What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Facebook is a black hole. The constant stream of baby photos, #hashtags, BuzzFeed quiz results, and unintelligible status updates is mind-numbing. I know too much about too many people I hardly know.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

There's more to earning someone's trust than simply shaking their hand, especially if you're not particularly trustworthy. Your body language doesn't reveal your thoughts, it reveals your intentions, and sometimes intentions are better left unrevealed. Psychopaths, take note...

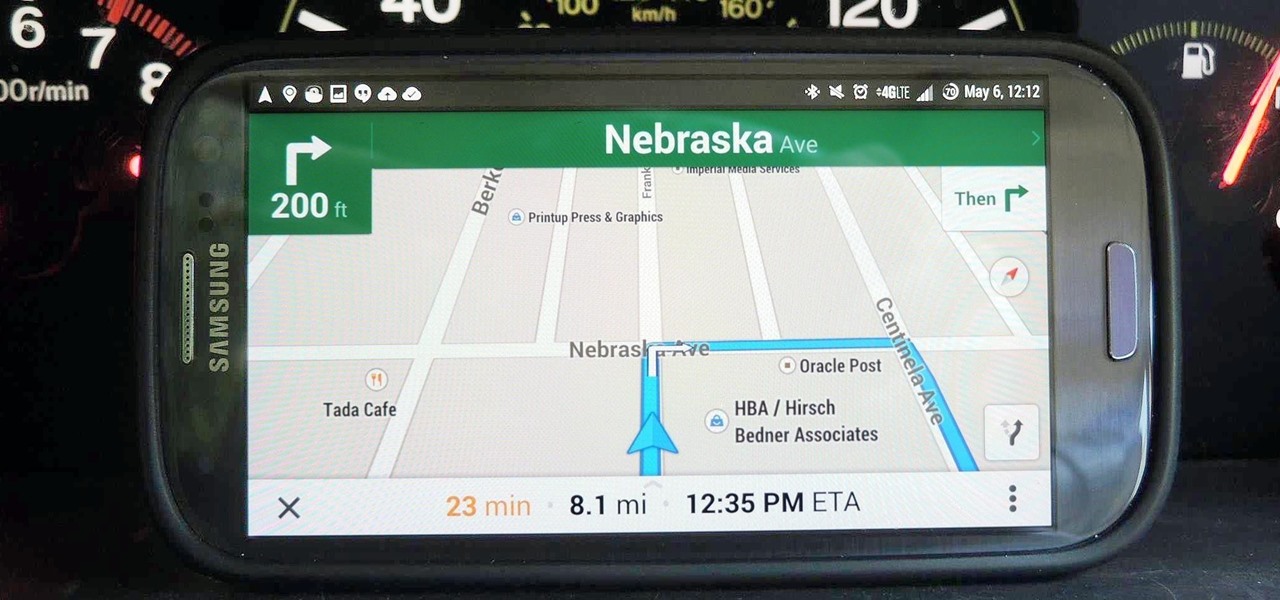
This week, Google sidestepped their usual "Update Wednesday" strategy by dropping a huge update to their Maps app for both Android and iOS. We're accustomed to seeing new features and bug fixes to their stable of apps on Wednesdays, but today's Maps update was presumably big enough to get its own release day (it's Tuesday, folks).

I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

The Galaxy S5 is a flagship-level device with some pretty advanced features, like its 4K video recording capability, water-resistant casing, fingerprint sensor, and KitKat running out of the gate.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Out of the box, your Android device can be customized in many different ways, and a ton more with root access, but adjusting the actual interface of the system is a little bit more challenging. Changing the status bar size, icon width/length, and positioning of toast notifications are things that require a little bit more know-how—until now.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

Update: May 7, 2014: Google's Camera has seen its first update, with a small yet important addition baked into the app—the ability to take pictures while recording a video. Now, when in video mode, simply tap on the screen to take a picture, while your recording continues as normal. The update to version 2.1.042 is set to hit today, but if you haven't yet received it, apply it manually by downloading the apk here.

The list of streaming services is pretty vast, from HBO GO to Hulu to Netflix, these subscription-based services have never been so popular, and have never been easier to watch now that they have Chromecast support.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Last week, we covered a new, open-source live wallpaper (LWP) called Muzei, and less than a week later we have no less than twenty beautiful add-on extensions to the app.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

Texting can be difficult sometimes. When you're browsing the web or playing a game on your iPhone and need to respond to text message real quick, you have to exit your current app to do so. Not exactly efficient, especially if a quick "K" is all you need to say.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Like the buttons on your computer's mouse and keyboard, the Home key on your Samsung Galaxy S4 serves a vital function in navigating through your device. It can get pressed dozens of times a day, going through hours of use and abuse.

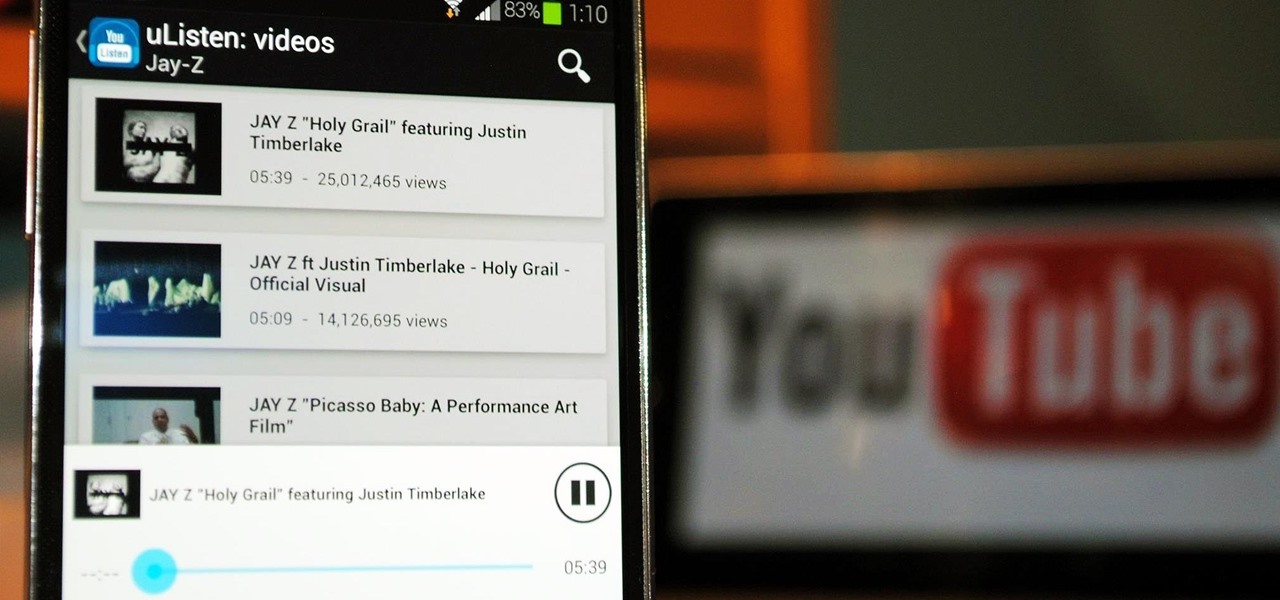
YouTube may have started out as a video-sharing site, but these days a lot of people use it as a source for music. When I'm browsing the internet on my desktop, I usually have a YouTube tab open in the background playing some music.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

The Nexus 7 is a huge jump in screen size when coming from a phone, but obviously this tablet is still smaller than some of the major players such as the Nexus 10, Galaxy Tab, etc. One way to squeeze out a little more space is to eliminate the navigation and status bars.

Walking into a bar or crowded dinner party can be intimidating. Being surrounded by a bunch of people you're unfamiliar with or trying to impress the smokeshow at the bar is no easy task...for most of us.

Customization is one of Android's popular selling points, and going hand-in-hand with that is being able to set default apps for different actions. Whether you want to play a song, navigate somewhere, or send a text, you can set a go-to app for each of those tasks.

If you've had the pleasure of owning both an iOS and Android device, you may have noticed one subtle difference on each one's PIN unlock screen. Android's lock screen requires you to press "OK" after entering the PIN, whereas iOS's simply unlocks the screen right after the last digit.

Russians are well known for their knack at documenting exciting and horribly beautiful events on the go, from insane car accidents to attempted insurance fraud and even a superbolide meteor streaking across the sky.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

The stock Android app icons that come with your Samsung Galaxy S4 can vary wildly in shape and size, as they will with any out-of-the-box Android device.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

As mentioned before, the Home button is one of the most important keys on your Samsung Galaxy S3, and pretty much all Android devices for that matter. However, when it comes to customization, it's rather tame.