
News: Leaked Videos Show Off the HTC One M9
While the official unveiling will happen at Mobile World Congress in Barcelona on March 1st, several images and promotional videos for the HTC One M9 have leaked online.


While the official unveiling will happen at Mobile World Congress in Barcelona on March 1st, several images and promotional videos for the HTC One M9 have leaked online.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Soup can be one of the most finicky dishes to make. While seemingly innocuous at first, the texture of this meal can change in an instant. For example, adding too many vegetables can result in soup that's too watery, such as tomatoes, which contain a lot of liquid.

While most people build collections of things with intrinsic value such as coins, stamps, or rare post cards, I collect wine corks—the natural ones, not the plastic kind. Corks are a natural product harvested from the cork oak tree. It takes the better part of 10 to 12 years before a tree can have its bark manually removed for the production of cork. Thankfully, no tree is harmed in the process and in 12 years, the tree bark can be harvested yet again.

Sweaty palms, stuttered speech, and terror blackouts: if you're someone who absolutely despises speaking before audiences, you've probably experienced side effects like these. No matter how well prepared we are, or how familiar our audience is, giving a presentation can be an experience more terrifying than death, according to psychologists. Unfortunately, it's impossible to avoid public speeches, but you can make these events less frightening with a few simple hacks.

One of the golden rules to cooking a Thanksgiving turkey is to place it on a roasting rack before it goes into the oven. Missing this step and cooking it directly on the pan will burn the bottom of the bird, resulting in overcooked, dry meat.

The "Smart Keyboard" on the LG G3 has received a lot of praise for its ability to adequately analyze user keystrokes, provide adjustable sizes, and customize key placements, among other things. These features, combined with predictive text, swipe gestures, and autocorrect make the Smart Keyboard one of the most powerful typing tools available for Android. Now, it's easy to get it installed on your Samsung Galaxy Note 3.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.
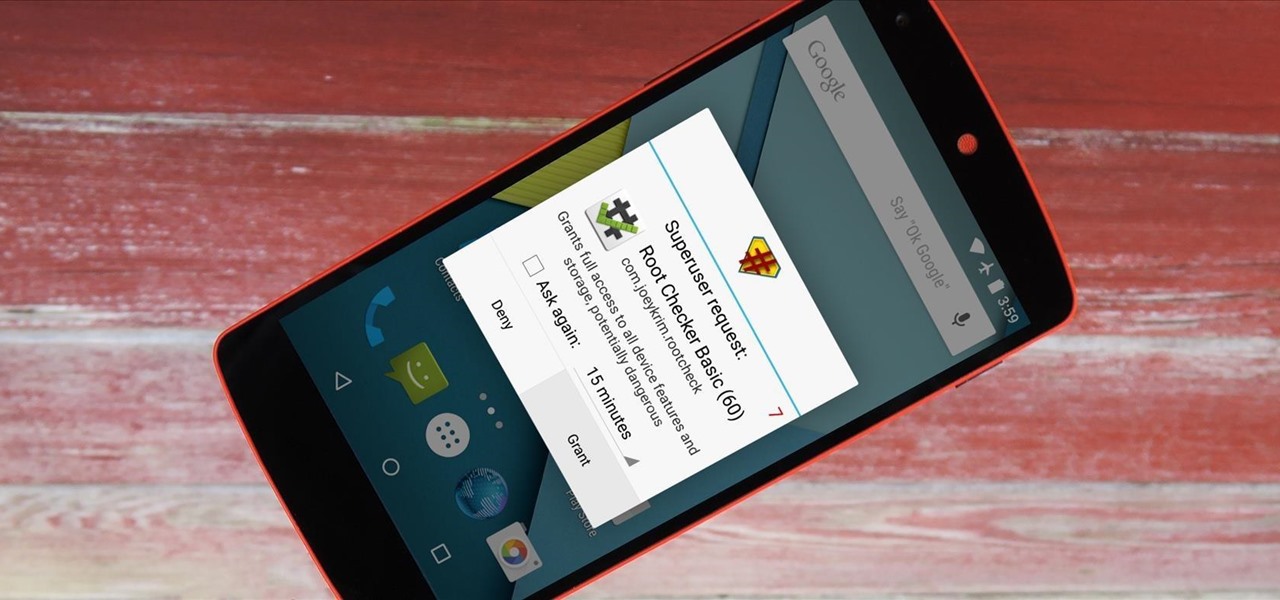
It didn't take long at all for developer Chainfire to sort out a root method for the new Android 5.0 Lollipop. After handling a few issues with changes to the SELinux kernel module, Chainfire pushed out an update to his popular SuperSU root app.
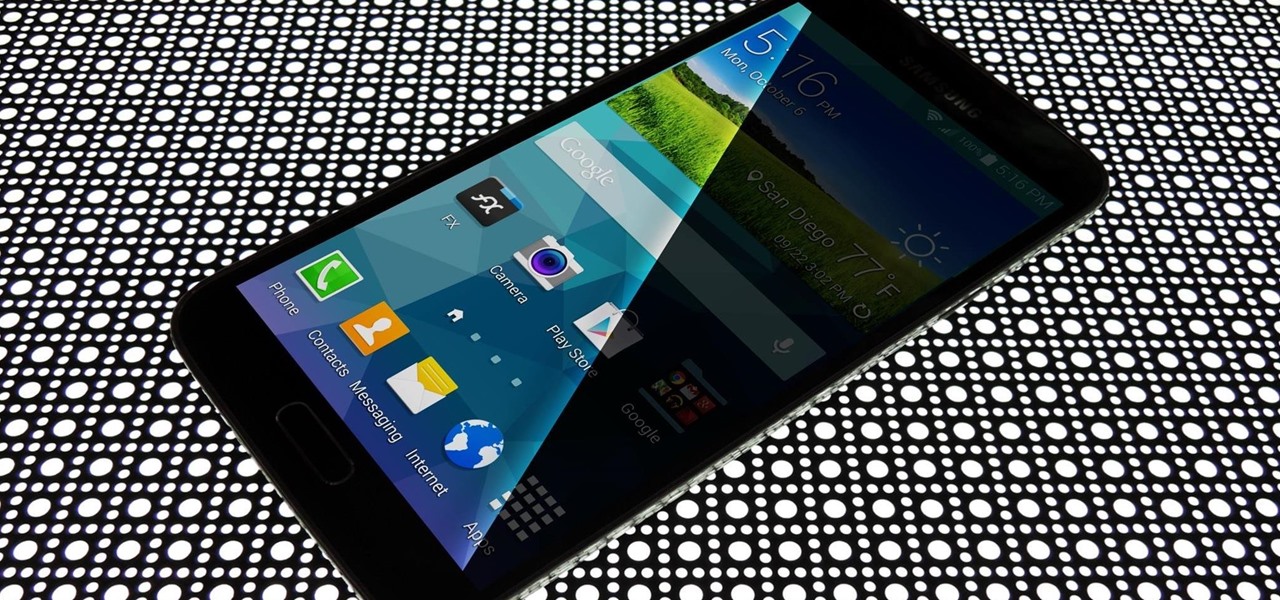
If you pay close attention, you might notice that the screen on your Android begins to flicker or pulsate when you lower the brightness past a certain point. This is a result of the AMOLED technology Samsung, among other manufacturers, use in their displays, and the way that these types of screens operate.

If your headlights are not working when you pull the switch or if your turn signals are the only things working, Then your headlight switch might be broken. This is often due to loose connections or wear and tear on the part itself. The first thing I would highly recommend before starting this project is to make sure that your connections at the headlights are tight. You can test this by simply putting a piece of foil in the connector or by bending the prongs slightly. Also check to see if yo...
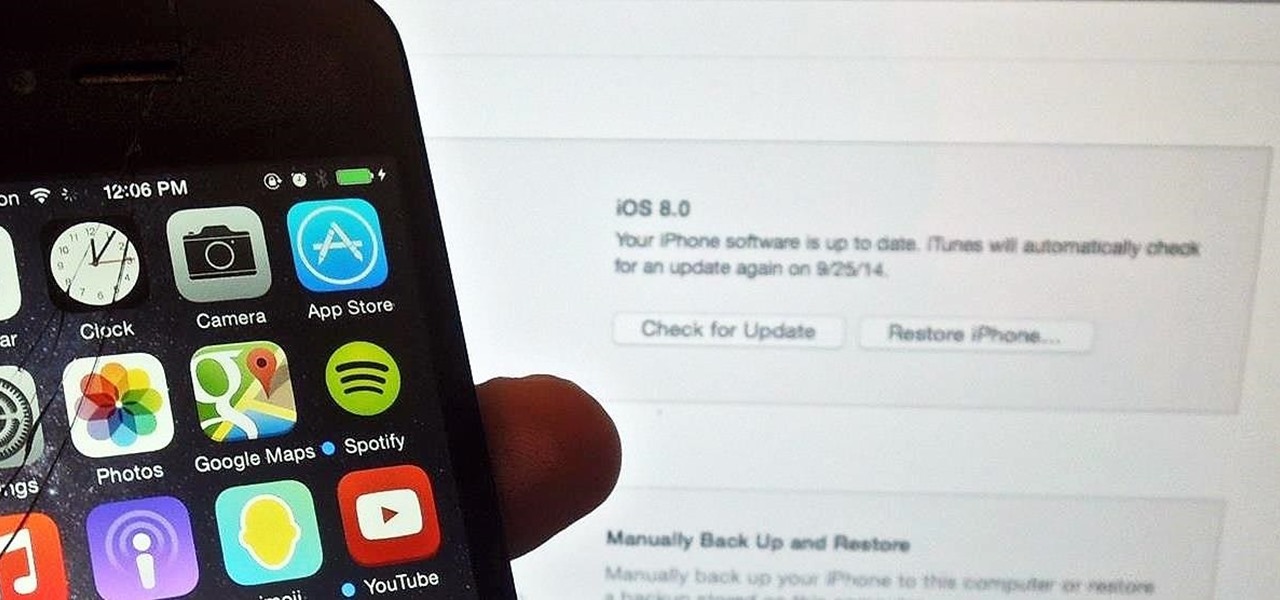
There are a lot of great new features in iOS 8, but not everyone is enjoying them. Some of you may just genuinely prefer iOS 7 over iOS 8, and some of you may be experiencing lag on older devices like the iPhone 4S, however minimal it may be. Whatever the reason, if you don't want iOS 8 on your iPad, iPhone, or iPod touch, there's still time to downgrade back to iOS 7.1.2.

iPad, iPhone, and iPod touch owners: it's that time again. iOS 8 has been released to the public, and those who have been eager to update since Apple's WWDC announcement won't have to wait any longer. Since iOS 8 promises to pack a bunch of new, really great features, it's time to present your options for getting on the latest and greatest for your Apple device.
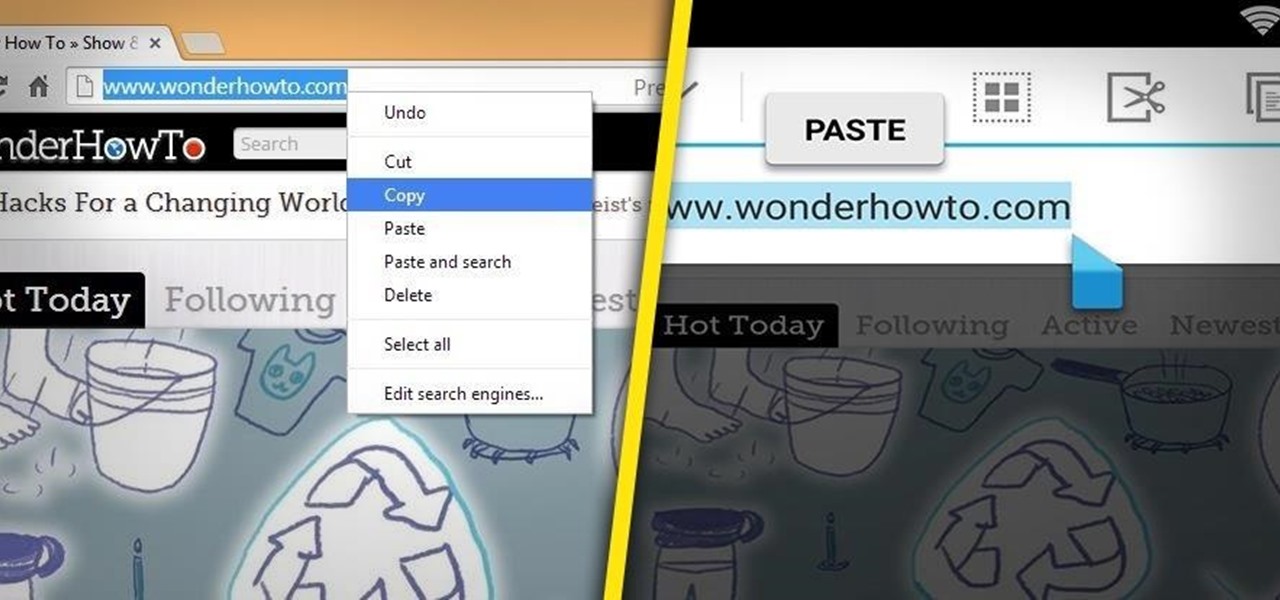
Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.
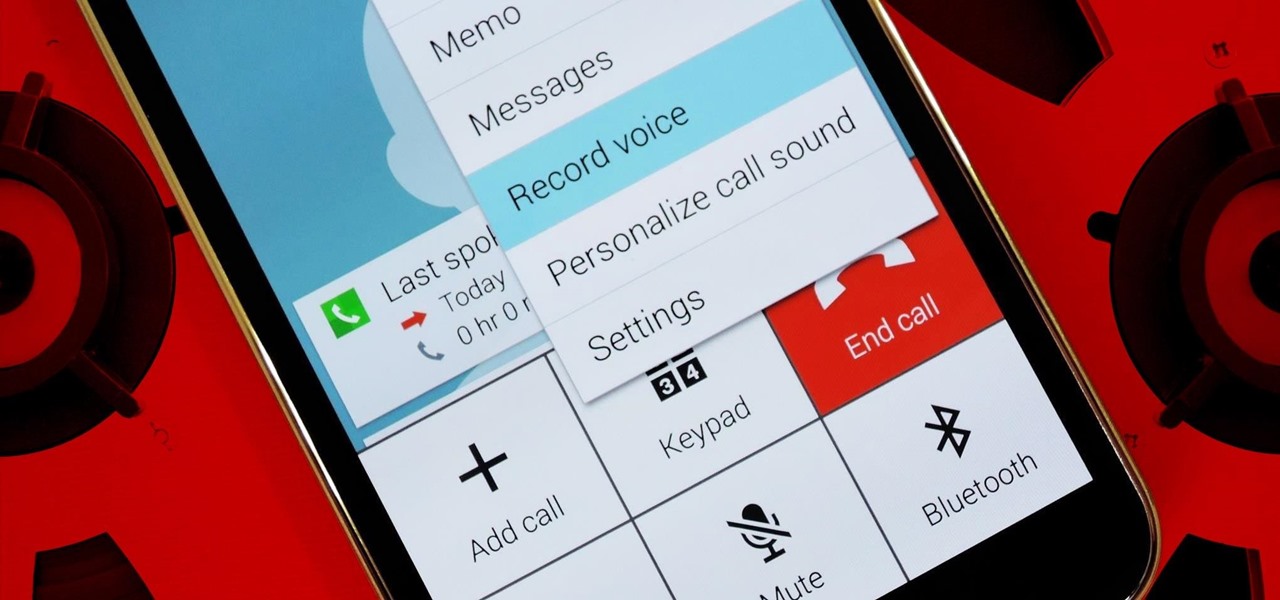
Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

How many times do you misplace your phone? Once a day? Twice? As much as you may hate losing your phone, it always seems to happen, and finding it isn't very easy if you left it on silent mode.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

I went to one of the Berlins market on a search for Pearls / Beads and other stuff for Macrame. I really love the sound of this market which is in lots of different languages of the world and its so cool. And then I went to Alexanderplatz and you can see how it looks there, if you haven't been there.

Finally! A media box that gives you everything you want, in one tiny package. The EzeeCube will allow you to view your pictures and videos while staying organized at the same time.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

Sony is ready to get into the micro-console gaming fight, with its PlayStation TV set to debut this fall.

To-do list and reminder apps are a dime a dozen on Google Play, so trying to find the right one for you could take hours as you sift through hundreds of similar apps and widgets. Well, search no more, as we've found one of the most well-designed and easy-to-use reminder apps out there.

Last week marked the announcement of LG's new G3 smartphone, and with it came a ton of new features and improvements to their Optimus UI. While most manufacturers put little effort into their keyboards—probably due to the attraction of third-party alternatives—LG has made their latest iteration one of the best OEM keyboards I have ever used.

A month ago, we showed you what I, and many around the web, dubbed the "Nexus Killer". That device is the OnePlus One, a low-priced, high-powered, CyanogenMod-run Android device.

Your beloved Samsung Galaxy S3 is nearing the end of its life cycle. Sure, it can do most of what newer devices can, especially if you were lucky enough to receive the KitKat update, but your diminishing battery and scratched up screen have seen better days.

Removing the thin aluminum foil wrapping from a Hershey Kiss isn't necessarily a difficult thing, but even the easiest of things can be annoying sometimes. For instance, getting chocolate under your fingernail when you're trying to peel the wrapper off, or making a wrapper mess. To make this first-world problem go away, simply grab a Hershey Kiss in-between your index finger and thumb, then pull on the paper plume to yank the chocolate straight out of the wrapper. The plume was originally des...

This Square knot design feature picots, which are small loops at the sides of the knot. Picots are simply loops along the edges. Picot Designs are vintage Macrame techniques. They are often used to make the edges of craft items to look like as flower petals. This is a good project for children and beginners to learn one of the basic knots frequently used in Macrame. To this pattern you can add pearls and have an interesting look.

Midway through 2013, a popular custom ROM called Paranoid Android introduced their multitasking feature "Halo." Bubble-style notifications inspired by Facebook chat heads pop up near the top of the screen, and you simply tap on them to bring up the app in a floating window.
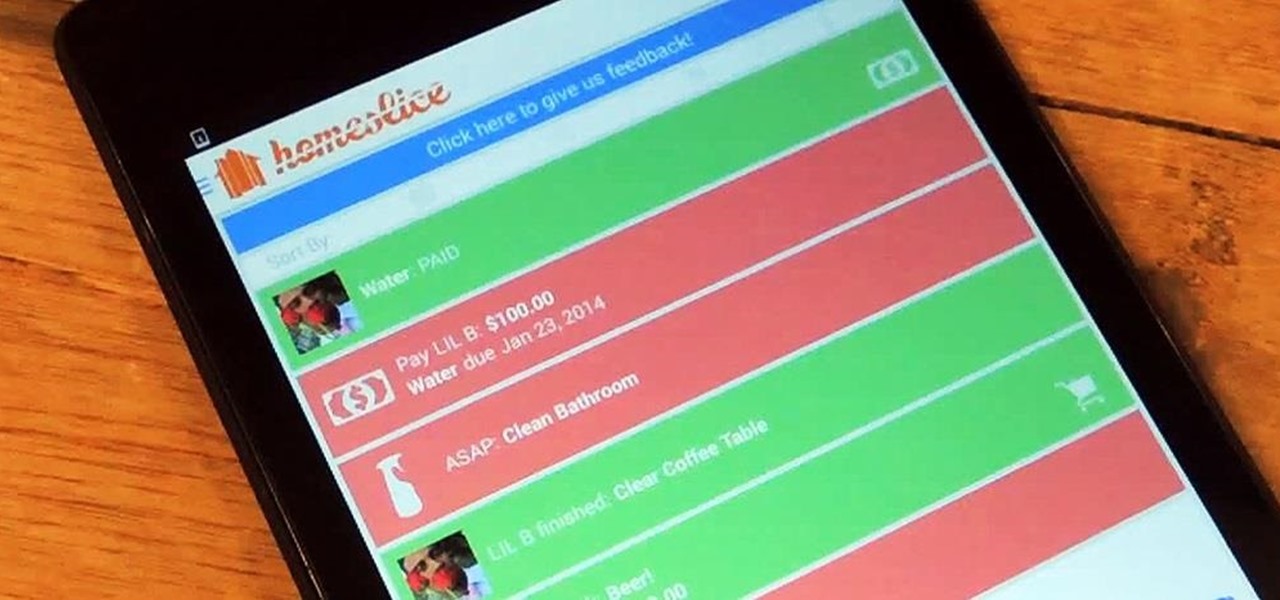
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!

Video: . It can some time be a pain to separate egg whites from the yolk. I did some searching online and came to find some great ways to separate them.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.
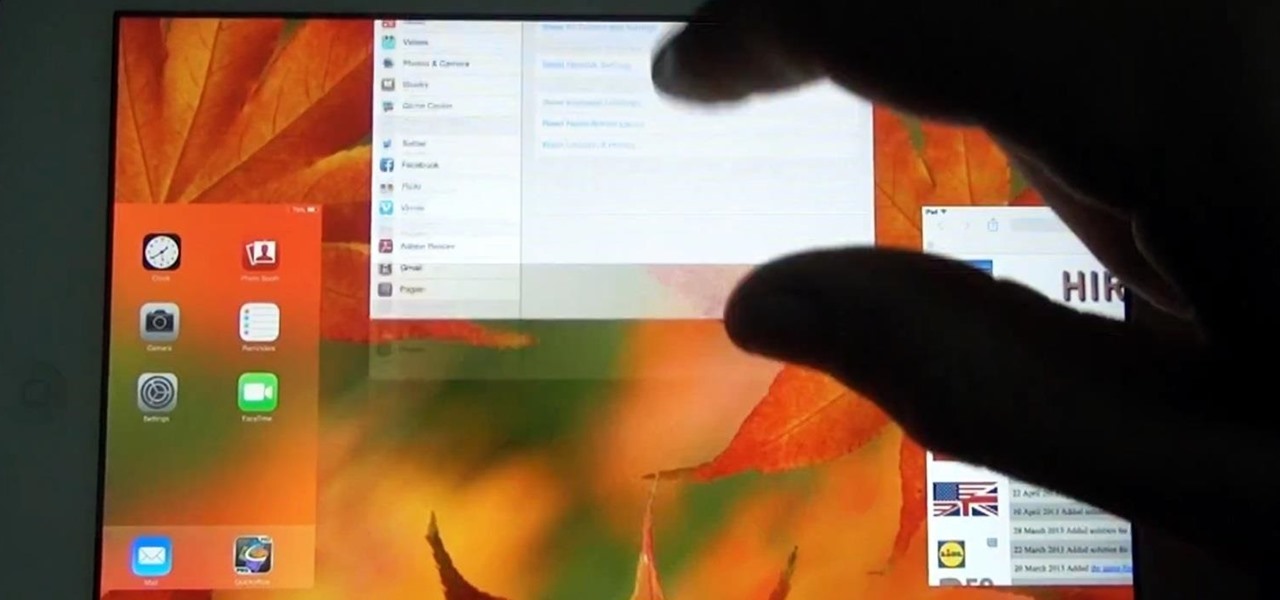
The new Apple iOS 7 is here for your iPad Mini. Closing running apps prevents them from taking up precious memory, resources and battery. Simply quitting an app by pressing the home button doesn't work; the application is still running. Watch the video below to see how to close them completely.


Video: . In Adobe Photoshop CS5.1 there are several ways to perform same action. I make a video tutorial in which you can learn that how to combine two images to perform your different operations. I used a very simple and quick method. To follow my method you can get a quick adjustment of two or more then two images just in single frame and get the result you desire.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.