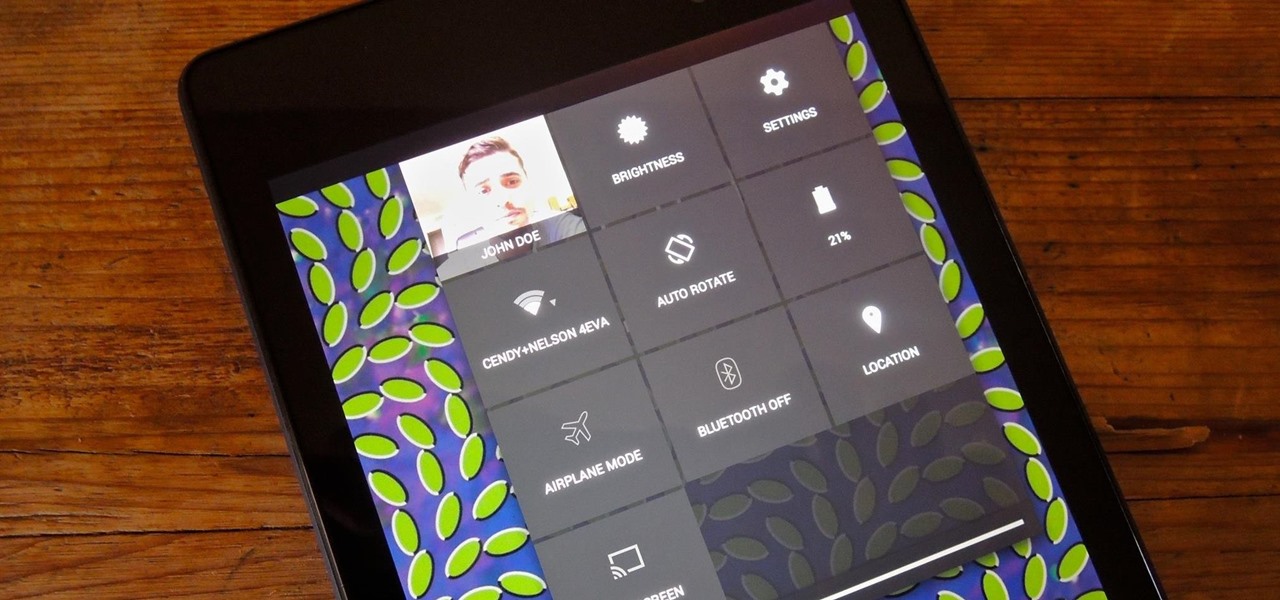
A great aspect of using Android is having the ability to change and tweak aspects of the user experience to your liking. You can easily change things like home screens, widgets, and icons on your Nexus 7 tablet, but also core system settings if you want, like volume settings. Most stock systems come standard with a "15 step" volume control. That means simply that you have 15 levels from mute to the loudest volume settings. Whether your an audiophile or just someone who wants a little more con...

What is your Samsung Galaxy Note 2 running? More than likely, you're still rocking Jelly Bean 4.1.2, which is already pretty outdated. My grandma uses 4.1.2.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

There may only be a few hardware buttons on your Samsung Galaxy Note 2, but when they're not working, your phone might as well be a doorstop. A few years back, I was texting while walking to class and a student on a bicycle crashed into me. My phone was flung thirty feet—straight into a puddle. I picked it up and checked for damage, but everything seemed okay. The biker apologized profusely, but nothing was wrong, so I told him not to worry about it and proceeded to class.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

We've all been there. Your phone's either dead or barely hanging on with a few minutes of life left, and you only have a small window of time to charge it before you need to head out. Sure, you can charge it for the few minutes you have, but what's the point if your device is going to die again in several minutes?

You know that moment when you finally figure out something, but you figured it out years after you really needed it? Don't you freaking hate that?!