"Enter your email address. Confirm your email address." I absolutely hate seeing those two sentences when I'm signing up for something online, especially on my Samsung Galaxy S3. The less keyboard work I have to do on my mobile the better. Luckily, there is a way to enter your email address without having to type it all out, and I'm going to show you how it's done.

Change is something everyone needs every now and then. President Obama used it as his campaign slogan and adult movie stars use it to hide their real identifies. Change is in itself versatile. You never want to have the same thing day in and day out, and that's why us Android users appreciate the massive amount of customization available.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Don't be greedy, sharing is caring. If you have a brand new Xbox One, let some friends and family in on the action by getting a few extra controllers. You can connect up to eight controllers on one Xbox One console. Now that's a gamer party waiting to happen.

The infamous Red Ring of Death plagued the Xbox 360 for years, leading people like me over to the PlayStation 3 console. Now it looks like Sony and its new PlayStation 4 are running into the same problems as Microsoft did.

It has been 7 long years since the PlayStation 3 was released, which makes it no surprise that over 1 million gamers purchased the new PlayStation 4 this weekend.

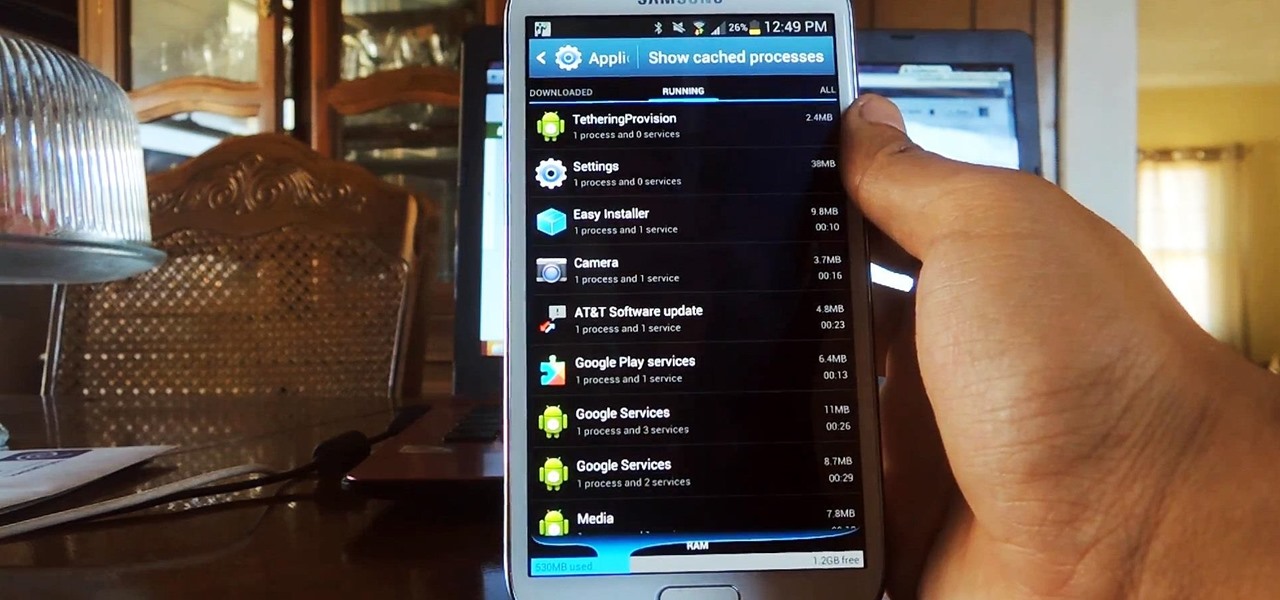
A certain selection of applications on your Android device (both system and downloaded) start running as soon as your Samsung Galaxy Note 2 turns on, laboriously hammering away at whatever tasks they have to do.

Phone interruptions are commonplace, as is evident by my historically epic missed phone call list, ranging from annoying sales people to my mom checking in every five minutes to see if I'm still alive.

Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by the week.

Most smartphone manufacturers focus on megapixels when it comes to cameras, but HTC took a different direction with the HTC One. Instead of trying to compete with the 13MP camera on the Samsung Galaxy S4, or the 20MP camera on the Sony Xperia Z1, or even the newer iPhone's 8MP, they decided on a simple 4MP camera. At first, you might think that 4MP is terrible, but not so fast. There are many advantages to your HTC One's camera that other phones just don't have.

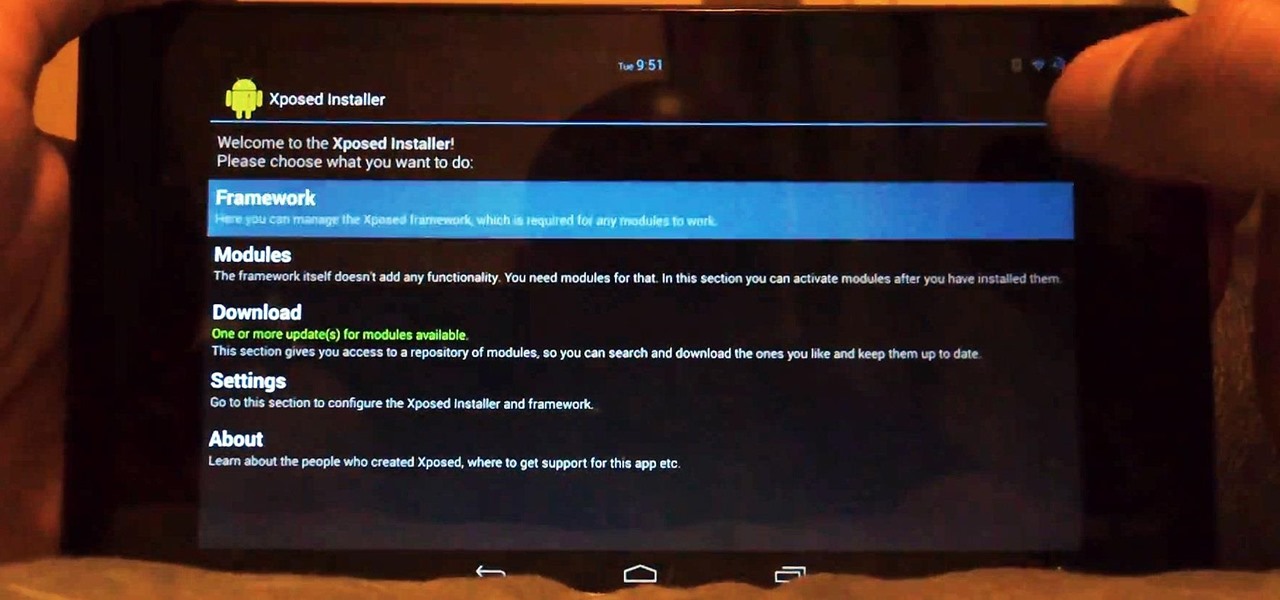
Xposed, by XDA developer rovo89, is a framework for your Samsung Galaxy S4 (or other Android device) that lets you add tweaks and customizations to your ROM (either stock or custom) without any real hassle.

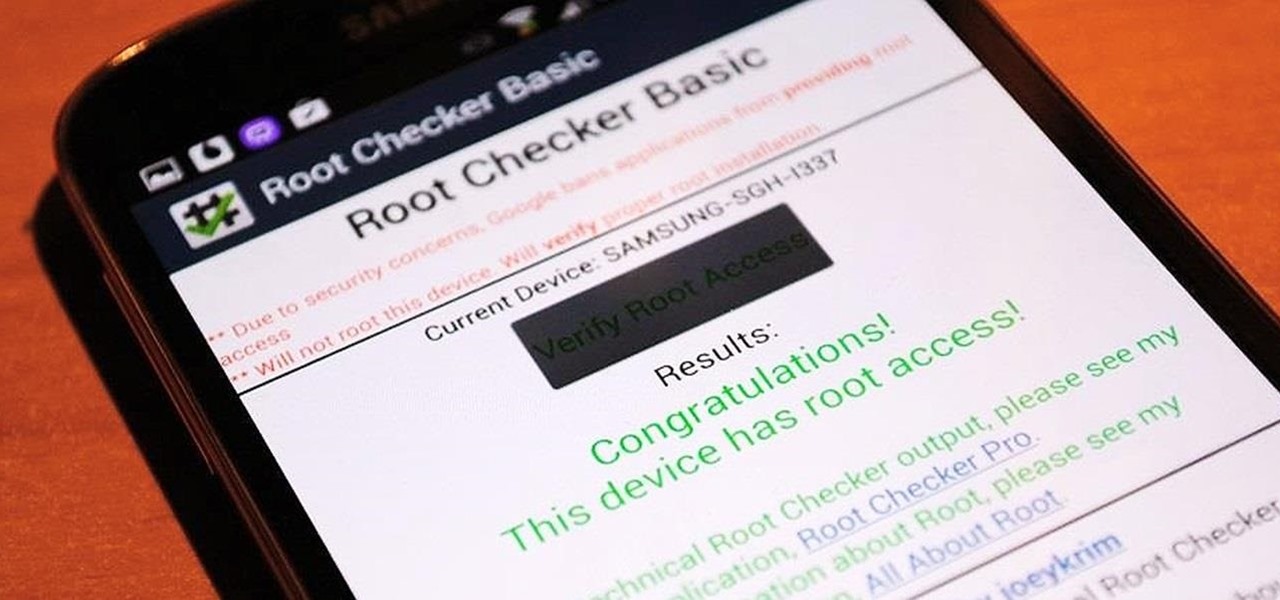
Rooting is usually the first thing on the to-do list whenever one of us softModders gets a new Android device. Unfortunately our efforts are sometimes hindered by certain obstacles; a common one is a locked bootloader.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

The high limit thermostat can be found in gas and electric dryers and serves as a safety feature that helps to prevent the dryer from becoming too hot when it’s running. The thermostat is designed to shut off power to the dryer’s heater when the dryer vent is blocked or clogged. The high limit thermostat on your dryer is something that does need to be replaced from time to time. Fortunately, it is a job that you can do on your own with basic tools.

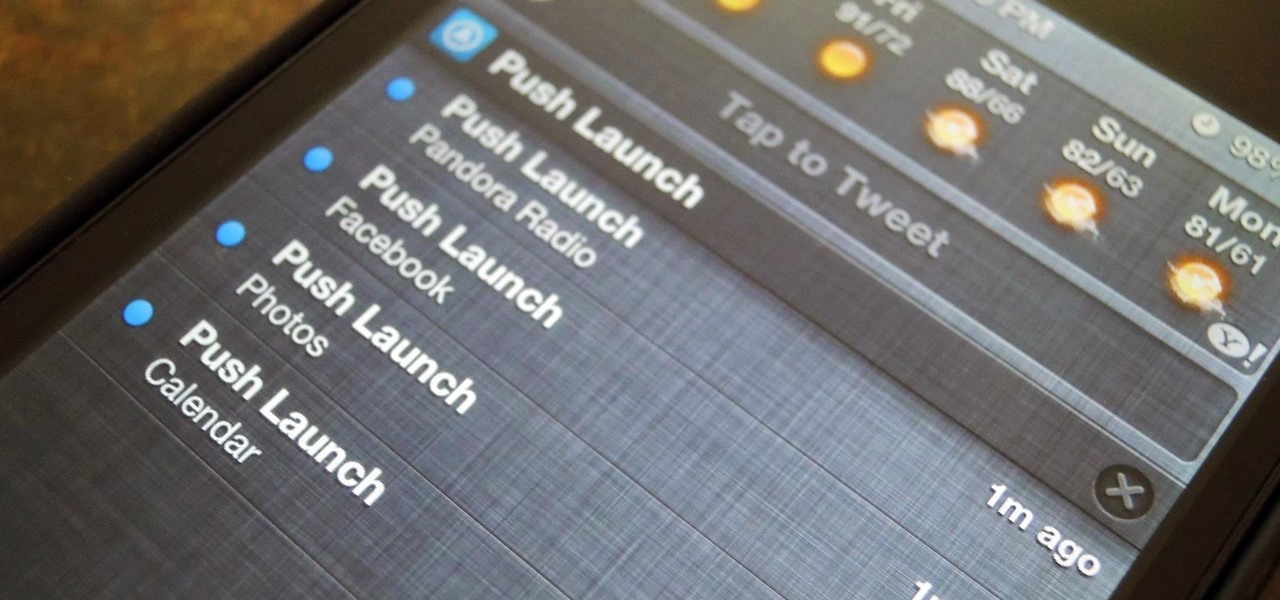
The shortest distance between two points is a straight line, but the shortest way to launch an app on an iPhone can be a much more complicated process.

For someone used to the old-style HTC Sense, upgrading to an HTC One with Sense 5 is a pretty intuitive experience, but there's one thing that some users find obtrusively different. Blinkfeed, an app which aggregates newsworthy articles from various sources and pins them in a scrolling feed on your home screen. If you don't like staying current on news, or don't like how much RAM it eats up, you probably want to get rid of it. There's been some questions about removing Blinkfeed in our forum,...

With CyanogenMod 10.2 recently released and the Samsung Galaxy S4 still waiting on Android 4.3, it only makes sense that the coveted features from both firmwares are highly desired by Android owners all over. We've already brought you a feature from each firmware—the cLock home/lock screen widget from CyanogenMod and the Google Play Edition Camera and Gallery from Android 4.3. Now we're bringing you another in the form of an updated text messaging application, ported from both Android 4.3 and...

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

Probably the most favorite custom ROM among softModders is CyanogenMod, a theme-friendly take on stock Android that not only makes it easier to customize your device, but also increases performance using a variety of system tweaks and enhancements.

The new Moto X may not have a lot going for it when it comes to hardware, but there are some pretty cool software features that makes it a tempting device. One of these cool features is its Active Display notifications that appear on the lock screen.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

I'm constantly browsing the web, taking pictures, and playing games on my Samsung Galaxy Note 2, but there's one thing that I'm always doing—playing music. No matter what I'm doing on my smartphone, I'm always playing my music in the background at the same time.

I've already showed you how to magically unlock your Samsung Galaxy S3 with the simple wave of a hand, but why stop there? Sure, you could go out and purchase a Samsung Galaxy S4 so you have Air Gestures that let you control the lock screen, SMS, sound, wireless, and more.

Due to its enormously awesome size, the Samsung Galaxy Note 2 usually takes two hands to maneuver through photos and texts, write emails, and get directions on the map.

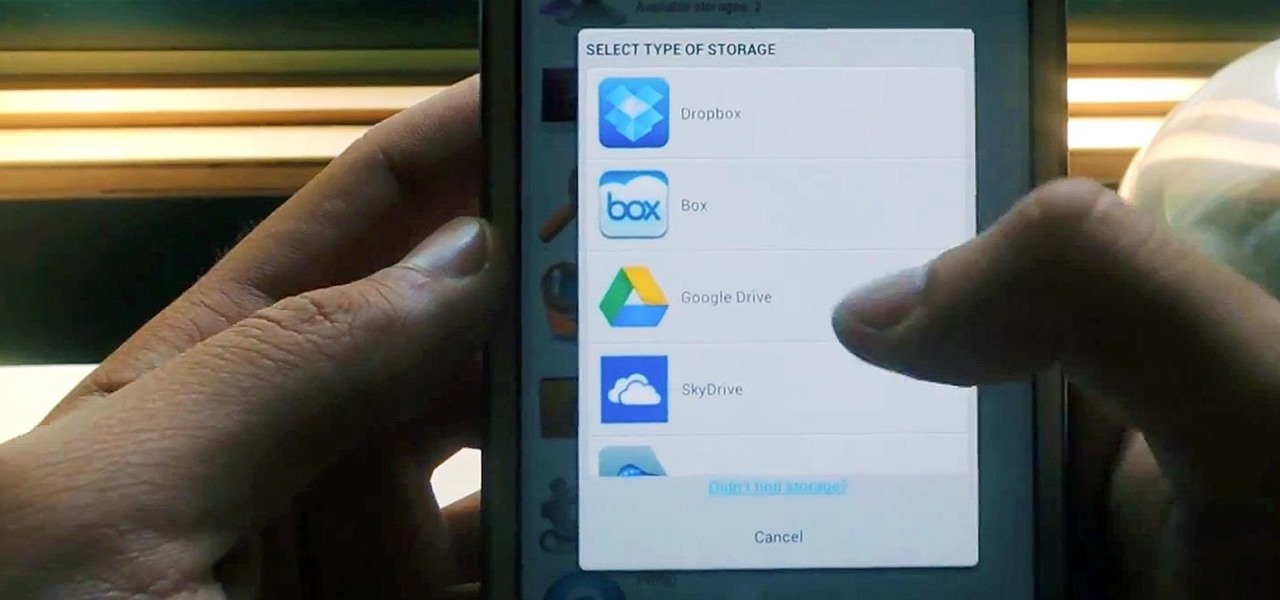
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

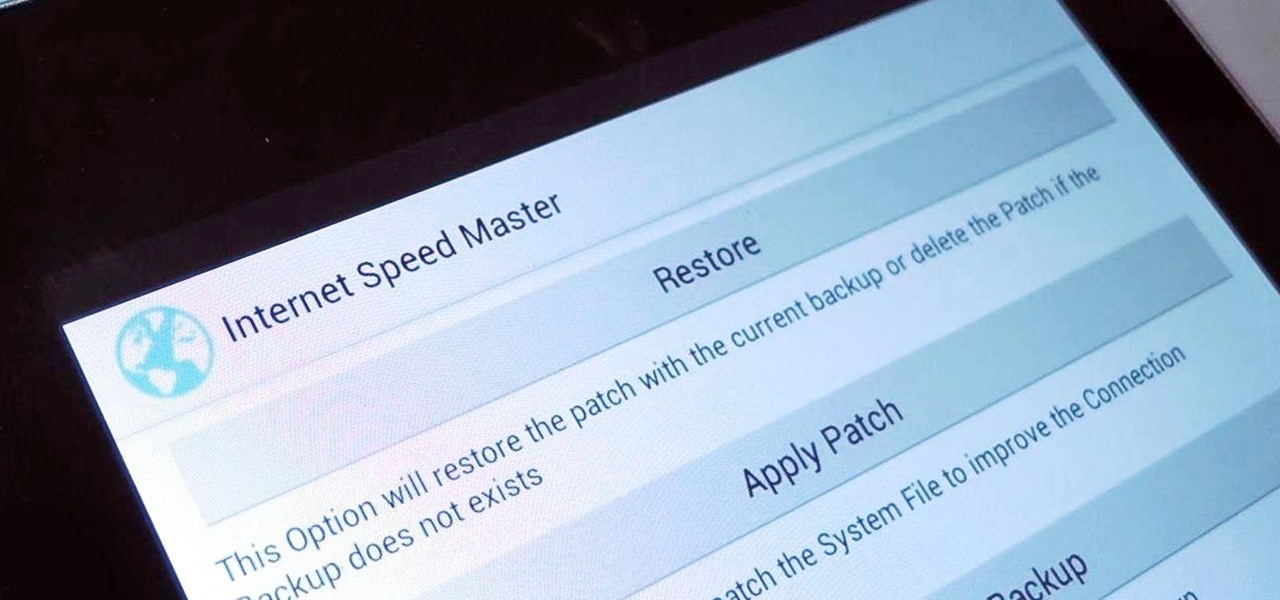
Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

Hey dolls! I have to share the secret of Copper peptides with you all. I don't know why it's taken me so long to jump on this band wagon because the science and studies behind the product are amazing!

Selfies are on there way out. Not because I said so, but just because I want them to. They're both aberrant and curious. They carefully hobble between the lines of self-exploration and crippling insecurities terribly masked as blatant narcissism.

Just like the HTC One Google Play Edition, the recently released Samsung Galaxy S4 Google Play Edition ditches the manufacturer's UI in favor of a pure Google experience, i.e. AOSP, but is also optimized specifically for the device's hardware.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

Thanks to its dedicated ImageChip, the HTC One has one of the best cameras out of all the smartphones currently on the market. Their branded UltraPixel Camera can take full resolution photos while shooting video, has superior auto-focusing, and provides great overall quality for everything from low-light to action shots.

Facebook knows who all of your closest friends and family are. When you backpacked across Europe last summer, they went along on the trip. Remember that break up two years ago? Yeah, they were there. The breakfast you ate this morning? They probably have a picture of it. They're even right under your own feet.

If you're a frequent Snapchatter like myself, you're probably well aware that Snapchat can't stop you or anyone else from taking a screenshot of a photo received. Instead, they notify the sender that a screenshot was taken—a greatly appreciated fair warning when impetuous photographs are involved. However, there is a loophole to this.

If you're constantly going from dark to brightly lit areas, you've probably noticed that the stock auto brightness feature on your Samsung Galaxy Note 2 doesn't work that well. Either the screen is really dim and unreadable, or it's just way too damn bright. Sure, you can disable auto brightness, but then you have to manually adjust the brightness all of the time for that perfect comfort level. This isn't really all that bad of an option, but don't be surprised when you see this: However, the...

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

When you have to take four different freeways to go twelve miles, Google Maps becomes a very close and dear friend—especially in Los Angeles. Without my trusty Samsung Galaxy S3, I seriously don't know if I could make it back home half of the time. Of course, you'd probably get better directions using a Garmin, TomTom, or other GPS device, but when you already have a smartphone like the GS3, dedicated GPS units become nothing more than a luxury item.