Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.
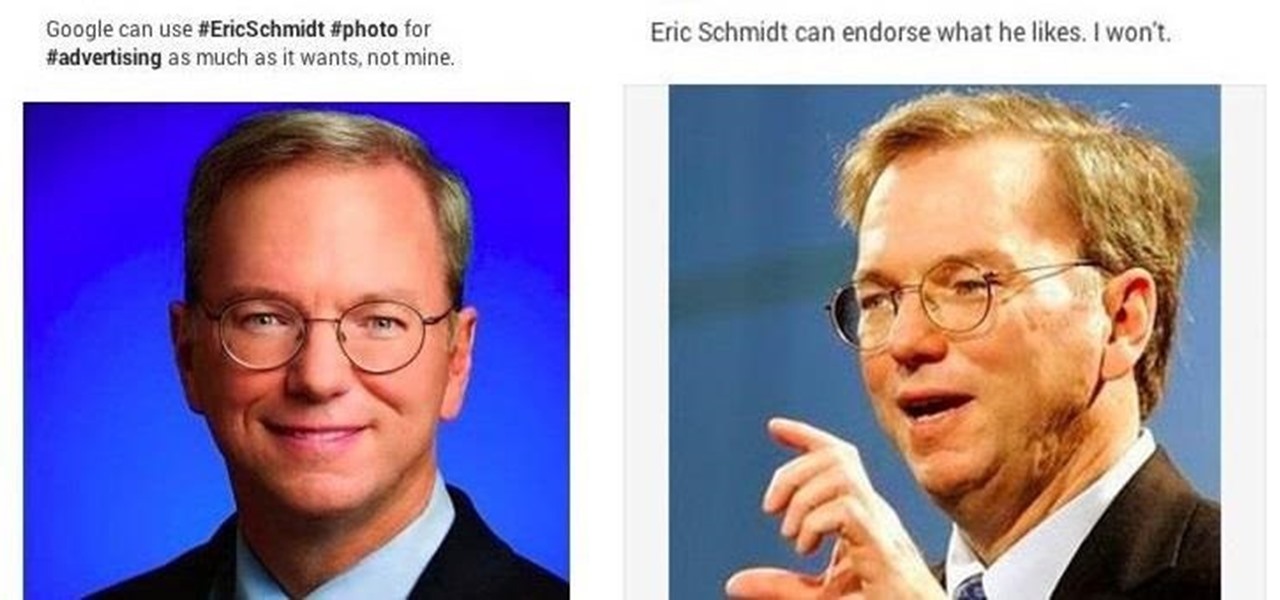
Every time you Google something or click on an ad in a YouTube video, Google gets paid. They are estimated to make well over $100 million a day, and I honestly think that's low-balling it.

Apple's line of iPhones, iPads, and iPods are of some of the most advanced devices available on the market. Usually, the biggest complaint is that they are not customizable, but they can be if you exploit a few bugs in the system.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.
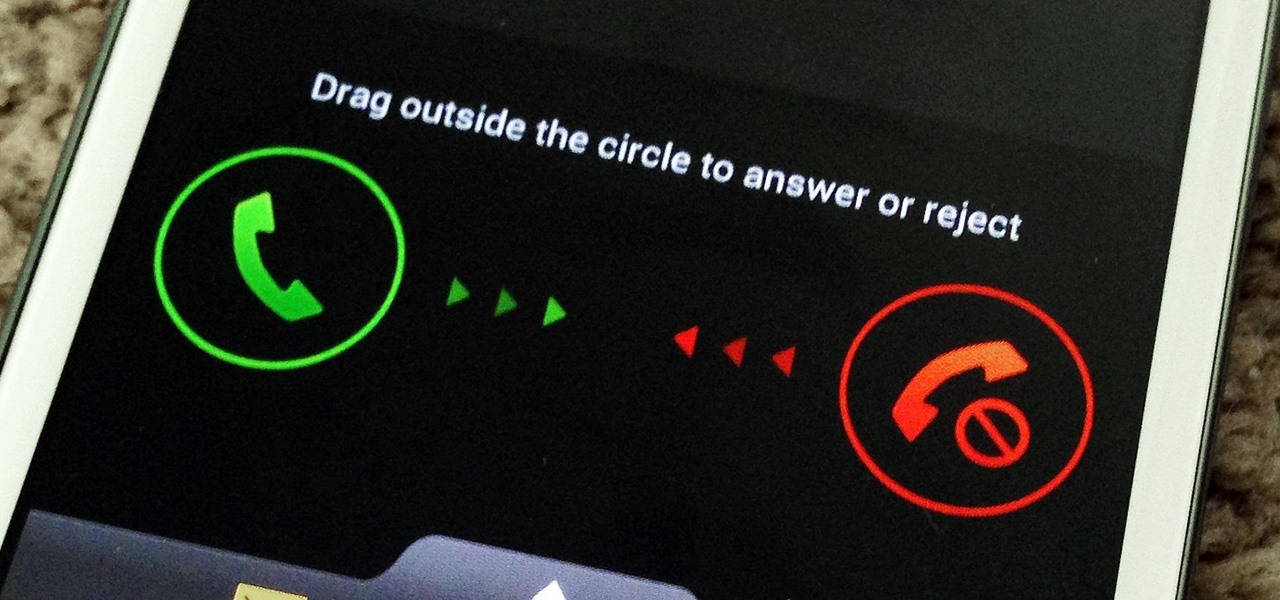
You don't have to be in debt to receive annoying calls from unwanted numbers. You may love your grandma, but if she calls you three times a day to ask how to turn on the television, you might just want to push all of her calls to voicemail.

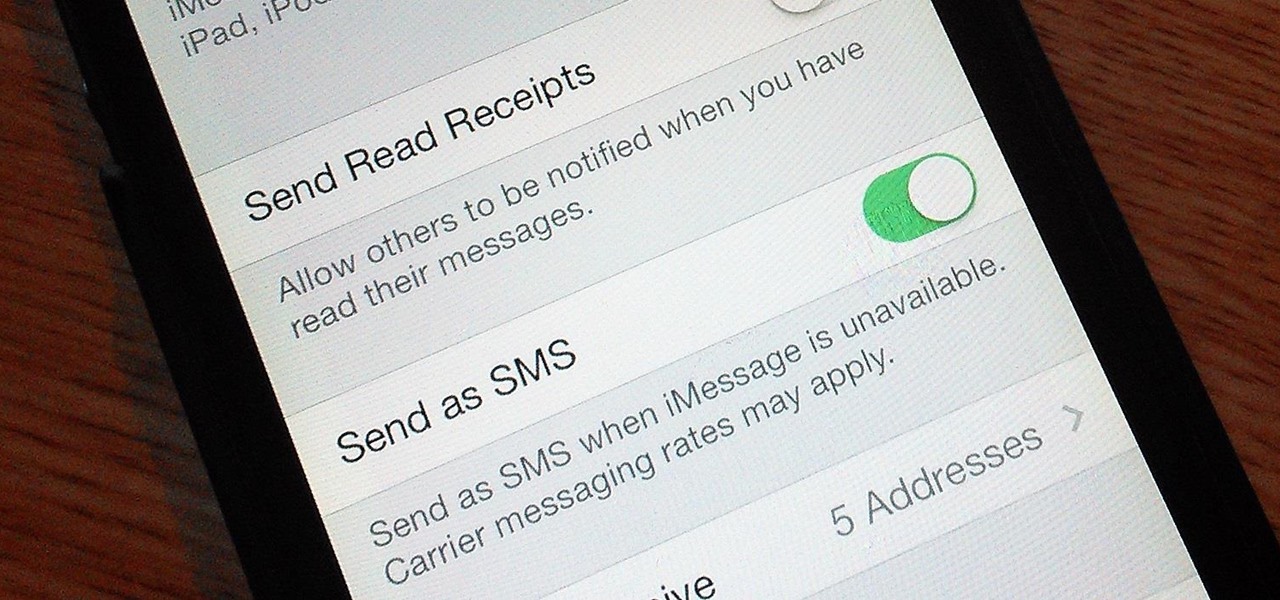
If you're an iPhone user, iMessage is great for cutting down on SMS costs from your carrier, but it doesn't always work right away.

It's that time of the year again when scores of students are flocking to stores for school supplies. Pens, pencils, books, and for math students, calculators.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

If you've never played with a Nexus 10 tablet, then you probably have no idea that your Nexus 7 actually has a different user interface. For some reason, Google decided it was better for the Nexus 7 to use a phone UI instead of a tablet one, but luckily for us, we don't have to accept that.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

One of the best features on the new Moto X is Touchless Control, which lets you verbally ask the device questions or perform tasks without ever touching or turning on the display, a feature that would do quite nicely on the Nexus 7, if it could handle it.

From a very early age we have an intrinsic obsession with things that float. Why do you think we love balloons and bubbles so much? So, it's no surprise that our smartphones are being invaded by floating features.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

David Blaine has made millions off his magic tricks and mind-bending illusions, so why shouldn't we get in on the action, too? Well, your Samsung Galaxy S3 can do all kinds of things, but magic isn't one of them...yet.

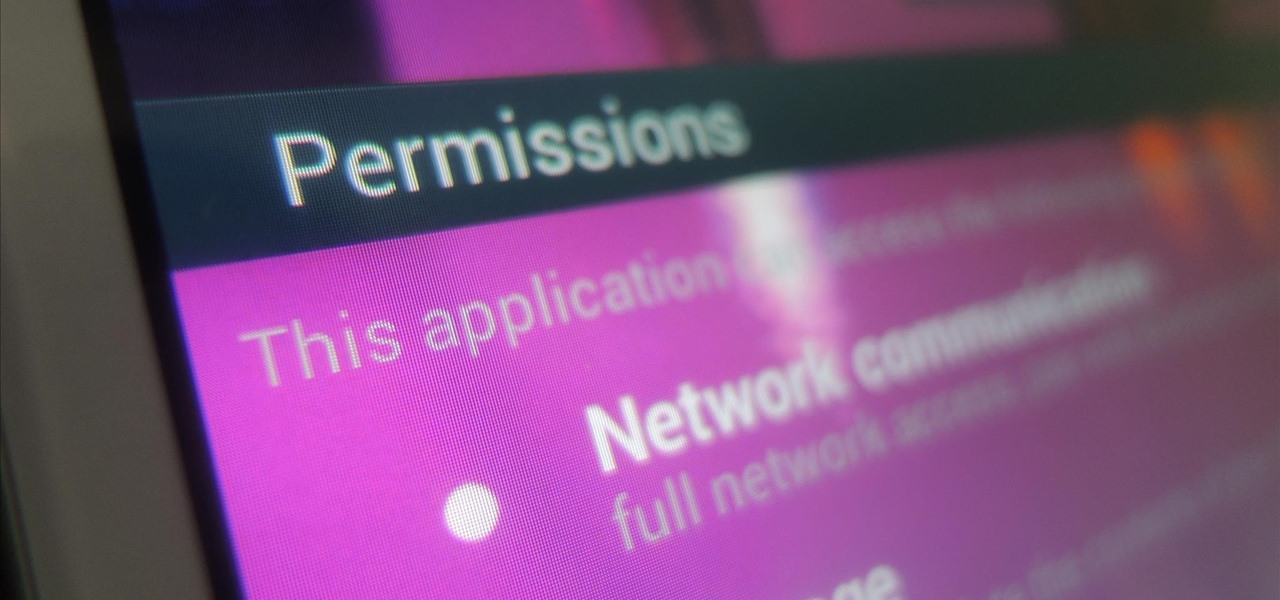
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

While there are many customization options available for the Samsung Galaxy Note 2, they aren't always easy. The large selection of custom ROMs and difficulty implementing certain hacks and mods can be a nightmare for anyone not well versed in all things Android. But the good news is, it doesn't always have to be complicated.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Don't always believe the marketing hype. "PlayStation Certified" does not mean anything to a softModder. All this indicates is that a smartphone or tablet labeled as "PlayStation Certified" has met the guidelines and hardware requirements issued by Sony to display PlayStation Mobile (PSM) content from the PlayStation Mobile Store correctly. No Nexus 7 here.

Apple is set to release its latest operating system for iPad, iPhone, and iPod touch this fall, and if you haven't noticed yet from our iOS 7 softModder guides, it's going to be pretty slick.

If you want to play games that aren't in the iOS App Store, Apple makes it pretty tough for you. Usually, the only solution is to jailbreak your iPad or iPhone, but that's something most avoid because it will void the warranty and may cause potential bricking issues.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Some of my favorite games include Super Mario World, Super Mario Kart, Super Punch Out, and Super Metroid. If you still haven't caught on, I'm a big Super Nintendo fan. Growing up in the '90s meant spending Saturday mornings engulfed in front on my TV with the good old SNES running hard.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

Theming and modding are a big part of the softModder community, but there are endless ways to customize our Android devices. Which ones should you download? Which ones should you avoid? It's extremely frustrating to find them all—and pick and choose.

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

The battery in the Samsung Galaxy S4 may pack 500 more milliamps per hour than the old S3 battery, but that doesn't necessarily mean more battery life. High-powered devices need lots of juice, and the S4 is definitely more powerful than its predecessor. The new battery can handle a third more in standby days, and over twice as much in talk time hours. But, when you live on your phone all day long, that means nothing. You're battery is still going to have a hard time keeping up with you.

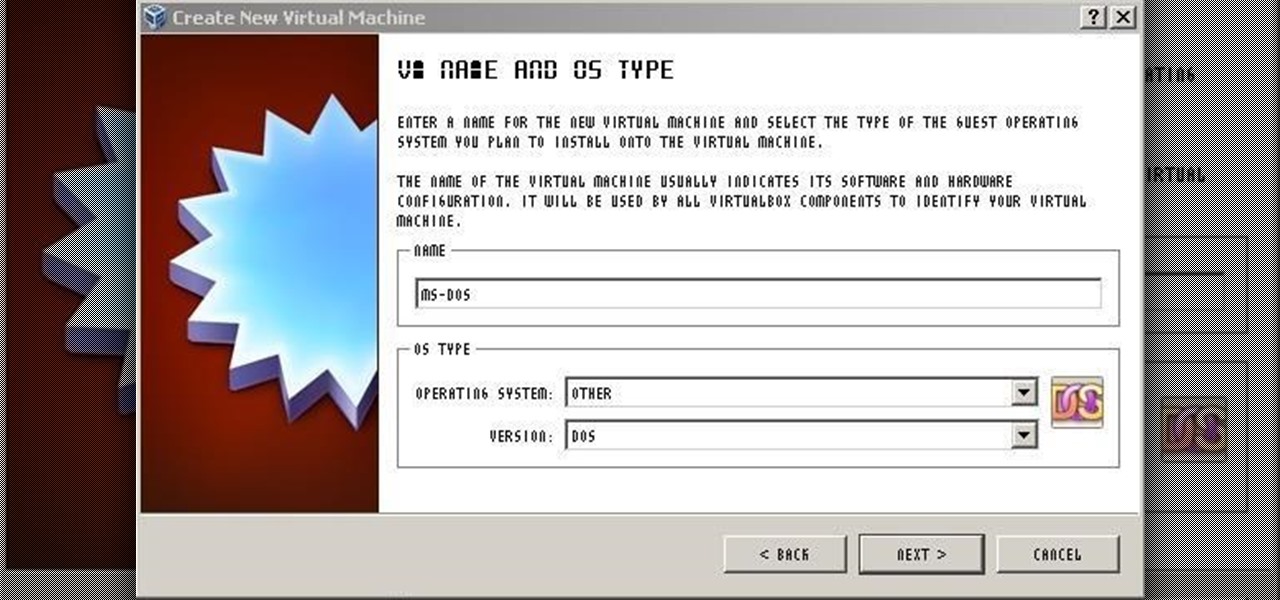
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...

Remember that PSP you had? I pretty much dropped mine when smartphones became more prevalent in the mobile gaming scene. Why would I want to carry around a huge PlayStation Portable when I've already got an Android in my pocket?

I spend practically all day surfing the web and writing on my laptop, and just as much time texting and checking emails on my smartphone. So, it's only natural for me to charge my iPhone using the USB port on my MacBook Pro.

Screenshots are great, but sometimes they don't tell the whole story. You can show off that new app you got or that awesome new live wallpaper, but a screenshot isn't going to get the point across. What exactly am I trying to show you in the screenshot above? You probably have no idea, and that's the point. You can't see the action I'm trying to demonstrate, but in a video you can.

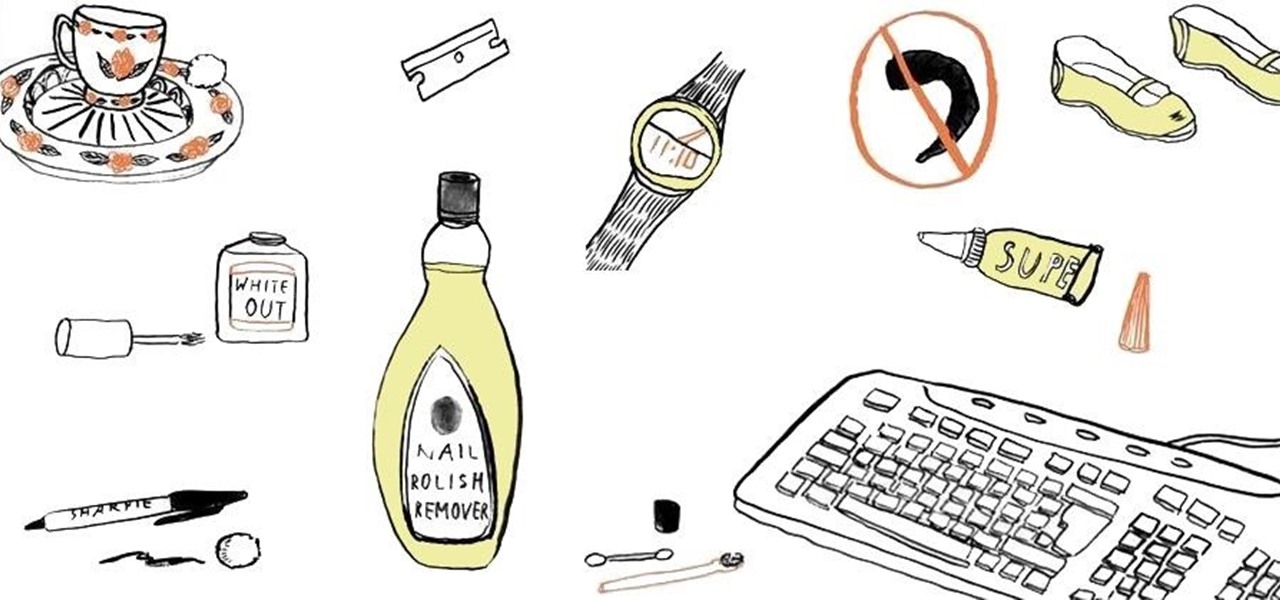
Acetone-based nail polish remover is great for removing nail polish, and it's also great for some DIY uses around the home. From eliminating scratches to fixing the consistency of correction fluid, its uses are varied but all effective. With nail polish remover, you can also clean your computer keyboard, get rid of ink stains, and even remove leeches from your skin. Talk about versatile!

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

We've all been there. Your phone's either dead or barely hanging on with a few minutes of life left, and you only have a small window of time to charge it before you need to head out. Sure, you can charge it for the few minutes you have, but what's the point if your device is going to die again in several minutes?

They say imitation is the sincerest form of flattery. You have a Google Nexus 7 tablet, but you really wanted an iPad. What do you do? Skin it to make it look like an iPad, of course! Today, I’ll show you how to transform your Nexus 7 into an iPad and trick your friends into thinking it runs iOS! Let’s begin.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

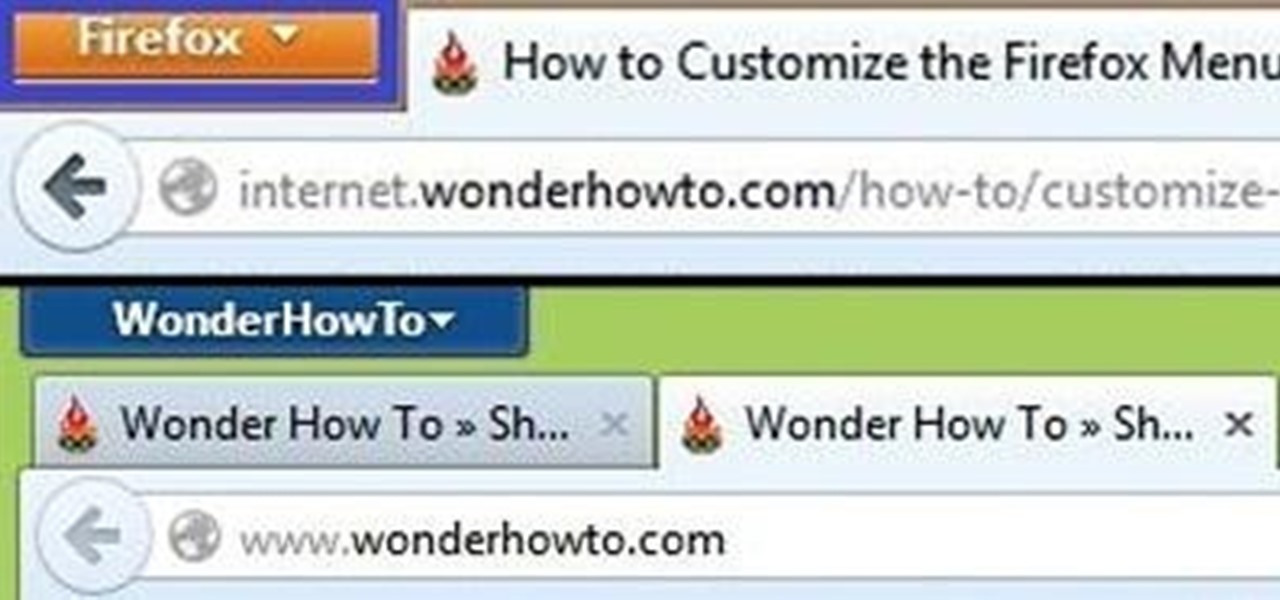
Browser customization is one of Firefox's best attributes. You can personalize your Firefox with extensions, add-ons, themes, and so on. And if all of that still doesn't cut it, you can even customize the Firefox Menu button to say whatever you want. To start off, you'll need to download a user file editor called ChromEdit Plus. Click Add to Firefox, then hit Allow when prompted and wait for it to install. You will need to restart Firefox afterwards.